一、HTTPS介绍:
超文本传输安全协议(Hypertext Transfer Protocol Secure)缩写:HTTPS是一种通过计算机网络进行安全通信的传输协议。HTTPS经由HTTP进行通信,但利用SSL/TLS来加密数据包。HTTPS开发的主要目的,是提供对网站服务器的身份认证,保护交换数据的隐私与完整性。这个协议由网景公司(Netscape)在1994年首次提出,随后扩展到互联网上。
历史上,HTTPS连接经常用于万维网上的交易支付和企业信息系统中敏感信息的传输。在2000年代晚期和2010年代早期,HTTPS开始广泛使用于保护所有类型网站上的网页真实性,保护账户和保持用户通信,身份和网络浏览的私密性。
二、主要思想:
HTTPS的主要思想是在不安全的网络上创建一安全信道,并可在使用适当的加密包和服务器证书可被验证且可被信任时,对窃听和中间人攻击提供合理防护。
HTTPS的信任继承基于预先安装在浏览器中的证书颁发机构(如Symantec、Comodo、GoDaddy和GlobalSign等)(意即“我信任证书颁发机构告诉我应该信任的”)。因此,一个到某网站的HTTPS连接可被信任,当且且当:
- 用户相信他们的浏览器正确实现了HTTPS且安装了正确的证书颁发机构;
- 用户相信证书颁发机构仅信任合法的网站;
- 被访问的网站提供了一个有效的证书,意即,它是由一个被信任的证书颁发机构签发的(大部分浏览器会对无效的证书发出警告);
- 该证书正确地验证了被访问的网站(如,访问https://example.com 时收到了给 example.com 而不是其他组织的证书);
- 或者互联网上相关节点是值得信任的,或者用户相信本协议的加密层(TLS或SSL)不能被窃听者破坏。
以上来自维基百科
三、实验:
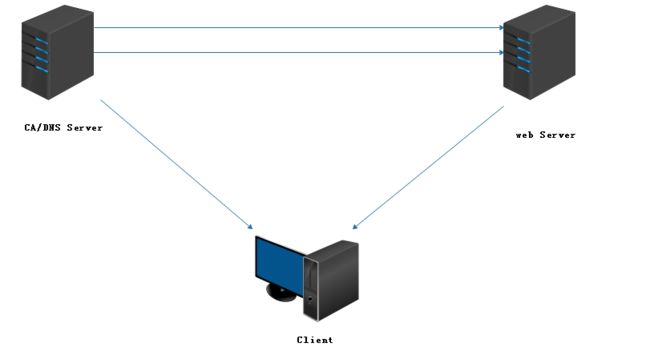
环境拓扑:
SSL 会话的简化过程
(1) 客户端发送可供选择的加密方式,并向服务器请求证书
(2) 服务器端发送证书以及选定的加密方式给客户端
(3) 客户端取得证书并进行证书验证
如果信任给其发证书的CA
(a) 验证证书来源的合法性;用CA 的公钥解密证书上数字签名
(b) 验证证书的内容的合法性:完整性验证
(c) 检查证书的有效期限
(d) 检查证书是否被吊销
(e) 证书中拥有者的名字,与访问的目标主机要一致
(4) 客户端生成临时会话密钥(对称密钥),并使用服务器端的公钥加密
此数据发送给服务器,完成密钥交换
(5) 服务用此密钥加密用户请求的资源,响应给客户端
注意:SSL 是基于IP 地址实现, 单IP 的主机仅可以使用一个https 虚拟主机
DNS解析详见DNS之正向反向解析(二)
CA服务端创建私有CA证书并颁发
(1)生成密钥
[root@CentOS7 /etc/pki/CA]#(umask 066;openssl genrsa -out private/cakey.pem 4096)
Generating RSA private key, 4096 bit long modulus
..................................................................................................................................................................................++
....++
e is 65537 (0x10001)
[root@CentOS7 /etc/pki/CA]#tree
.
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem
4 directories, 1 file
命令回顾解释:
( )表示将会在当前shell中新建一个子shell,将( )中的命令放在该子shell中执行,执行完毕后关闭shell并回到当前shell
由于要对生成的cakey.pem文件设置合适权限,可以使用umask修改文件的默认权限设置。为了不影响当前shell的默认权限设置,使用( )将这些命令放到子shell中执行
genrsa:指定使用rsa算法生成密钥
-out:指定生成的私钥的存放位置(注意:该存放位置是在配置文件中默认定义的了,路径和文件名不能随意修改)
2048:指定生成一个2048位的密钥
(2)自签证书
[root@CentOS7 /etc/pki/CA]#openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:huizhou
Organization Name (eg, company) [Default Company Ltd]:cnnavy.cn
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:ca.cnnavy.cn
Email Address []:
[root@CentOS7 /etc/pki/CA]#openssl x509 -in cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 17929557096528780391 (0xf8d2952f36ae9c67)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=guangdong, L=huizhou, O=cnnavy.cn, OU=opt, CN=ca.cnnavy.cn
Validity
Not Before: Sep 29 07:25:14 2017 GMT
Not After : Sep 27 07:25:14 2027 GMT
Subject: C=CN, ST=guangdong, L=huizhou, O=cnnavy.cn, OU=opt, CN=ca.cnnavy.cn
命令回顾解释:
req:生成证书签署请求
-news:新请求
-key /path/to/keyfile:指定私钥文件(req命令能根据私钥自动抽取出公钥)
-out /path/to/somefile:(路径和文件名不用随意修改!)
-509:专门用于生成自签署证书
-days n:有效天数(一般和-x509一起使用才有意义)
(3)初始化工作环境(只有第一次创建CA时,才需要初始化工作环境)
[root@CentOS7 /etc/pki/CA]#touch index.txt
[root@CentOS7 /etc/pki/CA]#echo 00 > serial #指定序列号从那个数字开始
[root@CentOS7 /etc/pki/CA]#tree
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
├── private
│ └── cakey.pem
└── serial
4 directories, 4 files
Web Server节点申请证书
(1)为私钥请求证书创建单独目录便于存放
[root@CentOS6 ~]#cd /etc/httpd/conf.d/
[root@CentOS6 /etc/httpd/conf.d]#mkdir ssl
[root@CentOS6 /etc/httpd/conf.d]#pwd
/etc/httpd/conf.d
a、生成密钥对儿
[root@CentOS6 /etc/httpd/conf.d/ssl]#(umask 066;openssl genrsa -out httpd.key 2014)
Generating RSA private key, 2014 bit long modulus
...............................................................+++
...........................................+++
e is 65537 (0x10001)
[root@CentOS6 /etc/httpd/conf.d/ssl]#ls
httpd.key
b、生成证书签署请求
[root@CentOS6 /etc/httpd/conf.d/ssl]#openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:huizhou
Organization Name (eg, company) [Default Company Ltd]:cnnavy.cn
Organizational Unit Name (eg, section) []:opt
Common Name (eg, your name or your server's hostname) []:*.a.com #*泛域名解析
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@CentOS6 /etc/httpd/conf.d/ssl]#ll
total 8
-rw-r--r-- 1 root root 989 Sep 29 04:13 httpd.csr
-rw------- 1 root root 1639 Sep 29 04:12 httpd.key
-csr :证书签署请求,一般都是这样的后缀
c、将签署请求文件发送给CA服务
[root@CentOS6 /etc/httpd/conf.d/ssl]#scp httpd.csr 192.168.1.107:/etc/pki/CA/
(2)CA签署证书
[root@CentOS7 /etc/pki/CA]#openssl ca -in httpd.csr -out httpd.crt -days 300
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 0 (0x0)
Validity
Not Before: Sep 29 07:47:28 2017 GMT
Not After : Jul 26 07:47:28 2018 GMT
Subject:
countryName = CN #国家
stateOrProvinceName = guangdong #省份名
organizationName = cnnavy.cn #公司名
organizationalUnitName = opt #部门名
commonName = *.a.com #主机名
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
8C:B3:FE:24:51:29:CD:0E:14:57:2A:0A:25:79:C8:3A:3C:61:78:76
X509v3 Authority Key Identifier:
keyid:14:04:18:32:14:50:A0:C9:01:32:D1:42:A0:9B:C8:58:7D:69:63:26
Certificate is to be certified until Jul 26 07:47:28 2018 GMT (300 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
将签署好的证书发回给Web Server申请者
[root@CentOS7 /etc/pki/CA]#scp certs/httpd.crt 192.168.1.106:/etc/httpd/conf.d/ssl/
[root@CentOS7 /etc/pki/CA]#scp cacert.pem 192.168.1.106:/etc/httpd/conf.d/ssl/
Web Server端配置httpd 支持使用ssl,及使用证书
(1)安装 mod_ssl
[root@CentOS6 /etc/httpd/conf.d/ssl]#yum -y install mod_ssl
[root@CentOS6 /etc/httpd/conf.d/ssl]#ll
total 16
-rw-r--r-- 1 root root 2025 Sep 29 04:47 cacert.pem
-rw-r--r-- 1 root root 5674 Sep 29 04:28 httpd.crt
-rw-r--r-- 1 root root 989 Sep 29 04:13 httpd.csr
-rw------- 1 root root 1639 Sep 29 04:12 httpd.key
(2)修改"/etc/httpd/conf.d/ssl.conf" 配置文件并重新加载httpd服务
100 # Server Certificate:
101 # Point SSLCertificateFile at a PEM encoded certificate. If
102 # the certificate is encrypted, then you will be prompted for a
103 # pass phrase. Note that a kill -HUP will prompt again. A new
104 # certificate can be generated using the genkey(1) command.
105 SSLCertificateFile /etc/httpd/conf.d/ssl/httpd.crt #修改为证书保存路径
107 # Server Private Key:
108 # If the key is not combined with the certificate, use this
109 # directive to point at the key file. Keep in mind that if
110 # you've both a RSA and a DSA private key you can configure
111 # both in parallel (to also allow the use of DSA ciphers, etc.)
112 SSLCertificateKeyFile /etc/httpd/conf.d/ssl/httpd.key #修改为私有密钥保存路径
123 # Certificate Authority (CA):
124 # Set the CA certificate verification path where to find CA
125 # certificates for client authentication or alternatively one
126 # huge file containing all of them (file must be PEM encoded)
127 SSLCACertificateFile /etc/httpd/conf.d/ssl/cacert.pem #修改CA证书保存路径
[root@CentOS6 /etc/httpd/conf.d/ssl]#service httpd reload Reloading httpd:
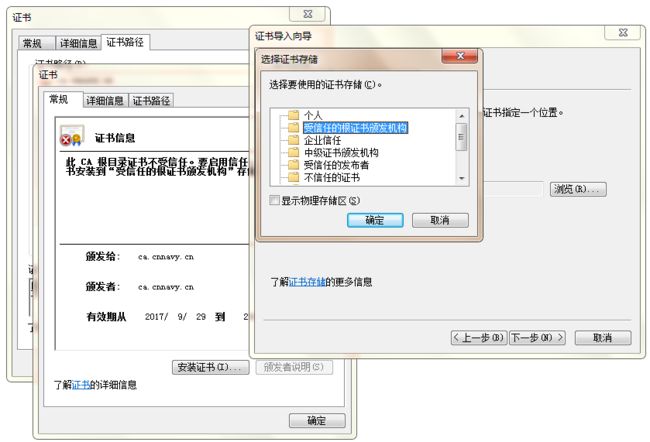
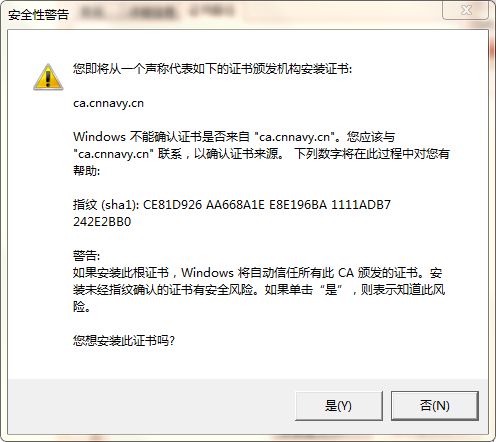
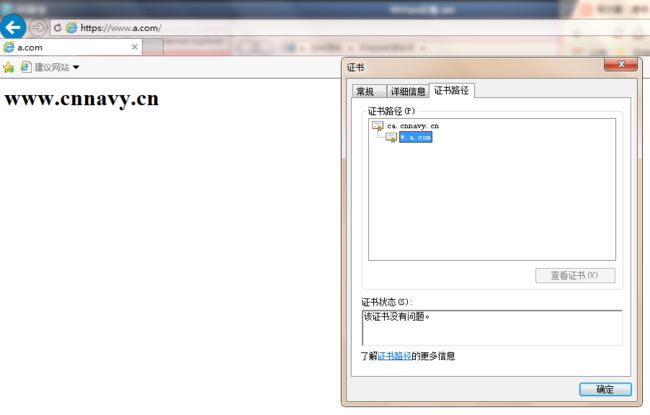
Client导入证书
设置http 重定向https,将http请求直接转发至https的URL
重定向status 状态:
- 永久(Permanent)返回永久重定向状态 (301) 表明资源已永久移动
Redirect Permanent / https://www.cnnavy.cn/ - 临时(Temp)返回一个临时重定向状态(302)。默认设置
Redirect temp / https://www.cnnavy.cn/
HSTS重定向https访问
- HSTS:HTTP Strict Transport Security
服务器端配置支持HSTS 后,会在给浏览器返回的HTTP 首部中携带
HSTS 字段。浏览器获取到该信息后,会将所有HTTP 访问请求在内部做307 跳转到HTTPS 。而无需任何网络过程。 - HSTS preload list
Chrome 浏览器中的HSTS 预载入列表,在该列表中的网站,使用Chrome 浏览器访问时,会自动转换成HTTPS 。Firefox 、Safari、 Edge 浏览器也会采用这个列表。
[root@CentOS6 /var/log/httpd]#vim /etc/httpd/conf.d/test.conf
1 Header always set Strict-Transport-Security "max-age=15768000"
2 RewriteEngine on
3 RewriteRule ^(/.*)$ https://%{HTTP_HOST}$1 [REDIRECT=301]