How I Cracked your Windows Password (Part 1)
How Windows creates and stores passwordhashes and how those hashes are cracked.
If youwould like to read the next part in this article series please go toHowI Cracked your Windows Password (Part 2).
Introduction
Passwords tend to be our main and sometimes only line ofdefense against intruders. Even if attackers do not have physical access to amachine they can often access a server through the remote desktop protocol orauthenticate to a service via an outward facing web application.
The purpose of this article is to educate you on how Windows creates and stores password hashes, and how those hashes are cracked.After demonstrating how to crack Windows passwords I will provide some tips forensuring you are not vulnerable to these types of attacks.
How Windows Stores Passwords
Windows-based computers utilize two methods for the hashingof user passwords, both having drastically different security implications.These are LAN Manager (LM) and NT LAN Manager version 2 (NTLMv2). A hash is theresult of a cryptographic function that takes an arbitrarily sized string ofdata, performs a mathematical encryption function on it, and returns afixed-size string.
LM Password Hashes
The LAN Manager hash was one of the first password hashingalgorithms to be used by Windows operating systems, and the only version to besupported up until the advent of NTLMv2 used in Windows 2000, XP, Vista, and 7.These newer operating systems still support the use of LM hashes for backwardscompatibility purposes. However, it is disabled by default for Windows Vistaand Windows 7.
The LM hash of a password is computed using a six stepprocess:
- The user’s password is converted into all uppercase letters
- The password has null characters added to it until it equals 14 characters
- The new password is split into two 7 character halves
- These values are used to create two DES encryption keys, one from each half with a parity bit added to each to create 64 bit keys.
- Each DES key is used to encrypt a preset ASCII string (KGS!@#$%), resulting in two 8-byte ciphertext values
- The two 8-byte ciphertext values are combined to form a 16-byte value, which is the completed LM hash
In practice, the password “PassWord123” would be convertedas follows:
- PASSWORD123
- PASSWORD123000
- PASSWOR and D123000
- PASSWOR1 and D1230001
- E52CAC67419A9A22 and 664345140A852F61
- E52CAC67419A9A22664345140A852F61
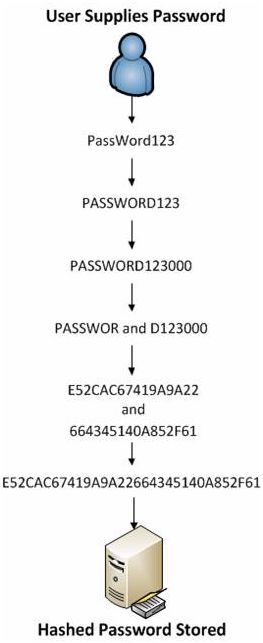
Figure 1: A password transformed into an LM hash
LM stored passwords have a few distinct disadvantages. Thefirst of these is that the encryption is based on the Data Encyrption Standard(DES). DES originated from a 1970s IBM project that was eventually modified byNIST, sponsored by the NSA, and released as an ANSI standard in 1981. DES wasconsidered secure for many years but came under scrutiny in the nineties due toits small key size of only 56-bits. This came to a head in 1998 when theElectronic Frontier Foundation was able to crack DES in about 23 hours. Sincethis, DES has been considered insecure and has since been replaced withTriple-DES and AES. In short, it’s another encryption standard that has fallenvictim to modern computing power and can be cracked in no time at all.
Perhaps the biggest weakness in the LM hash is in thecreation of the DES keys. In this process, a user supplied password isautomatically converted to all uppercase, padded to fourteen characters (thisis the max length for an LM hashed password), and split into two sevencharacter halves. Consider that there are 95 to the power of 14differentpossible passwords made up of 14 printable ASCII characters, this decreases to95 to the power of 7possible passwords when split into a 7 character half, andthen decreases to 69 to the power of 7 possible passwords when you are onlyallowed uppercase ASCII characters. Essentially, this makes the use of varyingcharacter cases and increased password length nearly useless when the passwordis stored as an LM hash, which makes LM passwords incredibly vulnerable tobrute force cracking attempts.
NTLMv2 Password Hashes
NT LAN Manager (NTLM) is the Microsoft authenticationprotocol that was created to be the successor of LM. Eventually enhanced,NTLMv2 was accepted as the new authentication method of choice and implementedwith Windows NT 4.
The creation of an NTLMv2 hash (henceforth referred to asthe NT hash) is actually a much simpler process in terms of what the operatingsystem actually does, and relies on the MD4 hashing algorithm to create thehash based upon a series of mathematical calculations. The MD4 algorithm isused three times in order to produce the NT hash. In practice, the password“PassWord123” would be represented as an MD4 hash with “94354877D5B87105D7FEC0F3BF500B33”.
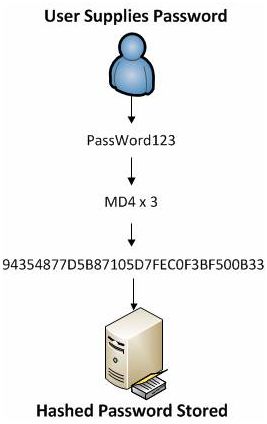
Figure 2: A password being transformed into an NTLMv2 hash
MD4 is considered to be significantly stronger than DES asit allows for longer password lengths, it allows for distinction betweenuppercase and lowercase letters and it does not split the password intosmaller, easier to crack chunks.
Perhaps the biggest complaint with NTLMv2 created hashes isthat Windows does not utilize a technique called salting. Salting is atechnique in which a random number is generated in order to compute the hashfor the password. This means that the same password could have two completelydifferent hash values, which would be ideal.
With this being the case, it is possible for a user togenerate what are called rainbow tables. Rainbow tables are not just coffeetables painted with bright colors; they are actually tables containing everysingle hash value for every possible password possibility up to a certainnumber of characters. Using a rainbow table, you can simply take the hash valueyou have extracted from the target computer and search for it. Once it is foundin the table, you will have the password. As you can imagine, a rainbow tablefor even a small number of characters can grow to be very large, meaning thattheir generation, storage, and indexing can be quite a task.
Conclusion
In the first part of this article we have examined passwordhashes and the mechanisms Windows utilizes to create and store these values.We’ve also touched upon the weaknesses of each method and possible avenues thatcan be used to crack those passwords. In the follow-up to this article we willactually step through the process of extracting and cracking these hashes todemonstrate their weaknesses. Once demonstrated I will provide tips forproviding additional layers of security and creating a properly strengthenedpassword.
If youwould like to read the next part in this article series please go toHowI Cracked your Windows Password (Part 2).