Sendmail之安全
一、配置STARTTLS
1.产生颁发机构
[root@mail ~]# cd /etc/pki/
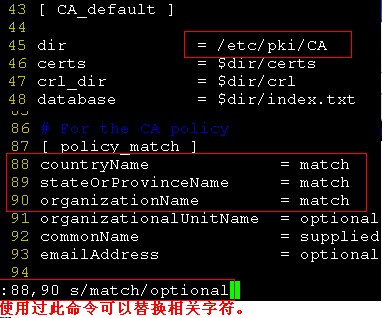
[root@mail pki]# vim tls/openssl.cnf
[root@mail CA]# pwd
/etc/pki/CA
[root@mail CA]# mkdir crl certs newcerts
[root@mail CA]# touch index.txt serial
[root@mail CA]# echo "01" >serial
[root@mail CA]# openssl genrsa 1024 >private/cakey.pem
Generating RSA private key, 1024 bit long modulus
......................................++++++
.........................................................++++++
e is 65537 (0x10001)
[root@mail CA]# chmod 600 private/*
[root@mail CA]#
[root@mail CA]# pwd
/etc/pki/CA
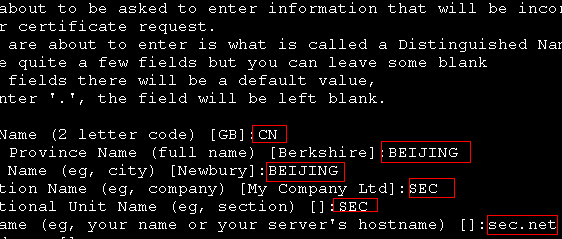
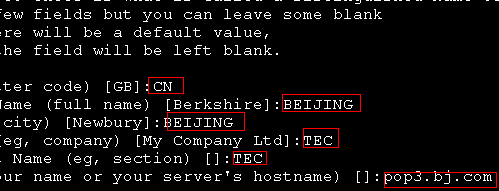
[root@mail CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650
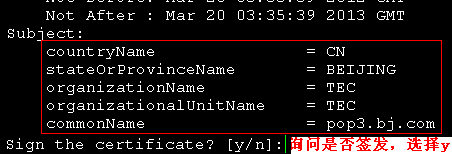
2.为Sendmail颁发证书
[root@mail mail]# pwd
/etc/mail
[root@mail mail]# mkdir certs
[root@mail mail]# cd certs
[root@mail certs]# openssl genrsa 1024 >Sendmail.key
Generating RSA private key, 1024 bit long modulus
....................++++++
........++++++
e is 65537 (0x10001)
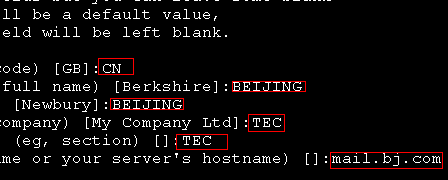
[root@mail certs]# openssl req -new -key Sendmail.key -out Sendmail.csr
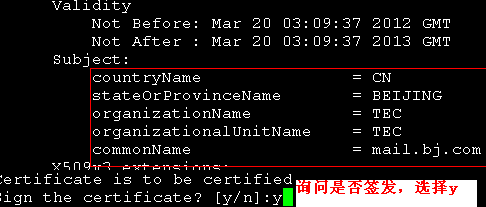
[root@mail certs]# openssl ca -in Sendmail.csr -out Sendmail.cert
[root@mail certs]# pwd
/etc/mail/certs
[root@mail certs]# cp /etc/pki/CA/cacert.pem ./
[root@mail certs]# chmod 600 *
[root@mail certs]# cd ..
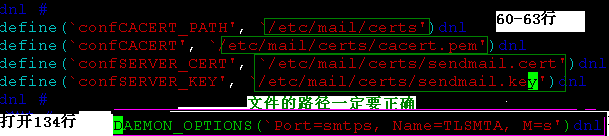
[root@mail mail]# vim Sendmail.mc
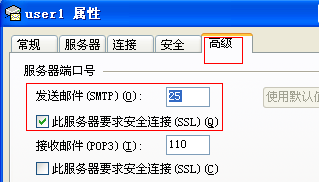
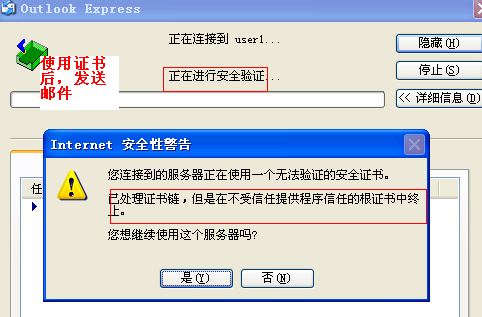
3.Sendmail测试
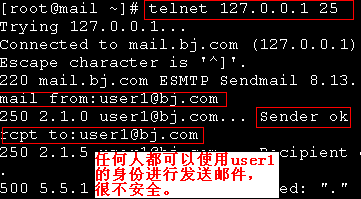
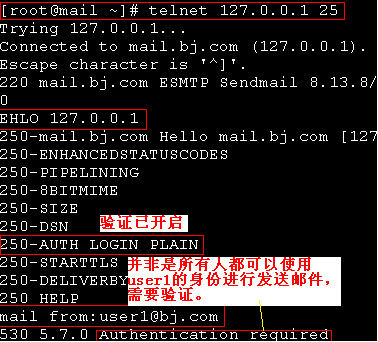
[root@mail mail]# telnet 127.0.0.1 25
Trying 127.0.0.1...
Connected to mail.bj.com (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Tue, 20 Mar 2012 11:30:14 +0800
EHLO 127.0.0.1
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-STARTTLS 证明已经开启
250-DELIVERBY
250 HELP
使用主机测试
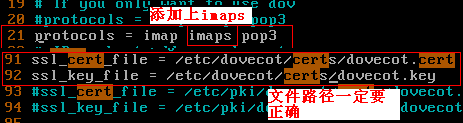
4.为dovecot颁发证书
[root@mail mail]# mkdir -pv /etc/dovecot/certs
mkdir: created directory `/etc/dovecot'
mkdir: created directory `/etc/dovecot/certs'
[root@mail mail]# cd /etc/dovecot/certs/
[root@mail certs]# openssl genrsa 1024 >dovecot.key
Generating RSA private key, 1024 bit long modulus
.......................................................................................++++++
........++++++
e is 65537 (0x10001)
[root@mail certs]#
[root@mail certs]# openssl req -new -key dovecot.key -out dovecot.csr
[root@mail certs]# openssl ca -in dovecot.csr -out dovecot.cert
[root@mail certs]# chmod 600 *
[root@mail certs]# vim /etc/dovecot.conf
[root@mail certs]# service dovecot restart
Stopping Dovecot Imap: [ OK ]
Starting Dovecot Imap: [ OK ]
[root@mail certs]# netstat -tupln |grep dovecot
tcp 0 0 :::993 :::* LISTEN 3660/dovecot
tcp 0 0 :::110 :::* LISTEN 3660/dovecot
tcp 0 0 :::143 :::* LISTEN 3660/dovecot
[root@mail certs]#
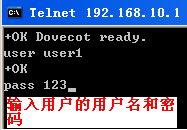
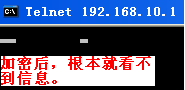
5.dovecot测试
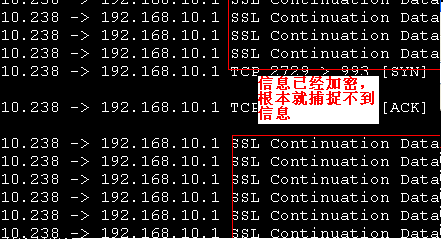
安装wireshark抓包工具
[root@mail ~]# yum install wireshark.i386
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 110"
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 993"
二、配置Sasl
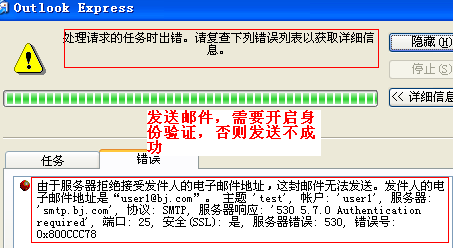
为了尽可能的提供更高的安全性,需要开启Sasl对用户进行验证。系统默认并不启用Sasl,这样就造成了任何人都可以以用户身份发送邮件。
1.查看安装Sasl相关组件
[root@mail Server]# pwd
/mnt/cdrom/Server
[root@mail Server]# rpm -qa|grep Sasl
cyrus-Sasl-lib-2.1.22-5.el5
cyrus-Sasl-2.1.22-5.el5
cyrus-Sasl-devel-2.1.22-5.el5
cyrus-Sasl-plain-2.1.22-5.el5
[root@mail Server]#
[root@mail ~]# service Saslauthd start
Starting Saslauthd: [ OK ]
[root@mail ~]#
[root@mail Server]# chkconfig --list|grep Sasl
Saslauthd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
[root@mail Server]# chkconfig Saslauthd on
[root@mail Server]# chkconfig --list|grep Sasl
Saslauthd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
[root@mail Server]#
[root@mail Server]# rpm -qc cyrus-Sasl
/etc/rc.d/init.d/Saslauthd
/etc/sysconfig/Saslauthd
[root@mail Server]#
2.修改Sasl相关配置文件
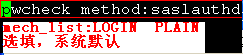
[root@mail ~]# cd /usr/lib/Sasl2/
[root@mail Sasl2]# vim Sendmail.conf
[root@mail Sasl2]# cd /etc/mail
[root@mail mail]# pwd
/etc/mail
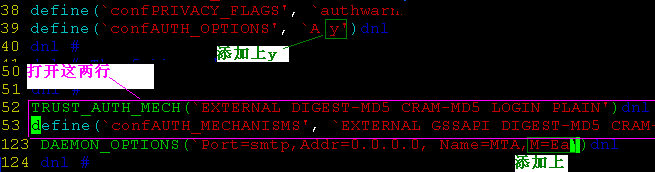
[root@mail mail]# vim Sendmail.mc
[root@mail mail]# service Sendmail restart
Shutting down sm-client: [ OK ]
Shutting down Sendmail: [ OK ]
Starting Sendmail: [ OK ]
Starting sm-client: [ OK ]
[root@mail mail]#
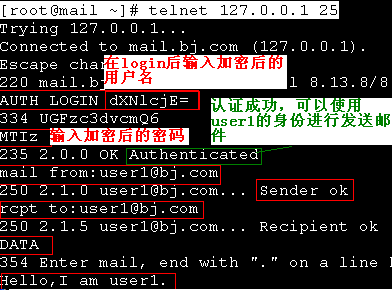
3.帐号测试
对用户的帐号进行编码
[root@mail ~]# echo -n "user1"|openssl base64
dXNlcjE=
[root@mail ~]# echo -n "123"|openssl base64
MTIz
[root@mail ~]#
4.邮件测试
在不开启身份验证的情况下,发送邮件
开启身份验证