高通平台(8917/8937/8953...) secure boot 软件配置
以下以8917平台为例,其他平台类似,找到对应配置文件即可
1.新建临时目录
mkdir tmp
cd tmp
2.复制openssl文件到临时目录
cp ../LA.UM.*/LINUX/android/vendor/qcom/proprietary/common/scripts/gensecimage/qpsa/alt_resources/default/openssl/opensslroot.cfg ./
cp ../LA.UM.*/LINUX/android/vendor/qcom/proprietary/common/scripts/gensecimage/qpsa/alt_resources/default/openssl/v3.ext ./
3.生成证书文件等
openssl genrsa -out oem_rootca.key -3 2048
openssl req -new -key oem_rootca.key -x509 -out oem_rootca.crt -subj /C="US"/ST="CA"/L="SANDIEGO"/O="OEM"/OU="General OEM rootca"/CN="OEM ROOT CA" -days 7300 -set_serial 1 -config opensslroot.cfg
openssl genrsa -out oem_attestca.key -3 2048
openssl req -new -key oem_attestca.key -out oem_attestca.csr -subj /C="US"/ST="CA"/L="SANDIEGO"/O="OEM"/OU="General OEM attestation CA"/CN="OEM attestation CA" -days 7300 -config opensslroot.cfg
openssl x509 -req -in oem_attestca.csr -CA oem_rootca.crt -CAkey oem_rootca.key -out oem_attestca.crt -set_serial 5 -days 7300 -extfile v3.ext
openssl x509 -in oem_rootca.crt -inform PEM -out oem_rootca.cer -outform DER
openssl x509 -in oem_attestca.crt -inform PEM -out oem_attestca.cer -outform DER
4.重命名证书文件并生成对应哈希值
mv oem_rootca.key qpsa_rootca.key
mv oem_attestca.key qpsa_attestca.key
mv oem_rootca.cer qpsa_rootca.cer
mv oem_attestca.cer qpsa_attestca.cer
openssl dgst -sha256 qpsa_rootca.cer
这里生成的SHA256(qpsa_rootca.cer)值需要保存,如下修改配置文件
MSM8917.LA.3.2.1/common/sectools/config/8917/8917_fuseblower_USER.xml
contains the OEM public key hash as set by OEM
root_cert_hash
- 0000000000000000000000000000000000000000000000000000000000000000
+ df6d19a0095ffd6c76cfa79d5b2fb55a0ef93313f8cf345ecab8cba99cde7951
SHA256 signed root cert to generate root hash
@@ -38,7 +38,7 @@
PK Hash is in Fuse for SEC_BOOT1 : Apps
SEC_BOOT1_PK_Hash_in_Fuse
- false
+ true
If PK Hash in Fuse is 0, then this index selects which of 16 keys in ROM to use
@@ -53,7 +53,7 @@
PK Hash is in Fuse for SEC_BOOT2 : MBA
SEC_BOOT2_PK_Hash_in_Fuse
- false
+ true
If PK Hash in Fuse is 0, then this index selects which of 16 keys in ROM to use
@@ -68,7 +68,7 @@
PK Hash is in Fuse for SEC_BOOT3 : MPSS
SEC_BOOT3_PK_Hash_in_Fuse
- false
+ true
5.将生成证书文件copy到对应目录
cp qpsa_rootca.key qpsa_attestca.key qpsa_rootca.cer qpsa_attestca.cer ../MSM8917.LA.3.2.1/common/sectools/resources/data_prov_assets/Signing/Local/qti_presigned_certs-key2048_exp65537/
qti_presigned_certs-key2048_exp65537 这个文件取决于项目配置
MSM8917.LA.3.2.1\common\sectools\config\8917\8917_secimage.xml
......
2048
65537
......
6.生成sec.dat文件并进行validate
cd ../MSM8917.LA.3.2.1/common/sectools/
# 生成sec.dat文件,生成路径: fuseblower_output/v2/sec.dat
python sectools.py fuseblower -e config/8917/8917_fuseblower_OEM.xml -q config/8917/8917_fuseblower_QTI.xml -u config/8917/8917_fuseblower_USER.xml -g verbose -vvv
# 校验sec.dat和xml配置是否匹配,成功提示 Validate Successful!
python sectools.py fuseblower --oem_config_path=config/8917/8917_fuseblower_OEM.xml --qti_config_path=config/8917/8917_fuseblower_QTI.xml --user_config_path=config/8917/8917_fuseblower_USER.xml --secdat=fuseblower_output/v2/sec.dat --validate
7.工具弄好好,对image进行签名
理论上,8917_secimage.xml文件中有的image都需要进行签名
cd MSM8917.LA.3.2.1/common/sectools/
# 8917_secimage.xml中配置的image整体签名,签名后文件保存到 ./sec_output 目录下
python sectools.py secimage -m ../../../MSM8917.LA.3.2.1 -c ./config/8917/8917_secimage.xml -o ./sec_output -sa
# 对单个文件进行签名操作
# python sectools.py secimage -i ../../../BOOT.BF.3.3.2/boot_images/build/ms/bin/JAASANAZ/sbl1.mbn -c ./config/8917/8917_secimage.xml -o ./sec_output -sa
8.重新生成NON-HLOS.bin,将image放到download_image
将wcnss.mbn,mba.mbn,qdsp6sw.mbn(签名后叫modem.mbn)重新放回源目录下,到common/build下面执行python update_common_info.py,更新modem分区
cp sec_output/8917/appsbl/emmc_appsboot.mbn $IMAGES_DIR/
cp sec_output/8917/prog_emmc_firehose_ddr/prog_emmc_firehose_8917_ddr.mbn $IMAGES_DIR/
cp sec_output/8917/rpm/rpm.mbn $IMAGES_DIR/
cp sec_output/8917/sbl1/sbl1.mbn $IMAGES_DIR/
cp sec_output/8917/devcfg/devcfg.mbn $IMAGES_DIR/
cp sec_output/8917/keymaster/km4.mbn $IMAGES_DIR/
cp sec_output/8917/qsee/tz.mbn $IMAGES_DIR/
cp sec_output/8917/smplap32/smplap32.mbn $IMAGES_DIR/
cp sec_output/8917/smplap64/smplap64.mbn $IMAGES_DIR/
cp sec_output/8917/cmnlib/cmnlib_30.mbn $IMAGES_DIR/
cp sec_output/8917/cmnlib64/cmnlib64_30.mbn $IMAGES_DIR/
cp sec_output/8917/cmnlib/cmnlib_30.mbn $TZ_DIR/
cp sec_output/8917/cmnlib64/cmnlib64_30.mbn $TZ_DIR/
cp sec_output/8917/cppf/cppf.mbn $TZ_DIR/
cp sec_output/8917/dhsecapp/dhsecapp.mbn $TZ_DIR/
cp sec_output/8917/fingerprint/fingerprint.mbn $TZ_DIR/
cp sec_output/8917/fingerprint64/fingerprint64.mbn $TZ_DIR/
cp sec_output/8917/isdbtmm/isdbtmm.mbn $TZ_DIR/
cp sec_output/8917/widevine/widevine.mbn $TZ_DIR/
cp sec_output/8917/mdtp/mdtp.mbn $TZ_DIR/
cp sec_output/8917/qmpsecap/qmpsecap.mbn $TZ_DIR/
cp sec_output/8917/mba/mba.mbn $MPSS_DIR/
cp sec_output/8917/modem/modem.mbn $MPSS_DIR/qdsp6sw.mbn
cp sec_output/8917/venus/venus.mbn $VIDEO_DIR
cp sec_output/8917/wcnss/wcnss.mbn ../../../CNSS.PR.4.0.3/wcnss_proc/build/ms/bin/8937/reloc
cp sec_output/8917/adsp/adsp.mbn ../../../ADSP.VT.3.0/adsp_proc/obj/8937/signed/
cp common_output/v2/sec.dat $IMAGES_DIR/
cd ../../..
# 重新生成下NON-HLOS.bin
cd ./MSM8917.LA.3.2.1/common/build
python build.py --nonhlos
cp bin/asic/NON-HLOS.bin $IMAGES_DIR/
9.刷机
只有导入sec.dat文件才是真正的secure boot版本,有两种方式:
1、刷机时配置下刷机包中rawprogram_unsparse.xml文件
filename=“sec.dat” 这里写上sec.dat即可。默认是空的值,表示不写入。
2、使用fastboot工具将步骤6生成的sec.dat刷到sec分区
adb root
adb reboot bootloader
fastboot flash sec sec.dat
fastboot reboot
10.验证
进入fastboot模式,查看即可
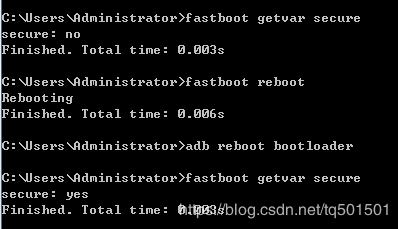
如果已启动secure boot,可以看到提示 secure: yes。
切记机器中刷入了sec.dat后,就无法刷其他非相同签名的 secure 版本了。
11.启动secure boot后刷机
启动secure boot后,还是使用QFIL工具刷机,但是需要修改一处代码,跳过烧录时对secure boot检查。建议(必须)一开始就同步修改。
BOOT.BF.3.3/boot_images/core/storage/tools/deviceprogrammer_ddr/src/firehose/deviceprogrammer_initialize.c
- if (FALSE == isValidationMode() && TRUE == isAuthenticationEnabled())
- {
- strlcat(err_log, "Secure boot detected. VIP not enabled:fail ", sizeof(err_log));
- }
+ // if (FALSE == isValidationMode() && TRUE == isAuthenticationEnabled())
+ // {
+ // strlcat(err_log, "Secure boot detected. VIP not enabled:fail ", sizeof(err_log));
+ // }