bugkuCTF--就五层你能解开吗
@Time : 2018/10/17
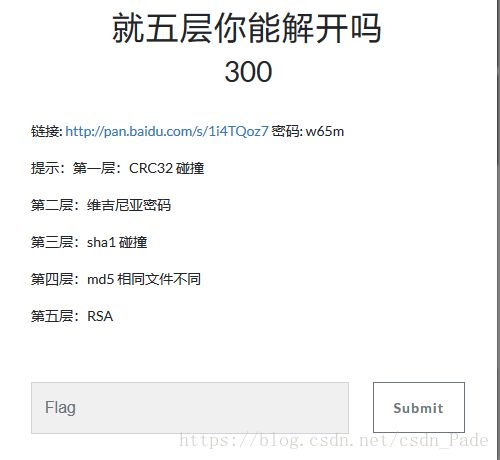
bugku的一道CTF题
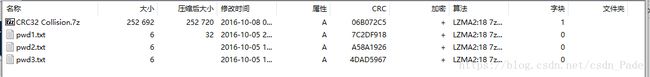
第一层
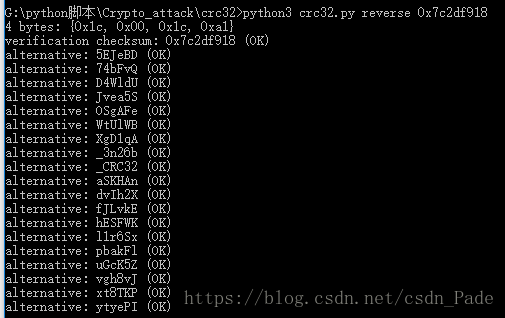
CRC32爆破,附上神器:https://github.com/theonlypwner/crc32 可以解6位CRC
爆破三次就可以得到key:_CRC32_i5_n0t_s4f3
当然,还是需要一点眼力才能看出来的,嘻嘻~
第二层
维吉尼亚密码,参考这位大佬的文章和代码,之后又改了一下代码, https://www.cnblogs.com/maoguy/p/6002510.html
由于输出太多,就加了一个限制输出的条件,一个字符为一个单词的只有 i 或者 a ,于是就有一个判断:
#-*-coding:utf-8-*-
#维吉尼亚解密
def VigenereDecrypto (output , key) :
quotient = len(output) // len(key)
remainder = len(output) % len(key)
key = key*quotient+key[:remainder]
inp = ""
a = 0
for i in range(len(key)) :
if not output[i].isalpha():
inp += ' '
a += 1
else:
c = ord('a') + (ord(output[i])-(ord(key[i-a])+32))%26
inp += chr(c)
return inp
if __name__ == '__main__':
with open('keys.txt','r') as f:
keys = f.read().split('\n')[:-1]
with open('ciphertext.txt','r') as f:
ciphertext = f.read()
for key in keys:
try:
plaintext = VigenereDecrypto(ciphertext,key)
if(plaintext[23:24]=='i' or plaintext[23:24]=='a'):
if(plaintext[148:149]=='i' or plaintext[148:149]=='a'):
if(plaintext[132:133]=='i' or plaintext[132:133]=='a'):
if(plaintext[71:72]=='i' or plaintext[71:72]=='a'):
print(plaintext)
except:
pass这个脚本,好气哦,我把空格算进去了,于是就纠结无数时间,最后看了另外一位大佬的解密脚本,
https://blog.csdn.net/qin_jin_blog/article/details/21889033
#########################Vigenere密码#########################
letter_list='ABCDEFGHIJKLMNOPQRSTUVWXYZ' #字母表
#根据输入的key生成key列表
def Get_KeyList(key):
key_list=[]
for ch in key:
key_list.append(ord(ch.upper())-65)
return key_list
#解密函数
def Decrypt(ciphertext,key_list):
plaintext=""
i=0
for ch in ciphertext: #遍历密文
if 0==i%len(key_list):
i=0
if ch.isalpha(): #密文为否为字母,如果是,则判断大小写,分别进行解密
if ch.isupper():
plaintext+=letter_list[(ord(ch)-65-key_list[i]) % 26]
i+=1
else:
plaintext+=letter_list[(ord(ch)-97-key_list[i]) % 26].lower()
i+=1
else: #如果密文不为字母,直接添加到明文字符串里
plaintext+=ch
return plaintext
if __name__=='__main__':
with open('keys.txt','r') as f:
keys = f.read().split('\n')[:-1]
with open('ciphertext.txt','r') as f:
ciphertext = f.read()
for key in keys:
key_list = Get_KeyList(key)
try:
plaintext = Decrypt(ciphertext,key_list)
if(plaintext[23:24]=='i' or plaintext[23:24]=='a'):
if(plaintext[148:149]=='i' or plaintext[148:149]=='a'):
if(plaintext[132:133]=='i' or plaintext[132:133]=='a'):
if(plaintext[71:72]=='i' or plaintext[71:72]=='a'):
print(plaintext)
except:
pass最后得出password: vigenere cipher funny
第三层
sha1 碰撞,这个倒是不难,遇到过好多次了,写个脚本,
import string
import hashlib
a = '619c20c'
b = 'a4de755'
char = string.printable
print(char)
for i in char:
for j in char:
for k in char:
for l in char:
x = '{0}7{1}5-{2}4{3}3?'.format(i,k,j,l)
ha = hashlib.sha1(x.encode(encoding='utf-8')).hexdigest()
if (a in ha) and (b in ha):
print(x)
print(ha)第四层
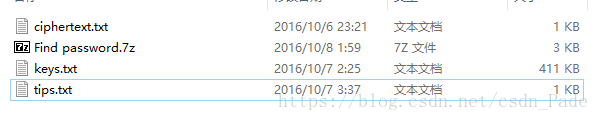
这题,说实话,我不会,看了大佬的做法,,,https://blog.csdn.net/preserphy/article/details/79599397
这里说道了打印helloword与打印goodbye的是相同md5,于是我也去网上找了一下,找到这篇文章,里面讲的很清楚了
https://blog.csdn.net/sysprogram/article/details/73753354
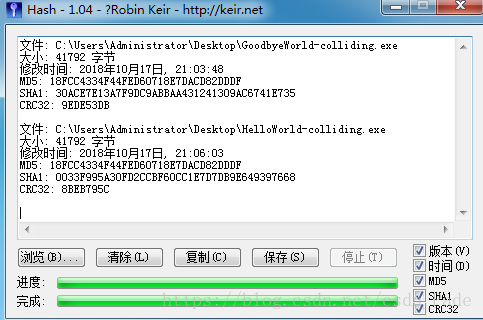
然后我去下载了里面的两个文件,
一个打印Hello World,一个循环打印Goodbye World
再来看看hash,可以看到他们的md5是不同的,而他们的sha1是相同的
OK,就到这里我们得到这个密码是 Goodbye World :-( (虽然来的不光彩,还是写上去了 ummmmmm~)
第五层
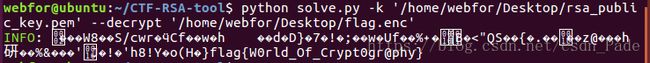
这最后一关是解 RSA ,可以看到他只给了这么几个东西,不过,嘿嘿嘿~我有CTF-RSA-tool,这里给出 git 地址
git clone https://github.com/D001UM3/CTF-RSA-tool.git
cd CTF-RSA-tool
pip install -r "requirements.txt"参考这里面的RSA http://www.freebuf.com/articles/others-articles/161475.html
最后得到了~
--END