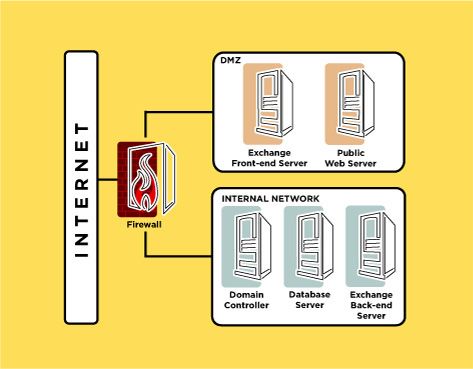
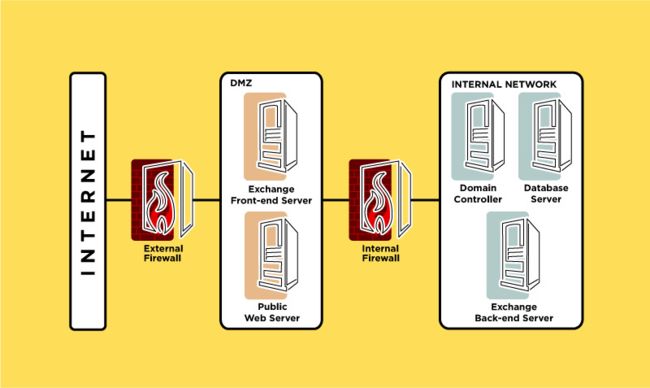
- 2023-10-22
奥雷里亚诺第n
昨天在B站看到关于猫喜欢挠人的视频,视频教导说猫挠人的话就抓住它的后脖颈然后用手打打挠人的那个爪子。视频本身没什么,但评论区却炸开了锅(真是符合挑食者厌食心理)。令我印象最深刻的一个甚至上升到了关于我是谁这种终极问题。它说,猫就是畜生,它挠人就打它别惯着它,反正我六道轮回成了人就应该保持人的高贵,谁都别想来打破。我顿时汗颜,但看到下面全是类似的言论只不过后面的理由各有不同,本来想骂人的心都凉了一半
- 【Git】常见命令(仅笔记)
好想有猫猫
GitLinux学习笔记git笔记elasticsearchlinuxc++
文章目录创建/初始化本地仓库添加本地仓库配置项提交文件查看仓库状态回退仓库查看日志分支删除文件暂存工作区代码远程仓库使用`.gitigore`文件让git不追踪一些文件标签创建/初始化本地仓库gitinit添加本地仓库配置项gitconfig-l#以列表形式显示配置项gitconfiguser.name"ljh"#配置user.namegitconfiguser.email"
[email protected]
- 简单了解 JVM
记得开心一点啊
jvm
目录♫什么是JVM♫JVM的运行流程♫JVM运行时数据区♪虚拟机栈♪本地方法栈♪堆♪程序计数器♪方法区/元数据区♫类加载的过程♫双亲委派模型♫垃圾回收机制♫什么是JVMJVM是JavaVirtualMachine的简称,意为Java虚拟机。虚拟机是指通过软件模拟的具有完整硬件功能的、运行在一个完全隔离的环境中的完整计算机系统(如:JVM、VMwave、VirtualBox)。JVM和其他两个虚拟机
- 178 坚守自律
花儿迎风飞扬
如果错过了太阳时你流了泪,那么你也要错过群星了。如果你错过了早上而懊悔,那么你也要错过一整天了。白俊庭老师说,如果没有外部环境的咄咄逼人和自己逼自己,我们一般都不会自己走出舒适区,就像那只温水里的青蛙。百炼成钢,就是要锻造,就是锤打,给自己压力才有动力。咄咄逼人的外部环境是他律,是外力,走出舒适区是觉醒,是顿悟;而自己逼自己,是自律,是意志,是恒心,是内驱力。女儿的中学生活开始,开学整整一个月,也
- 骑昆明到北海—119 砚山县
61清风i
从十年前第一次长途骑行青海湖开始每年一次长途骑行看风景,尝各地美食,探访异域文化,记录途中美食美景美事,已逐渐形成习惯。每年春季详细规划好线路,夏季出行,2020年因为疫情迟迟不能确定线路和行程。总算到了暑期疫情逐渐消失,规划了50多天的云南昆明—广西北海计划。本次行程从云南昆明出发到广西北海市结束,五十一天骑行二千多公里线路昆明-官渡古镇-环滇池--澄江市一抚仙湖—路居镇--江川区--通海县—龙
- 常见的 JVM 调优方法有哪些?
爪哇天下
jvm
常见的JVM调优方法有哪些?可以具体到调整哪个参数,调成什么值?对年轻代的EdenSurvivor的比例进行配置-XX:SurvivorRatio=8:表示设置2个Survivor区:1个Eden区的大小比值为2:8,这意味着Survivor区占整个年轻代的1/5,这个参数默认为8如果经常性的SurvivorTo放不下YGC的剩余的对象时候,可以适当的调整比例常用的CMS收集器:设置回收阈值,需要
- 康定城,一颗镶嵌在康巴藏区上的明珠,一曲《康定情歌》传唱至今
蚕子桑叶
蚕子在桑叶上行走,小编在地球上旅游,嗨,大家好,我们又见面了!今天继续向大家分享我的“川西自驾游日记”。康定是甘孜州州府所在地。康定历史悠久,是川藏咽喉,茶马古道重镇,藏汉交汇中心。自古以来就是康巴藏区政治、经济、文化、商贸、信息中心和交通枢纽。康定系汉语名,因丹达山以东为“康”,取康地安定之意,故名。藏语称康定为“打折多”,意为打曲(雅拉河)、折曲(折多河)两河交汇处。这里海拔低了不少(2560
- 史上最全git命令,git回滚,git命令大全
騒周
其他git
git命令大全一、Git整体理解二、由暂存区本地仓库三、由本地仓->远程仓库四、冲突处理五、Git分支操作六、bug的分支七、feature分支八、暂存的使用九、远程仓的操作十、标签的使用十一、Git配置全局信息十二、Linux的一些简单操作和一些符号的解释十三、符号解释十四、显示安装详细信息十五、gitconfig十六、Gitclone十七、Gitinit十八、gitstatus十九、gitre
- 2022-07-06
榜一大哥啊
非洲猪瘟检测流程要点1、进入实验室按照要求穿好装备进入实验室,病原稀释及制备,将实验用假阳性按照倍数稀释,最高稀释到一万倍。所有操作流程都在生物安全柜进行,按照流程进行编号,编写检测编号。在每个实验室都要将白大褂以及手套进行更换。2、到试剂准备区进行试剂准备,按照样品数量加阴阳对照进行配备,该项目在超净工作台进行。将制备好的试剂放入传递窗,进入核酸提取环节。3、核酸提取区,进行核酸提纯,用磁吸法核
- 【JS】前端文件读取FileReader操作总结
程序员-张师傅
前端前端javascript开发语言
前端文件读取FileReader操作总结FileReader是JavaScript中的一个WebAPI,它允许web应用程序异步读取用户计算机上的文件(或原始数据缓冲区)的内容,例如读取文件以获取其内容,并在不将文件发送到服务器的情况下在客户端使用它。这对于处理图片、文本文件等非常有用,尤其是当你想要在用户界面中即时显示文件内容或进行文件预览时。创建FileReader对象首先,你需要创建一个Fi
- 公道中学举行校园安全目标责任书签订仪式
公中盛传云
图片发自App为认真做好学校校园安全管理工作,切实将安全抓实抓细,真正落实到位,责任到人,形成齐抓共管的局面。公道中学在毓贤楼多功能教室举行了2018-2019学年校园安全目标责任书签订仪式。公道中学全体教职工近150人参加签订仪式。图片发自App会议开始,公道中学校长助理盛传云传达了《扬州市邗江区教育系统社会治安综合治理暨平安校园建设责任书》的精神及近期有关上级教育主管部门下发有关食品安全、交通
- 保证RTOS线程安全的常规操作
WittXie
单片机嵌入式硬件
线程安全定义原子操作:一种不可分割的操作,要么完全执行成功,要么完全不执行,不能被打断临界区:一段代码,这段代码需要在同一时间只允许一个线程执行互斥锁:一种用于保护共享资源的机制,确保同一时间只有一个线程可以访问特定资源应用裸机原子操作/临界区可以通过暂时关闭中断响应实现一般用不到互斥锁RTOS原子操作:暂时关闭中断响应+挂起所有应用(不建议,RTOS尽量不要开启中断,改为线程监听)临界区:挂起所
- 游藏马山 邸坤宁
圆祥妈咪
大年初四,我们走完了姥姥家,爸爸说带我们去藏马山旅游度假区赶庙会。藏马山度假区在胶南,开车一个半小时就到了。我们下车排队去买票,天啊,售票处真是人山人海,今天来旅游的人可真不少呢!我们要坐观光车进去。在观光车上,我们看到了一座座别墅,很快,我们就到了景点。说起赶庙会,一共有两个景点可以参观,左右两边都可以参观游玩,我们先进了右边的景点。首先,一进去,一条小吃街映入我们的眼帘,里面有许多美食吸引着我
- 如何区分Python中数据类型可变还是不可变
秸秆混凝烧结工程师
关键字改变元素值,内存地址发生改变,被称为数据内型不可变如string,元组,存储数据类型单一,不能同时存在两个数据类型,新增元素后,表容量,元素个数,元素存储区ID改变,典型的内置元素一体存储法;改变元素值,但是内存地址不改变就是可变数据内型,如list,存储元素可以不同,删除,新增,插入,表序列不改变,扩展表容量时,对象地址ID不变,属于顺序表的,分离式存储结构,外置元素法,python中不可
- 【C#Mutex】 initiallyOwned错误引起的缺陷
闻缺陷则喜何志丹
c#互斥量进程同步WaitOneinitiallyOwned临界区
临界区只能对同一个进程的不同线程同步,互斥量可以跨进程同步。典型应用场景:两个exe会操作同一个注册表项。错误代码封装类publicclassCMutexHelp:IDisposable{publicCMutexHelp(){s_mutex.WaitOne();}privatestaticMutexs_mutex=newMutex(true,"Time202409091406ab");public
- 广州复刻包包市场(盘点十个广州复刻包包批发渠道)
美鞋之家
广州作为中国最大的商品交易基地,众多的货源市场使其深受商家们的喜欢。其中复刻包包市场更是闻名全国,以下就为你盘点十个广州复刻包包批发渠道。微信:1179517285(下单赠送精美礼品)1.白马包包批发市场白马包包批发市场是广州最有名的复刻包批发市场之一,这里的包包种类繁多,设计独特,适合各类人群购买使用。2.海珠区新华洲包城新华洲包城主要经营女士配饰、鞋包等商品,这里的复刻包包既有精仿的高端品牌,
- git:文件存储方式
xuanyu22
工具gitgithub
引言我们知道git跟踪文件会经历三个阶段:工作区,暂存区和本地仓库(参考git:理解工作区,暂存区和本地仓库),在这些阶段文件如何被储存?理解git文件的存储方式能帮助我们掌握git的工作原理。git对象在上述三个阶段,文件会以对象(object)的形式存储在.git/objects目录下,对象主要有三类:commit,tree和blob。假设初始目录如下:├──.git├──file│└──c.
- 茶界“董明珠”,黄红缨,她跑了12万公里嫁给了一片山
黄红缨茶庄
黄红缨,一个专注农业21年、爱喝茶的女人,深知中国“三农”的痛点,对茶产业土地极度污染、农药化肥滥用、价格混乱、品质低劣等问题深恶痛绝。图片发自App驱车12万余公里走遍全国各大茶区,终于在茶叶生长黄金经纬线上下找到了一片平均海拔1350米的净土,她义无反顾地娶了那片山、嫁给了这片茶,一头扎在云雾高山之间用6年时间开辟了12000多亩茶山,她带着团队钻进灌木林拓荒平整梯田,不远千里从内蒙原生牧场拖
- 《心毒》‖邪恶的人性好似一剂毒药
那花评书
《心毒》是一部刑侦小说,作者初禾也是一位高人气原创作者,在她细腻的笔触之下,不论是小说情节还是人物都显得紧凑而饱满。本书分为两起案件,一起名为“红颜”,一起名为“知己”。第一案红颜中讲到,在某个城市边缘的穷人区发现一位女性受害者,她离奇又蹊跷的受害场景,让当时的办案人员都唏嘘不已,紧接着引出了本书的男主角花崇和柳至秦这对“柳暗花明”组合。看过刑侦小说的朋友都知道,接下来的情节就是侦破案件的过程,同
- 半马之前
南九条7号
最近状态调整的不错,跑起来充满力量。今天慢跑1小时,差点儿没压住,让心率超过1区。业余选手训练时间真的是最大的敌人,原本计划晚上的饭局,不用我去了,高兴之余,今天的课表完全打乱了。让我重新计划明天早上半马的训练。上一次半马的时候,只跑了6公里就放弃了,然后和教练墨迹了半天。但是从那以后,茅塞顿开,训练质量开始有了保障。明天又是半马,我计划早上4点半起床,热身、跑步、冷身。跑前最后测试有氧能力的机会
- 破解你的负面想法——PR025《工具》
逆旅沙鸥
在日常生活中我们有时会被一些负面情绪所困扰,在《工具》这本书里,菲尔·施图茨和巴里·米歇尔斯两位作者把这些问题当做我们开发内在力量的机会,运用心理学技巧使用五种工具帮助我们破解负面想法。这里给大家分享其中两种:一、消除逃避的工具:逆转渴望每个人都有自己的舒适区,舒适区外面是成长区,对有些人来说,离开舒适区前往成长区是意味着痛苦的,因为害怕痛苦,回避痛苦,所以一直躲在舒适区里面,久而久之就失去了成长
- MySQL内存结构
san.hang
数据库数据结构与算法
实际上MySQL内存的组成和Oracle类似,也可以分为SGA(系统全局区)和PGA(程序缓存区)。mysql>showvariableslike"%buffer%";一、SGA1.innodb_buffer_bool用来缓存Innodb表的数据、索引、插入缓冲、数据字典等信息。2.innodb_log_buffer事务在内存中的缓冲,即redlogbuffer的大小3.querycache高速查
- 星舰历险
GhostLauren
2098年的秋天,北欧地区遭遇大面积不明物体袭击,所在地区已完全沦陷,大灾难应急中心正在积极调查此事,派我们这些飞行员前去支持。我们718西部编队被派遣做先锋队。有一架ZC6-562中型运输机和20架ATX-6战略攻击机,共计62人,以冲锋阵型飞往沦陷区。到达沦陷区边境时。几个黑色物体朝我们飞来。队长大喊“全体戒备,保持阵型!”突然,敌人的一颗脉冲弹击中了我们的一架ATX-69。“开火!”我操纵着
- 撤消操作
guanjianhe
有时候我们提交完了才发现漏掉了几个文件没有添加,或者提交信息写错了。此时,可以运行带有--amend选项的提交命令尝试重新提交:$gitcommit--amend这个命令会将暂存区中的文件提交。如果自上次提交以来你还未做任何修改(例如,在上次提交后马上执行了此命令),那么快照会保持不变,而你所修改的只是提交信息。文本编辑器启动后,可以看到之前的提交信息。编辑后保存会覆盖原来的提交信息。例如,你提交
- 游“杜陵”
海阔魚翔
杜陵杜陵位于西安市三兆村南,陵区南北长约4公里,东西宽约3公里。是西汉后期宣帝刘询的陵墓。陵墓所在地原来是一片高地,潏、浐两河流经此地,汉代旧名"鸿固原"。宣帝少时好游于原上,他即帝位后,遂在此选择陵地,建造陵园。杜陵遗址是许多人熟悉又陌生的地方。我虽在西安居多年,但一直没能前往,今天有兴同北京来的一位文化学者,李老师一起前往去了解一下它的前世今生和发展规划。这里是全国文物重点保护单位,全国100
- 【YashanDB知识库】数据库获取时间和服务器时间不一致
YashanDB
YashanDB知识库数据库运维崖山数据库YashanDByashandb知识库
本文转自YashanDB官网,具体内容可见数据库获取时间和服务器时间不一致【问题分类】功能使用【关键字】服务器时间、数据库时间【问题描述】数据库获取的时间和服务器时间不一致。【问题原因分析】YashanDB并没有时区的概念,数据库的时间以数据库启动时的系统时间为准。出现这个情况有可能是数据库部署时服务器时间为0时区,因此数据库以0时区拉起,后来系统修改为东八区,但是数据库仍然为0时区,导致数据库获
- 释放“AI+”新质生产力,深算院如何“把大数据变小”?
YashanDB
YashanDB国产数据库数据库数据库大数据
近期,南都·湾财社推出《新质·中国造》栏目,深入千行百业,遍访湾区企业,解锁湾区新质生产力,共探高质量发展之道。本期对话深圳计算科学研究院YashanDB首席技术官陈志标,探讨国产数据库如何实现创新突围,抢抓数字经济时代的新机遇。以下是专访内容:如何应对AI时代所面临的算力挑战?南都·湾财社:数据、算力和算法是发展人工智能的三要素,深算院做了怎样的前瞻性布局?陈志标:今年,政府工作报告中首次提及开
- 2018-08-31
松岗微生活
一场上了热搜的雨是怎样的雨?▼▲“哎呀,这雨简直不是下雨,是砸雨啊!”28日23时至29日21时宝安全区录得平均雨量为133.3毫米最大累计雨量196.5毫米全区各级各部门迅速落实市、区部署加强巡查防范提前开展各项防御工作松岗全力以赴确保平稳度汛截至30日16时松岗街道48小时累计降雨量达350.8毫米该街道积极组织开展防汛及消防安全网格巡查整治工作累计出动巡查人员3560人次、车辆1412台次,
- 9.11事件背后的阴谋
250e4f21a70d
美国以本·拉登策划了“911”事件为由发动了阿富汗战争。可是,战争已经过去10多年了。“9.11”事件还有许多谜底至今尚未被解开。在2001年9月11日,美国东部时间约早上8时50分,纽约市曼哈顿区遭到恐怖袭击。世贸中心被两架遭恐怖分子劫持的民航客机相继冲击,两座大厦随即起火并冒出大量浓烟稍后相继倒下,伤亡人数难以估计。此外,世贸中心倒塌后大约一小时,位于华盛顿的五角大楼被第三架飞机撞击,两度爆炸
- 显卡新拐点,涨价或成必然!2019下半年如何选购笔记本?
笔点酷玩
电脑硬件的售价经常浮动,普通消费者完全无法摸透。这是一场持久战,你需要一颗强劲的心脏,以及一些超出预算的资金,降价还好办,万一涨价呢?比如近大半年内存、SSD的持续降价,不少装机人已经沉浸在历史舒适区难以自拔,ddr266616GB已从千元降至500价位段,ddr432008GB也能二百多入手,很难想象1年前还要600入手。除了内存和SSD,处于“换代”的显卡同样带来香甜价格,比如RX5808GB
- js动画html标签(持续更新中)
843977358
htmljs动画mediaopacity
1.jQuery 效果 - animate() 方法 改变 "div" 元素的高度: $(".btn1").click(function(){ $("#box").animate({height:"300px
- springMVC学习笔记
caoyong
springMVC
1、搭建开发环境
a>、添加jar文件,在ioc所需jar包的基础上添加spring-web.jar,spring-webmvc.jar
b>、在web.xml中配置前端控制器
<servlet>
&nbs
- POI中设置Excel单元格格式
107x
poistyle列宽合并单元格自动换行
引用:http://apps.hi.baidu.com/share/detail/17249059
POI中可能会用到一些需要设置EXCEL单元格格式的操作小结:
先获取工作薄对象:
HSSFWorkbook wb = new HSSFWorkbook();
HSSFSheet sheet = wb.createSheet();
HSSFCellStyle setBorder = wb.
- jquery 获取A href 触发js方法的this参数 无效的情况
一炮送你回车库
jquery
html如下:
<td class=\"bord-r-n bord-l-n c-333\">
<a class=\"table-icon edit\" onclick=\"editTrValues(this);\">修改</a>
</td>"
j
- md5
3213213333332132
MD5
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
public class MDFive {
public static void main(String[] args) {
String md5Str = "cq
- 完全卸载干净Oracle11g
sophia天雪
orale数据库卸载干净清理注册表
完全卸载干净Oracle11g
A、存在OUI卸载工具的情况下:
第一步:停用所有Oracle相关的已启动的服务;
第二步:找到OUI卸载工具:在“开始”菜单中找到“oracle_OraDb11g_home”文件夹中
&
- apache 的access.log 日志文件太大如何解决
darkranger
apache
CustomLog logs/access.log common 此写法导致日志数据一致自增变大。
直接注释上面的语法
#CustomLog logs/access.log common
增加:
CustomLog "|bin/rotatelogs.exe -l logs/access-%Y-%m-d.log
- Hadoop单机模式环境搭建关键步骤
aijuans
分布式
Hadoop环境需要sshd服务一直开启,故,在服务器上需要按照ssh服务,以Ubuntu Linux为例,按照ssh服务如下:
sudo apt-get install ssh
sudo apt-get install rsync
编辑HADOOP_HOME/conf/hadoop-env.sh文件,将JAVA_HOME设置为Java
- PL/SQL DEVELOPER 使用的一些技巧
atongyeye
javasql
1 记住密码
这是个有争议的功能,因为记住密码会给带来数据安全的问题。 但假如是开发用的库,密码甚至可以和用户名相同,每次输入密码实在没什么意义,可以考虑让PLSQL Developer记住密码。 位置:Tools菜单--Preferences--Oracle--Logon HIstory--Store with password
2 特殊Copy
在SQL Window
- PHP:在对象上动态添加一个新的方法
bardo
方法动态添加闭包
有关在一个对象上动态添加方法,如果你来自Ruby语言或您熟悉这门语言,你已经知道它是什么...... Ruby提供给你一种方式来获得一个instancied对象,并给这个对象添加一个额外的方法。
好!不说Ruby了,让我们来谈谈PHP
PHP未提供一个“标准的方式”做这样的事情,这也是没有核心的一部分...
但无论如何,它并没有说我们不能做这样
- ThreadLocal与线程安全
bijian1013
javajava多线程threadLocal
首先来看一下线程安全问题产生的两个前提条件:
1.数据共享,多个线程访问同样的数据。
2.共享数据是可变的,多个线程对访问的共享数据作出了修改。
实例:
定义一个共享数据:
public static int a = 0;
- Tomcat 架包冲突解决
征客丶
tomcatWeb
环境:
Tomcat 7.0.6
win7 x64
错误表象:【我的冲突的架包是:catalina.jar 与 tomcat-catalina-7.0.61.jar 冲突,不知道其他架包冲突时是不是也报这个错误】
严重: End event threw exception
java.lang.NoSuchMethodException: org.apache.catalina.dep
- 【Scala三】分析Spark源代码总结的Scala语法一
bit1129
scala
Scala语法 1. classOf运算符
Scala中的classOf[T]是一个class对象,等价于Java的T.class,比如classOf[TextInputFormat]等价于TextInputFormat.class
2. 方法默认值
defaultMinPartitions就是一个默认值,类似C++的方法默认值
- java 线程池管理机制
BlueSkator
java线程池管理机制
编辑
Add
Tools
jdk线程池
一、引言
第一:降低资源消耗。通过重复利用已创建的线程降低线程创建和销毁造成的消耗。第二:提高响应速度。当任务到达时,任务可以不需要等到线程创建就能立即执行。第三:提高线程的可管理性。线程是稀缺资源,如果无限制的创建,不仅会消耗系统资源,还会降低系统的稳定性,使用线程池可以进行统一的分配,调优和监控。
- 关于hql中使用本地sql函数的问题(问-答)
BreakingBad
HQL存储函数
转自于:http://www.iteye.com/problems/23775
问:
我在开发过程中,使用hql进行查询(mysql5)使用到了mysql自带的函数find_in_set()这个函数作为匹配字符串的来讲效率非常好,但是我直接把它写在hql语句里面(from ForumMemberInfo fm,ForumArea fa where find_in_set(fm.userId,f
- 读《研磨设计模式》-代码笔记-迭代器模式-Iterator
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
import java.util.Arrays;
import java.util.List;
/**
* Iterator模式提供一种方法顺序访问一个聚合对象中各个元素,而又不暴露该对象内部表示
*
* 个人觉得,为了不暴露该
- 常用SQL
chenjunt3
oraclesqlC++cC#
--NC建库
CREATE TABLESPACE NNC_DATA01 DATAFILE 'E:\oracle\product\10.2.0\oradata\orcl\nnc_data01.dbf' SIZE 500M AUTOEXTEND ON NEXT 50M EXTENT MANAGEMENT LOCAL UNIFORM SIZE 256K ;
CREATE TABLESPA
- 数学是科学技术的语言
comsci
工作活动领域模型
从小学到大学都在学习数学,从小学开始了解数字的概念和背诵九九表到大学学习复变函数和离散数学,看起来好像掌握了这些数学知识,但是在工作中却很少真正用到这些知识,为什么?
最近在研究一种开源软件-CARROT2的源代码的时候,又一次感觉到数学在计算机技术中的不可动摇的基础作用,CARROT2是一种用于自动语言分类(聚类)的工具性软件,用JAVA语言编写,它
- Linux系统手动安装rzsz 软件包
daizj
linuxszrz
1、下载软件 rzsz-3.34.tar.gz。登录linux,用命令
wget http://freeware.sgi.com/source/rzsz/rzsz-3.48.tar.gz下载。
2、解压 tar zxvf rzsz-3.34.tar.gz
3、安装 cd rzsz-3.34 ; make posix 。注意:这个软件安装与常规的GNU软件不
- 读源码之:ArrayBlockingQueue
dieslrae
java
ArrayBlockingQueue是concurrent包提供的一个线程安全的队列,由一个数组来保存队列元素.通过
takeIndex和
putIndex来分别记录出队列和入队列的下标,以保证在出队列时
不进行元素移动.
//在出队列或者入队列的时候对takeIndex或者putIndex进行累加,如果已经到了数组末尾就又从0开始,保证数
- C语言学习九枚举的定义和应用
dcj3sjt126com
c
枚举的定义
# include <stdio.h>
enum WeekDay
{
MonDay, TuesDay, WednesDay, ThursDay, FriDay, SaturDay, SunDay
};
int main(void)
{
//int day; //day定义成int类型不合适
enum WeekDay day = Wedne
- Vagrant 三种网络配置详解
dcj3sjt126com
vagrant
Forwarded port
Private network
Public network
Vagrant 中一共有三种网络配置,下面我们将会详解三种网络配置各自优缺点。
端口映射(Forwarded port),顾名思义是指把宿主计算机的端口映射到虚拟机的某一个端口上,访问宿主计算机端口时,请求实际是被转发到虚拟机上指定端口的。Vagrantfile中设定语法为:
c
- 16.性能优化-完结
frank1234
性能优化
性能调优是一个宏大的工程,需要从宏观架构(比如拆分,冗余,读写分离,集群,缓存等), 软件设计(比如多线程并行化,选择合适的数据结构), 数据库设计层面(合理的表设计,汇总表,索引,分区,拆分,冗余等) 以及微观(软件的配置,SQL语句的编写,操作系统配置等)根据软件的应用场景做综合的考虑和权衡,并经验实际测试验证才能达到最优。
性能水很深, 笔者经验尚浅 ,赶脚也就了解了点皮毛而已,我觉得
- Word Search
hcx2013
search
Given a 2D board and a word, find if the word exists in the grid.
The word can be constructed from letters of sequentially adjacent cell, where "adjacent" cells are those horizontally or ve
- Spring4新特性——Web开发的增强
jinnianshilongnian
springspring mvcspring4
Spring4新特性——泛型限定式依赖注入
Spring4新特性——核心容器的其他改进
Spring4新特性——Web开发的增强
Spring4新特性——集成Bean Validation 1.1(JSR-349)到SpringMVC
Spring4新特性——Groovy Bean定义DSL
Spring4新特性——更好的Java泛型操作API
Spring4新
- CentOS安装配置tengine并设置开机启动
liuxingguome
centos
yum install gcc-c++
yum install pcre pcre-devel
yum install zlib zlib-devel
yum install openssl openssl-devel
Ubuntu上可以这样安装
sudo aptitude install libdmalloc-dev libcurl4-opens
- 第14章 工具函数(上)
onestopweb
函数
index.html
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/
- Xelsius 2008 and SAP BW at a glance
blueoxygen
BOXelsius
Xelsius提供了丰富多样的数据连接方式,其中为SAP BW专属提供的是BICS。那么Xelsius的各种连接的优缺点比较以及Xelsius是如何直接连接到BEx Query的呢? 以下Wiki文章应该提供了全面的概览。
http://wiki.sdn.sap.com/wiki/display/BOBJ/Xcelsius+2008+and+SAP+NetWeaver+BW+Co
- oracle表空间相关
tongsh6
oracle
在oracle数据库中,一个用户对应一个表空间,当表空间不足时,可以采用增加表空间的数据文件容量,也可以增加数据文件,方法有如下几种:
1.给表空间增加数据文件
ALTER TABLESPACE "表空间的名字" ADD DATAFILE
'表空间的数据文件路径' SIZE 50M;
&nb
- .Net framework4.0安装失败
yangjuanjava
.netwindows
上午的.net framework 4.0,各种失败,查了好多答案,各种不靠谱,最后终于找到答案了
和Windows Update有关系,给目录名重命名一下再次安装,即安装成功了!
下载地址:http://www.microsoft.com/en-us/download/details.aspx?id=17113
方法:
1.运行cmd,输入net stop WuAuServ
2.点击开