实验目的:
通过ez*** client客户端和公司建立连接,获得server分配的一个ip地址来访问公司内网。
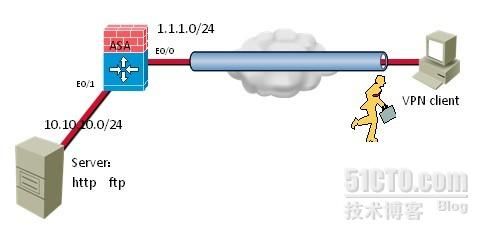
实验拓扑:
![]()
|
|
|
实验配置:
ASA服务端配置:
ciscoasa(config)# sh run
interface Vlan1 //真机下只能借助于vlan配置接口地址,在接口下划分vlan即可
nameif inside
security-level 100
ip address 10.10.10.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 1.1.1.2 255.255.255.0
!
interface Ethernet0/0 //outside接口
switchport access vlan 2
interface Ethernet0/1 //inside接口
switchport access vlan 1
access-list nonat extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
nat (inside) 0 access-list nonat //***流量不进行nat,否则无法通信。
nat (inside) 1 0.0.0.0 0.0.0.0 //配置nat转换
global (outside) 1 interface //pat
//用于隧道分离,正常当问外网
access-list 100 extended permit ip 10.10.10.0 255.255.255.0 any
ip local pool test 10.10.11.10-10.10.11.20 //定义client接入是获取的地址池
crypto isakmp policy 10 //定义阶段一策略
authentication pre-share
encryption 3des
hash sha
group 2
crypto ipsec transform-set myset esp-3des esp-sha-hmac //转换集
crypto dynamic-map dmap 1 set transform-set myset //动态map
crypto dynamic-map dmap 1 set reverse-route
crypto map mymap 1 ipsec-isakmp dynamic dmap //静态map调用dynamic map
crypto map mymap interface outside //outside接口下应用map
crypto isakmp enable outside
group-policy mypolicy internal //定义组策略
group-policy mypolicy attributes
split-tunnel-policy tunnelspecified //配置隧道分离策略
split-tunnel-network-list value 100 //配置隧道分离流量
default-domain value gezi.com
address-pools value test
username xiaomeng password KQ0c1Ql7yB6uQTZX encrypted //创建用户登录
username xiaomeng attributes
***-group-policy mypolicy
tunnel-group meng type remote-access
tunnel-group meng general-attributes
default-group-policy mypolicy
authentication-server-group local //调用本地用户组登录
tunnel-group meng ipsec-attributes
pre-shared-key *
实验验证:
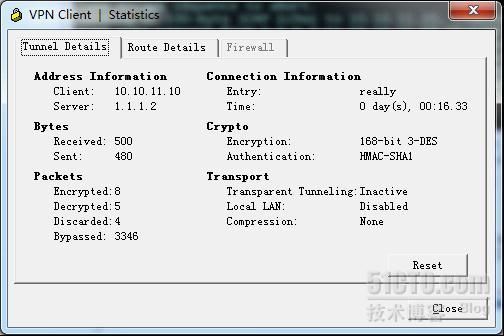
接入成功的tunnel信息:包含获取到的ip地址和server地址(ASA outside接口地址)
ciscoasa# sh crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 1.1.1.138
Type : user Role : responder
Rekey : no State : AM_ACTIVE
ciscoasa# sh crypto ipsec sa
interface: outside
Crypto map tag: dmap, seq num: 1, local addr: 1.1.1.2
local和remote端的信息
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (10.10.11.10/255.255.255.255/0/0)
current_peer: 1.1.1.138, username: xiaomeng
dynamic allocated peer ip: 10.10.11.10
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 8, #pkts decrypt: 8, #pkts verify: 8
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 5, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 1.1.1.2, remote crypto endpt.: 1.1.1.138 //真实网卡地址
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: 1B906805
inbound esp sas:
spi: 0x244ED9B4 (609147316)
transform: esp-3des esp-sha-hmac no compression
in use settings ={RA, Tunnel, }
slot: 0, conn_id: 4096, crypto-map: dmap
sa timing: remaining key lifetime (sec): 27739
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x000001FF
outbound esp sas:
spi: 0x1B906805 (462448645)
transform: esp-3des esp-sha-hmac no compression
in use settings ={RA, Tunnel, }
slot: 0, conn_id: 4096, crypto-map: dmap
sa timing: remaining key lifetime (sec): 27739
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
ciscoasa# sh route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
C 1.1.1.0 255.255.255.0 is directly connected, outside
S 10.10.11.10 255.255.255.255 [1/0] via 1.1.1.138, outside //自动生成一条静态路由
C 10.10.10.0 255.255.255.0 is directly connected, inside