hyperledger fabric1.0动态添加peer节点之fabric-ca应用
前言:了解过的应该都知道fabric1.0中e2e_cli实例,在启动时应用的证书及创世块、通道配置创世块、锚节点配置文件是由工具生成,作为动态添加peer节点不建议使用工具和fabric-ca混合生成证书文件进行互相认证,这里我们使用fabric-ca生成(同工具一样的)配置文件,并额外生成动态添加peer的证书文件。动态添加peer是基于e2e_cli实例进行的,所以前提是大家的e2e_cli要可以运行起来。
一、启动fabric-ca服务端
找一个空目录作为fabric-ca服务端目录,然后运行启动命令。
#-b提供注册用户的名称和密码
#可以直接执行fabric-ca-server start,系统默认会执行一次init操作
$ fabric-ca-server init -b admin:adminpw
$ fabric-ca-server start -b admin:adminpw
#推荐使用以下命令启动服务
#start命令启动时会创建默认组织
#默认创建的组织不是我们需要的,对组织操作用以下命令启动
$ fabric-ca-server start -b admin:adminpw --cfg.affiliations.allowremove --cfg.identities.allowremove &
# fabric-ca服务中断,需要重新连接上次记录时可以尝试如下方法(之前start或init生成的文件)
$ fabric-ca-server start --ca.certfile /path/path --ca.keyfile /path/path -b admin:adminpw -d成功执行会生成自签名的ca-cert.pen根证书,私钥、默认配置文件fabric-ca-server-conifg.yaml及SQLite3数据文件。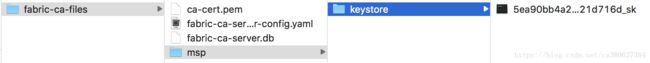 通过以下命令可查看SQLite3
通过以下命令可查看SQLite3
$ sqlite3 fabric-ca-server.db
$ .tables
# users用户信息
# certificates证书信息
# affiliations组织信息
$ select * from users;二、生成fabric-ca admin凭证
注:如果执行以下命令,提示目录不存在的情况下,请自行创建,如
#执行此命令失败,目录不存在,则先进行目录创建
$ fabric-ca-client enroll -u http://admin:adminpw@localhost:7054 -H `pwd`/fabric-ca-files/admin
#创建所需目录
$ mkdir -p `pwd`/fabric-ca-files/admin继续正文:
#随意定义位置
$ cd $GOPATH/bin
$ mkdir -p fabric-ca-files
#设置fabric-ca环境变量
$ export FABRIC_CA_CLIENT_HOME=`pwd`/fabric-ca-files/admin
#登记管理员用户
$ fabric-ca-client enroll -u http://admin:adminpw@localhost:7054 -H `pwd`/fabric-ca-files/admin
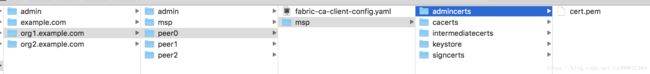
这时目录结构应该为这样,包含管理员的证书和私钥等信息
三、创建联盟
#查看目前联盟信息
#指定admin查看
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation list结果为fabric-ca-server生成的默认联盟。我们删除掉,并创建所需的e2e_cli联盟
#删除联盟org1 org2
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation remove --force org1
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation remove --force org1
#添加所需联盟
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation add com
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation add com.example
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation add com.example.org1
$ fabric-ca-client -H `pwd`/fabric-ca-files/admin affiliation add com.example.org2四、为各联盟创建msp
#使用getcacert得到msp目录中只有CA证书
#tls在配置文件中默认设置为false,随后也会禁用tls
$ fabric-ca-client getcacert -M `pwd`/fabric-ca-files/example.com/msp
$ fabric-ca-client getcacert -M `pwd`/fabric-ca-files/org1.example.com/msp
$ fabric-ca-client getcacert -M `pwd`/fabric-ca-files/org2.example.com/msp现在目录结构为
注:example为crypto-config中ordererOrganizations中的内容, org1.example.com,org2.example.com为crypto-config中peerOrganizations中的内容。
五、创建各组织中的admin用户
# --id.name 注册名称
# --id.affiliation 对应的隶属关系
# --id.type client 所属类型
# --id.secret 设置的密码,不设置会随机生成
#注册example.com中的Admin管理员用户
$ fabric-ca-client register --id.name [email protected] --id.type client --id.affiliation "com.example" --id.secret test123 --id.attrs '"hf.Registrar.Roles=client,orderer,peer,user","hf.Registrar.DelegateRoles=client,orderer,peer,user",hf.Registrar.Attributes=*,hf.GenCRL=true,hf.Revoker=true,hf.AffiliationMgr=true,hf.IntermediateCA=true,role=admin:ecert'
#登记example.com中的Admin管理员用户
$ fabric-ca-client enroll -u http://[email protected]:test123@localhost:7054 -H `pwd`/fabric-ca-files/example.com/admin
#获取管理权限
#将[email protected]的证书复制到example.com/msp/admincerts/
$ mkdir fabric-ca-files/example.com/msp/admincerts/
$ cp fabric-ca-files/example.com/admin/msp/signcerts/cert.pem fabric-ca-files/example.com/msp/admincerts/
#注册org1.example.com中的[email protected]管理员用户
$ fabric-ca-client register --id.name [email protected] --id.type client --id.affiliation "com.example.org1" --id.secret test123 --id.attrs '"hf.Registrar.Roles=client,orderer,peer,user","hf.Registrar.DelegateRoles=client,orderer,peer,user",hf.Registrar.Attributes=*,hf.GenCRL=true,hf.Revoker=true,hf.AffiliationMgr=true,hf.IntermediateCA=true,role=admin:ecert'
#登记org1.example.com中的[email protected]管理员用户
$ fabric-ca-client enroll -u http://[email protected]:test123@localhost:7054 -H `pwd`/fabric-ca-files/org1.example.com/admin
#获取管理权限
#将[email protected]的证书复制到org1.example.com的msp/admincerts中
$ mkdir fabric-ca-files/org1.example.com/msp/admincerts/
$ cp fabric-ca-files/org1.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org1.example.com/msp/admincerts/
#将[email protected]中创建admincerts目录并复制管理员签名证书singcerts/cert.pem
$ mkdir fabric-ca-files/org1.example.com/admin/msp/admincerts/
$ cp fabric-ca-files/org1.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org1.example.com/admin/msp/admincerts/
#注册org2.example.com中的[email protected]管理员用户
$ fabric-ca-client register --id.name [email protected] --id.type client --id.affiliation "com.example.org2" --id.secret test123 --id.attrs '"hf.Registrar.Roles=client,orderer,peer,user","hf.Registrar.DelegateRoles=client,orderer,peer,user",hf.Registrar.Attributes=*,hf.GenCRL=true,hf.Revoker=true,hf.AffiliationMgr=true,hf.IntermediateCA=true,role=admin:ecert'
#登记org2.example.com中的[email protected]管理员用户
$ fabric-ca-client enroll -u http://[email protected]:test123@localhost:7054 -H `pwd`/fabric-ca-files/org2.example.com/admin
#获取管理权
$ mkdir fabric-ca-files/org2.example.com/msp/admincerts/
$ cp fabric-ca-files/org2.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org2.example.com/msp/admincerts/
#将[email protected]中创建admincerts目录并复制管理员签名证书singcerts/cert.pem
$ mkdir fabric-ca-files/org2.example.com/admin/msp/admincerts/
$ cp fabric-ca-files/org2.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org2.example.com/admin/msp/admincerts/
#登记完成后就可以使用对应的用户查看所拥有的权限
fabric-ca-client affiliation list -H `pwd`/fabric-ca-files/example.com/admin
fabric-ca-client affiliation list -H `pwd`/fabric-ca-files/org1.example.com/admin
fabric-ca-client affiliation list -H `pwd`/fabric-ca-files/org2.example.com/admin六、使用各管理员用户创建其它用户
#使用[email protected]注册并登记账号orderer.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/example.com/admin --id.secret=test123 --id.name orderer.example.com --id.type orderer --id.affiliation "com.example" --id.maxenrollments "0" --id.attrs 'role=orderer:ecert'
$ mkdir ./fabric-ca-files/example.com/orderer
$ fabric-ca-client enroll -u http://orderer.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/example.com/orderer
#获取管理员签名证书
$ mkdir fabric-ca-files/example.com/orderer/msp/admincerts
$ cp fabric-ca-files/example.com/admin/msp/signcerts/cert.pem fabric-ca-files/example.com/orderer/msp/admincerts/
#使用[email protected]注册并登记账号peer0.org1.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/org1.example.com/admin/ --id.secret=test123 --id.name peer0.org1.example.com --id.type peer --id.affiliation "com.example.org1" --id.maxenrollments "0" --id.attrs 'role=peer:ecert'
$ mkdir ./fabric-ca-files/org1.example.com/peer0
$ fabric-ca-client enroll -u http://peer0.org1.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/org1.example.com/peer0
#获取管理员签名证书
$ mkdir fabric-ca-files/org1.example.com/peer0/msp/admincerts
$ cp fabric-ca-files/org1.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org1.example.com/peer0/msp/admincerts/
#使用[email protected]注册并登记账号peer1.org1.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/org1.example.com/admin --id.secret=test123 --id.name peer1.org1.example.com --id.type peer --id.affiliation "com.example.org1" --id.maxenrollments "0" --id.attrs 'role=peer:ecert'
$ mkdir ./fabric-ca-files/org1.example.com/peer1
$ fabric-ca-client enroll -u http://peer1.org1.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/org1.example.com/peer1
#获取管理员签名证书
$ mkdir fabric-ca-files/org1.example.com/peer1/msp/admincerts
$ cp fabric-ca-files/org1.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org1.example.com/peer1/msp/admincerts/
#使用[email protected]注册并登记账号peer0.org2.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/org2.example.com/admin --id.secret=test123 --id.name peer0.org2.example.com --id.type peer --id.affiliation "com.example.org2" --id.maxenrollments "0" --id.attrs 'role=peer:ecert'
$ mkdir ./fabric-ca-files/org2.example.com/peer0
$ fabric-ca-client enroll -u http://peer0.org2.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/org2.example.com/peer0
#获取管理员签名证书
$ mkdir fabric-ca-files/org2.example.com/peer0/msp/admincerts
$ cp fabric-ca-files/org2.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org2.example.com/peer0/msp/admincerts/
#使用[email protected]注册并登记账号peer1.org2.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/org2.example.com/admin --id.secret=test123 --id.name peer1.org2.example.com --id.type peer --id.affiliation "com.example.org2" --id.maxenrollments "0" --id.attrs 'role=peer:ecert'
$ mkdir ./fabric-ca-files/org2.example.com/peer1
$ fabric-ca-client enroll -u http://peer1.org2.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/org2.example.com/peer1
#获取管理员签名证书
$ mkdir fabric-ca-files/org2.example.com/peer1/msp/admincerts
$ cp fabric-ca-files/org2.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org2.example.com/peer1/msp/admincerts/至此生成的目录结构如下图
其中org1.example.com中peer2大家是没有,这里的peer2是动态添加所需要的。想尝试以上是否可用的可直接跳至下一步。接下来先贴peer2证书生成过程。
#使用[email protected]注册并登记账号peer2.org1.example.com
$ fabric-ca-client register -H `pwd`/fabric-ca-files/org1.example.com/admin/ --id.secret=test123 --id.name peer2.org1.example.com --id.type peer --id.affiliation "com.example.org1" --id.maxenrollments "0" --id.attrs 'role=peer:ecert'
$ mkdir ./fabric-ca-files/org1.example.com/peer2
$ fabric-ca-client enroll -u http://peer2.org1.example.com:test123@localhost:7054 -H `pwd`/fabric-ca-files/org1.example.com/peer2
#获取管理员签名证书
$ mkdir fabric-ca-files/org1.example.com/peer2/msp/admincerts
$ cp fabric-ca-files/org1.example.com/admin/msp/signcerts/cert.pem fabric-ca-files/org1.example.com/peer2/msp/admincerts/七、替换证书
#因为我们是运行在e2e_cli实例上的,我们先切换到e2e_cli目录下
$ cd $GOPATH/src/github.com/hyperledger/fabric/examples/e2e_cli/
#运行generateArtifacts.sh脚本生成crypto-config文件夹
#大家自行分析目录结构
#接下来进行手动替换
#替换ordererOrganizations/example.com/msp 为 fabric-ca-files/example.com/msp
#替换ordererOrganizations/example.com/users/[email protected]/msp 为 fabric-ca-files/example.com/admin/msp
#替换ordererOrganizations/example.com/orderers/orderer.example.com/msp 为 fabric-ca-files/example.com/orderer/msp
#替换peerOrganizations/org1.example.com 和 peerOrganizations/org2.example.com
#具体内容与ordererOrganizations/example.com一样八、修改相关文件
#修改generateArtifacts.sh,注释掉倒数第二第三行
#使network_setup.sh up启动网络时,不会使工具生成新文件替换掉我们自己准备的crypto-config
> #generateCerts
> #replacePrivateKey
> generateChannelArtifacts
#修改network_setup.sh文件中的networkDown方法
#使我们关闭网络时不删除我们的crypto-config,只删除创世块文件及锚点文件
> #rm -rf channel-artifacts/*.block channel-artifacts/*.tx crypto-config
> rm -rf channel-artifacts/*.block channel-artifacts/*.tx
#关闭TLS功能,共修改三处
#docker-compose-cli.yaml cli
#base/docker-compose-base.yaml orderer.example.com
#base/peer-base.yaml peer-base
> CORE_PEER_TLS_ENABLED=false九、结语
为保证测试fabric-ca证书文件是否可用,大家自行确定使用工具生成的证书,可以跑通。跑通后在进行证书替换,测试fabric-ca证书。有问题可在下方留言。
相关文献:
https://blog.csdn.net/mellymengyan/article/details/80765472
https://www.cnblogs.com/midfielder/p/7173121.html