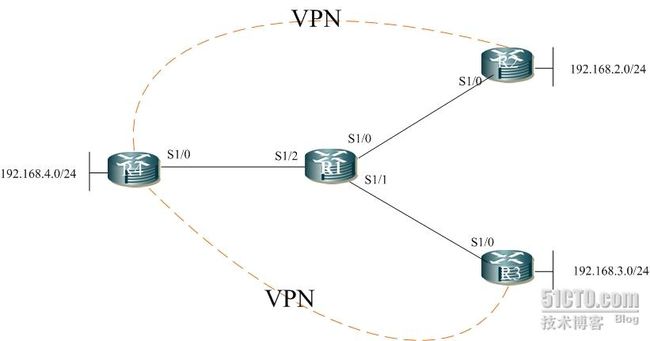
做一个基本的 IPSEC ×××实验,拓扑为SPOKE TO HUB 模式。
实验环境为模拟器
dynamips for linux 2.82
dynagen for linux 0.11
IOS:3745-k9
注意:只有 k8和k9 的路由器ios 支持×××特性。
路由器R2,R3和R4做IPsec ×××。
R1的接口地址为:S1/0 1.1.1.1/24
S1/1 1.1.2.1/24
S1/2 1.1.3.1/23
R2的接口地址为:S1/0 1.1.1.2/24
LO 0 192.168.2.0/24
R3的接口地址为:S1/0 1.1.2.2/24
LO 0 192.168.3.0/24
R4的接口地址为:S1/0 1.1.3.2/24
LO 0 192.168.4.0/24
其中LO口为需要加密的网络,因为基本的×××不支持动态路由协议,如果要用路由则需要GRE封装,这里只启用静态路由,关于×××的理论知识,这里不作介绍。
静态路由设置,IP地址设置等在这里不做描述了。
贴上R1的路由表:
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 3 subnets
C 1.1.1.0 is directly connected, Serial1/0
C 1.1.2.0 is directly connected, Serial1/1
C 1.1.3.0 is directly connected, Serial1/2
S 192.168.4.0/24 is directly connected, Serial1/2
S 192.168.2.0/24 is directly connected, Serial1/0
S 192.168.3.0/24 is directly connected, Serial1/1
C 1.1.1.0 is directly connected, Serial1/0
C 1.1.2.0 is directly connected, Serial1/1
C 1.1.3.0 is directly connected, Serial1/2
S 192.168.4.0/24 is directly connected, Serial1/2
S 192.168.2.0/24 is directly connected, Serial1/0
S 192.168.3.0/24 is directly connected, Serial1/1
现在R2上面启用IPsec ×××
r2(config)#crypto isakmp policy 1 #定义IKE策略1
r2(config-isakmp)#authentication pre-share #定义认证的方式采用预共享KEY
r2(config-isakmp)#encryption 3des #定义加密算法采用3des
r2(config-isakmp)#hash sha #定义哈西采用sha
r2(config-isakmp)#group 2 #定义DH交换采用组2 模式
r2(config-isakmp)#exit
r2(config)#crypto isakmp key fhw address 0.0.0.0 #定义预共享key 和认证对端ip
r2(config-isakmp)#exit
阶段一设置结束,设置ipsec过程
r2(config)#crypto ipsec transform-set test esp-3des ah-sha-hmac #定义ipsec 加密方式和散列算法
r2(cfg-crypto-trans)#mode tunnel #定义隧道模式
r2(config)#crypto map r2 1 ipsec-isakmp #定义加密图,认证方式采用ipsec-isakmp
r2(config-crypto-map)#set peer 1.1.3.2 #设置***对端,此处为r4的s1/0地址
r2(config-crypto-map)#set transform-set test #设置采用刚刚定义的加密方式test
r2(config-crypto-map)#match address 101 #定义受保护流量为acl 101
r2(config)#access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.4.0 0.0.0.255 #定义访问控制列表101,在这里r4受保护流量为192.168.4.0/24
r2(config)#int s1/0
r2(config-if)#crypto map r2 #在端口s1/0上面应用加密图
至此,r2上面基本的***设置完成。
设置R4上面定义IKE
r4(config)#crypto isakmp policy 1
r4(config-isakmp)#authentication pre-share
r4(config-isakmp)#encryption 3des
r4(config-isakmp)#group 2
r4(config-isakmp)#authentication pre-share
r4(config-isakmp)#encryption 3des
r4(config-isakmp)#group 2
r4(config-isakmp)#hash sha
r4(config)#crypto isakmp key fhw address 0.0.0.0
定义R4上面的ipsec,在这里可以通过方向路由注入的方式和对端通讯,因为在很多情况下可能并不知道对端的ip,比如对段为动态adsl接入时。
r4(config)#crypto ipsec transform-set test esp-3des ah-sha-hmac
r4(cfg-crypto-trans)#mode tunnel
r4(config)#crypto dynamic-map r 1 #因为要采用反向路由注入,所以采用动态加密图的方式
r4(config-crypto-map)#reverse-route #启用返乡路由注入
r4(config-crypto-map)#match address 101
r4(config-crypto-map)#set transform-set test
r4(config)#crypto map r4 1 ipsec-isakmp dynamic r #定义加密图r4 并将动态加密图发布进来
r4(config)#access-list 101 permit ip 192.168.4.0 0.0.0.255 192.168.2.0 0.0.0.255
r4(config)#int s1/0
r4(config-if)#crypto map r4
OK,到这里R1和R4上面的×××设置都OK了。
测试:
在R2上面测试:
r2#ping 192.168.4.1 source 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.4.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 12/48/84 ms
Sending 5, 100-byte ICMP Echos to 192.168.4.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 12/48/84 ms
r2#show crypto isakmp sa
dst src state conn-id slot
1.1.3.2 1.1.1.2 QM_IDLE 1 0
dst src state conn-id slot
1.1.3.2 1.1.1.2 QM_IDLE 1 0
可以看到IKE的SA关联已经建立
r2#show crypto ipsec sa
interface: Serial1/0
Crypto map tag: r2, local addr. 1.1.1.2
Crypto map tag: r2, local addr. 1.1.1.2
protected vrf:
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.4.0/255.255.255.0/0/0)
current_peer: 1.1.3.2:500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.4.0/255.255.255.0/0/0)
current_peer: 1.1.3.2:500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 1.1.1.2, remote crypto endpt.: 1.1.3.2
path mtu 1500, ip mtu 1500, ip mtu idb Serial1/0
current outbound spi: 62A2B4A0
path mtu 1500, ip mtu 1500, ip mtu idb Serial1/0
current outbound spi: 62A2B4A0
inbound esp sas:
spi: 0xEE25A9E(249715358)
transform: esp-3des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2002, flow_id: 1, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3384)
IV size: 8 bytes
replay detection support: Y
spi: 0xEE25A9E(249715358)
transform: esp-3des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2002, flow_id: 1, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3384)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
spi: 0xF209E41A(4060734490)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3381)
replay detection support: Y
spi: 0xF209E41A(4060734490)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3381)
replay detection support: Y
inbound pcp sas:
outbound esp sas:
spi: 0x62A2B4A0(1654830240)
transform: esp-3des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2003, flow_id: 2, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3381)
IV size: 8 bytes
spi: 0x62A2B4A0(1654830240)
transform: esp-3des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2003, flow_id: 2, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3381)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
spi: 0xBBC0DEC3(3149979331)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3372)
replay detection support: Y
spi: 0xBBC0DEC3(3149979331)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: r2
sa timing: remaining key lifetime (k/sec): (4588906/3372)
replay detection support: Y
outbound pcp sas:
可以看到IPSEC的SA关联信息
至此实验基本OK!
设置R3可以参考R1的设置,相同道理。
由于是SPOKE TO HUB的方式,所以访问控制列表控制比较麻烦,因为各个节点和中心通讯是没有问题的,如果想让各个节点如R2和R3通讯,则需要在R4上面作全互联的访问控制列表,比较繁琐,所以很多资料里面也说明这种SPOKE TO HUB方式的IPsec ×××建议不要超过10个外点,否则维护起来很麻烦,还有要说明的是,不可以用permit ip any any的方式来保护流量,要求精确匹配!!