防火墙双机热备之VRRP与静态路由实现双机热备旁挂
一、VRF
VRF(Virtual Routing and Forwarding,虚拟路由转发)技术通过在一台三层转发设备上创建多张路由表实现数据或业务的隔离,常用于MPLS VPN、防火墙等一些需要实现隔离的应用场景。
需求:实现研发和管理网路内部的数据通信,同时隔离两张网络之间的通信,即研发部只能访问研发部服务器,并管理部的服务器。
[AR1]interface g0/0/0
[AR1-GigabitEthernet0/0/0]ip add 3.3.3.254 24
[AR1-GigabitEthernet0/0/0]interface g0/0/1
[AR1-GigabitEthernet0/0/1]ip add 5.5.5.1 24
[AR2]interface g0/0/0
[AR2-GigabitEthernet0/0/0]ip add 4.4.4.254 24
[AR2-GigabitEthernet0/0/0]interface g0/0/1
[AR2-GigabitEthernet0/0/1]ip add 6.6.6.1 24
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ip add 1.1.1.254 24
[AR3-GigabitEthernet0/0/0]interface g0/0/1
[AR3-GigabitEthernet0/0/1]ip add 5.5.5.254 24
[AR3-GigabitEthernet0/0/1]interface g0/0/2
[AR3-GigabitEthernet0/0/2]ip add 6.6.6.254 24
[AR3-GigabitEthernet0/0/2]interface g4/0/0
[AR3-GigabitEthernet4/0/0]ip add 2.2.2.254 24[AR3]ip -instance route_1
[AR3--instance-route_1]ipv4-family
[AR3--instance-route_1-af-ipv4]q
[AR3--instance-route_1]q
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ip binding -instance route_1
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[AR3-GigabitEthernet0/0/0]display this
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip binding -instance route_1
#
return
[AR3-GigabitEthernet0/0/0]ip add 1.1.1.254 24
[AR3-GigabitEthernet0/0/0]interface g0/0/1
[AR3-GigabitEthernet0/0/1]ip binding -instance route_1
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[AR3-GigabitEthernet0/0/1]display this
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip binding -instance route_1
#
return
[AR3-GigabitEthernet0/0/1]ip add 5.5.5.254 24
[AR3-GigabitEthernet0/0/1]display this
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip binding -instance route_1
ip address 5.5.5.254 255.255.255.0
#
return
[AR3-GigabitEthernet0/0/1][AR3]ip -instance route_2
[AR3--instance-route_2]ipv4-family
[AR3--instance-route_2-af-ipv4]q
[AR3--instance-route_2]q
[AR3]interface g0/0/2
[AR3-GigabitEthernet0/0/2]ip binding -instance route_2
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[AR3-GigabitEthernet0/0/2]ip add 6.6.6.254 24
[AR3-GigabitEthernet0/0/2]display this
[V200R003C00]
#
interface GigabitEthernet0/0/2
ip binding -instance route_2
ip address 6.6.6.254 255.255.255.0
#
return
[AR3-GigabitEthernet0/0/2]interface g4/0/0
[AR3-GigabitEthernet4/0/0]ip binding -instance route_2
Info: All IPv4 related configurations on this interface are removed!
Info: All IPv6 related configurations on this interface are removed!
[AR3-GigabitEthernet4/0/0]ip add 2.2.2.254 24
[AR3-GigabitEthernet4/0/0]display this
[V200R003C00]
#
interface GigabitEthernet4/0/0
ip binding -instance route_2
ip address 2.2.2.254 255.255.255.0
#
return注意:若用AR3 ping 部门,需要带上对应的VPN实例!
[AR3]display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 4 Routes : 4
Destination/Mask Proto Pre Cost Flags NextHop Interface
127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0
127.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[AR3]display ip routing-table -instance route_1
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: route_1
Destinations : 7 Routes : 7
Destination/Mask Proto Pre Cost Flags NextHop Interface
1.1.1.0/24 Direct 0 0 D 1.1.1.254 GigabitEthernet
0/0/0
1.1.1.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
1.1.1.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/0
5.5.5.0/24 Direct 0 0 D 5.5.5.254 GigabitEthernet
0/0/1
5.5.5.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
5.5.5.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/1
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[AR3]display ip routing-table -instance route_2
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: route_2
Destinations : 7 Routes : 7
Destination/Mask Proto Pre Cost Flags NextHop Interface
2.2.2.0/24 Direct 0 0 D 2.2.2.254 GigabitEthernet
4/0/0
2.2.2.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
4/0/0
2.2.2.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
4/0/0
6.6.6.0/24 Direct 0 0 D 6.6.6.254 GigabitEthernet
0/0/2
6.6.6.254/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
6.6.6.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet
0/0/2
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
[AR3]查看总路由表以及对应的VPN实例路由表,可看出对应的区别,若想实现需求,还需配置静态路由或者动态路由,只需要在对应的VPN实例运行即可。
[AR3]ip route-static -instance route_1 3.3.3.0 24 5.5.5.1
[AR3]ip route-static -instance route_2 4.4.4.0 24 6.6.6.1
[AR3]display ip routing-table -instance route_1
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: route_1
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost Flags NextHop Interface
3.3.3.0/24 Static 60 0 RD 5.5.5.1 GigabitEthernet
0/0/1
[AR3]display ip routing-table -instance route_2
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: route_2
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost Flags NextHop Interface
4.4.4.0/24 Static 60 0 RD 6.6.6.1 GigabitEthernet
0/0/2
接下来采用动态路由,以VPN实例route_1为例。
[AR3]ospf -instance route_1
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]network 1.1.1.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 5.5.5.0 0.0.0.255
[AR1]ospf
[AR1-ospf-1]area 0
[AR1-ospf-1-area-0.0.0.0]network 5.5.5.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 3.3.3.0 0.0.0.255
[AR3]display ip routing-table -instance route_1
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: route_1
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost Flags NextHop Interface
3.3.3.0/24 OSPF 10 2 D 5.5.5.1 GigabitEthernet
0/0/1
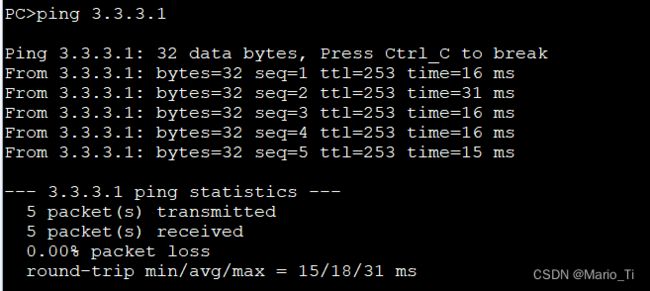
二、VRRP与静态路由实现双机热备旁挂
LW3:
interface Vlanif10
ip binding -instance in_vrf
ip address 5.5.5.2 255.255.255.0
#
interface Vlanif20
ip binding -instance out_vrf
ip address 3.3.3.2 255.255.255.0
#
interface Vlanif30
ip binding -instance in_vrf
ip address 10.0.0.4 255.255.255.0
vrrp vrid 3 virtual-ip 10.0.0.6
vrrp vrid 3 priority 120
vrrp vrid 3 preempt-mode timer delay 10
#
interface Vlanif40
ip binding -instance out_vrf
ip address 10.1.1.4 255.255.255.0
vrrp vrid 4 virtual-ip 10.1.1.6
vrrp vrid 4 priority 120
vrrp vrid 4 preempt-mode timer delay 10
#
return
#
ospf 1 -instance in_vrf
area 0.0.0.0
network 5.5.5.0 0.0.0.255
#
ospf 2 -instance out_vrf
area 0.0.0.0
network 3.3.3.0 0.0.0.255
#
ip route-static -instance in_vrf 0.0.0.0 0.0.0.0 10.0.0.3
ip route-static -instance out_vrf 192.168.1.0 255.255.255.0 10.1.1.3
#
LW4:
interface Vlanif10
ip binding -instance in_vrf
ip address 5.5.5.4 255.255.255.0
#
interface Vlanif20
ip binding -instance out_vrf
ip address 4.4.4.2 255.255.255.0
#
interface Vlanif30
ip binding -instance in_vrf
ip address 10.0.0.5 255.255.255.0
vrrp vrid 3 virtual-ip 10.0.0.6
vrrp vrid 3 preempt-mode timer delay 10
#
interface Vlanif40
ip binding -instance out_vrf
ip address 10.1.1.5 255.255.255.0
vrrp vrid 4 virtual-ip 10.1.1.6
vrrp vrid 4 preempt-mode timer delay 10
#
return
#
ospf 1 -instance in_vrf
area 0.0.0.0
network 5.5.5.0 0.0.0.255
#
ospf 2 -instance out_vrf
area 0.0.0.0
network 4.4.4.0 0.0.0.255
#
ip route-static -instance in_vrf 0.0.0.0 0.0.0.0 10.0.0.3
ip route-static -instance out_vrf 192.168.1.0 255.255.255.0 10.1.1.3
#FW1:
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.1.1 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.1.3 active
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.0.0.1 255.255.255.0
vrrp vrid 1 virtual-ip 10.0.0.3 active
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.10.10.1 255.255.255.0
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0.0.0.0 10.1.1.6
ip route-static 192.168.1.0 255.255.255.0 10.0.0.6
#
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.1.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.1.3 standby
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.0.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 10.0.0.3 standby
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.10.10.2 255.255.255.0
#
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0.0.0.0 10.1.1.6
ip route-static 192.168.1.0 255.255.255.0 10.0.0.6
#
#
security-policy
rule name tr_to_untr
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
action permit
#
参考资料:防火墙和VPN技术与实践——李学昭