SpringSecurity(06)——权限注解
注解使用
Spring Security默认是禁用注解的,要想开启注解,需要加上@EnableMethodSecurity注解
- 使用@Secured需要在配置类中添加注解***@EnableGlobalMethodSecurity(securedEnabled=true)***才能生效
- 使用@PreAuthorize和@PostAuthorize需要在配置类中配置注解***@EnableGlobalMethodSecurity(prePostEnable=true)***才能生效
注解方法
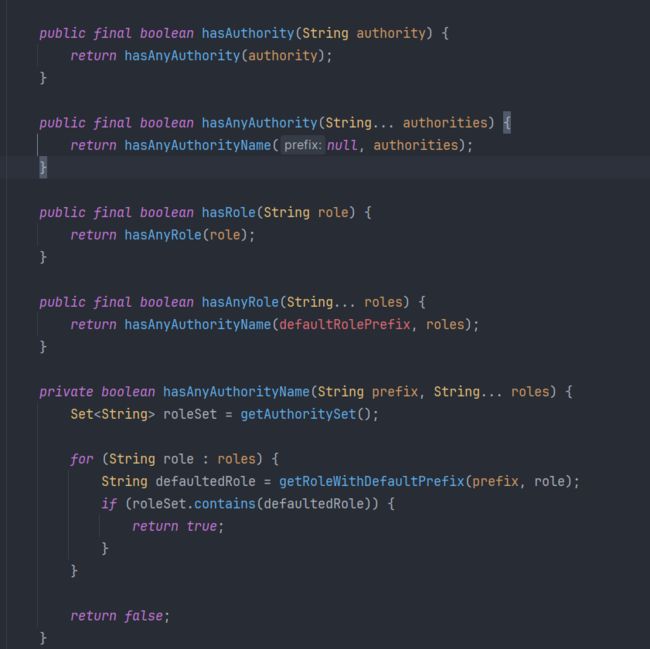
- hasAuthority(String):判断角色是否具有特定权限
http.authorizeRequests().antMatchers(“/main1.html”).hasAuthority(“admin”)
- hasAnyAuthority(String …):如果用户具备给定权限中某一个,就允许访问
http.authorizeRequests().antMatchers(“/admin/read”).hasAnyAuthority(“xxx”,“xxx”)
- hasRole(String):如果用户具备给定角色就允许访问,否则出现403
http.authorizeRequests().antMatchers(“/admin/read”).hasRole(“ROLE_管理员”)
- hasAnyRole(String …):如果用户具备给定角色的任意一个,就允许被访问
http.authorizeRequests().antMatchers(“/guest/read”).hasAnyRole(“ROLE_管理员”, “ROLE_访客”)
- hasIpAddress(String):请求是指定的IP就允许访问
http.authorizeRequests().antMatchers(“/ip”).hasIpAddress(“127.0.0.1”)
- permitAll():允许所有人(可无任何权限)访问
- denyAll():不允许任何(即使有最大权限)访问。
- isAnonymous():为可匿名(不登录)访问。
- isAuthenticated():为身份证认证后访问。
- isRememberMe():为记住我用户操作访问。
- isFullyAuthenticated():为非匿名且非记住我用户允许访问
@Secured
角色校验,请求到来访问控制单元方法时必须包含XX角色才能访问
注意:
- 角色必须添加ROLE_前缀
- 如果要求只有同时拥有admin和user的用户才能访问某个方法时,@Secured就无能为力了
@Component
public class UserDetailServiceImpl implements UserDetailsService {
@Resource
private PasswordEncoder passwordEncoder;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
if (username.equals("root")) {
return new User(username, passwordEncoder.encode("123"), AuthorityUtils.createAuthorityList("ROLE_read"));
} else if (username.equals("user")) {
return new User(username, passwordEncoder.encode("123"), AuthorityUtils.createAuthorityList("ROLE_write"));
}
return new User(username, passwordEncoder.encode("123"), AuthorityUtils.createAuthorityList("read"));
}
}
@RestController
public class HelloController {
@RequestMapping("/read")
@Secured(value = {"ROLE_read"})
public String read() {
return "read";
}
@RequestMapping("/write")
@Secured(value = {"ROLE_write"})
public String write() {
return "write";
}
// 错误实例
@RequestMapping("/read2")
@Secured(value = {"read"})
public String read2() {
return "read2";
}
}
@PreAuthorize
权限校验,请求到来访问控制单元之前必须包含XX权限才能访问,控制单元方法执行前进行角色校验
@RestController
public class HelloController {
@RequestMapping("/read3")
@PreAuthorize(value = "hasRole('ROLE_read')")
public String read3() {
return "read3";
}
@RequestMapping("/read4")
@PreAuthorize(value = "hasAnyRole('ROLE_read','ROLE_write')")
public String read4() {
return "read4";
}
@RequestMapping("/read5")
@PreAuthorize(value = "hasAnyAuthority('ROLE_read','read')")
public String read5() {
return "read5";
}
}
hasRole与hasAuthority的区别
- hasRole的值会添加ROLE_开头进行判断,而hasAuthority不会
- 其他方法判断一致
@PostAuthorize
权限校验,请求到来访问控制单元之后必须包含XX权限才能访问,在方法执行后进行权限校验,适合验证带有返回值的权限
@PostAuthorize("hasRole('ROLE_管理员')")
@RequestMapping("/toMain")
public String toMain(){
return "main";
}
@GetMapping("/helloUser")
@PostAuthorize("returnObject!=null && returnObject.username == authentication.name")
public User helloUser() {
Object pricipal = SecurityContextHolder.getContext().getAuthentication().getPrincipal();
User user;
if("anonymousUser".equals(pricipal)) {
user = null;
}else {
user = (User) pricipal;
}
return user;
}
@PreFilter
对传递参数值做过滤
@PostMapping("/preFilter")
@PreAuthorize("hasAnyAuthority('admin','update')") // 注意单引号
@PreFilter("filterObject.id % 2 == 0") // id为偶数才能请求
public String preFilter(@RequestBody List<User> userLists){
log.info("=== 进入当前 preFilter ====");
log.info(userLists.toString());
return "security test 5 preFilter 需要验证的接口";
}
@PostFilter
权限验证通过后,留下指定用户名的数据,对返回数据做过滤
@RequestMapping("/postFilter")
@PreAuthorize("hasAnyAuthority('admin','update')") // 注意单引号
@PostFilter("filterObject.username == 'xiangjiao'") // 针对返回数据做过滤
public List<User> postFilter(){
log.info("=== 进入当前 postFilter ====");
List<User> userLists = new ArrayList<>();
userLists.add(new User(1,"xiangjiao","bunana",1,0));
userLists.add(new User(2,"xiangjiao2","bunana2",1,0));
return userLists;
}
JSR-250注解
注意:使用JSR-250注解需要设置***@EnableGlobalMethodSecurity(jsr250Enabled=true)***才能使用
- @DenyAll
- @PermitAll
- @RolesAllowed
例如:@RolesAllowed({“USER”, “ADMIN”}),代表标注的方法只要具有USER、ADMIN任意一种权限就可以访问
自定义权限校验
interface TestPermissionEvaluator {
boolean check(Authentication authentication);
}
@Service("testPermissionEvaluator")
public class TestPermissionEvaluatorImpl implements TestPermissionEvaluator {
public boolean check(Authentication authentication) {
System.out.println("进入了自定义的匹配器" + authentication);
return false;
}
}
@PreAuthorize("@testPermissionEvaluator.check(authentication)")
public String test0() {
return "说明你有自定义权限";
}
权限异常处理
- AuthenticationEntryPoint:用来解决匿名用户访问无权限资源时的异常
注意:使用AuthenticationEntryPoint会导致原来的/login登录页面失效
- AccessDeniedHandler:用来解决认证过的用户访问无权限资源时的异常
public class CustomAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request, HttpServletResponse response,
AuthenticationException authException) throws IOException, ServletException {
response.setCharacterEncoding("utf-8");
response.setContentType("text/javascript;charset=utf-8");
response.getWriter().print(JSONObject.toJSONString(RestMsg.error("没有访问权限!")));
}
}
@Component
public class MyAccessDeniedHandler implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest request, HttpServletResponse response, AccessDeniedException e)
throws IOException, ServletException {
response.setStatus(HttpServletResponse.SC_OK);
response.setContentType("text/html;charset=UTF-8");
response.getWriter().write(
"" +
"" +
"" +
"权限不足,请联系管理员" +
"" +
"" +
""
);
response.getWriter().flush();//刷新缓冲区
}
}
@Configuration
@EnableGlobalMethodSecurity(prePostEnabled=true)
public class MyWebSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserDetailsService userDetailsService;
@Autowired
private BCryptPasswordEncoder bCryptPasswordEncoder;
@Override
protected void configure(HttpSecurity http) throws Exception {
http.cors()
.and()
.csrf().disable()
.authorizeRequests()
.antMatchers("/user/sign").permitAll()
.anyRequest()
.authenticated();
//添加自定义异常入口
http.exceptionHandling()
.authenticationEntryPoint(new CustomAuthenticationEntryPoint())
.accessDeniedHandler(new CustomAccessDeineHandler());
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userDetailsService)
.passwordEncoder(bCryptPasswordEncoder);
}
}