本文是关于漏洞靶场DWVA第一个模块Brute Force的详细解答
LOW等级
此为最低等级low等级下的登录页面,先查看下源代码
1 php 2 3 if( isset( $_GET[ 'Login' ] ) ) { 4 // Get username 5 $user = $_GET[ 'username' ]; 6 7 // Get password 8 $pass = $_GET[ 'password' ]; 9 $pass = md5( $pass ); 10 11 // Check the database 12 $query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';"; 13 $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '' ); 14 15 if( $result && mysqli_num_rows( $result ) == 1 ) { 16 // Get users details 17 $row = mysqli_fetch_assoc( $result ); 18 $avatar = $row["avatar"]; 19 20 // Login successful 21 echo "Welcome to the password protected area {$user}
"; 22 echo "$avatar}\" />"; 23 } 24 else { 25 // Login failed 26 echo "
"; 27 } 28 29 ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); 30 } 31 32 ?>
Username and/or password incorrect.
查看代码可以发现,此代码中将我们输入的用户名直接带入到sql语句中进行查询,
查询成功将显示 Welcome to the password protected area 和一个图片
查询失败将显示 Username and/or password incorrect.
由于在代码中并未对用户输入进行过滤,因此可以实现绕过。
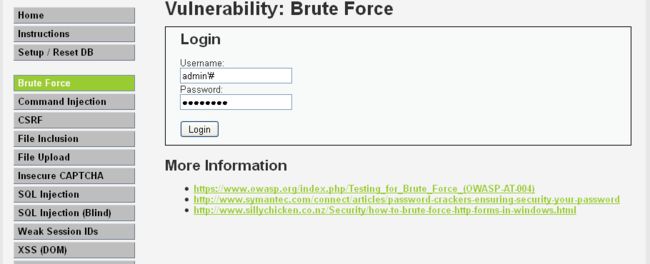
绕过方法--- 用户名‘ #
解读:输入正确的用户名并添加符号’来实现闭合,并用#将后面的字符注释掉,以防止出现闭合问题。
实现方法如图
成功登入效果图:
medium等级
1 php 2 3 if( isset( $_GET[ 'Login' ] ) ) { 4 // Sanitise username input 5 $user = $_GET[ 'username' ]; 6 $user = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $user ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 7 8 // Sanitise password input 9 $pass = $_GET[ 'password' ]; 10 $pass = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); 11 $pass = md5( $pass ); 12 13 // Check the database 14 $query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';"; 15 $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '' ); 16 17 if( $result && mysqli_num_rows( $result ) == 1 ) { 18 // Get users details 19 $row = mysqli_fetch_assoc( $result ); 20 $avatar = $row["avatar"]; 21 22 // Login successful 23 echo "Welcome to the password protected area {$user}
"; 24 echo "$avatar}\" />"; 25 } 26 else { 27 // Login failed 28 sleep( 2 ); 29 echo "
"; 30 } 31 32 ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); 33 } 34 35 ?>
Username and/or password incorrect.
Medium级别的代码主要增加了mysql_real_escape_string函数,这个函数会对字符串中的特殊符号(x00,n,r,,’,”,x1a)进行转义
可以用burpsuit抓包进行暴力破解。