最近在部署某公司的企业内联网,所以搭建了一个测试环境,将测试结果分享给大家。
一:实验目的:
xxx企业有北京总公司,上海分公司和深圳分公司,公司使用了NAT地址转换技术访问公网,并且要求分布在全国各地的企业内网之间也可以互相通信。
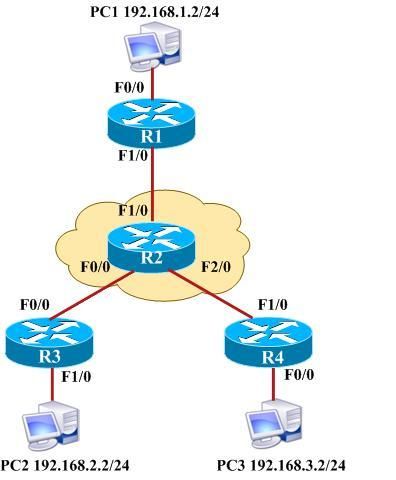
二:实验拓扑:
三:实验配置:
1:基本接口的配置
R1(config)#int f0/0
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#int f1/0
R1(config-if)#ip add 12.0.0.1 255.255.255.0
R1(config-if)#no sh
R2(config)#int f1/0
R2(config-if)#ip add 12.0.0.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#int f0/0
R2(config-if)#ip add 23.0.0.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#int f2/0
R2(config-if)#ip add 24.0.0.2 255.255.255.0
R2(config-if)#no sh
R3(config)#int f0/0
R3(config-if)#ip add 23.0.0.3 255.255.255.0
R3(config-if)#no sh
R3(config-if)#int f1/0
R3(config-if)#ip add 192.168.2.1 255.255.255.0
R3(config-if)#no sh
R4(config)#int f1/0
R4(config-if)#ip add 24.0.0.4 255.255.255.0
R4(config-if)#no sh
R4(config-if)#int f0/0
R4(config-if)#ip add 192.168.3.1 255.255.255.0
R4(config-if)#no sh
2:NAT和路由的配置:
R1(config)#int f0/0
R1(config-if)#ip nat inside
R1(config-if)#int f1/0
R1(config-if)#ip nat outside
R1(config)#access-list 101 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R1(config)#access-list 101 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
R1(config)#access-list 101 permit ip 192.168.1.0 0.0.0.255 any
R1(config)#ip nat inside source list 101 interface f1/0 overload
R1(config)#ip route 0.0.0.0 0.0.0.0 12.0.0.2
R3(config)#int f0/0
R3(config-if)#ip nat outside
R3(config-if)#int f1/0
R3(config-if)#ip nat inside
R3(config)#access-list 101 deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config)#access-list 101 deny ip 192.168.2.0 0.0.0.255 192.168.3.0 0.0.0.255
R3(config)#access-list 101 permit ip 192.168.2.0 0.0.0.255 any
R3(config)#ip nat inside source list 101 interface f0/0 overload
R3(config)#ip route 0.0.0.0 0.0.0.0 23.0.0.2
R4(config)#int f1/0
R4(config-if)#ip nat outside
R4(config-if)#int f0/0
R4(config-if)#ip nat inside
R4(config-if)#exit
R4(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
R4(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.2.0 0.0.0.255
R4(config)#access-list 101 permit ip 192.168.3.0 0.0.0.255 any
R4(config)#ip nat inside source list 101 interface f1/0 overload
R4(config)#ip route 0.0.0.0 0.0.0.0 24.0.0.2
3:×××的配置:
R1(config)#ip access-list extended R1-to-R3
R1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R1(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 192.168.2.0 0.0.0.255
R1(config)#ip access-list extended R1-to-R4
R1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
R1(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.3.0 0.0.0.255
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash md5
R1(config-isakmp)#group 2
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 6 R1-to-R3 address 23.0.0.3
R1(config)#crypto isakmp key 6 R1-to-R4 address 24.0.0.4
R1(config)#crypto ipsec transform-set mytrans esp-aes esp-md5-hmac
R1(cfg-crypto-trans)#mode tunnel
R1(cfg-crypto-trans)#exit
R1(config)#crypto map mymap 1 ipsec-isakmp
R1(config-crypto-map)#match address R1-to-R3
R1(config-crypto-map)#set peer 23.0.0.3
R1(config-crypto-map)#set transform-set mytrans
R1(config)#crypto map mymap 2 ipsec-isakmp
R1(config-crypto-map)#match address R1-to-R4
R1(config-crypto-map)#set peer 24.0.0.4
R1(config-crypto-map)#set transform-set mytrans
R1(config-crypto-map)#int f1/0
R1(config-if)#crypto map mymap
R3(config)#ip access-list extended R3-to-R1
R3(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.3.0 0.0.0.255
R3(config-ext-nacl)#exit
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption aes
R3(config-isakmp)#hash md5
R3(config-isakmp)#group 2
R3(config-isakmp)#exit
R3(config)#crypto isakmp key 6 R1-to-R3 address 12.0.0.1
R3(config)#crypto ipsec transform-set mytrans esp-aes esp-md5-hmac
R3(cfg-crypto-trans)#mode tunnel
R3(cfg-crypto-trans)#exit
R3(config)#crypto map mymap 1 ipsec-isakmp
R3(config-crypto-map)#match address R3-to-R1
R3(config-crypto-map)#set transform-set mytrans
R3(config-crypto-map)#set peer 12.0.0.1
R3(config)#int f0/0
R3(config-if)#crypto map mymap
R4(config)#ip access-list extended R4-to-R1
R4(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
R4(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 192.168.2.0 0.0.0.255
R4(config-ext-nacl)#exit
R4(config)#crypto isakmp policy 1
R4(config-isakmp)#authentication pre-share
R4(config-isakmp)#encryption aes
R4(config-isakmp)#hash md5
R4(config-isakmp)#group 2
R4(config-isakmp)#exit
R4(config)#crypto isakmp key 6 R1-to-R4 address 12.0.0.1
R4(config)#crypto ipsec transform-set mytrans esp-aes esp-md5-hmac
R4(cfg-crypto-trans)#mode tunnel
R4(cfg-crypto-trans)#exit
R4(config)#crypto map mymap 10 ipsec-isakmp
R4(config-crypto-map)#match address R4-to-R1
R4(config-crypto-map)#set transform-set mytrans
R4(config-crypto-map)#set peer 12.0.0.1
R4(config-crypto-map)#int f1/0
R4(config-if)#crypto map mymap
4:测试:
VPCS 1 >sho ip int b
NAME IP/CIDR GATEWAY LPORT RPORT
PC1 192.168.1.2/24 192.168.1.1 10001 11100
PC2 192.168.2.2/24 192.168.2.1 10002 11310
PC3 192.168.3.2/24 192.168.3.1 10003 11400
PC4 0.0.0.0/0 0.0.0.0 10004 30003
PC5 0.0.0.0/0 0.0.0.0 10005 30004
PC6 0.0.0.0/0 0.0.0.0 10006 30005
PC7 0.0.0.0/0 0.0.0.0 10007 30006
PC8 0.0.0.0/0 0.0.0.0 10008 30007
PC9 0.0.0.0/0 0.0.0.0 10009 30008
VPCS 1 >ping 192.168.2.2
192.168.2.2 icmp_seq=1 time=188.000 ms
192.168.2.2 icmp_seq=2 time=172.000 ms
192.168.2.2 icmp_seq=3 time=188.000 ms
192.168.2.2 icmp_seq=4 time=188.000 ms
192.168.2.2 icmp_seq=5 time=172.000 ms
VPCS 1 >ping 192.168.3.2
192.168.3.2 icmp_seq=1 time=188.000 ms
192.168.3.2 icmp_seq=2 time=172.000 ms
192.168.3.2 icmp_seq=3 time=171.000 ms
192.168.3.2 icmp_seq=4 time=203.000 ms
192.168.3.2 icmp_seq=5 time=172.000 ms
R1#sho crypto isakmp sa
dst src state conn-id slot status
24.0.0.4 12.0.0.1 QM_IDLE 2 0 ACTIVE
12.0.0.1 23.0.0.3 QM_IDLE 1 0 ACTIVE
R1#sho crypto ipsec sa
interface: FastEthernet1/0
Crypto map tag: mymap, local addr 12.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 23.0.0.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 16, #pkts encrypt: 16, #pkts digest: 16
#pkts decaps: 16, #pkts decrypt: 16, #pkts verify: 16
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 23.0.0.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/0
current outbound spi: 0x98B8F0B2(2562257074)
inbound esp sas:
spi: 0x7D92B7A1(2106767265)
transform: esp-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4557387/2955)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x98B8F0B2(2562257074)
transform: esp-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4557387/2954)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 24.0.0.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 2, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 24.0.0.4
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/0
current outbound spi: 0x50BAFCC3(1354431683)
inbound esp sas:
spi: 0xACEA01A8(2901017000)
transform: esp-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4394896/3482)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x50BAFCC3(1354431683)
transform: esp-aes esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4394896/3482)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 24.0.0.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 24.0.0.4
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/0
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 23.0.0.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.0.0.1, remote crypto endpt.: 23.0.0.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/0
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
四:实验总结:
测试结果符合企业需求,如果公司在全国的分布点更多,建议使用动态多点×××或MPLS ×××实现。
静态多点×××和动态多点×××都是企业自己部署,不需要花费额外的费用,而MPLS ×××需要给运营商付费,但MPLS ×××的传输效率会更高一些,客户在部署企业内联网时可根据企业实际需求选择合适的解决方案。