Kali-linux:nmap命令
概念
Nmap用于在远程机器上探测网络,执行安全扫描,网络审计和搜寻开放端口。它会扫描远程在线主机,该主机的操作系统,包过滤器和开放的端口。
使用场景
掌握了具体使用场景,主要就是掌握如下参数使用:以192.168.31.18为目标靶机
1.普通扫描
root@sunjin:/home/sunjin# nmap 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 09:46 CST
Nmap scan report for 192.168.31.18
Host is up (0.0014s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
443/tcp open https
3306/tcp open mysql
8089/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.21 seconds
通过添加-sV参数,能够得到服务版本信息,
root@sunjin:/home/sunjin# nmap -sV 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 09:48 CST
Nmap scan report for 192.168.31.18
Host is up (0.0012s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
443/tcp open ssl/https
3306/tcp open mysql MySQL 5.7.32
8089/tcp open unknown
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port443-TCP:V=7.80%T=SSL%I=7%D=11/6%Time=5FA4AB6E%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,DE,"HTTP/1\.1\x20302\x20\r\nCache-Control:\x20private\r\n
SF:Expires:\x20Thu,\x2001\x20Jan\x201970\x2000:00:00\x20GMT\r\nLocation:\x
SF:20https://localhost/index2\.html\r\nContent-Language:\x20zh-CN\r\nConte
SF:nt-Length:\x200\r\nDate:\x20Fri,\x2006\x20Nov\x202020\x2001:48:26\x20GM
SF:T\r\nConnection:\x20close\r\n\r\n")%r(HTTPOptions,B8,"HTTP/1\.1\x20200\
SF:x20\r\nCache-Control:\x20private\r\nExpires:\x20Thu,\x2001\x20Jan\x2019
SF:70\x2000:00:00\x20GMT\r\nAllow:\x20GET,HEAD,POST,PUT,PATCH,DELETE,OPTIO
SF:NS\r\nDate:\x20Fri,\x2006\x20Nov\x202020\x2001:48:26\x20GMT\r\nConnecti
SF:on:\x20close\r\n\r\n")%r(FourOhFourRequest,113,"HTTP/1\.1\x20302\x20\r\
SF:nCache-Control:\x20private\r\nExpires:\x20Thu,\x2001\x20Jan\x201970\x20
……
通过添加-sC参数,能够得到更加详细的服务信息
root@sunjin:/home/sunjin# nmap -sC 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 09:50 CST
Nmap scan report for 192.168.31.18
Host is up (0.0012s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 8e:45:b1:49:8e:4b:80:a7:cc:f0:ba:6c:be:a1:97:a1 (RSA)
| 256 2d:13:df:d4:9e:87:50:e8:db:fe:1c:f4:8a:7e:4c:6c (ECDSA)
|_ 256 16:54:fd:53:27:c6:61:4f:76:f9:85:79:97:2b:0c:c5 (ED25519)
443/tcp open https
| http-methods:
|_ Potentially risky methods: PUT PATCH DELETE
| http-title: \xE5\xB7\xA5\xE4\xB8\x9A\xE4\xBA\x92\xE8\x81\x94\xE7\xBD\x91\xE8\xAE\xA4\xE8\xAF\x81\xE7\xBD\x91\xE5\x85\xB3\xE7\xAE\xA1\xE7\x90\x86\xE7\xB3\xBB\xE7\xBB\x9F
|_Requested resource was /login.html
| ssl-cert: Subject: commonName=192.168.31.111/organizationName=demo/countryName=cn
| Not valid before: 2020-10-13T03:14:26
|_Not valid after: 2021-10-13T03:14:26
|_ssl-date: 2020-11-06T01:50:37+00:00; -4s from scanner time.
3306/tcp open mysql
| mysql-info:
| Protocol: 10
| Version: 5.7.32
| Thread ID: 13
| Capabilities flags: 65535
| Some Capabilities: SupportsLoadDataLocal, LongPassword, IgnoreSpaceBeforeParenthesis, SwitchToSSLAfterHandshake, DontAllowDatabaseTableColumn, IgnoreSigpipes, SupportsTransactions, Speaks41ProtocolOld, Speaks41ProtocolNew, InteractiveClient, ConnectWithDatabase, Support41Auth, ODBCClient, SupportsCompression, FoundRows, LongColumnFlag, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: 9B|\x7F \x04,[\x03^Y\x05\x0E]x\x14\x0C\x0C\x19v
|_ Auth Plugin Name: mysql_native_password
8089/tcp open unknown
Host script results:
|_clock-skew: -4s
Nmap done: 1 IP address (1 host up) scanned in 1.74 seconds
2.漏洞扫描
#使用nmap对某主机进行一系列的证书鉴权检查
nmap --script=auth [目标IP]
root@sunjin:/home/sunjin# nmap --script=auth 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 09:57 CST
Nmap scan report for 192.168.31.18
Host is up (0.0014s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-auth-methods:
| Supported authentication methods:
| publickey
| gssapi-keyex
| gssapi-with-mic
|_ password
| ssh-publickey-acceptance:
|_ Accepted Public Keys: No public keys accepted
443/tcp open https
|_http-config-backup: ERROR: Script execution failed (use -d to debug)
| http-vuln-cve2010-0738:
|_ /jmx-console/: Authentication was not required
3306/tcp open mysql
8089/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 5.31 seconds
#使用nmap 对常见的服务进行暴力力破解
nmap --script=brute [目标IP]
可以看到有不少密码被破译出来了!
root@sunjin:/home/sunjin# nmap --script=brute 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 09:59 CST
Nmap scan report for 192.168.31.18
Host is up (0.0011s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-brute:
| Accounts: No valid accounts found
| Statistics: Performed 0 guesses in 1 seconds, average tps: 0.0
|_ ERROR: The service seems to have failed or is heavily firewalled...
443/tcp open https
|_citrix-brute-xml: FAILED: No domain specified (use ntdomain argument)
| http-brute:
|_ Path "/" does not require authentication
|_http-joomla-brute: ERROR: Script execution failed (use -d to debug)
| http-wordpress-brute:
| Accounts:
| root:root - Valid credentials
| netadmin:netadmin - Valid credentials
| guest:guest - Valid credentials
| user:user - Valid credentials
| web:web - Valid credentials
| sysadmin:sysadmin - Valid credentials
| administrator:administrator - Valid credentials
| webadmin:webadmin - Valid credentials
| admin:admin - Valid credentials
| test:test - Valid credentials
|_ Statistics: Performed 13 guesses in 1 seconds, average tps: 13.0
3306/tcp open mysql
| mysql-brute:
| Accounts:
| root:123456 - Valid credentials
|_ Statistics: Performed 45012 guesses in 317 seconds, average tps: 191.2
| mysql-enum:
| Valid usernames:
| root:<empty> - Valid credentials
| netadmin:<empty> - Valid credentials
| guest:<empty> - Valid credentials
| user:<empty> - Valid credentials
| web:<empty> - Valid credentials
| sysadmin:<empty> - Valid credentials
| administrator:<empty> - Valid credentials
| webadmin:<empty> - Valid credentials
| admin:<empty> - Valid credentials
| test:<empty> - Valid credentials
|_ Statistics: Performed 10 guesses in 1 seconds, average tps: 10.0
8089/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 317.33 seconds
#使用nmap 进行基本的扫描
nmap --script=default [目标IP]
这个和普通扫描结果差不多
#使用nmap 进行信息挖掘
nmap --script=discovery [目标IP]
这个会显示大量服务消息,例如TLS的加密算法类型
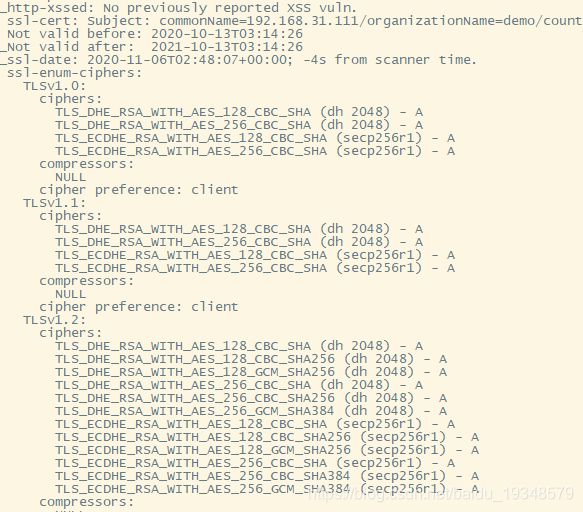
#使用nmap 进行拒绝服务攻击
nmap --script=dos [目标IP]
这个没有测试,毕竟是公共服务器
#使用nmap 利用已知的漏洞入侵系统
nmap --script=exploit [目标IP]
#使用nmap 进行利用第三方的数据库或资源进行信息收集或者攻击
nmap --script=external [目标IP]
这个没有测试,毕竟是公共服务器
#使用nmap 进行模糊测试,发送异常的包到目标机,探测出潜在漏洞
nmap --script=fuzzer [目标IP]
#使用nmap 进行入侵,此类脚本可能引发对方的IDS/IPS的记录或屏蔽
nmap --script=intrusive [目标IP]
这个没有测试,毕竟是公共服务器
#使用nmap 探测目标机是否感染了病毒、开启了后门等信息
nmap --script=malware [目标IP]
root@sunjin:/home/sunjin# nmap --script=malware 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 13:50 CST
Nmap scan report for 192.168.31.18
Host is up (0.0011s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
443/tcp open https
3306/tcp open mysql
8089/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds
#使用nmap 对系统进行安全检查
nmap --script=safe [目标IP]
这个结果比较长,可以自行测试
#使用nmap 对目标机进行检查是否存在常见的漏洞
nmap --script=vuln [目标IP]
root@sunjin:/home/sunjin# nmap --script=vuln 192.168.31.18
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-06 13:47 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.31.18
Host is up (0.0012s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
443/tcp open https
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /login.html: Possible admin folder
| /examples/: Sample scripts
|_ /docs/: Potentially interesting folder
|_http-majordomo2-dir-traversal: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-vuln-cve2010-0738:
|_ /jmx-console/: Authentication was not required
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_sslv2-drown:
3306/tcp open mysql
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
8089/tcp open unknown
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 137.77 seconds