入门论文阅读
入门论文阅读
- Trick or Heat? Manipulating Critical Temperature-Based Control Systems Using Rectification Attacks(10.1145/3319535.3354195)
- Summary
- Note
- [28]The infant incubator in the neonatal intensive care unit:unresolved issues and future developments
- [29]Truth will out:Departure-based process-level detection of stealthy attacks on control systems.
- Summary
- Note
- [30]Servocontrol: Incubator and radiant warmer
- [31]A Note on Grounded Thermocouple Circuits
- Summary
- [32]Protecting Instrumentation Amplifiers
- [33]EFFECTS OF INTENTIONAL ELECTROMAGNETIC INTERFERENCE ON ANALOG TO DIGITAL CONVERTER MEASUREMENTS OF SENSOR OUTPUTS AND GENERAL PURPOSE INPUT OUTPUT PINS
- [34]Does the incubator control mode influence outcomes of low-birth-weight neonates during the first days of life and at hospital discharge?
- [35]Susceptibility of sensor networks to intentional electromagnetic interference
- [36]Two Ways to Measure Temperature Using Thermocouples Feature Simplicity, Accuracy, and Flexibility
- [37]Unlocking the Access to the Effects induced by IEMI on a Civilian UAV
- [38]Practical 3D printers: The science and art of 3D printing.
- [39]Negative Temperature Coefficient Resistance (NTCR) Ceramic Thermistors: An Industrial Perspective
- [40]An Analog Front End Based on Chopped Signals Highly Immune to RFI
- Summary
- Note
- [41]A Sensor Signal Amplifier Resilient to EMI
- [42]A Confidence-Based Approach to the Self-Validation, Fusion and Reconstruction of Quasi-Redundant Sensor Data
- [43]Risks of trusting the physics of sensors
- [44]A statistical survey of common-mode noise
- [46]Vaccine storage practices in primary care physician offices: Assessment and intervention
- [47]SoK: Taxonomy and Challenges of Out-of-Band Signal Injection Attacks and Defenses
- [48]A Framework for Evaluating Security in the Presence of Signal Injection Attacks
- [49]Attack-Resilient Sensor Fusion for Safety-Critical Cyber-Physical Systems.
- [50]Redundant Sensor Calibration and Estimation for Monitoring and Control of Nuclear Power Plants.
- [51]Mulle: a minimal sensor networking device: implementation and manufacturing challenges.
- [52]Hyperthermia, inflammation, and perinatal brain injury.
- [53]Remote and Silent Voice Command Injection on a Smartphone through Conducted IEMI - Threats of Smart IEMI for Information Security
- [54]Practical design techniques for sensor signal conditioning
- [56]Multisensor data fusion: A review of the state-of-the-art
- [57]A designer’s guide to instrumentation amplifiers.
- [58]Distributed temperature control system based on multi-sensor data fusion.
Trick or Heat? Manipulating Critical Temperature-Based Control Systems Using Rectification Attacks(10.1145/3319535.3354195)
Summary
This paper is talking about attcking temperatur with EMI.They found EMI of different frequence caused different DC offset, just like temperatur changes.
They gave several ways to defend against this attack.One of them is called Hardware Anomaly Detection System, in fact they build a receiver circuit about the frequence they used.
Note
They only used Analog Temperature Sensors for test, and I think tahe DC offset can occur because the circuit constitutes the receiving antenna.So the effect of this method on the Digital Thermometer such as DS18B20 sensor makes me curious.
There is a test call EMC or Electromagnetic compatibility.Obviously none of the products attacked in the paper could pass EMC.
[1]-[27]
They are not paper.
[28]The infant incubator in the neonatal intensive care unit:unresolved issues and future developments
It’s talking about neonatal intensive care unit.
[29]Truth will out:Departure-based process-level detection of stealthy attacks on control systems.
Summary
In this paper, they development a a light-weight and fast model-free Process-Aware Stealthy-Attack Detection mechanismc alled pasad.Its basic principle is monitoring sensors in ICS in real time.
Note
I think this approach is similar to machine learning.
[30]Servocontrol: Incubator and radiant warmer
It’s a handbook, talking about neonatology.
[31]A Note on Grounded Thermocouple Circuits
Summary
This paper talks about how to groubded properly.
[32]Protecting Instrumentation Amplifiers
It’s talking about protection circuits.
[33]EFFECTS OF INTENTIONAL ELECTROMAGNETIC INTERFERENCE ON ANALOG TO DIGITAL CONVERTER MEASUREMENTS OF SENSOR OUTPUTS AND GENERAL PURPOSE INPUT OUTPUT PINS
It’s a thesis submitted in partial fulfillment of the requirements for the degree. It studies interference when EMI sources directly connected to circuit.
[34]Does the incubator control mode influence outcomes of low-birth-weight neonates during the first days of life and at hospital discharge?
It shows two different control mode in NTE.
[35]Susceptibility of sensor networks to intentional electromagnetic interference
Author attacked the sensor with EMI around 2.4Ghz at high energy.
[36]Two Ways to Measure Temperature Using Thermocouples Feature Simplicity, Accuracy, and Flexibility
Two Ways to Measure Temperature Using Thermocouples.
[37]Unlocking the Access to the Effects induced by IEMI on a Civilian UAV
They proved that IEMI can interfered sensors on UAVs.
[38]Practical 3D printers: The science and art of 3D printing.
It’s a book aboud 3d printing.
[39]Negative Temperature Coefficient Resistance (NTCR) Ceramic Thermistors: An Industrial Perspective
Showing NTCR is common.
[40]An Analog Front End Based on Chopped Signals Highly Immune to RFI
Summary
This paper shows that the immunity to RFI of analog circuits based on feedback opamps is significantly improved if input signals are chopped before being amplified.
Note
This means if the input signal is chopped before being amplified, the time-varying component at the amplifier output is not concerned by the demodulated RFI.We can use this method to defend attacks.
[41]A Sensor Signal Amplifier Resilient to EMI
This paper illustrates the impact of EMI on amplifiers from a micro perspective.
[42]A Confidence-Based Approach to the Self-Validation, Fusion and Reconstruction of Quasi-Redundant Sensor Data
An algorithm based on confidence whice can self-Validation, fusion and reconstruction of Quasi-Redundant sensor data.Can this work done by LTSM?
[43]Risks of trusting the physics of sensors
Sensors are vulnerable to spoofing by transduction attacks.Didn’t say much about technology, just some examples.
[44]A statistical survey of common-mode noise
A application Note. Analyzed the noise of some typical applications。
[46]Vaccine storage practices in primary care physician offices: Assessment and intervention
Abour preventive medicine.Tempure is import.
[47]SoK: Taxonomy and Challenges of Out-of-Band Signal Injection Attacks and Defenses
Gived some examples about Out-of-Band signal injection attacks.The attack methods used are acoustic, conducted, electromagnetic, and optical.
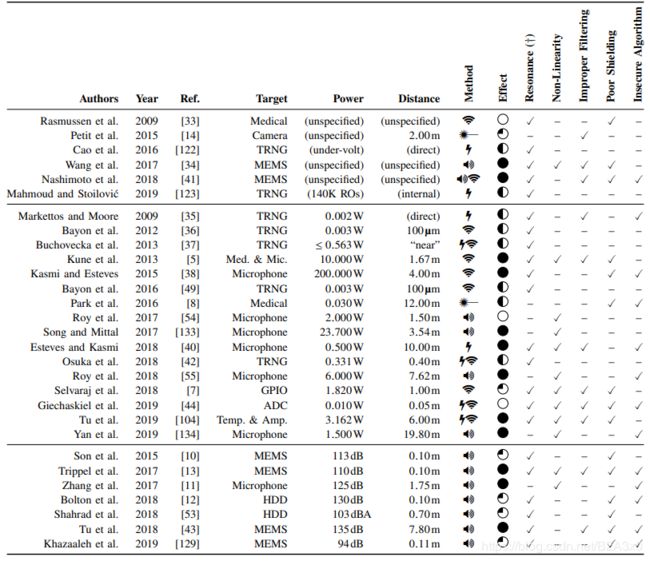
[48]A Framework for Evaluating Security in the Presence of Signal Injection Attacks
Gives a approch of evaluating the susceptibility of systems against signal injection attacks
[49]Attack-Resilient Sensor Fusion for Safety-Critical Cyber-Physical Systems.
A approch using mutli-sencor can defensive attack
[50]Redundant Sensor Calibration and Estimation for Monitoring and Control of Nuclear Power Plants.
This paper presents a calibration and estimation filter for redundancy management of sensor data and analytical measurements.
[51]Mulle: a minimal sensor networking device: implementation and manufacturing challenges.
Analyzed Network connected sensors
[52]Hyperthermia, inflammation, and perinatal brain injury.
A medical paper
[53]Remote and Silent Voice Command Injection on a Smartphone through Conducted IEMI - Threats of Smart IEMI for Information Security
EMI again.But in thia paper, they used USB cable for injection attack.I think this approch more easy than optical.
[54]Practical design techniques for sensor signal conditioning
Sensor signal conditioning design tutorial.
[56]Multisensor data fusion: A review of the state-of-the-art
A review of the state-of-the-art.Multi-sensor.
[57]A designer’s guide to instrumentation amplifiers.
A designer’s guide form ADI company.
[58]Distributed temperature control system based on multi-sensor data fusion.
Another data fusion algorithm.Under attarcking fusion will be difficult or wrong.