IPSec在企业网中的应用 案例(野蛮模式)
IPSec主模式和野蛮模式的区别包含如下几点:
1. 交换的消息:主模式为6个,野蛮模式为3个。
2. NAT支持:对预共享密钥认证:主模式不支持NAT转换,而野蛮模式支持。而对于证书方式认证:两种模式都能支持。
3. 对等体标识:主模式只能采用IP地址方式标识对等体;而野蛮模式可以采用IP地址方式或者Name方式标识对等体。这是由于主模式在交换完3、4消息以后,需要使用预共享密钥来计算SKEYID,当一个设备有多个对等体时,必须查找到该对等体对应的预共享密钥,但是由于其对等体的ID信息在消息5、6中才会发送,此时主模式的设备只能使用消息3、4中的IP报文源地址来找到与其对应的预共享密钥;如果主模式采用Name方式,Name信息却包含在消息5、6中,而设备必须在消息5、6之前找到其对等体的预共享密钥,所以就造成了矛盾,无法完成Name方式的标识。
而在野蛮模式中,ID消息在消息1、2中就已经发送了,设备可以根据ID信息查找到对应的预共享密钥,从而计算SKEYID。但是由于野蛮模式交换的3个消息没有经过加密,所以ID信息也是明文的,也相应造成了安全隐患。
4. 提议转换对数量:在野蛮模式中,由于第一个消息就需要交换DH消息,而DH消息本身就决定了采用哪个DH组,这样在提议转换对中就确定了使用哪个DH组,如果第一个消息中包含多个提议转换对,那么这多个转换对的DH组必须相同(和DH消息确定的DH组一致),否则消息1中只能携带和确定DH组相同的提议转换对。
5. 协商能力:由于野蛮模式交换次数的限制,因此野蛮模式协商能力低于主模式。
案例:
设备:三台防火墙,一台交换机
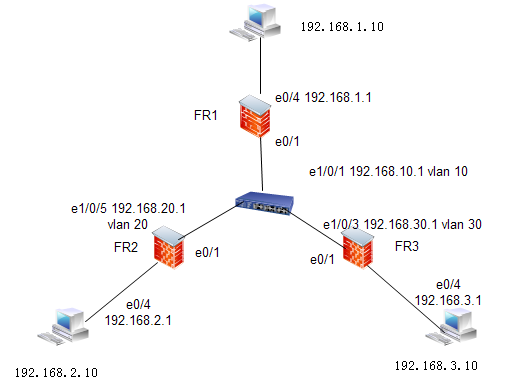
配置:
FR1 :
firewall zone trust
add interface Ethernet 0/4
quit
firewall zone untrust
add interface Ethernet 0/1
int e0/4
ip add 192.168.1.1 24
int e0/1
ip add 192.168.10.200 24
quit
ip route-static 0.0.0.0 0.0.0.0 192.168.10.1
acl number 3000
rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule deny ip source any destination any
quit
acl number 3001
rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule deny ip source any destination any
quit
ipsec proposal tran1
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm md5
quit
ipsec proposal tran2
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm md5
quit
ike local-name FR1
ike peer peer1
exchange-mode aggressive
pre-shard-key simple 1234
local-address 192.168.10.200
id-type name
remote-name FR2
quit
ike peer peer2
exchange-mode aggressive
pre-shard-key simple abcd
local-address 192.168.10.200
id-type name
remote-name FR3
quit
ipsec poli policy 10 isakmp
proposal tran1
security acl 3000
ike-peer peer1
quit
ipsec poli policy 20 isakmp
proposal tran2
security acl 3001
ike-peer peer1
quit
int e0/1
ipsec policy policy
FR2的配置:
firewall zone trust
add interface Ethernet 0/4
quit
firewall zone untrust
add interface Ethernet 0/1
quit
int e0/4
ip add 192.168.2.1 24
int e0/1
ip address dhcp-alloc
quit
ip route-static 0.0.0.0 0.0.0.0 192.168.20.1
acl number 3000
rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule deny ip source any destination any
quit
ipsec proposal tran1
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm md5
quit
ike local-name FR2
ike peer peer1
exchange-mode aggressive
pre-shard-key simple 1234
id-type name
remote-name FR1
remote-address 192.168.10.200
quit
ipsec poli policy 10 isakmp
proposal tran1
security acl 3000
ike-peer peer1
quit
int e0/1
ipsec policy policy
FR3 的配置:
配置ip和默认路由:
firewall zone trust
add interface Ethernet 0/4
firewall zone untrust
add interface Ethernet 0/1
int e0/4
ip add 192.168.3.1 24
int e0/1
ip address dhcp-alloc
ip route-static 0.0.0.0 0.0.0.0 192.168.30.1
acl number 3000
rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule deny ip source any destination any
ipsec proposal tran2
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm md5
ike local-name FR3
ike peer peer2
exchange-mode aggressive
pre-shard-key simple abcd
id-type name
remote-address 192.168.10.200
remote-name FR1
ipsec poli policy 20 isakmp
proposal tran2
security acl 3001
ike-peer peer2
int e0/1
ipsec policy policy
witch配置:
vlan 10
port e1/0/1
vlan 20
port e1/0/5
vlan 30
port e1/0/3
interface vlan-interface 10
ip add 192.168.10.1 255.255.255.0
interface vlan-interface 20
ip add 192.168.20.1 255.255.255.0
interface vlan-interface 30
ip add 192.168.30.1 255.255.255.0
dhcp server ip-pool FR2
network 192.168.20.0 mask 255.255.255.0
quit
dhcp server ip-pool FR3
network 192.168.30.0 mask 255.255.255.0
quit
dhcp server enable
1.0网段ping 2.0网段
C:\Documents and Settings\Administrator>ping 192.168.2.1
Pinging 192.168.2.1 with 32 bytes of data:
Reply from 192.168.2.1: bytes=32 time=14ms TTL=254
Reply from 192.168.2.1: bytes=32 time=14ms TTL=254
Reply from 192.168.2.1: bytes=32 time=13ms TTL=254
Reply from 192.168.2.1: bytes=32 time=12ms TTL=254
Ping statistics for 192.168.2.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
C:\Documents and Settings\Administrator>ping 192.168.2.10
Pinging 192.168.2.10 with 32 bytes of data:
Reply from 192.168.2.10: bytes=32 time=15ms TTL=64
Reply from 192.168.2.10: bytes=32 time=14ms TTL=64
Reply from 192.168.2.10: bytes=32 time=12ms TTL=64
Reply from 192.168.2.10: bytes=32 time=11ms TTL=64
Ping statistics for 192.168.2.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
1.0网段ping 3.0网段
C:\Documents and Settings\Administrator>ping 192.168.3.1
Pinging 192.168.3.1 with 32 bytes of data:
Reply from 192.168.3.1: bytes=32 time=17ms TTL=254
Reply from 192.168.3.1: bytes=32 time=17ms TTL=254
Reply from 192.168.3.1: bytes=32 time=14ms TTL=254
Reply from 192.168.3.1: bytes=32 time=12ms TTL=254
Ping statistics for 192.168.3.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
C:\Documents and Settings\Administrator>ping 192.168.3.10
Pinging 192.168.3.10 with 32 bytes of data:
Reply from 192.168.3.10: bytes=32 time=12ms TTL=126
Reply from 192.168.3.10: bytes=32 time=14ms TTL=126
Reply from 192.168.3.10: bytes=32 time=16ms TTL=126
Reply from 192.168.3.10: bytes=32 time=16ms TTL=126
Ping statistics for 192.168.3.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms