NAT+ACL+ASA 实验全网互通
一概述:
1,地址转换:
动态NAT:多对多的映射(将一组ip地址转换为指定地址池中的ip地址
动态PAT:一对多的映射(地址转换与接口转换)
静态NAT:一对一的固定ip转换(可用于双向通信)
静态PAT:一对一的端口号转换(与静态NAT类似)
静态PAT语法:{static (dmz,outside) tcp(udp) 外部全局地址 接口(http,smtp等) 内部本地地址 本地端口 netmask}
2,启用NAT控制:
总结:在启用NAT控制时,NAT规则是必需的
在禁用NAT控制时,NAT规则是并不是必需的
3,NAT豁免:
NAT豁免的应用背景
当启用NAT控制时,每个发起的连接都需要一个相应的NAT规则
在某些应用场合(例如配置×××)需要绕过NAT规则
NAT豁免允许双向通信
NAT豁免的配置步骤
定义一个ACL,用于指定需要绕过NAT规则的流量
配置NAT命令
asa(config)# nat (interface_name) 0 access-list acl_name
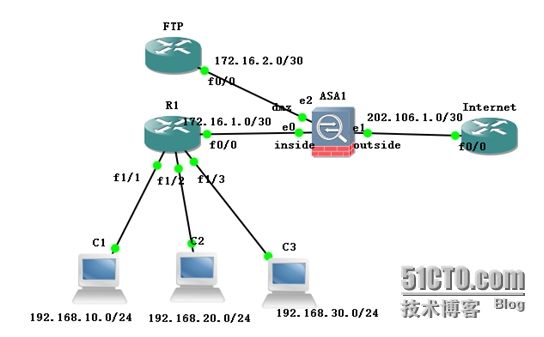
二,实验拓扑图:
要求:
1,R1、R2、R3使用acl+NAT豁免ping通FTP
2,R1、R2、R3使用acl+动态NAT转换成公网ping通internet
3,internet与FTP服务器之间acl+静态NAT能互通
4,C1能远程ASA防火墙
三,步骤:
1,各个设备配ip
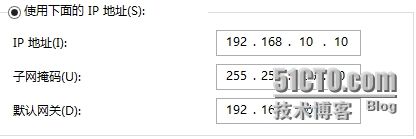
PC机配置:
R1配置:
R1#conf t
R1(config)#int f1/1
R1(config-if)#no switchport
R1(config-if)#ip add 192.168.10.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f1/2
R1(config-if)#no switchport
R1(config-if)#ip add 192.168.20.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f1/3
R1(config-if)#no switchport
R1(config-if)#ip add 192.168.30.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f0/0
R1(config-if)#ip add 172.16.1.1 255.255.255.252
R1(config-if)#no shut
R1(config)#ip route 0.0.0.0 0.0.0.0 172.16.1.2
ciscoasa配置:
ciscoasa# conf t
ciscoasa(config)# int e0/0
ciscoasa(config-if)# nameif inside
ciscoasa(config-if)# ip add 172.16.1.2 255.255.255.252
ciscoasa(config-if)# no shut
ciscoasa(config-if)# int e0/1
ciscoasa(config-if)# nameif outside
ciscoasa(config-if)# ip add 202.106.1.1 255.255.255.252
ciscoasa(config-if)# no shut
ciscoasa(config-if)# int e0/2
ciscoasa(config-if)# nameif dmz
ciscoasa(config-if)# security-level 50
ciscoasa(config-if)# ip add 172.16.2.1 255.255.255.252
ciscoasa(config-if)# no shut
Internet配置:
Internet(config)#int f0/0
Internet(config-if)#ip add 202.106.1.2 255.255.255.252
Internet(config-if)#no shut
FTP配置:
FTP#conf t
FTP(config)#int f0/0
FTP(config-if)#ip add 172.16.2.2 255.255.255.252
FTP(config-if)#no shut
FTP(config)#ip route 0.0.0.0 0.0.0.0 172.16.2.1
2,acl+NAT豁免配置:
ciscoasa配置:
ciscoasa(config)# nat-control
ciscoasa(config)# nat (inside) 1 0 0 //为Inside区域内的所有网段拿地址,进行地址转换
ciscoasa(config)# global (dmz) 1 202.106.2.1-202.106.2.100 netmask 255.255.255.0//为dmz区域定义全局地址池
ciscoasa(config)# access-list nonat extended permit ip any 172.16.2.0 255.255.255.252//允许公司内部(192.168.0.0/24)访问FTP服务器(172.16.2.0/30)
ciscoasa(config)# nat (inside) 0 access-list nonat //公司内部(192.168.0.0/24)访问FTP服务器(172.16.2.0/30)不进行NAT转换,也叫NAT豁免
ciscoasa(config)# access-list 10 extended permit icmp any any
ciscoasa(config)# access-group 10 in interface dmz
ciscoasa(config)# route inside 0 0 172.16.1.1//从inside口路由到任何地
FTP配置:
FTP(config)#ip route 202.106.2.0 255.255.255.0 172.16.2.1
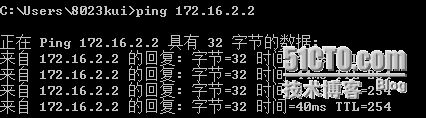
验证:
FTP#
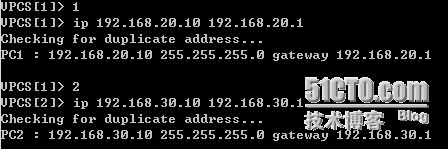
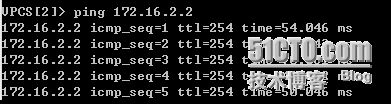
*Mar 1 01:58:47.223: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.20.10
*Mar 1 01:58:48.279: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.20.10
FTP#
*Mar 1 01:58:13.219: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.30.10
*Mar 1 01:58:14.275: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.30.10
FTP#
*Mar 1 02:00:50.139: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.10.10
*Mar 1 02:00:51.139: ICMP: echo reply sent, src 172.16.2.2, dst 192.168.10.10
(acl+NAT豁免完成)
3,acl+动态NAT转换成公网配置:
ciscoasa配置:
ciscoasa(config)# global (outside) 1 202.106.3.1-202.106.3.100 netmask 255.255.255.0
ciscoasa(config)# access-group 10 in interface outside
Internet配置:
Internet(config)#ip route 202.106.3.0 255.255.255.0 202.106.1.1
验证:
Internet#
*Mar 1 00:31:53.055: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.1
*Mar 1 00:31:54.091: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.1
Internet#
*Mar 1 00:32:56.379: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.2
*Mar 1 00:32:57.427: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.2
Internet#
*Mar 1 00:33:57.091: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.3
*Mar 1 00:33:58.095: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.3
(acl+动态NAT转换成公网完成)
4,internet与FTP服务器之间acl+静态NAT配置:
ciscoasa配置:
ciscoasa(config)# static (dmz,outside) 202.106.3.10 172.16.2.2 //FTP服务器172.16.2.2地址转换成公网地址202.106.3.10
验证:
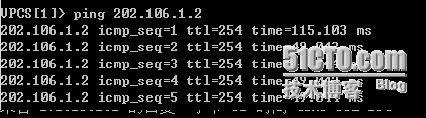
FTP#ping 202.106.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 202.106.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/40/72 ms
Internet(config)#
*Mar 1 01:41:16.823: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.10
*Mar 1 01:41:16.879: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.10
*Mar 1 01:41:16.907: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.10
*Mar 1 01:41:16.927: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.10
*Mar 1 01:41:16.947: ICMP: echo reply sent, src 202.106.1.2, dst 202.106.3.10
Internet#ping 202.106.2.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 202.106.2.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/41/84 ms
FTP#
*Mar 1 01:41:50.951: ICMP: echo reply sent, src 172.16.2.2, dst 202.106.1.2
*Mar 1 01:41:51.039: ICMP: echo reply sent, src 172.16.2.2, dst 202.106.1.2
*Mar 1 01:41:51.083: ICMP: echo reply sent, src 172.16.2.2, dst 202.106.1.2
*Mar 1 01:41:51.111: ICMP: echo reply sent, src 172.16.2.2, dst 202.106.1.2
*Mar 1 01:41:51.131: ICMP: echo reply sent, src 172.16.2.2, dst 202.106.1.2
(internet与FTP服务器之间acl+静态NAT能互通)
5,ssh远程ASA防火墙配置:
ciscoasa配置:
ciscoasa(config)# hostname ASA //更改名字
ASA(config)# enable password abc//用户模式进入特权模式的密码
ASA(config)# domain-name benet.com//更改密码
ASA(config)# crypto key generate rsa modulus 1024//根据防火墙名字与域名生成RSA密钥对
ASA(config)# username asa802 password abc123 privilege 15//更改用户名与密码,用户名默认为pix,并设置优先级为15
ASA(config)# aaa authentication ssh console LOCAL//控制端认证ssh远程服务
ASA(config)# ssh 192.168.10.0 255.255.255.0 inside//内网允许远程的主机
ASA(config)# ssh 0 0 outside //允许所有到外网
ASA(config)# ssh timeout 30//空闲超时时间
ASA(config)# ssh version 2//ssh支持的版本
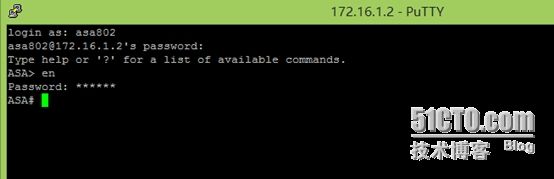
验证:
(C1使用ssh远程ASA防火墙)
ASA(config)# show xlate detail //查看xlate表,能看见NAT转换条目
7 in use, 7 most used
Flags: D - DNS, d - dump, I - identity, i - dynamic, n - no random,
r - portmap, s - static
NAT from dmz:172.16.2.2 to outside:202.106.3.10 flags s
NAT from inside:192.168.10.10 to outside:202.106.3.3 flags i
NAT from inside:192.168.10.10 to dmz:202.106.2.3 flags i
NAT from inside:192.168.30.10 to outside:202.106.3.2 flags i
NAT from inside:192.168.30.10 to dmz:202.106.2.1 flags i
NAT from inside:192.168.20.10 to outside:202.106.3.1 flags i
NAT from inside:192.168.20.10 to dmz:202.106.2.2 flags i