从零开始做题:2019年湖湘杯miscmisc
题目信息
https://adworld.xctf.org.cn/challenges/list
解题环境
KAli2023虚拟机,windows10
解题工具
binwalk Advanced Zip Password Recover StegSolve Zsteg
知识点
文件分离 通过binwalk等工具将一个文件拆分恢复为原数量的文件
明文攻击 通过选择对攻击有利的特定明文及其对应的密文,求解密钥或从截获的密文求解相应明文的密码分析方法
解题步骤
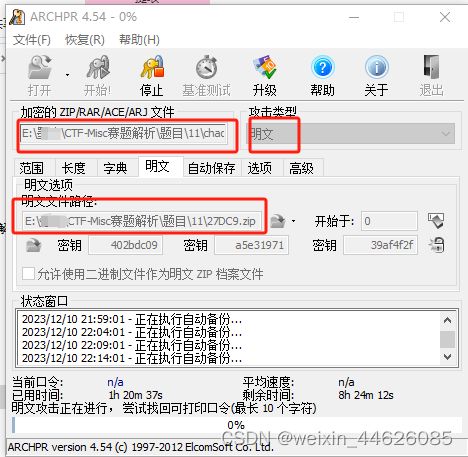
压缩包明文攻击
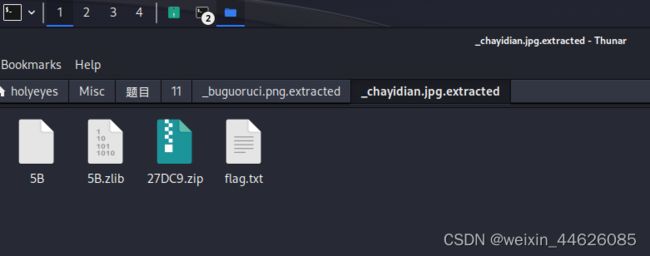
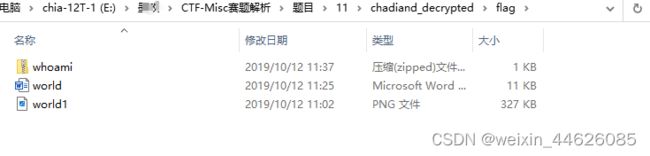
第二个包可以看到有一个flag.txt没有加密,crc校验和加密包里一样,说明是同一个文件,直接压缩包明文攻击解密。得到新的加密压缩包和word文档还有一张图
解Lsb隐写
图片是png图片。用zsteg跑lsb隐写解密,发现密码提示
压缩包密码猜解
在word文档里发现有隐藏字符,但隐藏字符本身不具备特殊含义,将每一行隐藏字符的最后一个字母连起来和上一步lsb得到的半截密码拼接,解密成功,得到flag
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/题目/11]
└─$ binwalk -e buguoruci.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 198 x 195, 8-bit/color RGBA, non-interlaced
91 0x5B Zlib compressed data, compressed
WARNING: Extractor.execute failed to run external extractor 'jar xvf '%e'': [Errno 2] No such file or directory: 'jar', 'jar xvf '%e'' might not be installed correctly
46098 0xB412 Zip archive data, at least v2.0 to extract, compressed size: 291018, uncompressed size: 291005, name: chadiand.zip
337158 0x52506 Zip archive data, at least v2.0 to extract, compressed size: 162503, uncompressed size: 163449, name: chayidian.jpg
499893 0x7A0B5 End of Zip archive, footer length: 22
499915 0x7A0CB Zip archive data, at least v2.0 to extract, compressed size: 162503, uncompressed size: 163449, name: chayidian.jpg
662461 0xA1BBD Zip archive data, at least v2.0 to extract, compressed size: 290992, uncompressed size: 291005, name: chadian.zip
953682 0xE8D52 End of Zip archive, footer length: 22
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/题目/11/_buguoruci.png.extracted]
└─$ binwalk -e chayidian.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 530 x 449, 8-bit/color RGBA, non-interlaced
91 0x5B Zlib compressed data, compressed
163273 0x27DC9 Zip archive data, at least v2.0 to extract, compressed size: 26, uncompressed size: 52, name: flag.txt
163427 0x27E63 End of Zip archive, footer length: 22
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/题目/11/_buguoruci.png.extracted]
└─$
工具 Advanced Zip Password Recover ,
//工具下载地址
https://pan.baidu.com/s/182n4JAAzbgPv2XDhtklJyw
提取码:7949
将kali2023下的两个压缩文件包拷贝到windows
安装Stegsolve
// 工具下载 链接:https://pan.baidu.com/s/1hH2qthCCb7alApkhEUyL_g
// 提取码:7pcb
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc]
└─$ java -version
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
openjdk version "17.0.8" 2023-07-18
OpenJDK Runtime Environment (build 17.0.8+7-Debian-1)
OpenJDK 64-Bit Server VM (build 17.0.8+7-Debian-1, mixed mode, sharing)
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc]
└─$ java -jar Stegsolve.jar
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
打开图片然后试探各种通道,在LSB BGR条件下发现pass,所以这是LSB信息隐写。得到pass:z^ea
安装zsteg
GitHub - zed-0xff/zsteg: detect stegano-hidden data in PNG & BMP
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc]
└─$ git clone https://github.com/zed-0xff/zsteg.git
(base) ┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc/zsteg]
└─$ sudo gem install zsteg
(base) ┌──(holyeyes㉿kali2023)-[~/…/题目/11/chadiand_decrypted/flag]
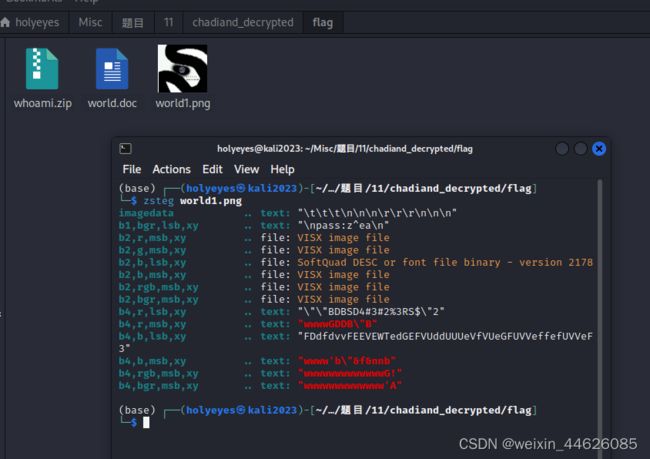
└─$ zsteg world1.png
imagedata .. text: "\t\t\t\n\n\n\r\r\r\n\n\n"
b1,bgr,lsb,xy .. text: "\npass:z^ea\n"
b2,r,msb,xy .. file: VISX image file
b2,g,msb,xy .. file: VISX image file
b2,b,lsb,xy .. file: SoftQuad DESC or font file binary - version 2178
b2,b,msb,xy .. file: VISX image file
b2,rgb,msb,xy .. file: VISX image file
b2,bgr,msb,xy .. file: VISX image file
b4,r,lsb,xy .. text: "\"\"BDBSD4#3#2%3RS$\"2"
b4,r,msb,xy .. text: "wwwwGDDB\"B"
b4,b,lsb,xy .. text: "FDdfdvvFEEVEWTedGEFVUddUUUeVfVUeGFUVVeffefUVVeF3"
b4,b,msb,xy .. text: "wwww'b\"&f&nnb"
b4,rgb,msb,xy .. text: "wwwwwwwwwwwwwG!"
b4,bgr,msb,xy .. text: "wwwwwwwwwwwww'A"
(base) ┌──(holyeyes㉿kali2023)-[~/…/题目/11/chadiand_decrypted/flag]
└─$
根据提示 pass in world 从 world.doc 文件里,ctrl+A 全选,右击—字体—取消勾选隐藏。发现了隐藏字符,
除了这个就差一点点了
Zdfaw1234
3daeghalz
2aeaqrqfa
Weasa65fa
Ezafasfasf3
Sadera85fa
Daaszffasfz
Asdfafsfaff
Sad54656a8
脑筋急转弯,谁会想到最后的密码是 pass内容+world里每行字符串的最后一个字符,
就是密码 :z^ea4zaa3azf8
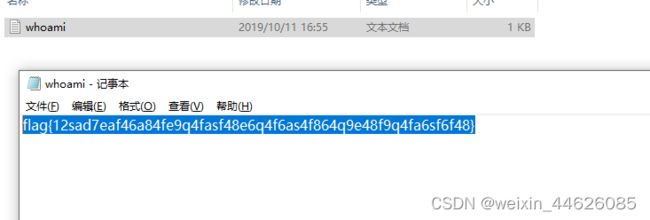
用这个密码解压whoami.zip
flag{12sad7eaf46a84fe9q4fasf48e6q4f6as4f864q9e48f9q4fa6sf6f48}