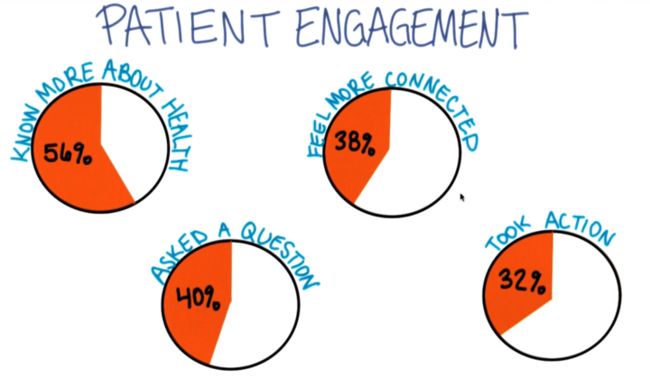
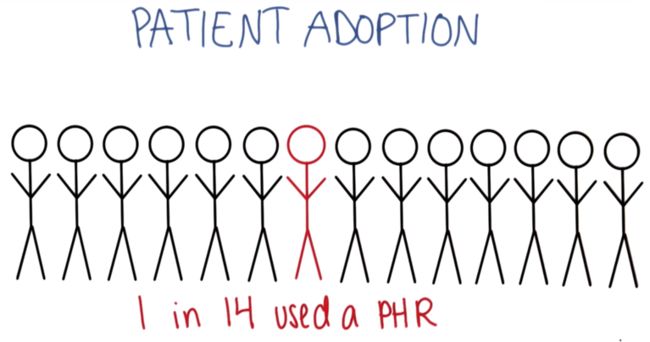
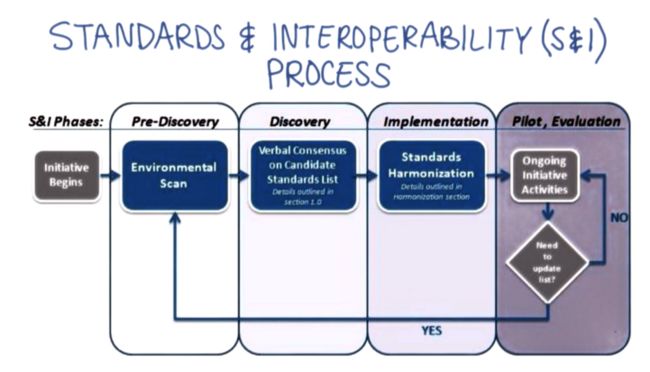
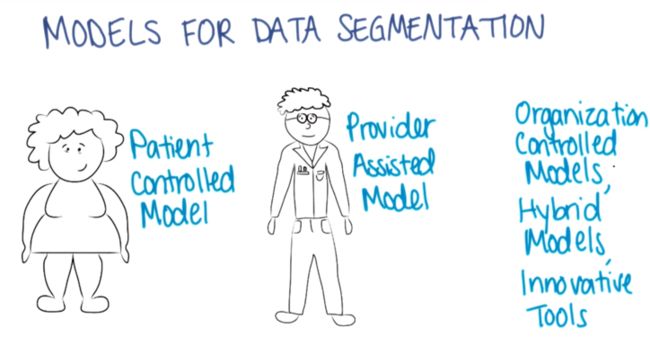
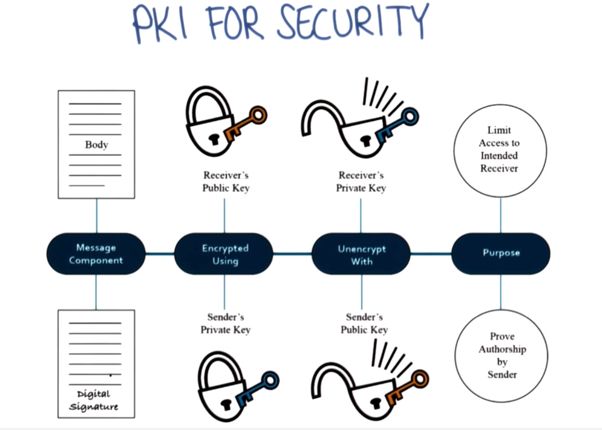
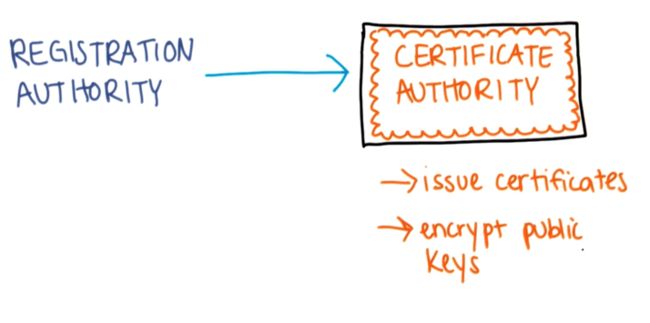
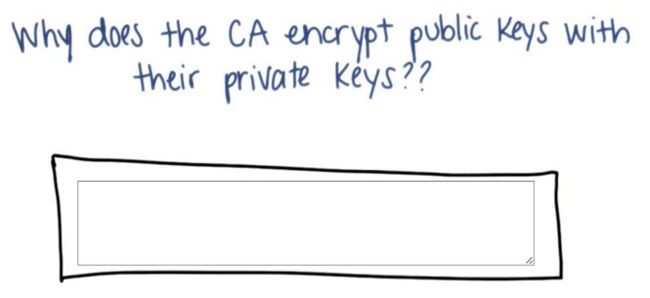
- 黄金屋 #2 我应该将产品开源吗?
_tison
开源
“开源”(Open-Source),如同“自由软件”(FreeSoftware)一样,凭借其有意为之的模糊赢得了广泛传播。泛泛而谈开源,甚至是将所谓开源硬件、开源文档、开放设计等都归入开源的范畴,很容易丧失焦点。本文不讨论任意个体或组织开发的任意软件是否应该开源,而是聚焦在企业研发的商业软件产品应当采取的开源策略。从著名的《大教堂与集市》文集当中第四篇《魔法锅》开始。其中4.6节“闭源的理由”写到
- ruoyi 小程序使用笔记
万变不离其宗_8
笔记小程序笔记
1.上传图片页面jsimportuploadfrom'@/utils/upload.js'methods:{upload(){constconfig={filePath:this.$refs.imageUploadRetire.files[0].path,url:'/api/common/file/upload'}upload(config).then(res=>{this.form.retire
- 技术革命、需求升级与商业生态迭代——基于开源AI大模型与智能商业范式的创新研究
说私域
人工智能开源小程序微信零售
摘要:本文以技术哲学与商业生态系统理论为分析框架,通过质性研究与案例分析法,系统阐释第三次与第四次科技革命如何通过技术范式创新引发用户需求跃迁,进而驱动商业生态系统的结构性变革。研究聚焦开源AI大模型、AI智能名片、S2B2C商城及小程序源码等前沿技术工具,解构其如何重构"技术赋权-需求进化-商业物种爆发"的价值传导链条。研究发现:技术革命通过创造新需求空间、重构价值网络拓扑结构、降低创新参与门槛
- MySQL学习路线
蜡笔小新星
MySQL数据库mysql学习经验分享
本专栏纯干货订阅专栏不迷路以下是一个详细的MySQL学习路线,适合从初学者到中高级用户的逐步学习。整个路线分为几个阶段,每个阶段包含了必要的知识点和学习材料。第一阶段:基础知识(1-2周)目标:了解数据库的基本概念,熟悉MySQL的基本用法。学习内容:数据库基础什么是数据库、数据库管理系统(DBMS)数据库的类型(关系型数据库与非关系型数据库)SQL(结构化查询语言)概述MySQL入门MySQL的
- GS-SLAM论文阅读笔记-MGSO
zenpluck
GS论文阅读论文阅读笔记
前言MGSO首字母缩略词是直接稀疏里程计(DSO),我们建立的光度SLAM系统和高斯飞溅(GS)的混合。这应该是第一个前端用DSO的高斯SLAM,不知道这个系统的组合能不能打得过ORB-SLAM3,以及对DSO会做出怎么样的改进以适应高斯地图,接下来就看一下吧!GishelloG^s_ihelloGishello我是红色文章目录前言1.背景介绍2.关键内容2.1SLAMmodule2.2Dense
- 家用笔记本换装centos7当服务器全流程
吕域
服务器windows电脑centos
目录1、安装centos7系统硬件准备软件和镜像准备制作启动盘2、网络连接和ssh远程登陆centos7连接网络ssh远程登陆3、笔记本闭盖不休眠(7*24小时可用)4、定时开关机(省电、保护电脑)5、配置开发环境(此处以python为例,非必要项,示需求安装)1、安装centos7系统硬件准备老旧淘汰笔记本一台(新笔记本不合算,舍不得)一个大于8G的U盘网线一根(后续联网用)软件和镜像准备软件U
- CentOS 7.x 快速搭建ARK服务器
Aorsion
Linuxarkserverarkservercentos方舟服务器搭建Linux方舟开服教程方舟多人联机
本人菜鸟一枚,最近喜欢上了ark,也找到了2个基友,但是在别的服玩的不是很开心(非人民币玩家,你们懂),刚好有台闲置的拯救者14笔记本,i7-4720HQ、16G内存、128G三星970pro,1T机械,索性拿来装个Centos7.6搭个服自己玩,就多点电费的事,下面把自己折腾一天的开服经历做个笔记留给和我一样的童鞋,喜欢开服工具的请绕道友情提醒:ARK需要大量内存,建议使用至少具有6GBRAM以
- 设计模式--增强工厂、安全工厂
ଲ218
设计模式javascript前端
增强工厂//通过类来创建对象functionPeople(name,age,sex){this.name=name;this.age=age;this.sex=sex;}//方法People.prototype.intro=function(){console.log('我是'+this.name+'性别是'+this.sex+'今年'+this.age);}//创建实例varp1=newPeop
- docker-compose笔记
Re_Virtual
dockerdocker笔记容器
docker目前docker官网已经无法登录,但是还可以从清华镜像站(https://mirrors.tuna.tsinghua.edu.cn/docker-ce/)下载。使用方法可以参考早期文章《docker笔记》docker-compose可以从Github下载不同版本的二进制文件,例如docker-compose-linux-x86_64。下载完成后,将二进制文件复制入路径,例如/usr/l
- iOS接入微信支付(小白都能看懂的微信支付)
马拉萨的春天
功能模块一天一读基础知识点
因为近期项目中需要接入微信支付功能,自己也爬了很多的坑,所以做了一下这边文章供大家学习参考,远离爬坑,文章主要讲到以下五部分:一、填写商户平台所需资料二、具体Demo代码@Github下载地址本文为本人学习记录笔记,如需转载,请注明出处@iOS_lyon填写商户平台所需资料一、填写经营信息@查看截图指引下图选择不同的类目,所需要上传的资料也是有所不同的,下图拿其它为例子填写经营信息二、填写商户信息
- 关于误差平面小记
文弱_书生
乱七八糟平面算法神经网络机器学习
四维曲面的二维切片:误差平面详解在深度学习优化过程中,我们通常研究损失函数(LossFunction)的变化,试图找到权重的最优配置。由于神经网络的参数空间通常是高维的,我们需要使用低维可视化的方法来理解优化过程和误差平面(ErrorSurface)。在这里,我们讨论一个四维曲面的二维切片,其中:三个维度是网络的权重(w1,w2,w3w_1,w_2,w_3w1,w2,w3)。第四个维度是误差(损失
- MySQL性能优化实战笔记 - 通俗易懂版
泥潭硬拔
mysql性能优化笔记
1.存储引擎选择-到底选哪个?InnoDBvsMyISAM通俗对比想象你开了一家银行:InnoDB就像是有保险柜的银行支持事务:比如转账,要么都成功,要么都失败行级锁:小明在存钱时,小红还能同时取钱缺点:需要更多内存和CPUMyISAM就像是简易储物柜不支持事务:操作简单直接表级锁:一个人在用时,其他人要等待优点:读取速度快,占用资源少2.实战案例:常见性能问题及解决方案案例1:查询特别慢--糟糕
- rust学习笔记16-206.反转链表(递归)
水蜜桃one
学习笔记链表
rust函数递归在14中已经提到,接下来我们把206.反转链表,用递归法实现递归函数通常包含两个主要部分:基准条件(BaseCase):递归终止的条件,避免无限递归。递归步骤(RecursiveStep):将问题分解为更小的子问题,并调用自身来解决这些子问题。//Definitionforsingly-linkedlist.#[derive(PartialEq,Eq,Clone,Debug)]pu
- 嵌入式笔记 | 正点原子STM32F103ZET6 3 | 时钟系统
J鸟
笔记stm32单片机嵌入式硬件
1.RCC(复位和时钟控制)RCC(ResetandClockControl)是STM32的时钟系统控制模块,负责管理整个芯片的时钟信号。在使用任何外设之前,必须先使能其时钟。2.时钟系统框图解析时钟源(5种)HSI(高速内部时钟)由内部RC振荡器产生,默认8MHz精度较低,适用于对时钟精度要求不高的应用可作为系统时钟源HSE(高速外部时钟)由外部晶振(石英/陶瓷谐振器或外部时钟)产生,频率范围4
- 25年申报工商年报前先看这篇笔记,帮你避坑,少走弯路!
搬砖小杨聊资质
笔记
又到工商年报申报的时候了(25年截止日期6月30日),今年年报申报与去年有点区别,我特意整理出来与大家分享,帮助大家避坑。笔记不长,5分钟时间让你事半功倍,你就是老板眼中最靓的仔!!1、今年国家企业信用信息公示系统做了个更新,未完成年报填写或有多家公司需要申报的,一定要点击退出登录,不要直接关闭网页。否则当你想要继续填写年报或申报其他公司的,需要等待系统【自动退出登录】,时间2-3个小时,会大大影
- day11 学习笔记
豆豆
学习笔记python
文章目录前言一、类方法二、静态方法三、构造方法四、魔术方法前言通过今天的学习,我掌握了更多Python中有关面向对象编程思想中方法的概念与操作,包括类方法,静态方法,构造方法,魔术方法一、类方法类方法是属于类的行为,一般使用类而非对象进行调用类方法需要使用@classmethod装饰器定义类方法至少有一个形参用于绑定类,约定为cls类和该类的实例都可以调用类方法,但一般不用实例进行调用类方法不能访
- 《Operating System Concepts》阅读笔记:p449-p459
操作系统
《OperatingSystemConcepts》学习第35天,p449-p459总结,总计11页。一、技术总结1.NVM&SSDFlash-memory-basedNVMisfrequentlyusedinadisk-drive-likecontainer,inwhichcaseitiscalledasolid-statedisk(SSD)(Figure11.3)。2.HDDScheduling
- 【typescript进阶篇】(第四章) webpack编译ts及第三方库声明文件
蒜香拿铁
typescript系列typescriptwebpackjavascript
使用webpack打包TS文件安装依赖安装webpack环境npmiwebpackwebpack-cliwebpack-dev-server-D安装TypeScriptnpminstalltypescript-D编译TSnpminstallts-loader-D热更新服务npminstallwebpack-dev-server-DHTML模板npminstallhtml-webpack-plugi
- vllm安装踩坑
蒸土豆的技术细节
人工智能
今天是2024/7/18.vllm0.5.2最近一周出了个不好搞的新issue,会遇到torch.ops._C没有rms_norm,或者没有reshape_and_cache_flash这两个属性的问题。完整报错如下:AttributeError:‘_OpNamespace’‘_C_cache_ops’objecthasnoattribute‘reshape_and_cache_flash’Att
- 数智读书笔记系列021《大数据医疗》:探索医疗行业的智能变革
Allen_Lyb
数智读书笔记大数据健康医疗人工智能python
一、书籍介绍《大数据医疗》由徐曼、沈江、余海燕合著,由机械工业出版社出版。徐曼是南开大学商学院副教授,在大数据驱动的智能决策研究领域颇有建树,尤其在大数据驱动的医疗与健康决策方面有着深入研究,曾获天津优秀博士论文、教育部博士研究生新人奖。沈江等作者也在相关学术和实践领域有着丰富的经验和深厚的专业知识。这本书系统且深入地探讨了大数据技术在医疗领域的应用与变革,对推动医疗行业的智能化发展具有重要的理论
- 笔记:代码随想录算法训练营day57:99.岛屿数量 深搜、岛屿数量 广搜、100.岛屿的最大面积
jingjingjing1111
深度优先算法笔记
学习资料:代码随想录注:文中含大模型生成内容99.岛屿数量卡码网题目链接(ACM模式)先看深搜方法:找到未标标记过的说明找到一片陆地的或者一片陆地的一个角落,dfs搜索是寻找相连接的陆地其余部分并做好标记#include#includeusingnamespacestd;intdirection[4][2]={0,1,-1,0,0,-1,1,0};voiddfs(constvector>&B612
- 笔记:代码随想录算法训练营day56:图论理论基础、深搜理论基础、98. 所有可达路径、广搜理论基础
jingjingjing1111
笔记
学习资料:代码随想录连通图是给无向图的定义,强连通图是给有向图的定义朴素存储:二维数组邻接矩阵邻接表:list基础知识:C++容器类|菜鸟教程深搜是沿着一个方向搜到头再不断回溯,转向;广搜是每一次搜索要把当前能够得到的方向搜个遍深搜三部曲:传入参数、终止条件、处理节点+递推+回溯98.所有可达路径卡码网题目链接(ACM模式)先是用邻接矩阵,矩阵的x,y表示从x到y有一条边主要还是用回溯方法遍历整个
- Neo4j GDS-02-graph-data-science 插件库安装实战笔记
后端java
neo4japoc系列Neo4jAPOC-01-图数据库apoc插件介绍Neo4jAPOC-01-图数据库apoc插件安装neo4jonwindows10Neo4jAPOC-03-图数据库apoc实战使用使用Neo4jAPOC-04-图数据库apoc实战使用使用apoc.path.spanningTree最小生成树Neo4jAPOC-05-图数据库apoc实战使用使用labelFilterNeo4
- git推送内容到远程库时,显示登陆失败Logon failed,ues ctrl+c to cancel basic credential prompt
谭弹潭
经验分享命令模式
首先出现这个问题的原因可能是你的gitbash太旧了,需要更新,而且github在21年的时候就把密码认证的方式给删掉了,而选择用personalaccesstoken来代替密码的认证。所以就算你输入的帐号和密码是正确的,但你还是无法正确登陆。第一步:登陆github的官网,点击右上角的头像第二步:点击setting第三步:点击Developersettings第四步:点击Generatenewt
- 为了拯救minerU镜像制作过程给大家带来的痛苦,我决定放一个备份到阿里云上
几道之旅
人工智能智能体及数字员工人工智能
文章目录第零步,如果你只是想用这个镜像,那你后面的都不用看。第一步,搜索阿里云,并进入官网第二步,把光标放在产品上,就会出现所有的产品目录第三步容器中,选择容器镜像服务第四步,点击“免费试用,就会让你登录”第五步,点击管理控制台第六步,示例列表中,选择个人版第七步,访问凭证中,设置固定密码第八步,在命名空间中,创建命名空间第九步:创建一个镜像仓库第十步,它会直接跳转到一个说明文档,告诉你具体该怎么
- 区块链驱动金融第四章——比特币实用指南:存储与使用全解析
小DuDu
区块链金融
在比特币的世界里,存储和使用比特币是每个参与者都必须面对的重要环节。第四章围绕这两个关键方面展开了详细的阐述,为我们提供了全面而深入的见解。现在,就让我们一起走进这一章,探索如何安全、便捷地存储和使用比特币。比特币的存储方式:多样选择,各有优劣简单本地储存:便捷与风险并存把比特币存储在本地设备上是最直接的方式,就像把钱放在钱包里一样方便。人们通常会使用比特币钱包软件来管理比特币和私钥,通过这些软件
- 洛谷每日1题-------Day25__P1424 小鱼的航程(改进版)
__雨夜星辰__
洛谷每日1题算法c++数据结构学习笔记
题目描述有一只小鱼,它平日每天游泳250公里,周末休息(实行双休日),假设从周x开始算起,过了n天以后,小鱼一共累计游泳了多少公里呢?输入格式输入两个正整数x,n,表示从周x算起,经过n天。输出格式输出一个整数,表示小鱼累计游泳了多少公里。输入输出样例输入#1复制310输出#1复制2000说明/提示数据保证,1≤x≤7,1≤n≤106。题解#includeusingnamespacestd;int
- Windows使用Browser Use笔记
人工智能ai开发
相关文档:https://docs.browser-use.com/quickstart首先安装UV命令行cmdpowershell-ExecutionPolicyByPass-c"irmhttps://astral.sh/uv/install.ps1|iex"设置环境变量setPath=C:\xx\.local\bin;%Path%查看版本uv-V查看可用和已安装的Python版本uvpytho
- 使用spring data MongoDB对MongoDB进行简单CURD操作示例
其实我就是个萌新
springmongodbjava
本文章为作者个人学习笔记,仅作参考。1.application.properties配置spring.data.mongodb.database=[数据库名]spring.data.mongodb.host=localhost[主机名,本机:localhost]spring.data.mongodb.port=[数据库端口,默认:27017]2.根据数据库文档定义实体类:@RequiredArgs
- 【Vue3笔记01】如何使用Vue3和Vite搭建前端项目的基础开发环境
Mr.小朱同学
Web前端笔记前端笔记vue.jsVue3Vite搭建项目环境
这篇文章,主要介绍如何使用Vue3和Vite搭建前端项目的基础开发环境【知识星球】。目录一、搭建项目环境1.1、前提条件1.2、开始搭建1.3、下载依赖1.4、启动工程一、搭建项目环境目前前端开发中,使用最多的就是Vue.js框架,目前Vue.js框架常用的有Vue2、Vue3两个版本,Vue3和Vue2在语法上还是存在很大的差异的,这里我将介绍如何搭建Vue3开发环境。1.1、前提条件在创建Vu
- java数字签名三种方式
知了ing
javajdk
以下3钟数字签名都是基于jdk7的
1,RSA
String password="test";
// 1.初始化密钥
KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA");
keyPairGenerator.initialize(51
- Hibernate学习笔记
caoyong
Hibernate
1>、Hibernate是数据访问层框架,是一个ORM(Object Relation Mapping)框架,作者为:Gavin King
2>、搭建Hibernate的开发环境
a>、添加jar包:
aa>、hibernatte开发包中/lib/required/所
- 设计模式之装饰器模式Decorator(结构型)
漂泊一剑客
Decorator
1. 概述
若你从事过面向对象开发,实现给一个类或对象增加行为,使用继承机制,这是所有面向对象语言的一个基本特性。如果已经存在的一个类缺少某些方法,或者须要给方法添加更多的功能(魅力),你也许会仅仅继承这个类来产生一个新类—这建立在额外的代码上。
- 读取磁盘文件txt,并输入String
一炮送你回车库
String
public static void main(String[] args) throws IOException {
String fileContent = readFileContent("d:/aaa.txt");
System.out.println(fileContent);
- js三级联动下拉框
3213213333332132
三级联动
//三级联动
省/直辖市<select id="province"></select>
市/省直辖<select id="city"></select>
县/区 <select id="area"></select>
- erlang之parse_transform编译选项的应用
616050468
parse_transform游戏服务器属性同步abstract_code
最近使用erlang重构了游戏服务器的所有代码,之前看过C++/lua写的服务器引擎代码,引擎实现了玩家属性自动同步给前端和增量更新玩家数据到数据库的功能,这也是现在很多游戏服务器的优化方向,在引擎层面去解决数据同步和数据持久化,数据发生变化了业务层不需要关心怎么去同步给前端。由于游戏过程中玩家每个业务中玩家数据更改的量其实是很少
- JAVA JSON的解析
darkranger
java
// {
// “Total”:“条数”,
// Code: 1,
//
// “PaymentItems”:[
// {
// “PaymentItemID”:”支款单ID”,
// “PaymentCode”:”支款单编号”,
// “PaymentTime”:”支款日期”,
// ”ContractNo”:”合同号”,
//
- POJ-1273-Drainage Ditches
aijuans
ACM_POJ
POJ-1273-Drainage Ditches
http://poj.org/problem?id=1273
基本的最大流,按LRJ的白书写的
#include<iostream>
#include<cstring>
#include<queue>
using namespace std;
#define INF 0x7fffffff
int ma
- 工作流Activiti5表的命名及含义
atongyeye
工作流Activiti
activiti5 - http://activiti.org/designer/update在线插件安装
activiti5一共23张表
Activiti的表都以ACT_开头。 第二部分是表示表的用途的两个字母标识。 用途也和服务的API对应。
ACT_RE_*: 'RE'表示repository。 这个前缀的表包含了流程定义和流程静态资源 (图片,规则,等等)。
A
- android的广播机制和广播的简单使用
百合不是茶
android广播机制广播的注册
Android广播机制简介 在Android中,有一些操作完成以后,会发送广播,比如说发出一条短信,或打出一个电话,如果某个程序接收了这个广播,就会做相应的处理。这个广播跟我们传统意义中的电台广播有些相似之处。之所以叫做广播,就是因为它只负责“说”而不管你“听不听”,也就是不管你接收方如何处理。另外,广播可以被不只一个应用程序所接收,当然也可能不被任何应
- Spring事务传播行为详解
bijian1013
javaspring事务传播行为
在service类前加上@Transactional,声明这个service所有方法需要事务管理。每一个业务方法开始时都会打开一个事务。
Spring默认情况下会对运行期例外(RunTimeException)进行事务回滚。这
- eidtplus operate
征客丶
eidtplus
开启列模式: Alt+C 鼠标选择 OR Alt+鼠标左键拖动
列模式替换或复制内容(多行):
右键-->格式-->填充所选内容-->选择相应操作
OR
Ctrl+Shift+V(复制多行数据,必须行数一致)
-------------------------------------------------------
- 【Kafka一】Kafka入门
bit1129
kafka
这篇文章来自Spark集成Kafka(http://bit1129.iteye.com/blog/2174765),这里把它单独取出来,作为Kafka的入门吧
下载Kafka
http://mirror.bit.edu.cn/apache/kafka/0.8.1.1/kafka_2.10-0.8.1.1.tgz
2.10表示Scala的版本,而0.8.1.1表示Kafka
- Spring 事务实现机制
BlueSkator
spring代理事务
Spring是以代理的方式实现对事务的管理。我们在Action中所使用的Service对象,其实是代理对象的实例,并不是我们所写的Service对象实例。既然是两个不同的对象,那为什么我们在Action中可以象使用Service对象一样的使用代理对象呢?为了说明问题,假设有个Service类叫AService,它的Spring事务代理类为AProxyService,AService实现了一个接口
- bootstrap源码学习与示例:bootstrap-dropdown(转帖)
BreakingBad
bootstrapdropdown
bootstrap-dropdown组件是个烂东西,我读后的整体感觉。
一个下拉开菜单的设计:
<ul class="nav pull-right">
<li id="fat-menu" class="dropdown">
- 读《研磨设计模式》-代码笔记-中介者模式-Mediator
bylijinnan
java设计模式
声明: 本文只为方便我个人查阅和理解,详细的分析以及源代码请移步 原作者的博客http://chjavach.iteye.com/
/*
* 中介者模式(Mediator):用一个中介对象来封装一系列的对象交互。
* 中介者使各对象不需要显式地相互引用,从而使其耦合松散,而且可以独立地改变它们之间的交互。
*
* 在我看来,Mediator模式是把多个对象(
- 常用代码记录
chenjunt3
UIExcelJ#
1、单据设置某行或某字段不能修改
//i是行号,"cash"是字段名称
getBillCardPanelWrapper().getBillCardPanel().getBillModel().setCellEditable(i, "cash", false);
//取得单据表体所有项用以上语句做循环就能设置整行了
getBillC
- 搜索引擎与工作流引擎
comsci
算法工作搜索引擎网络应用
最近在公司做和搜索有关的工作,(只是简单的应用开源工具集成到自己的产品中)工作流系统的进一步设计暂时放在一边了,偶然看到谷歌的研究员吴军写的数学之美系列中的搜索引擎与图论这篇文章中的介绍,我发现这样一个关系(仅仅是猜想)
-----搜索引擎和流程引擎的基础--都是图论,至少像在我在JWFD中引擎算法中用到的是自定义的广度优先
- oracle Health Monitor
daizj
oracleHealth Monitor
About Health Monitor
Beginning with Release 11g, Oracle Database includes a framework called Health Monitor for running diagnostic checks on the database.
About Health Monitor Checks
Health M
- JSON字符串转换为对象
dieslrae
javajson
作为前言,首先是要吐槽一下公司的脑残编译部署方式,web和core分开部署本来没什么问题,但是这丫居然不把json的包作为基础包而作为web的包,导致了core端不能使用,而且我们的core是可以当web来用的(不要在意这些细节),所以在core中处理json串就是个问题.没办法,跟编译那帮人也扯不清楚,只有自己写json的解析了.
- C语言学习八结构体,综合应用,学生管理系统
dcj3sjt126com
C语言
实现功能的代码:
# include <stdio.h>
# include <malloc.h>
struct Student
{
int age;
float score;
char name[100];
};
int main(void)
{
int len;
struct Student * pArr;
int i,
- vagrant学习笔记
dcj3sjt126com
vagrant
想了解多主机是如何定义和使用的, 所以又学习了一遍vagrant
1. vagrant virtualbox 下载安装
https://www.vagrantup.com/downloads.html
https://www.virtualbox.org/wiki/Downloads
查看安装在命令行输入vagrant
2.
- 14.性能优化-优化-软件配置优化
frank1234
软件配置性能优化
1.Tomcat线程池
修改tomcat的server.xml文件:
<Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" redirectPort="8443" maxThreads="1200" m
- 一个不错的shell 脚本教程 入门级
HarborChung
linuxshell
一个不错的shell 脚本教程 入门级
建立一个脚本 Linux中有好多中不同的shell,但是通常我们使用bash (bourne again shell) 进行shell编程,因为bash是免费的并且很容易使用。所以在本文中笔者所提供的脚本都是使用bash(但是在大多数情况下,这些脚本同样可以在 bash的大姐,bourne shell中运行)。 如同其他语言一样
- Spring4新特性——核心容器的其他改进
jinnianshilongnian
spring动态代理spring4依赖注入
Spring4新特性——泛型限定式依赖注入
Spring4新特性——核心容器的其他改进
Spring4新特性——Web开发的增强
Spring4新特性——集成Bean Validation 1.1(JSR-349)到SpringMVC
Spring4新特性——Groovy Bean定义DSL
Spring4新特性——更好的Java泛型操作API
Spring4新
- Linux设置tomcat开机启动
liuxingguome
tomcatlinux开机自启动
执行命令sudo gedit /etc/init.d/tomcat6
然后把以下英文部分复制过去。(注意第一句#!/bin/sh如果不写,就不是一个shell文件。然后将对应的jdk和tomcat换成你自己的目录就行了。
#!/bin/bash
#
# /etc/rc.d/init.d/tomcat
# init script for tomcat precesses
- 第13章 Ajax进阶(下)
onestopweb
Ajax
index.html
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/
- Troubleshooting Crystal Reports off BW
blueoxygen
BO
http://wiki.sdn.sap.com/wiki/display/BOBJ/Troubleshooting+Crystal+Reports+off+BW#TroubleshootingCrystalReportsoffBW-TracingBOE
Quite useful, especially this part:
SAP BW connectivity
For t
- Java开发熟手该当心的11个错误
tomcat_oracle
javajvm多线程单元测试
#1、不在属性文件或XML文件中外化配置属性。比如,没有把批处理使用的线程数设置成可在属性文件中配置。你的批处理程序无论在DEV环境中,还是UAT(用户验收
测试)环境中,都可以顺畅无阻地运行,但是一旦部署在PROD 上,把它作为多线程程序处理更大的数据集时,就会抛出IOException,原因可能是JDBC驱动版本不同,也可能是#2中讨论的问题。如果线程数目 可以在属性文件中配置,那么使它成为
- 正则表达式大全
yang852220741
html编程正则表达式
今天向大家分享正则表达式大全,它可以大提高你的工作效率
正则表达式也可以被当作是一门语言,当你学习一门新的编程语言的时候,他们是一个小的子语言。初看时觉得它没有任何的意义,但是很多时候,你不得不阅读一些教程,或文章来理解这些简单的描述模式。
一、校验数字的表达式
数字:^[0-9]*$
n位的数字:^\d{n}$
至少n位的数字:^\d{n,}$
m-n位的数字:^\d{m,n}$