buu reverse 5题 pwn简单nc 1题
1.新年快乐
if ( !strncmp((const char *)&v5, &v4, strlen(&v4)) )
result = puts("this is true flag!");
v5与v4比较,v4=HappyNewYear!
flag{HappyNewYear!}
2.[BJDCTF 2nd]guessgame1
无壳,拉入64位ida
F5伪代码,shilf+F12查看字符串,直接出来

BJD{S1mple_ReV3r5e_W1th_0D_0r_IDA}
3.helloword
这个了解到apk改之理
用apk改之理打开,找到helloword,一个个查找,看到flag

flag{7631a988259a00816deda84afb29430a}
4.不一样的flag
这道题,了解到迷宫题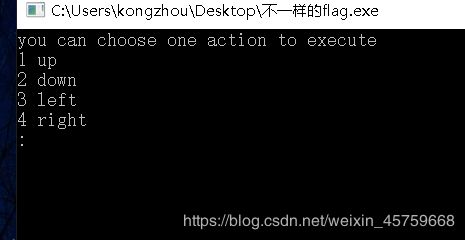
查看一下
无壳,拉入32位ida,找到main函数,F5获得伪代码
shilf+F12,看到一串字符,有25位,5*5的迷宫

if ( *((_BYTE *)&v8 + 5 * v4 + v5 - 41) == '1' )
exit(1);
if ( *((_BYTE *)&v8 + 5 * v4 + v5 - 41) == '#' )
{
puts("\nok, the order you enter is the flag!");
exit(0);
有上述代码得到,1停,#输出得到flag,从*开始,所以1为墙,0为路径
*1111
01000
01010
00010
1111#
flag{222441144222}
5.findit
下载附件是apk后缀,这个也是apk改之理打开

寻找findit看到两段长的十六进制数字,全部转化为ascll
转换为=ThisIsTheFlagHome
了解后转换第二段=pvkq{m164675262033I4m49Inp7p9mnk28k75}
看这个直接用凯撒密码

flag{c164675262033Y4c49Ydf7f9cda28a75}
后来看wp,可以写脚本
a = [0x70,
0x76,
0x6b,
0x71,
0x7b,
0x6d,
0x31,
0x36,
0x34,
0x36,
0x37,
0x35,
0x32,
0x36,
0x32,
0x30,
0x33,
0x33,
0x6c,
0x34,
0x6d,
0x34,
0x39,
0x6c,
0x6e,
0x70,
0x37,
0x70,
0x39,
0x6d,
0x6e,
0x6b,
0x32,
0x38,
0x6b,
0x37,
0x35,
0x7d,
]
x = ""
for i in a:
x += chr(i)
print(x)
直接就出来了


