某下载者的下载接管
样本来自卡饭论坛,本文主要展示如何对下载者的下载接管,注重网络通信部分,其他感染传播隐藏之类的功能暂且不涉及,代码分析部分暂不贴了。
一、样本基本信息
1)文件名称: yf.exe
2)MD5:9648c7cc2f01d7b67718cb89a48d927e
3)文件类型:EXE
4)壳或编译器信息:PACKER:UPX V2.00-V3.00 -> Markus Oberhumer & Laszlo Molnar & John Reiser [Overlay] *
5)子文件信息: upx30_b0a55865 / 8a92e75e5440e9bcf4ff98f85ff99248 / EXE
6)网络通信部分
请求主机:c.shidaihuabian.com
通信协议:http
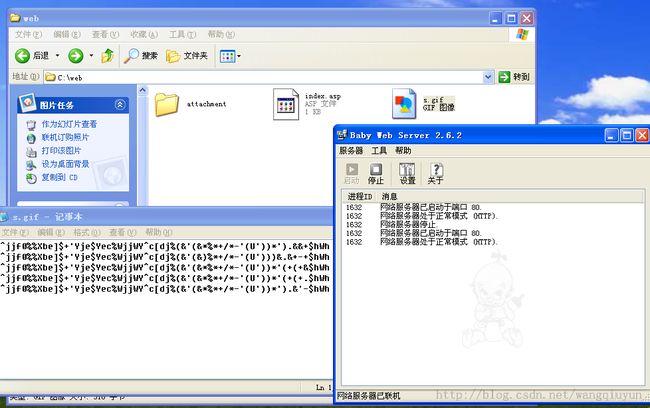
下载运行:s.gif
二、接管原理及过程
1)接管原理:通过hosts劫持修改样本主机的域名c.shidaihuabian.com转向,在目标主机web服务器提供http://c.shidaihuabian.com/s.gif,其中s.gif为加密下载列表如下:
^jjf0%%Xbe]$+'Yje$Yec%WjjWY^c[dj%(&'(&*%*+/*-'(U'))*').&&+$hWh ^jjf0%%Xbe]$+'Yje$Yec%WjjWY^c[dj%(&'(&)%*+/*-'(U')))&.&+-+$hWh ^jjf0%%Xbe]$+'Yje$Yec%WjjWY^c[dj%(&'(&*%*+/*-'(U'))*'(+(+&$hWh ^jjf0%%Xbe]$+'Yje$Yec%WjjWY^c[dj%(&'(&*%*+/*-'(U'))*'(+(+.$hWh ^jjf0%%Xbe]$+'Yje$Yec%WjjWY^c[dj%(&'(&*%*+/*-'(U'))*').&'-$hWh
样本下载解密后,获取接管程序下载地址:
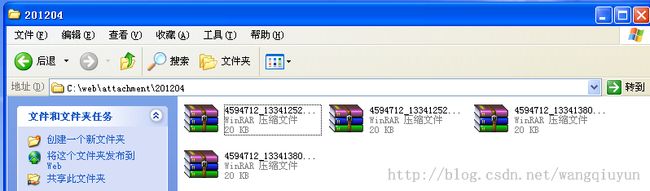
blog.51cto.com/attachment/201204/4594712_1334138005.rar blog.51cto.com/attachment/201203/4594712_1333080575.rar blog.51cto.com/attachment/201204/4594712_1334125250.rar blog.51cto.com/attachment/201204/4594712_1334125258.rar blog.51cto.com/attachment/201204/4594712_1334138017.rar
其中"http://c.shidaihuabian.com/s.gif" >> "%windir%\temp\olm.ini",压缩包下载至:
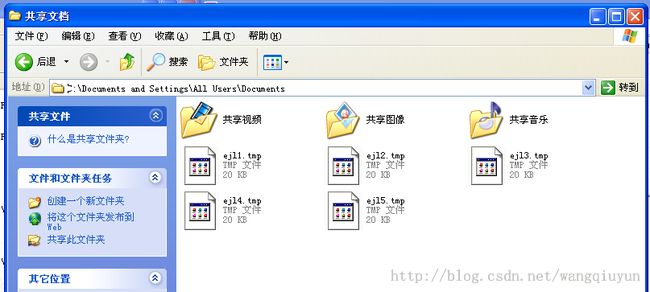
C:\Documents and Settings\All Users\Documents\ejl1.tmp C:\Documents and Settings\All Users\Documents\ejl2.tmp C:\Documents and Settings\All Users\Documents\ejl3.tmp C:\Documents and Settings\All Users\Documents\ejl4.tmp C:\Documents and Settings\All Users\Documents\ejl5.tmp
2)接管流程
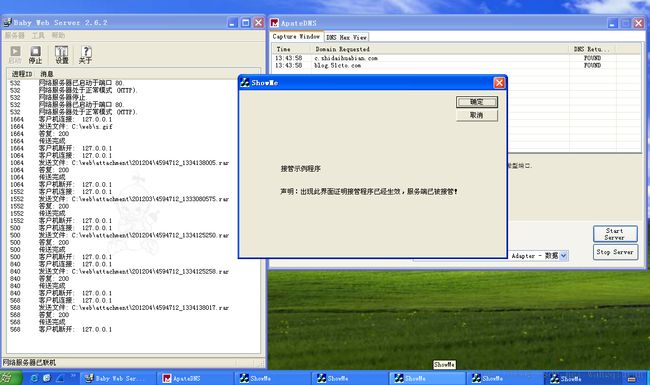
1、启动样本运行虚拟机,运行apateDNS,域名重定向至本地127.0.0.1
2、本地架设一个web服务器,提供s.gif,实际为加密下载列表,对应url:http://c.shidaihuabian.com/s.gif
3、提供接管程序伪装为blog.51cto.com/attachment/201204/4594712_133413 8005.rar之类的压缩包
4、运行样本
5、样本下载http://c.shidaihuabian.com/s.gif解密下载列表后,下载接管程序
6、下载列表http://c.shidaihuabian.com/s.gif下载至%windir%\temp\olm.ini,解析完后被删除,接管程序下载至
C:\Documents and Settings\All Users\Documents\ejl1.tmp C:\Documents and Settings\All Users\Documents\ejl2.tmp C:\Documents and Settings\All Users\Documents\ejl3.tmp C:\Documents and Settings\All Users\Documents\ejl4.tmp C:\Documents and Settings\All Users\Documents\ejl5.tmp
转载请注明:http://blog.csdn.net/wangqiuyun/article/details/38292957