不多说,直接上干货!
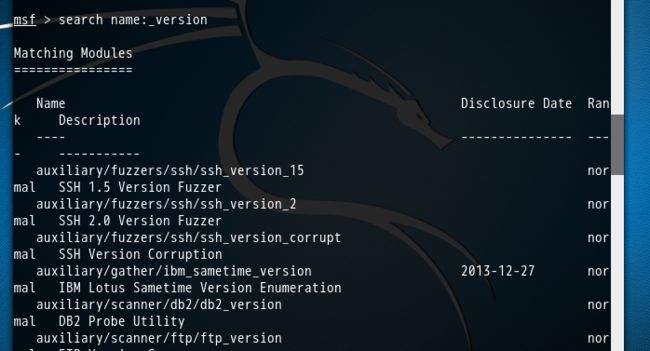
在MSF终端中,可以输入search name:_version命令查看所有可用的服务查点模块
该命令的执行结果如下:
root@kali:~# msfconsole
......
msf > search name:_version
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/fuzzers/ssh/ssh_version_15 normal SSH 1.5 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_2 normal SSH 2.0 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_corrupt normal SSH Version Corruption
auxiliary/gather/ibm_sametime_version 2013-12-27 normal IBM Lotus Sametime Version Enumeration
auxiliary/scanner/db2/db2_version normal DB2 Probe Utility
auxiliary/scanner/ftp/ftp_version normal FTP Version Scanner
auxiliary/scanner/h323/h323_version normal H.323 Version Scanner
auxiliary/scanner/http/coldfusion_version normal ColdFusion Version Scanner
auxiliary/scanner/http/http_version normal HTTP Version Detection
auxiliary/scanner/http/joomla_version normal Joomla Version Scanner
auxiliary/scanner/http/sap_businessobjects_version_enum normal SAP BusinessObjects Version Detection
auxiliary/scanner/http/ssl_version 2014-10-14 normal HTTP SSL/TLS Version Detection (POODLE scanner)
auxiliary/scanner/http/svn_scanner normal HTTP Subversion Scanner
auxiliary/scanner/imap/imap_version normal IMAP4 Banner Grabber
auxiliary/scanner/ipmi/ipmi_version normal IPMI Information Discovery
auxiliary/scanner/lotus/lotus_domino_version normal Lotus Domino Version
auxiliary/scanner/mysql/mysql_version normal MySQL Server Version Enumeration
auxiliary/scanner/oracle/tnslsnr_version 2009-01-07 normal Oracle TNS Listener Service Version Query
auxiliary/scanner/pop3/pop3_version normal POP3 Banner Grabber
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
auxiliary/scanner/printer/printer_version_info normal Printer Version Information Scanner
auxiliary/scanner/sap/sap_mgmt_con_version normal SAP Management Console Version Detection
auxiliary/scanner/scada/digi_addp_version normal Digi ADDP Information Discovery
auxiliary/scanner/scada/digi_realport_version normal Digi RealPort Serial Server Version
auxiliary/scanner/scada/modbusdetect 2011-11-01 normal Modbus Version Scanner
auxiliary/scanner/smb/smb_version normal SMB Version Detection
auxiliary/scanner/smtp/smtp_version normal SMTP Banner Grabber
auxiliary/scanner/snmp/aix_version normal AIX SNMP Scanner Auxiliary Module
auxiliary/scanner/ssh/ssh_version normal SSH Version Scanner
auxiliary/scanner/telnet/lantronix_telnet_version normal Lantronix Telnet Service Banner Detection
auxiliary/scanner/telnet/telnet_version normal Telnet Service Banner Detection
auxiliary/scanner/vmware/vmauthd_version normal VMWare Authentication Daemon Version Scanner
auxiliary/scanner/vxworks/wdbrpc_version normal VxWorks WDB Agent Version Scanner
exploit/multi/svn/svnserve_date 2004-05-19 average Subversion Date Svnserve
exploit/windows/browser/crystal_reports_printcontrol 2010-12-14 normal Crystal Reports CrystalPrintControl ActiveX ServerResourceVersion Property Overflow
exploit/windows/fileformat/digital_music_pad_pls 2010-09-17 normal Digital Music Pad Version 8.2.3.3.4 Stack Buffer Overflow
exploit/windows/fileformat/orbit_download_failed_bof 2008-04-03 normal Orbit Downloader URL Unicode Conversion Overflow
exploit/windows/fileformat/realplayer_ver_attribute_bof 2013-12-20 normal RealNetworks RealPlayer Version Attribute Buffer Overflow
exploit/windows/ftp/filecopa_list_overflow 2006-07-19 average FileCopa FTP Server Pre 18 Jul Version
exploit/windows/scada/iconics_genbroker 2011-03-21 good Iconics GENESIS32 Integer Overflow Version 9.21.201.01
msf >
很多很多。
下面呢,博主我,以常见的网络服务扫描。
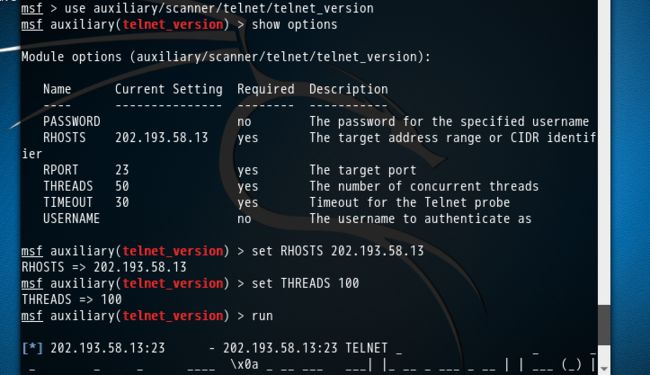
1、Telnet服务扫描
telnet服务的常用端口是23
服务,为下一步进行网络嗅探或口令猜测做好准备。如下所示。
msf > use auxiliary/scanner/telnet/telnet_version msf auxiliary(telnet_version) > show options Module options (auxiliary/scanner/telnet/telnet_version): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD no The password for the specified username RHOSTS 202.193.58.13 yes The target address range or CIDR identifier RPORT 23 yes The target port THREADS 50 yes The number of concurrent threads TIMEOUT 30 yes Timeout for the Telnet probe USERNAME no The username to authenticate as msf auxiliary(telnet_version) > set RHOSTS 202.193.58.13 RHOSTS => 202.193.58.13 msf auxiliary(telnet_version) > set THREADS 100 THREADS => 100 msf auxiliary(telnet_version) > run [*] 202.193.58.13:23 - 202.193.58.13:23 TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin with msfadmin/msfadmin to get started\x0a\x0a\x0ametasploitable login: [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed msf auxiliary(telnet_version) >
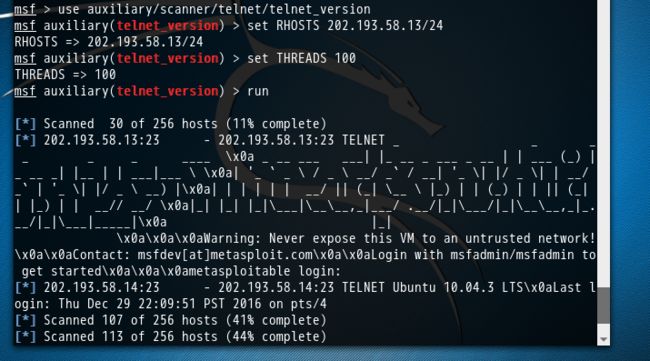
或者
msf > use auxiliary/scanner/telnet/telnet_version msf auxiliary(telnet_version) > set RHOSTS 202.193.58.13/24 RHOSTS => 202.193.58.13/24 msf auxiliary(telnet_version) > set THREADS 100 THREADS => 100 msf auxiliary(telnet_version) > run [*] Scanned 30 of 256 hosts (11% complete) [*] 202.193.58.13:23 - 202.193.58.13:23 TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin with msfadmin/msfadmin to get started\x0a\x0a\x0ametasploitable login: [*] 202.193.58.14:23 - 202.193.58.14:23 TELNET Ubuntu 10.04.3 LTS\x0aLast login: Thu Dec 29 22:09:51 PST 2016 on pts/4 [*] Scanned 107 of 256 hosts (41% complete) [*] Scanned 113 of 256 hosts (44% complete) [*] Scanned 182 of 256 hosts (71% complete) [*] Scanned 183 of 256 hosts (71% complete) [*] Scanned 184 of 256 hosts (71% complete) [*] Scanned 197 of 256 hosts (76% complete) [*] Scanned 206 of 256 hosts (80% complete) [*] Scanned 244 of 256 hosts (95% complete) [*] Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed msf auxiliary(telnet_version) >
当然,大家可以拿这个主机扫描
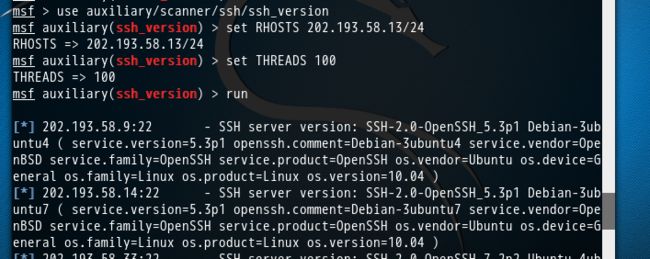
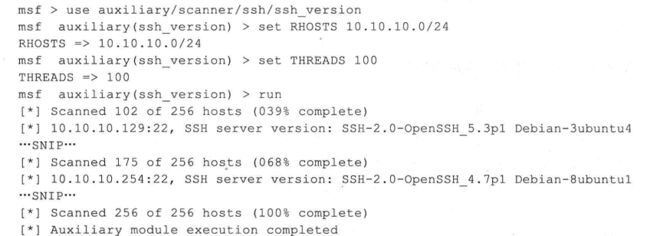
2、ssh服务扫描
ssh服务常用端口为22
![]()
了相应登录用户的所有权限。对网络中开放了SSH服务的主机进行了扫描。
msf > use auxiliary/scanner/ssh/ssh_version msf auxiliary(ssh_version) > set RHOSTS 202.193.58.13/24 RHOSTS => 202.193.58.13/24 msf auxiliary(ssh_version) > set THREADS 100 THREADS => 100 msf auxiliary(ssh_version) > run [*] 202.193.58.9:22 - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4 ( service.version=5.3p1 openssh.comment=Debian-3ubuntu4 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 ) [*] 202.193.58.14:22 - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu7 ( service.version=5.3p1 openssh.comment=Debian-3ubuntu7 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 ) [*] 202.193.58.33:22 - SSH server version: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1 ( service.version=7.2p2 openssh.comment=Ubuntu-4ubuntu2.1 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.certainty=0.75 ) [*] 202.193.58.55:22 - SSH server version: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4 [*] 202.193.58.11:22 - SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4 ( service.version=5.3p1 openssh.comment=Debian-3ubuntu4 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH os.vendor=Ubuntu os.device=General os.family=Linux os.product=Linux os.version=10.04 ) [*] Scanned 57 of 256 hosts (22% complete) [*] Scanned 60 of 256 hosts (23% complete) [*] Scanned 160 of 256 hosts (62% complete) [*] Scanned 162 of 256 hosts (63% complete) [*] Scanned 214 of 256 hosts (83% complete) [*] Scanned 222 of 256 hosts (86% complete) [*] Scanned 249 of 256 hosts (97% complete) [*] Scanned 255 of 256 hosts (99% complete) [*] Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed msf auxiliary(ssh_version) >
当然,大家可以拿这个来扫描
msf > search name:_login Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/admin/mssql/mssql_enum_sql_logins normal Microsoft SQL Server SUSER_SNAME SQL Logins Enumeration auxiliary/admin/oracle/oracle_login 2008-11-20 normal Oracle Account Discovery auxiliary/admin/vmware/terminate_esx_sessions normal VMWare Terminate ESX Login Sessions auxiliary/fuzzers/smb/smb_ntlm1_login_corrupt normal SMB NTLMv1 Login Request Corruption auxiliary/fuzzers/tds/tds_login_corrupt normal TDS Protocol Login Request Corruption Fuzzer auxiliary/fuzzers/tds/tds_login_username normal TDS Protocol Login Request Username Fuzzer auxiliary/scanner/acpp/login normal Apple Airport ACPP Authentication Scanner auxiliary/scanner/afp/afp_login normal Apple Filing Protocol Login Utility auxiliary/scanner/couchdb/couchdb_login normal CouchDB Login Utility auxiliary/scanner/ftp/ftp_login normal FTP Authentication Scanner auxiliary/scanner/http/appletv_login normal AppleTV AirPlay Login Utility auxiliary/scanner/http/axis_login normal Apache Axis2 Brute Force Utility auxiliary/scanner/http/buffalo_login normal Buffalo NAS Login Utility auxiliary/scanner/http/caidao_bruteforce_login normal Chinese Caidao Backdoor Bruteforce auxiliary/scanner/http/chef_webui_login normal Chef Web UI Brute Force Utility auxiliary/scanner/http/cisco_asa_asdm normal Cisco ASA ASDM Bruteforce Login Utility auxiliary/scanner/http/cisco_ironport_enum normal Cisco Ironport Bruteforce Login Utility auxiliary/scanner/http/cisco_ssl_ normal Cisco SSL VPN Bruteforce Login Utility auxiliary/scanner/http/dell_idrac normal Dell iDRAC Default Login auxiliary/scanner/http/dlink_dir_300_615_http_login normal D-Link DIR-300A / DIR-320 / DIR-615D HTTP Login Utility auxiliary/scanner/http/dlink_dir_615h_http_login normal D-Link DIR-615H HTTP Login Utility auxiliary/scanner/http/dlink_dir_session_cgi_http_login normal D-Link DIR-300B / DIR-600B / DIR-815 / DIR-645 HTTP Login Utility auxiliary/scanner/http/dolibarr_login normal Dolibarr ERP/CRM Login Utility auxiliary/scanner/http/etherpad_duo_login normal EtherPAD Duo Login Bruteforce Utility auxiliary/scanner/http/frontpage_login normal FrontPage Server Extensions Anonymous Login Scanner auxiliary/scanner/http/gitlab_login normal GitLab Login Utility auxiliary/scanner/http/glassfish_login normal GlassFish Brute Force Utility auxiliary/scanner/http/hp_sys_mgmt_login normal HP System Management Homepage Login Utility auxiliary/scanner/http/http_login normal HTTP Login Utility auxiliary/scanner/http/infovista_enum normal InfoVista VistaPortal Application Bruteforce Login Utility auxiliary/scanner/http/ipboard_login normal IP Board Login Auxiliary Module auxiliary/scanner/http/jenkins_login normal Jenkins-CI Login Utility auxiliary/scanner/http/joomla_bruteforce_login normal Joomla Bruteforce Login Utility auxiliary/scanner/http/manageengine_desktop_central_login normal ManageEngine Desktop Central Login Utility auxiliary/scanner/http/mybook_live_login normal Western Digital MyBook Live Login Utility auxiliary/scanner/http/octopusdeploy_login normal Octopus Deploy Login Utility auxiliary/scanner/http/openmind_messageos_login normal OpenMind Message-OS Portal Login Brute Force Utility auxiliary/scanner/http/oracle_ilom_login normal Oracle ILO Manager Login Brute Force Utility auxiliary/scanner/http/owa_ews_login normal OWA Exchange Web Services (EWS) Login Scanner auxiliary/scanner/http/owa_login normal Outlook Web App (OWA) Brute Force Utility auxiliary/scanner/http/pocketpad_login normal PocketPAD Login Bruteforce Force Utility auxiliary/scanner/http/radware_appdirector_enum normal Radware AppDirector Bruteforce Login Utility auxiliary/scanner/http/rfcode_reader_enum normal RFCode Reader Web Interface Login / Bruteforce Utility auxiliary/scanner/http/sentry_cdu_enum normal Sentry Switched CDU Bruteforce Login Utility auxiliary/scanner/http/sevone_enum 2013-06-07 normal SevOne Network Performance Management Application Brute Force Login Utility auxiliary/scanner/http/splunk_web_login normal Splunk Web Interface Login Utility auxiliary/scanner/http/symantec_web_gateway_login normal Symantec Web Gateway Login Utility auxiliary/scanner/http/tomcat_mgr_login normal Tomcat Application Manager Login Utility auxiliary/scanner/http/typo3_bruteforce normal Typo3 Login Bruteforcer auxiliary/scanner/http/vcms_login normal V-CMS Login Utility auxiliary/scanner/http/wordpress_login_enum normal WordPress Brute Force and User Enumeration Utility auxiliary/scanner/http/wordpress_xmlrpc_login normal Wordpress XML-RPC Username/Password Login Scanner auxiliary/scanner/http/zabbix_login normal Zabbix Server Brute Force Utility auxiliary/scanner/lotus/lotus_domino_login normal Lotus Domino Brute Force Utility auxiliary/scanner/misc/cctv_dvr_login normal CCTV DVR Login Scanning Utility auxiliary/scanner/misc/oki_scanner normal OKI Printer Default Login Credential Scanner auxiliary/scanner/mongodb/mongodb_login normal MongoDB Login Utility auxiliary/scanner/msf/msf_rpc_login normal Metasploit RPC Interface Login Utility auxiliary/scanner/msf/msf_web_login normal Metasploit Web Interface Login Utility auxiliary/scanner/mssql/mssql_login normal MSSQL Login Utility auxiliary/scanner/mysql/mysql_login normal MySQL Login Utility auxiliary/scanner/nessus/nessus_ntp_login normal Nessus NTP Login Utility auxiliary/scanner/nessus/nessus_rest_login normal Nessus RPC Interface Login Utility auxiliary/scanner/nessus/nessus_xmlrpc_login normal Nessus XMLRPC Interface Login Utility auxiliary/scanner/nexpose/nexpose_api_login normal NeXpose API Interface Login Utility auxiliary/scanner/openvas/openvas_gsad_login normal OpenVAS gsad Web Interface Login Utility auxiliary/scanner/openvas/openvas_omp_login normal OpenVAS OMP Login Utility auxiliary/scanner/openvas/openvas_otp_login normal OpenVAS OTP Login Utility auxiliary/scanner/oracle/isqlplus_login normal Oracle iSQL*Plus Login Utility auxiliary/scanner/oracle/oracle_login normal Oracle RDBMS Login Utility auxiliary/scanner/pcanywhere/pcanywhere_login normal PcAnywhere Login Scanner auxiliary/scanner/pop3/pop3_login normal POP3 Login Utility auxiliary/scanner/postgres/postgres_login normal PostgreSQL Login Utility auxiliary/scanner/redis/redis_login normal Redis Login Utility auxiliary/scanner/rservices/rexec_login normal rexec Authentication Scanner auxiliary/scanner/rservices/rlogin_login normal rlogin Authentication Scanner auxiliary/scanner/rservices/rsh_login normal rsh Authentication Scanner auxiliary/scanner/sap/sap_mgmt_con_brute_login normal SAP Management Console Brute Force auxiliary/scanner/sap/sap_soap_rfc_brute_login normal SAP SOAP Service RFC_PING Login Brute Forcer auxiliary/scanner/sap/sap_web_gui_brute_login normal SAP Web GUI Login Brute Forcer auxiliary/scanner/scada/koyo_login 2012-01-19 normal Koyo DirectLogic PLC Password Brute Force Utility auxiliary/scanner/smb/smb_login normal SMB Login Check Scanner auxiliary/scanner/snmp/snmp_login normal SNMP Community Login Scanner auxiliary/scanner/ssh/karaf_login normal Apache Karaf Login Utility auxiliary/scanner/ssh/ssh_login normal SSH Login Check Scanner auxiliary/scanner/ssh/ssh_login_pubkey normal SSH Public Key Login Scanner auxiliary/scanner/telnet/brocade_enable_login normal Brocade Enable Login Check Scanner auxiliary/scanner/telnet/telnet_login normal Telnet Login Check Scanner auxiliary/scanner/vmware/vmauthd_login normal VMWare Authentication Daemon Login Scanner auxiliary/scanner/vmware/vmware_http_login normal VMWare Web Login Scanner auxiliary/scanner/vnc/vnc_login normal VNC Authentication Scanner auxiliary/scanner/winrm/winrm_login normal WinRM Login Utility auxiliary/voip/asterisk_login normal Asterisk Manager Login Utility exploit/dialup/multi/login/manyargs 2001-12-12 good System V Derived /bin/login Extraneous Arguments Buffer Overflow exploit/linux/http/airties_login_cgi_bof 2015-03-31 normal Airties login-cgi Buffer Overflow exploit/linux/http/belkin_login_bof 2014-05-09 normal Belkin Play N750 login.cgi Buffer Overflow exploit/linux/misc/hp_vsa_login_bof 2013-06-28 normal HP StorageWorks P4000 Virtual SAN Appliance Login Buffer Overflow exploit/multi/http/coldfusion_rds 2013-08-08 great Adobe ColdFusion 9 Administrative Login Bypass exploit/osx/afp/loginext 2004-05-03 average AppleFileServer LoginExt PathName Overflow exploit/windows/brightstor/lgserver_rxrlogin 2007-06-06 average CA BrightStor ARCserve for Laptops and Desktops LGServer Buffer Overflow exploit/windows/http/hp_power_manager_login 2009-11-04 average Hewlett-Packard Power Manager Administration Buffer Overflow exploit/windows/http/integard_password_bof 2010-09-07 great Race River Integard Home/Pro LoginAdmin Password Stack Buffer Overflow exploit/windows/http/solarwinds_fsm_userlogin 2015-03-13 excellent Solarwinds Firewall Security Manager 6.6.5 Client Session Handling Vulnerability exploit/windows/imap/mailenable_login 2006-12-11 great MailEnable IMAPD (2.34/2.35) Login Request Buffer Overflow exploit/windows/imap/mercur_login 2006-03-17 average Mercur Messaging 2005 IMAP Login Buffer Overflow exploit/windows/imap/mercury_login 2007-03-06 average Mercury/32 LOGIN Buffer Overflow exploit/windows/misc/hp_dataprotector_dtbclslogin 2010-09-09 normal HP Data Protector DtbClsLogin Buffer Overflow exploit/windows/scada/realwin_on_fcs_login 2011-03-21 great RealWin SCADA Server DATAC Login Buffer Overflow post/osx/gather/autologin_password normal OSX Gather Autologin Password as Root post/windows/gather/credentials/windows_autologin normal Windows Gather AutoLogin User Credential Extractor msf >
同时,还可以利用ssh_login模块进行SSH服务口令破解。
![]()
![]()
通过暴力破解知道密码为ubuntu,
![]()
可以看到通过口令破解已经获得了一个10.10.10.254机器的shell
可以对该机器再进一步提权获得更多信息
当然,使用的字典还是非常重要的,还需要使用社会工程学加以完善
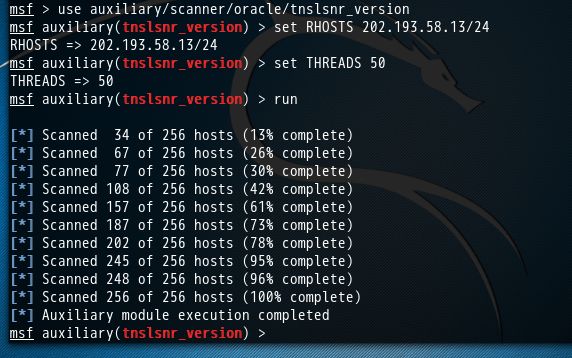
3、Orcal数据库服务查点
oracle数据库监听器tnslsnr默认端口为1521
msf > use auxiliary/scanner/oracle/tnslsnr_version msf auxiliary(tnslsnr_version) > set RHOSTS 202.193.58.13/24 RHOSTS => 202.193.58.13/24 msf auxiliary(tnslsnr_version) > set THREADS 50 THREADS => 50 msf auxiliary(tnslsnr_version) > run [*] Scanned 34 of 256 hosts (13% complete) [*] Scanned 67 of 256 hosts (26% complete) [*] Scanned 77 of 256 hosts (30% complete) [*] Scanned 108 of 256 hosts (42% complete) [*] Scanned 157 of 256 hosts (61% complete) [*] Scanned 187 of 256 hosts (73% complete) [*] Scanned 202 of 256 hosts (78% complete) [*] Scanned 245 of 256 hosts (95% complete) [*] Scanned 248 of 256 hosts (96% complete) [*] Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed msf auxiliary(tnslsnr_version) >
当然,大家也可以拿下面的主机来,
4、代理服务器探测
当如果靶机开启了代理服务器来隐藏自己身份的时候,我们使用auxiliary/scanner/http/open_proxy,可以探测到代理服务器的使用