HYPERLEDGER FABRIC-CA学习
概述
fabric-ca 是hyperledger的一个子项目,其功能主要是提供证书生成以及管理
Hyperleder Fabric系统架构核心逻辑包括MemberShip、Blockchain和Chaincode

其中上述3个核心逻辑中,Membership服务用来管理节点身份、隐私、confidentiality 和 auditability。在一个
non-permissioned的区块链网络里,参与者不要求授权,所有的节点被视作一样,都可以提交一个transaction,去把这些交易存到区块(blocks)中。Membership
Service将一个 non-permissioned的区块链网络变成一个permissioned的区块链网络,凭借着Public Key
Infrastructure (PKI)、去中心和一致性。从上面的描述中可以看出,对于一个隐私性要求较高,节点需要授权才可以加入区块链网络并节点可能存在不同角色的区块链我那个链,Membership从中起到授权用户、加密传输数据的作用。在Fabric
1.0版本中,MemberShip Service替换成fabric-ca模块。由于CA在pemissioned区块链网络中的重要作用,Fabric也将CA作为一个单独的模块,可以独立运行,其代码可从https://github.com/hyperledger/fabric-ca获取得到。
下面的图表描述了CA 服务器在Hyperleder Fabric框架体系架构中的工作方式:
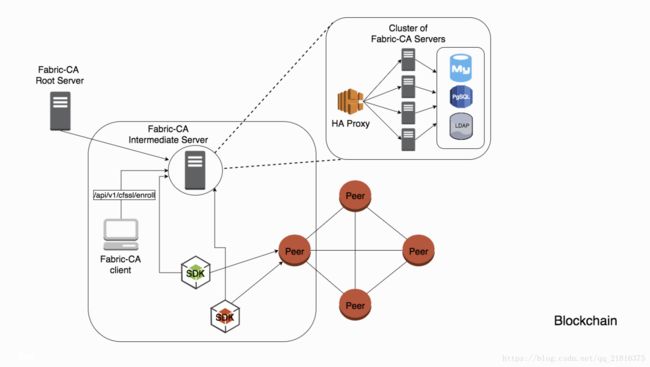
从表中可以看出,CA 服务器结构为树形结构,整个树形结构的根节点为根CA(Root Server),存在多个中间CA(Intermediate CA),图中每个中间CA服务器上可以配置一个CA服务集群,CA服务集群通过前置的HAproxy实现负载均衡。
Fabric CA提供了两种访问方式调用Server服务,一种是通过Client调用,另一种是通过SDK调用。两种调用都是REST风格的。本文使用的是通过Client调用。
接下来,参考fabric-ca官方文档说明要求,针对fabric-ca的请求/发放证书、注册节点等操作实践操作一遍已加深理解。
系统环境
[root@fabric-cli fabric-ca]# cat /etc/redhat-release
CentOS Linux release 7.4.1708 (Core) 获取代码以及安装编译环境
git clone https://github.com/hyperledger/fabric-ca.git
git checkout v1.1.0yum install golang libtool-ltdl-devel -y设置gopath
[root@fabric-cli ca1]# pwd
/root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-server/ca/ca1
[root@fabric-cli ca1]# echo $GOPATH
/root/
如果直接执行就不用修改github.com/hyperledger/fabric-ca/lib/version.go文件了
go get -u github.com/hyperledger/fabric-ca/cmd/...修改github.com/hyperledger/fabric-ca/lib/version.go
// GetVersion returns the version
func GetVersion() string {
if Version == "" {
Version="1.1.0" //添加这一行
panic("Version is not set for fabric-ca library")
}
return Version
}如果不修改会报错
[root@fabric-cli fabric-ca-server]# ./fabric-ca-server start -b admin:adminpw
2018/05/04 16:21:06 [INFO] Configuration file location: /root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-server/fabric-ca-server-config.yaml
2018/05/04 16:21:06 [INFO] Starting server in home directory: /root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-server
panic: Version is not set for fabric-ca library
goroutine 1 [running]:
github.com/hyperledger/fabric-ca/lib/metadata.GetVersion(0x1, 0xc4202973b0)
/root/src/github.com/hyperledger/fabric-ca/lib/metadata/version.go:58 +0x8b
github.com/hyperledger/fabric-ca/lib.(*Server).init(0xc420274a20, 0x0, 0xc420103bd8, 0x1)
/root/src/github.com/hyperledger/fabric-ca/lib/server.go:98 +0x29
github.com/hyperledger/fabric-ca/lib.(*Server).Start(0xc420274a20, 0xc420274a20, 0xc4200158d4)
/root/src/github.com/hyperledger/fabric-ca/lib/server.go:131 +0xee
main.(*ServerCmd).init.func3(0xc42006efc0, 0xc420168520, 0x0, 0x2, 0x0, 0x0)
/root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-server/ser
...编译
cd /root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-server
go build
cd /root/src/github.com/hyperledger/fabric-ca/cmd/fabric-ca-client
go build启动fabric-ca-server:
使用命令fabric-ca-server start -b admin:adminpw –cacount 2启动了一个包含了2个CA服务簇的CA server
[root@fabric-cli first]# fabric-ca-server start -b admin:adminpw --cacount 2
2018/05/05 09:41:53 [INFO] Created default configuration file at /root/first/fabric-ca-server-config.yaml
2018/05/05 09:41:53 [INFO] Starting server in home directory: /root/first
2018/05/05 09:41:53 [INFO] Server Version: 1.1.0
2018/05/05 09:41:53 [INFO] Server Levels: &{Identity:1 Affiliation:1 Certificate:1}
2018/05/05 09:41:53 [INFO] Loading CA from /root/first/ca/ca1/fabric-ca-config.yaml
2018/05/05 09:41:53 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:41:53 [INFO] encoded CSR
2018/05/05 09:41:53 [INFO] signed certificate with serial number 311619704474802174194156511492686636990995466448
2018/05/05 09:41:53 [INFO] The CA key and certificate were generated for CA ca1
2018/05/05 09:41:53 [INFO] The key was stored by BCCSP provider 'SW'
2018/05/05 09:41:53 [INFO] The certificate is at: /root/first/ca/ca1/ca-cert.pem
2018/05/05 09:41:53 [INFO] Initialized sqlite3 database at /root/first/ca/ca1/fabric-ca-server_ca1.db
2018/05/05 09:41:53 [INFO] Loading CA from /root/first/ca/ca2/fabric-ca-config.yaml
2018/05/05 09:41:53 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:41:53 [INFO] encoded CSR
2018/05/05 09:41:53 [INFO] signed certificate with serial number 9675068947773322809591550487667362524005377001
2018/05/05 09:41:53 [INFO] The CA key and certificate were generated for CA ca2
2018/05/05 09:41:53 [INFO] The key was stored by BCCSP provider 'SW'
2018/05/05 09:41:53 [INFO] The certificate is at: /root/first/ca/ca2/ca-cert.pem
2018/05/05 09:41:53 [INFO] Initialized sqlite3 database at /root/first/ca/ca2/fabric-ca-server_ca2.db
2018/05/05 09:41:53 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:41:53 [INFO] encoded CSR
2018/05/05 09:41:53 [INFO] signed certificate with serial number 692411238091865327503936658426428018548545759152
2018/05/05 09:41:53 [INFO] The CA key and certificate were generated for CA
2018/05/05 09:41:53 [INFO] The key was stored by BCCSP provider 'SW'
2018/05/05 09:41:53 [INFO] The certificate is at: /root/first/ca-cert.pem
2018/05/05 09:41:53 [INFO] Initialized sqlite3 database at /root/first/fabric-ca-server.db
2018/05/05 09:41:53 [INFO] Home directory for default CA: /root/first
2018/05/05 09:41:53 [INFO] Listening on http://0.0.0.0:7054
启动CA server后,在服务器根目录下分别新建了一个ca1和ca2两个文件夹,启动过程中服务器首先通过ecdsa SHA256算法生成密钥,然后编码生成CSR(证书签名请求,CSR签名请求中包含了请求用户的城市、公司等基本信息),CA服务器对CSR中的基本信息通过数字签名制作数字证书并颁发给申请者。上图可以看出最终生成的CA证书最终存储在ca1和ca2文件夹下的ca-cert.pem文件里。生成数字证书后,CA服务器会将证书信息写入到数据库或LDAP目录服务器中。上图中默认存放在ca1和ca2文件夹下的sqlite3 db中。
[root@fabric-cli first]# tree
.
├── ca
│ ├── ca1
│ │ ├── ca-cert.pem
│ │ ├── fabric-ca-config.yaml
│ │ ├── fabric-ca-server_ca1.db
│ │ └── msp
│ │ └── keystore
│ │ └── 9698af7f2faf00d9fb0bde5e310862ea8cd7ace4b66144f229e661d125eaf559_sk
│ └── ca2
│ ├── ca-cert.pem
│ ├── fabric-ca-config.yaml
│ ├── fabric-ca-server_ca2.db
│ └── msp
│ └── keystore
│ └── a5f81a8b7a8eb78f033d44d2454fbb4a01b4751d26d7c5837daf9cd9f93abb1d_sk
├── ca-cert.pem
├── fabric-ca-server-config.yaml
├── fabric-ca-server.db
└── msp
└── keystore
└── b848bc83ee2bfebe64a3f046781b0eb4f9f628fcb26ffa6f207dd28c406f3a85_sk
9 directories, 12 files
切换到ca1文件夹下,通过openssl命令查看证书内容:
[root@fabric-cli ca]# cd ca1/
[root@fabric-cli ca1]# ls -l
总用量 48
[root@fabric-cli ca1]# openssl x509 -in ca-cert.pem -inform pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
36:95:82:c5:89:a0:43:25:19:0c:58:db:d9:d4:75:13:13:7d:88:d0
Signature Algorithm: ecdsa-with-SHA256
Issuer: C=US, ST=North Carolina, O=Hyperledger, OU=Fabric, CN=fabric-ca-server-ca1
Validity
Not Before: May 5 01:37:00 2018 GMT
Not After : May 1 01:37:00 2033 GMT
Subject: C=US, ST=North Carolina, O=Hyperledger, OU=Fabric, CN=fabric-ca-server-ca1
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:9a:7b:4b:53:e1:2c:a0:df:62:13:37:c2:3d:a6:
fb:b4:6c:46:3e:b1:9c:c5:88:13:c1:ee:d4:09:e9:
ca:f5:19:05:d8:6c:ad:b6:25:40:19:5d:dd:ed:7e:
f9:61:63:3d:a6:b7:ef:8b:e0:0c:21:8b:6f:38:d4:
08:93:bc:1f:0a
ASN1 OID: prime256v1
NIST CURVE: P-256
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:1
X509v3 Subject Key Identifier:
3C:7F:B6:D4:7E:80:64:C9:2F:31:17:68:18:19:38:C4:5C:08:6D:C3
Signature Algorithm: ecdsa-with-SHA256
30:45:02:21:00:85:32:25:54:07:24:3f:dd:ff:65:78:a2:9b:
63:3c:2d:8a:1b:5d:29:77:e6:31:89:3b:0b:61:b5:84:b3:63:
ca:02:20:7f:2a:2f:e4:c9:aa:fd:75:65:dc:f9:22:ce:71:4e:
11:0a:f3:68:28:b7:72:3b:dd:b0:c0:4a:88:d5:bb:1b:f3从上面的信息可以看到,数字证书包含了签名算法信息、申请者基本信息、申请者公钥信息等。
打开存储发放证书信息的sqlite3 数据库:
[root@fabric-cli first]# sqlite3 fabric-ca-server.db
SQLite version 3.7.17 2013-05-20 00:56:22
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite> .tables
affiliations certificates properties users
sqlite> select * from users;
admin|$2a$10$9nTYJLGwnqvFPVSO.wCgwurv9pJ.mwmk//h0/Gcv2LTzC6o7oWbSi|client||[{"name":"hf.Registrar.Roles","value":"peer,orderer,client,user"},{"name":"hf.Registrar.DelegateRoles","value":"peer,orderer,client,user"},{"name":"hf.Revoker","value":"1"},{"name":"hf.IntermediateCA","value":"1"},{"name":"hf.GenCRL","value":"1"},{"name":"hf.Registrar.Attributes","value":"*"},{"name":"hf.AffiliationMgr","value":"1"}]|0|-1|1
sqlite>
可以看到数据库中有3个表,其中users表中目前只有启动时设定的引导节点,还没有注册其他节点。certificates表中目前没有任何发放证书记录。
现在我们尝试使用fabric-ca先登记引导节点,命令如下:
fabric-ca-client enroll -H $PWD -u http://admin:adminpw@localhost:7054这里admin和adminpw即为fabric-ca-server启动时设置的引导节点登记id和密码
client执行结果如下:
[root@fabric-cli client-01]# fabric-ca-client enroll -H $PWD -u http://admin:adminpw@localhost:7054
2018/05/05 09:45:38 [INFO] Created a default configuration file at /root/client-01/fabric-ca-client-config.yaml
2018/05/05 09:45:38 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:45:38 [INFO] encoded CSR
2018/05/05 09:45:39 [INFO] Stored client certificate at /root/client-01/msp/signcerts/cert.pem
2018/05/05 09:45:39 [INFO] Stored root CA certificate at /root/client-01/msp/cacerts/localhost-7054.pem
2018/05/05 09:45:39 [INFO] Stored intermediate CA certificates at /root/client-01/msp/intermediatecerts/localhost-7054.pemserver端接收到登记请求:
2018/05/05 09:45:39 [INFO] signed certificate with serial number 113565818925120426742161970700227134872628277937
2018/05/05 09:45:39 [INFO] [::1]:53454 POST /enroll 201 0 "OK"在ca-client目录下生成的目录结构如下:
[root@fabric-cli client-01]# tree
.
├── fabric-ca-client-config.yaml
└── msp
├── cacerts
│ └── localhost-7054.pem
├── intermediatecerts
│ └── localhost-7054.pem
├── keystore
│ └── e9c5eaf48a95a9c32ec06db17cf608339526094309aca2a65f30302a52d8920d_sk
└── signcerts
└── cert.pem
5 directories, 5 files
回到ca-server目录下,打开sqlite3数据库,可以看到刚刚颁发的数字证书已经记录在数据库里了。
[root@fabric-cli first]# sqlite3 fabric-ca-server.db
SQLite version 3.7.17 2013-05-20 00:56:22
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite> .tables
affiliations certificates properties users
sqlite> select * from users;
admin|$2a$10$9nTYJLGwnqvFPVSO.wCgwurv9pJ.mwmk//h0/Gcv2LTzC6o7oWbSi|client||[{"name":"hf.Registrar.Roles","value":"peer,orderer,client,user"},{"name":"hf.Registrar.DelegateRoles","value":"peer,orderer,client,user"},{"name":"hf.Revoker","value":"1"},{"name":"hf.IntermediateCA","value":"1"},{"name":"hf.GenCRL","value":"1"},{"name":"hf.Registrar.Attributes","value":"*"},{"name":"hf.AffiliationMgr","value":"1"}]|0|-1|1
sqlite> select * from certificates;
admin|13e477aa7b82cedbf5cd7a048499113b07ccb2b1|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:46:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICPjCCAeSgAwIBAgIUE+R3qnuCztv1zXoEhJkROwfMsrEwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDEwMFoXDTE5MDUwNTAxNDYwMFowXTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGY2xpZW50MQ4wDAYDVQQDEwVhZG1pbjBZMBMGByqG
SM49AgEGCCqGSM49AwEHA0IABBfB1sXja/H8BTnyvmHxhq2CqfmQFmNJyZa6w4zw
fuN94luslQ2HBSiaNWgeKNjM3GzYKMdxnNTadkY/JaguLrOjdzB1MA4GA1UdDwEB
/wQEAwIHgDAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBSFIoO+i0EDfSif4smmQgQh
XkisczAfBgNVHSMEGDAWgBQPkPMWQyFwjQE2q6Od6+5JOt7y2jAVBgNVHREEDjAM
ggpmYWJyaWMtY2xpMAoGCCqGSM49BAMCA0gAMEUCIQDOKII56tG+c1pZDQHVV0yD
SRrZqVJTr26ISYXCV5Y/dAIgOGAn71VZ6v7AQoAZGV8zIIut1Yt6b/5o6RYHdXWB
Ngs=
-----END CERTIFICATE-----
|1
接下来使用fabric-ca-client注册一个新的节点,这一步就是为fabric中的peer、user角色进行注册并登记的过程了,注册的命令为:
fabric-ca-client register --id.name admin2 --id.type user --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar'这里有两点需要注意:
1、–id.type参数必须是是server端配置文件里hf.Registrar.Roles属性值里的一个
打开fabric-ca-server的配置文件
#############################################################################
registry:
# Maximum number of times a password/secret can be reused for enrollment
# (default: -1, which means there is no limit)
maxenrollments: -1
# Contains identity information which is used when LDAP is disabled
identities:
- name: admin
pass: adminpw
type: client
affiliation: ""
attrs:
hf.Registrar.Roles: "peer,orderer,client,user"
hf.Registrar.DelegateRoles: "peer,orderer,client,user"
hf.Revoker: true
hf.IntermediateCA: true
hf.GenCRL: true
hf.Registrar.Attributes: "*"
hf.AffiliationMgr: true
#############################################################################其中通过hf.Registrar.Roles的属性值可以看出,客户端可以注册的类型有client,user,peer,validator和auditor
--id.affiliation这个属性表示:被注册对象的从属关系参数一定要归属于预先配置的组织属性。换句话说,被注册对象的affiliation参数一定要是预先配置的affiliation参数的一个前缀。例如,假设预先配置的组织关系为:“a.b.c”,那么新注册的对象的affiliation属性可以是“a.b.c”,也可以是“a.b”,但“a.c”就不能通过注册。
[root@fabric-cli client-01]# fabric-ca-client register --id.name admin2 --id.type user -H $PWD --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar'
2018/05/05 09:51:03 [INFO] Configuration file location: /root/client-01/fabric-ca-client-config.yaml
Password: JVkuTyRRbnUKfabric-ca-server 信息
2018/05/05 09:51:03 [INFO] [::1]:53456 POST /register 201 0 "OK"
登记刚刚注册过的admin2节点,登记命令为:
fabric-ca-client enroll -u http://admin2:JVkuTyRRbnUK@localhost:7054 -M $PWD/msp这里登记时使用的erollId和密码就是上边注册过程中的节点名称和返回的密码信息。这册过程中也是可以指定密码的。
执行登记命令,结果如下:
[root@fabric-cli client-01]# fabric-ca-client enroll -u http://admin2:JVkuTyRRbnUK@localhost:7054 -M $PWD/msp
2018/05/05 09:53:45 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:53:45 [INFO] encoded CSR
2018/05/05 09:53:45 [INFO] Stored client certificate at /root/client-01/msp/signcerts/cert.pem
2018/05/05 09:53:45 [INFO] Stored root CA certificate at /root/client-01/msp/cacerts/localhost-7054.pem
2018/05/05 09:53:45 [INFO] Stored intermediate CA certificates at /root/client-01/msp/intermediatecerts/localhost-7054.pemfabric-ca-server 信息
2018/05/05 09:53:45 [INFO] signed certificate with serial number 414694951994773083928698018225736094597082642758
2018/05/05 09:53:45 [INFO] [::1]:53458 POST /enroll 201 0 "OK"打开fabric-ca-server的sqlite数据库
[root@fabric-cli first]# sqlite3 fabric-ca-server.db
SQLite version 3.7.17 2013-05-20 00:56:22
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite> .tables
affiliations certificates properties users
sqlite> select * from users;
admin|$2a$10$9nTYJLGwnqvFPVSO.wCgwurv9pJ.mwmk//h0/Gcv2LTzC6o7oWbSi|client||[{"name":"hf.Registrar.Roles","value":"peer,orderer,client,user"},{"name":"hf.Registrar.DelegateRoles","value":"peer,orderer,client,user"},{"name":"hf.Revoker","value":"1"},{"name":"hf.IntermediateCA","value":"1"},{"name":"hf.GenCRL","value":"1"},{"name":"hf.Registrar.Attributes","value":"*"},{"name":"hf.AffiliationMgr","value":"1"}]|0|-1|1
sqlite> select * from certificates;
admin|13e477aa7b82cedbf5cd7a048499113b07ccb2b1|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:46:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICPjCCAeSgAwIBAgIUE+R3qnuCztv1zXoEhJkROwfMsrEwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDEwMFoXDTE5MDUwNTAxNDYwMFowXTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGY2xpZW50MQ4wDAYDVQQDEwVhZG1pbjBZMBMGByqG
SM49AgEGCCqGSM49AwEHA0IABBfB1sXja/H8BTnyvmHxhq2CqfmQFmNJyZa6w4zw
fuN94luslQ2HBSiaNWgeKNjM3GzYKMdxnNTadkY/JaguLrOjdzB1MA4GA1UdDwEB
/wQEAwIHgDAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBSFIoO+i0EDfSif4smmQgQh
XkisczAfBgNVHSMEGDAWgBQPkPMWQyFwjQE2q6Od6+5JOt7y2jAVBgNVHREEDjAM
ggpmYWJyaWMtY2xpMAoGCCqGSM49BAMCA0gAMEUCIQDOKII56tG+c1pZDQHVV0yD
SRrZqVJTr26ISYXCV5Y/dAIgOGAn71VZ6v7AQoAZGV8zIIut1Yt6b/5o6RYHdXWB
Ngs=
-----END CERTIFICATE-----
|1
sqlite> select * from users;
admin|$2a$10$9nTYJLGwnqvFPVSO.wCgwurv9pJ.mwmk//h0/Gcv2LTzC6o7oWbSi|client||[{"name":"hf.Registrar.Roles","value":"peer,orderer,client,user"},{"name":"hf.Registrar.DelegateRoles","value":"peer,orderer,client,user"},{"name":"hf.Revoker","value":"1"},{"name":"hf.IntermediateCA","value":"1"},{"name":"hf.GenCRL","value":"1"},{"name":"hf.Registrar.Attributes","value":"*"},{"name":"hf.AffiliationMgr","value":"1"}]|1|-1|1
admin2|$2a$10$euHgYm9FQb4uGem7PoD.5e7OU3An4q7R1FsA5W9d.E6bhf1r.Gd3m|user|org1.department1|[{"name":"hf.Revoker","value":"true"},{"name":"foo","value":"bar"},{"name":"hf.EnrollmentID","value":"admin2","ecert":true},{"name":"hf.Type","value":"user","ecert":true},{"name":"hf.Affiliation","value":"org1.department1","ecert":true}]|1|-1|1
查看用户信息,其中有一个client节点admin和一个user节点admin2。其中admin是一个intermediateCA。
打开数据库表certificates,这是可以看到给admin2所颁发的证书已经记录了。
qlite> select * from certificates;
admin|13e477aa7b82cedbf5cd7a048499113b07ccb2b1|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:46:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICPjCCAeSgAwIBAgIUE+R3qnuCztv1zXoEhJkROwfMsrEwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDEwMFoXDTE5MDUwNTAxNDYwMFowXTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGY2xpZW50MQ4wDAYDVQQDEwVhZG1pbjBZMBMGByqG
SM49AgEGCCqGSM49AwEHA0IABBfB1sXja/H8BTnyvmHxhq2CqfmQFmNJyZa6w4zw
fuN94luslQ2HBSiaNWgeKNjM3GzYKMdxnNTadkY/JaguLrOjdzB1MA4GA1UdDwEB
/wQEAwIHgDAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBSFIoO+i0EDfSif4smmQgQh
XkisczAfBgNVHSMEGDAWgBQPkPMWQyFwjQE2q6Od6+5JOt7y2jAVBgNVHREEDjAM
ggpmYWJyaWMtY2xpMAoGCCqGSM49BAMCA0gAMEUCIQDOKII56tG+c1pZDQHVV0yD
SRrZqVJTr26ISYXCV5Y/dAIgOGAn71VZ6v7AQoAZGV8zIIut1Yt6b/5o6RYHdXWB
Ngs=
-----END CERTIFICATE-----
|1
admin2|48a39095760013a4b0a7987722155c695455f946|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:54:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICyTCCAm+gAwIBAgIUSKOQlXYAE6Swp5h3IhVcaVRV+UYwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDkwMFoXDTE5MDUwNTAxNTQwMFowfTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEuMAsGA1UECxMEdXNlcjALBgNVBAsTBG9yZzEwEgYDVQQLEwtkZXBh
cnRtZW50MTEPMA0GA1UEAxMGYWRtaW4yMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEv6uyVrYvccW2JKx970ssQxZSrIlH+vEcm20aaxWqZOQCBfwUAIo82H+79hg5
bkPQiOKjVNeVK1lspGzJuEKgYaOB4TCB3jAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0T
AQH/BAIwADAdBgNVHQ4EFgQUIsG+F7zV+YJUu5LUD2Hs5JcFiiwwHwYDVR0jBBgw
FoAUD5DzFkMhcI0BNqujnevuSTre8towFQYDVR0RBA4wDIIKZmFicmljLWNsaTBn
BggqAwQFBgcIAQRbeyJhdHRycyI6eyJoZi5BZmZpbGlhdGlvbiI6Im9yZzEuZGVw
YXJ0bWVudDEiLCJoZi5FbnJvbGxtZW50SUQiOiJhZG1pbjIiLCJoZi5UeXBlIjoi
dXNlciJ9fTAKBggqhkjOPQQDAgNIADBFAiEA3ffGpEK32v9ig+EygVgDkEYC1VHW
90UIZjALrnS/egMCIEFDnwWRSFTQ2oYDUA5C+ZroTvDz1VPJQrcaMlKLjWOm
-----END CERTIFICATE-----
|1
重新登记节点,在节点授权即将到期是需要重新登记节点信息。重新登记的命令为:
[root@fabric-cli client-01]# fabric-ca-client reenroll -H $PWD
2018/05/05 09:57:35 [INFO] Configuration file location: /root/client-01/fabric-ca-client-config.yaml
2018/05/05 09:57:35 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 09:57:35 [INFO] encoded CSR
2018/05/05 09:57:35 [INFO] Stored client certificate at /root/client-01/msp/signcerts/cert.pem
2018/05/05 09:57:35 [INFO] Stored root CA certificate at /root/client-01/msp/cacerts/localhost-7054.pem
2018/05/05 09:57:35 [INFO] Stored intermediate CA certificates at /root/client-01/msp/intermediatecerts/localhost-7054.pem重新登记过程重新发送签名证书请求,获取新的数字证书。
打开server端数据库,可以看到两条颁发给节点admin2的证书记录,两个证书颁发的时间不一样。
sqlite> select * from certificates;
admin|13e477aa7b82cedbf5cd7a048499113b07ccb2b1|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:46:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICPjCCAeSgAwIBAgIUE+R3qnuCztv1zXoEhJkROwfMsrEwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDEwMFoXDTE5MDUwNTAxNDYwMFowXTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGY2xpZW50MQ4wDAYDVQQDEwVhZG1pbjBZMBMGByqG
SM49AgEGCCqGSM49AwEHA0IABBfB1sXja/H8BTnyvmHxhq2CqfmQFmNJyZa6w4zw
fuN94luslQ2HBSiaNWgeKNjM3GzYKMdxnNTadkY/JaguLrOjdzB1MA4GA1UdDwEB
/wQEAwIHgDAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBSFIoO+i0EDfSif4smmQgQh
XkisczAfBgNVHSMEGDAWgBQPkPMWQyFwjQE2q6Od6+5JOt7y2jAVBgNVHREEDjAM
ggpmYWJyaWMtY2xpMAoGCCqGSM49BAMCA0gAMEUCIQDOKII56tG+c1pZDQHVV0yD
SRrZqVJTr26ISYXCV5Y/dAIgOGAn71VZ6v7AQoAZGV8zIIut1Yt6b/5o6RYHdXWB
Ngs=
-----END CERTIFICATE-----
|1
admin2|48a39095760013a4b0a7987722155c695455f946|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:54:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICyTCCAm+gAwIBAgIUSKOQlXYAE6Swp5h3IhVcaVRV+UYwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDkwMFoXDTE5MDUwNTAxNTQwMFowfTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEuMAsGA1UECxMEdXNlcjALBgNVBAsTBG9yZzEwEgYDVQQLEwtkZXBh
cnRtZW50MTEPMA0GA1UEAxMGYWRtaW4yMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEv6uyVrYvccW2JKx970ssQxZSrIlH+vEcm20aaxWqZOQCBfwUAIo82H+79hg5
bkPQiOKjVNeVK1lspGzJuEKgYaOB4TCB3jAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0T
AQH/BAIwADAdBgNVHQ4EFgQUIsG+F7zV+YJUu5LUD2Hs5JcFiiwwHwYDVR0jBBgw
FoAUD5DzFkMhcI0BNqujnevuSTre8towFQYDVR0RBA4wDIIKZmFicmljLWNsaTBn
BggqAwQFBgcIAQRbeyJhdHRycyI6eyJoZi5BZmZpbGlhdGlvbiI6Im9yZzEuZGVw
YXJ0bWVudDEiLCJoZi5FbnJvbGxtZW50SUQiOiJhZG1pbjIiLCJoZi5UeXBlIjoi
dXNlciJ9fTAKBggqhkjOPQQDAgNIADBFAiEA3ffGpEK32v9ig+EygVgDkEYC1VHW
90UIZjALrnS/egMCIEFDnwWRSFTQ2oYDUA5C+ZroTvDz1VPJQrcaMlKLjWOm
-----END CERTIFICATE-----
|1
admin2|6892d7d741f433c9a4ad66103d32ddb46b4085ce|f90f3164321708d0136aba39debee493adef2da||good|0|2019-05-05 01:58:00+00:00|0001-01-01 00:00:00+00:00|-----BEGIN CERTIFICATE-----
MIICyDCCAm+gAwIBAgIUaJLX10H0M8mkrWYQPTLdtGtAhc4wCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNTMwMFoXDTE5MDUwNTAxNTgwMFowfTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEuMAsGA1UECxMEdXNlcjALBgNVBAsTBG9yZzEwEgYDVQQLEwtkZXBh
cnRtZW50MTEPMA0GA1UEAxMGYWRtaW4yMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEvwg0s4et+TywcGv+zNyA1wTtHNZMlosHF6Asqd5rsuv+dISqNQiMpeA/F3qt
DYnHPihSLlKNycvJNSyDjra1zaOB4TCB3jAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0T
AQH/BAIwADAdBgNVHQ4EFgQUcpZvmm4utQpA6gjxQ4k0hEGpSFUwHwYDVR0jBBgw
FoAUD5DzFkMhcI0BNqujnevuSTre8towFQYDVR0RBA4wDIIKZmFicmljLWNsaTBn
BggqAwQFBgcIAQRbeyJhdHRycyI6eyJoZi5BZmZpbGlhdGlvbiI6Im9yZzEuZGVw
YXJ0bWVudDEiLCJoZi5FbnJvbGxtZW50SUQiOiJhZG1pbjIiLCJoZi5UeXBlIjoi
dXNlciJ9fTAKBggqhkjOPQQDAgNHADBEAiB0zbnY+Hvjj49lHanOwSXokCxedV17
cPHFMnJuzek14AIgN4CPtMtQuUAXSm3VIg43qi1oReKC2SO76SwF0hcKcmY=
-----END CERTIFICATE-----
|1
注销证书
注销证书的命令为
fabric-ca-client revoke -e <enrollment_id> -r <reason>其中reason参数可以为:
1. keycompromise
2. cacompromise
3. affiliationchange
4. superseded
5. cessationofoperation
6. certificatehold
7. removefromcrl
8. privilegewithdrawn
9. aacompromise
10. unspecified
下面我们注销掉刚刚登记的admin2节点试一下,执行命令fabric-ca-client revoke -H $PWD -e admin2:
执行结果如下:
[root@fabric-cli client-01]# fabric-ca-client revoke -H $PWD -e admin2
2018/05/05 10:01:32 [INFO] Configuration file location: /root/client-01/fabric-ca-client-config.yaml
2018/05/05 10:01:32 [INFO] Sucessfully revoked certificates: [{Serial:48a39095760013a4b0a7987722155c695455f946 AKI:f90f3164321708d0136aba39debee493adef2da} {Serial:6892d7d741f433c9a4ad66103d32ddb46b4085ce AKI:f90f3164321708d0136aba39debee493adef2da}]改为已注销
|1
admin2|48a39095760013a4b0a7987722155c695455f946|f90f3164321708d0136aba39debee493adef2da||revoked|0|2019-05-05 01:54:00+00:00|2018-05-05 02:01:32|-----BEGIN CERTIFICATE-----
MIICyTCCAm+gAwIBAgIUSKOQlXYAE6Swp5h3IhVcaVRV+UYwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNDkwMFoXDTE5MDUwNTAxNTQwMFowfTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEuMAsGA1UECxMEdXNlcjALBgNVBAsTBG9yZzEwEgYDVQQLEwtkZXBh
cnRtZW50MTEPMA0GA1UEAxMGYWRtaW4yMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEv6uyVrYvccW2JKx970ssQxZSrIlH+vEcm20aaxWqZOQCBfwUAIo82H+79hg5
bkPQiOKjVNeVK1lspGzJuEKgYaOB4TCB3jAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0T
AQH/BAIwADAdBgNVHQ4EFgQUIsG+F7zV+YJUu5LUD2Hs5JcFiiwwHwYDVR0jBBgw
FoAUD5DzFkMhcI0BNqujnevuSTre8towFQYDVR0RBA4wDIIKZmFicmljLWNsaTBn
BggqAwQFBgcIAQRbeyJhdHRycyI6eyJoZi5BZmZpbGlhdGlvbiI6Im9yZzEuZGVw
YXJ0bWVudDEiLCJoZi5FbnJvbGxtZW50SUQiOiJhZG1pbjIiLCJoZi5UeXBlIjoi
dXNlciJ9fTAKBggqhkjOPQQDAgNIADBFAiEA3ffGpEK32v9ig+EygVgDkEYC1VHW
90UIZjALrnS/egMCIEFDnwWRSFTQ2oYDUA5C+ZroTvDz1VPJQrcaMlKLjWOm
-----END CERTIFICATE-----
|1
admin2|6892d7d741f433c9a4ad66103d32ddb46b4085ce|f90f3164321708d0136aba39debee493adef2da||revoked|0|2019-05-05 01:58:00+00:00|2018-05-05 02:01:32|-----BEGIN CERTIFICATE-----
MIICyDCCAm+gAwIBAgIUaJLX10H0M8mkrWYQPTLdtGtAhc4wCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNTMwMFoXDTE5MDUwNTAxNTgwMFowfTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEuMAsGA1UECxMEdXNlcjALBgNVBAsTBG9yZzEwEgYDVQQLEwtkZXBh
cnRtZW50MTEPMA0GA1UEAxMGYWRtaW4yMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEvwg0s4et+TywcGv+zNyA1wTtHNZMlosHF6Asqd5rsuv+dISqNQiMpeA/F3qt
DYnHPihSLlKNycvJNSyDjra1zaOB4TCB3jAOBgNVHQ8BAf8EBAMCB4AwDAYDVR0T
AQH/BAIwADAdBgNVHQ4EFgQUcpZvmm4utQpA6gjxQ4k0hEGpSFUwHwYDVR0jBBgw
FoAUD5DzFkMhcI0BNqujnevuSTre8towFQYDVR0RBA4wDIIKZmFicmljLWNsaTBn
BggqAwQFBgcIAQRbeyJhdHRycyI6eyJoZi5BZmZpbGlhdGlvbiI6Im9yZzEuZGVw
YXJ0bWVudDEiLCJoZi5FbnJvbGxtZW50SUQiOiJhZG1pbjIiLCJoZi5UeXBlIjoi
dXNlciJ9fTAKBggqhkjOPQQDAgNHADBEAiB0zbnY+Hvjj49lHanOwSXokCxedV17
cPHFMnJuzek14AIgN4CPtMtQuUAXSm3VIg43qi1oReKC2SO76SwF0hcKcmY=
-----END CERTIFICATE-----
|1
注册一个中间CA
[root@fabric-cli peer]# fabric-ca-server start -b admin1:adminpw1 -p 7055 -H $PWD -u http://admin:adminpw@localhost:7054
2018/05/05 10:04:14 [INFO] Created default configuration file at /root/peer/fabric-ca-server-config.yaml
2018/05/05 10:04:14 [INFO] Starting server in home directory: /root/peer
2018/05/05 10:04:14 [INFO] Server Version: 1.1.0
2018/05/05 10:04:14 [INFO] Server Levels: &{Identity:1 Affiliation:1 Certificate:1}
2018/05/05 10:04:14 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 10:04:14 [INFO] encoded CSR
2018/05/05 10:04:15 [INFO] The CA key and certificate were generated for CA
2018/05/05 10:04:15 [INFO] The key was stored by BCCSP provider 'SW'
2018/05/05 10:04:15 [INFO] The certificate is at: /root/peer/ca-cert.pem
2018/05/05 10:04:15 [INFO] Initialized sqlite3 database at /root/peer/fabric-ca-server.db
2018/05/05 10:04:15 [INFO] Home directory for default CA: /root/peer
2018/05/05 10:04:15 [INFO] Listening on http://0.0.0.0:7055
上述命令重新启动了一个CA服务器,作为引导节点CA服务器下的中间CA
打开ca-chain.pem查看刚刚登记的中间CA服务器证书链:
[root@fabric-cli client-02]# cat ../peer/ca-chain.pem
-----BEGIN CERTIFICATE-----
MIICLTCCAdOgAwIBAgIUFXJxtOHxn8zBjYPIjQMRr/3oztYwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxNTkwMFoXDTIzMDUwNDAyMDQwMFowXTELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGY2xpZW50MQ4wDAYDVQQDEwVhZG1pbjBZMBMGByqG
SM49AgEGCCqGSM49AwEHA0IABOKxAKDUklNUmNMFnT034yp5UtSupyTz+Lu+Drv0
RxX7ydBVIAeZmXrEX17pdNpVye8pqdo02YpNnbteZ1tRJ9CjZjBkMA4GA1UdDwEB
/wQEAwIBBjASBgNVHRMBAf8ECDAGAQH/AgEAMB0GA1UdDgQWBBTHr+fY0av7Ix03
puo921GDhhvRtjAfBgNVHSMEGDAWgBQPkPMWQyFwjQE2q6Od6+5JOt7y2jAKBggq
hkjOPQQDAgNIADBFAiEArb4HQ6SAfPiaYH72Et4T/byQyBBaNBrtP40cXuKlRXAC
IFPG5bNs4Vlxd45yTaFokeV4vm0Q2XxYg+sOIQ1VK/gS
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIICFjCCAb2gAwIBAgIUeUjLMw6gVNNf+GjGZjyPVysBJ7AwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxMzcwMFoXDTMzMDUwMTAxMzcwMFowaDELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMtY2Etc2Vy
dmVyMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEILG2FJ+c37twKNojFB6ErPgq
gvaKYvlIlu8TPUP3GYQn2pFYkf/Xn1C5Y2xZYwG3D5r3N7O9NUJKMC6TB5Z2MKNF
MEMwDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQIMAYBAf8CAQEwHQYDVR0OBBYE
FA+Q8xZDIXCNATaro53r7kk63vLaMAoGCCqGSM49BAMCA0cAMEQCIGWQZ7bZ12Ob
+1epkoK7jueC9LdLqemwPsFa84PEU308AiBEWnAwqSigWwoO7Ed42/MWBdPJ4He1
q3OfQswaV1izvQ==
-----END CERTIFICATE-----服务端返回的结果
2018/05/05 10:04:15 [INFO] signed certificate with serial number 122440996379400339443912371377871659726075907798
2018/05/05 10:04:15 [INFO] [::1]:53468 POST /enroll 201 0 "OK"可以看到证书链中包含上级CA证书和自己的证书信息。
尝试在刚刚建立的CA server上注册登记一个节点,注册一个节点admin2的命令同上:
首先登记节点:
[root@fabric-cli client-02]# fabric-ca-client enroll -H /root/client-02/ -u http://admin1:adminpw1@localhost:7055
2018/05/05 10:40:46 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 10:40:46 [INFO] encoded CSR
2018/05/05 10:40:46 [INFO] Stored client certificate at /root/client-02/msp/signcerts/cert.pem
2018/05/05 10:40:46 [INFO] Stored root CA certificate at /root/client-02/msp/cacerts/localhost-7055.pem
2018/05/05 10:40:46 [INFO] Stored intermediate CA certificates at /root/client-02/msp/intermediatecerts/localhost-7055.pem
[root@fabric-cli client-02]# fabric-ca-client register --id.name admin2 --home $PWD --id.type user --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar'
2018/05/05 10:41:39 [INFO] Configuration file location: /root/client-02/fabric-ca-client-config.yaml
Password: JSidQazllwLg注册的结果已经记录在数据库中:
admin1|$2a$10$JPn9fBs7RlsiV8YrAMc3Auw5Gl7Lse6UQCml7UgKMCOqjXGm8TJ82|client||[{"name":"hf.GenCRL","value":"1"},{"name":"hf.Registrar.Attributes","value":"*"},{"name":"hf.AffiliationMgr","value":"1"},{"name":"hf.Registrar.Roles","value":"peer,orderer,client,user"},{"name":"hf.Registrar.DelegateRoles","value":"peer,orderer,client,user"},{"name":"hf.Revoker","value":"1"},{"name":"hf.IntermediateCA","value":"1"}]|1|-1|1
admin2|$2a$10$Il4HKQmTBi1/3/mqXED2g.3E.WwpEyin3hUB16CTkx72cdXmMBCfm|user|org1.department1|[{"name":"hf.Revoker","value":"true"},{"name":"foo","value":"bar"},{"name":"hf.EnrollmentID","value":"admin2","ecert":true},{"name":"hf.Type","value":"user","ecert":true},{"name":"hf.Affiliation","value":"org1.department1","ecert":true}]|0|-1|1
最后登记节点
[root@fabric-cli client-02]# fabric-ca-client enroll -H $PWD -u http://admin2:JSidQazllwLg@localhost:7055 -M $PWD/msp
2018/05/05 10:44:32 [INFO] generating key: &{A:ecdsa S:256}
2018/05/05 10:44:32 [INFO] encoded CSR
2018/05/05 10:44:33 [INFO] Stored client certificate at /root/client-02/msp/signcerts/cert.pem
2018/05/05 10:44:33 [INFO] Stored root CA certificate at /root/client-02/msp/cacerts/localhost-7055.pem
2018/05/05 10:44:33 [INFO] Stored intermediate CA certificates at /root/client-02/msp/intermediatecerts/localhost-7055.pem
进入刚刚登记的节点目录,生成如下目录结构:
[root@fabric-cli client-02]# tree
.
├── fabric-ca-client-config.yaml
└── msp
├── cacerts
│ └── localhost-7055.pem
├── intermediatecerts
│ └── localhost-7055.pem
├── keystore
│ ├── cb53d5219a75795f24e6a0a3bc549751ab56c94f426db55c3a64b1e780706306_sk
│ ├── cf752a33b03984a35c2fa616546405592b44d6d75af240a8dd4c606cf41a0b2c_sk
│ └── fb9a467ebd39d3f6a0a0cf668323093f104313085676322d6c95f32257efa6b2_sk
└── signcerts
└── cert.pem
5 directories, 7 files
[root@fabric-cli client-02]# cat msp/cacerts/localhost-7055.pem
-----BEGIN CERTIFICATE-----
MIICFjCCAb2gAwIBAgIUeUjLMw6gVNNf+GjGZjyPVysBJ7AwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAxMzcwMFoXDTMzMDUwMTAxMzcwMFowaDELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMtY2Etc2Vy
dmVyMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEILG2FJ+c37twKNojFB6ErPgq
gvaKYvlIlu8TPUP3GYQn2pFYkf/Xn1C5Y2xZYwG3D5r3N7O9NUJKMC6TB5Z2MKNF
MEMwDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQIMAYBAf8CAQEwHQYDVR0OBBYE
FA+Q8xZDIXCNATaro53r7kk63vLaMAoGCCqGSM49BAMCA0cAMEQCIGWQZ7bZ12Ob
+1epkoK7jueC9LdLqemwPsFa84PEU308AiBEWnAwqSigWwoO7Ed42/MWBdPJ4He1
q3OfQswaV1izvQ==
-----END CERTIFICATE-----打开cacerts下面的证书链文件,可以看到刚刚登记的节点证书链包含两个中间CA的数字证书信息,在验证由该个树形CA服务器中一个中间CA节点所颁发的数字证书是否真实有效时,会按照证书链自下向上进行验证,直至到达根证书。
如果区块链网络中有多个链,每个链为了保证各自的隐私性存在各自的CA服务器,那么当一个用户同时拥有两个链的权限时,怎样同时具备验证两个链上的节点所拥有的CA证书呢?按照上边证书链的原则,一个节点注册登记到一个中间CA后,应该只能拥有该条CA服务器链上的证书链。这里为了解决这个问题,有一种方法是交叉认证,在fabric-ca中也有类似的操作方法,即通过Restful接口获取另外一个CA服务器上的证书链。
具体命令为:
fabric-ca-client getcacert -u http://localhost:7055 -M $PWD/msp这里我们新建一个单独运行的CA服务器:
[root@fabric-cli server03]# fabric-ca-server start -b admin3:adminpw3 -p 7056
2018/05/05 10:49:54 [INFO] Configuration file location: /root/server03/fabric-ca-server-config.yaml
2018/05/05 10:49:54 [INFO] Starting server in home directory: /root/server03
2018/05/05 10:49:54 [INFO] Server Version: 1.1.0
2018/05/05 10:49:54 [INFO] Server Levels: &{Identity:1 Affiliation:1 Certificate:1}
2018/05/05 10:49:54 [INFO] The CA key and certificate already exist
2018/05/05 10:49:54 [INFO] The key is stored by BCCSP provider 'SW'
2018/05/05 10:49:54 [INFO] The certificate is at: /root/server03/ca-cert.pem
2018/05/05 10:49:54 [INFO] Initialized sqlite3 database at /root/server03/fabric-ca-server.db
2018/05/05 10:49:54 [INFO] Home directory for default CA: /root/server03
2018/05/05 10:49:54 [INFO] Listening on http://0.0.0.0:7056查看该根服务器的数字证书
[root@fabric-cli server03]# cat ca-cert.pem
-----BEGIN CERTIFICATE-----
MIICFjCCAb2gAwIBAgIUX2OUUlwjOgBzUIh4FZoKG3OcqWkwCgYIKoZIzj0EAwIw
aDELMAkGA1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQK
EwtIeXBlcmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMt
Y2Etc2VydmVyMB4XDTE4MDUwNTAyNDQwMFoXDTMzMDUwMTAyNDQwMFowaDELMAkG
A1UEBhMCVVMxFzAVBgNVBAgTDk5vcnRoIENhcm9saW5hMRQwEgYDVQQKEwtIeXBl
cmxlZGdlcjEPMA0GA1UECxMGRmFicmljMRkwFwYDVQQDExBmYWJyaWMtY2Etc2Vy
dmVyMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEMWTVtjZESsvaz1o9zD/KZlzo
I150vSMyHP1zGimYsd/4a2RRh5iy7Weovkrqi8gRQBIOX+J2hC2bTgij36hSzKNF
MEMwDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQIMAYBAf8CAQEwHQYDVR0OBBYE
FGdQoahILdWtPrClncg683eZNWMbMAoGCCqGSM49BAMCA0cAMEQCIGaqW75T4Woo
xzAxzFjZynBhk26QicgSSFOc2yHANotvAiAj/33gLW1Qj4Iil9ghbFDDuSBY7yPp
Xa4EqymGTCp/Eg==
-----END CERTIFICATE-----接下来,我们在上文登记的节点admin2上运行获取刚刚建立的CA服务器证书链命令
root@fabric-cli client-03]# fabric-ca-client getcacert -u http://localhost:7056 -M ../client-02/msp
2018/05/05 10:54:39 [INFO] Configuration file location: /root/.fabric-ca-client/fabric-ca-client-config.yaml
2018/05/05 10:54:39 [INFO] Stored root CA certificate at /root/client-02/msp/cacerts/localhost-7056.pem
2018/05/05 10:54:39 [INFO] Stored intermediate CA certificates at /root/client-02/msp/intermediatecerts/localhost-7056.pem执行命令结束后,查看admin2节点所对应的证书链目录:
[root@fabric-cli client-02]# tree
.
├── fabric-ca-client-config.yaml
└── msp
├── cacerts
│ ├── localhost-7055.pem
│ └── localhost-7056.pem
├── intermediatecerts
│ ├── localhost-7055.pem
│ └── localhost-7056.pem
├── keystore
│ ├── cb53d5219a75795f24e6a0a3bc549751ab56c94f426db55c3a64b1e780706306_sk
│ ├── cf752a33b03984a35c2fa616546405592b44d6d75af240a8dd4c606cf41a0b2c_sk
│ └── fb9a467ebd39d3f6a0a0cf668323093f104313085676322d6c95f32257efa6b2_sk
└── signcerts
└── cert.pem
5 directories, 9 files
可以看到启动在端口7056上的CA服务器所对应的证书链已经同步过来了。
Fabric-ca这个模块详细描述了CA工作过程中使用fabric-ca-client和sdk方式的方法,其中包括配置LDAP以及其他数据库的配置方法在文中也有说明,sdk方式的restful操作接口,可以查看fabric-ca源码根目录下的swagger.json文件。使用中需要根据区块链网络的特性,使用CA签发的数字证书进行认证、加密传输数据、授权用户、管理用户证书。
参考:
HYPERLEDGER FABRIC-CA学习
fabric-ca