基于linux下的iptables网络过滤器
iptables是什么?
1,IPTABLES 是与最新的3.5版本Linux内核集成的IP信息包过滤系统。如果Linux系统连接到因特网或LAN服务器或
连接LAN和因特网的代理服务器,则该系统有利于在Linux系统上更好地控制IP信息包过滤和防火墙配置。
2,防火墙在做信息包过滤决定时,有一套遵循和组成的规则,这些规则存储在专用的信息包过滤表中,而这些表集成
在 Linux 内核中。在信息包过滤表中,规则被分组放在我们所谓的链(chain)中。而netfilter/iptables IP信息包过滤系统
是一款功能强大的工具,可用于添加、编辑和移除规则。
3,虽然 netfilter/iptables IP 信息包过滤系统被称为单个实体,但它实际上由两个组件netfilter和iptables组成。
netfilter 组件也称为内核空间(kernelspace),是内核的一部分,由一些信息包过滤表组成,这些表包含内核用来控制信息包
过滤处理的规则集。iptables 组件是一种工具,也称为用户空间(userspace),它使插入、修改和除去信息包过滤表中的规则
变得容易。
4,iptables防火墙策略的规则的匹配顺序是从上往下的,因此要把较为严格,优先级高的策略规则放到前面,以免发生错误。
iptables默认的防火墙,链结构:

iptables的表名,链结构:
表名包括:
raw:高级功能,如:网址过滤。
mangle:数据包修改(QOS),用于实现服务质量。
nat:地址转换,用于网关路由器。
filter:包过滤,用于防火墙规则。
规则链名包括:
INPUT链:处理输入数据包。
OUTPUT链:处理输出数据包。
FORWARD链:处理转发数据包。
PREROUTING链:用于目标地址转换(DNAT)。
POSTOUTING链:用于源地址转换(SNAT)。
动作包括:
accept:接收数据包。
DROP:丢弃数据包。
REDIRECT:重定向、映射、透明代理。
SNAT:源地址转换。
DNAT:目标地址转换。
MASQUERADE:IP伪装(NAT),用于ADSL。
LOG:日志记录。
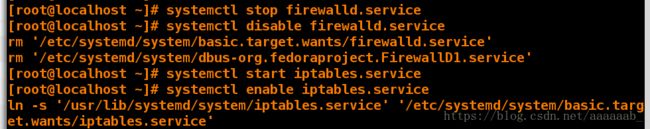
启动iptables服务:
[root@desktop Desktop]# systemctl stop firewalld 关闭防火墙
[root@desktop Desktop]# systemctl disable firewalld 开机自动关闭防火墙
rm '/etc/systemd/system/basic.target.wants/firewalld.service'
rm '/etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service'
[root@desktop Desktop]# systemctl start iptables.service 开启iptables服务
[root@desktop Desktop]# systemctl enable iptables.service 开机自动启动iptables服务
ln -s '/usr/lib/systemd/system/iptables.service' '/etc/systemd/system/basic.target.wants/iptables.service'
iptables的参数配置:
| 参数 | 作用 |
|---|---|
| -p | 设置默认策略 |
| -F | 清空规则链 |
| -L | 查看规则链 |
| -A | 在规则链的末尾加入新规则 |
| -I num | 在规则链的头部加入新规则 |
| -D num | 删除某一条规则 |
| -s | 匹配来源地址 IP/MASK,加叹号!表示除这个IP以外 |
| -d | 匹配目标地址 |
| -i 网卡名称 | 匹配从这块网卡流入的数据 |
| -o 网卡名称 | 匹配从这块网卡流出的数据 |
| -p | 匹配协议,如TCP,UDP,ICMP |
| –dport num | 匹配目标端口号 |
| –sport num | 匹配来源端口号 |
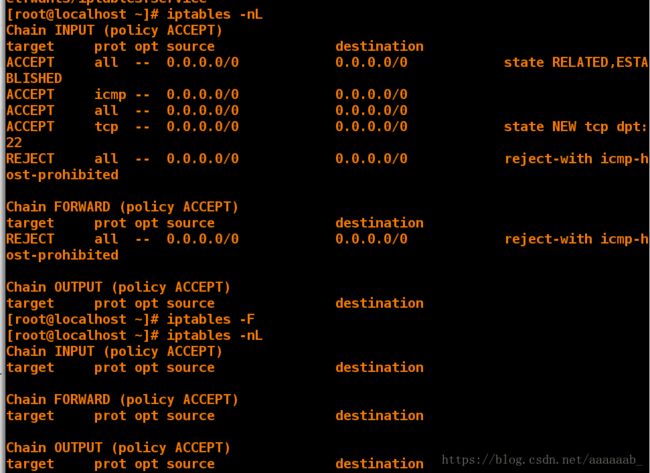
[root@desktop Desktop]# iptables -nL 查看iptables策略信息
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -F 刷新iptables
[root@desktop Desktop]# iptables -nL 查看iptables策略信息
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# service iptables save 保存
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
[root@desktop Desktop]# vim /etc/sysconfig/iptables 查看保存的策略文件
[root@desktop Desktop]# cd
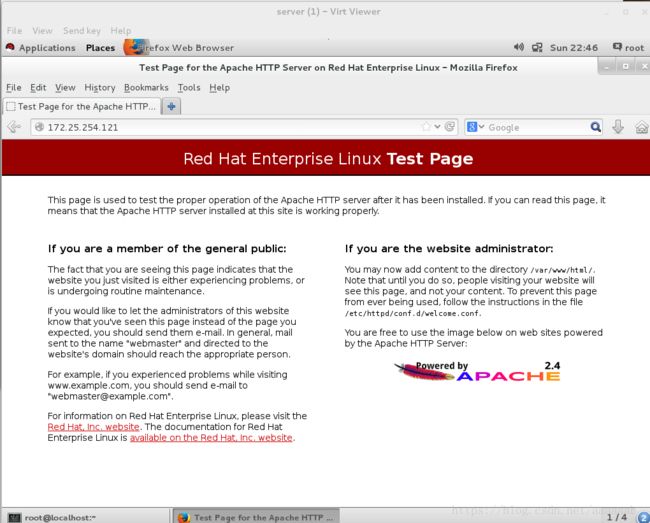
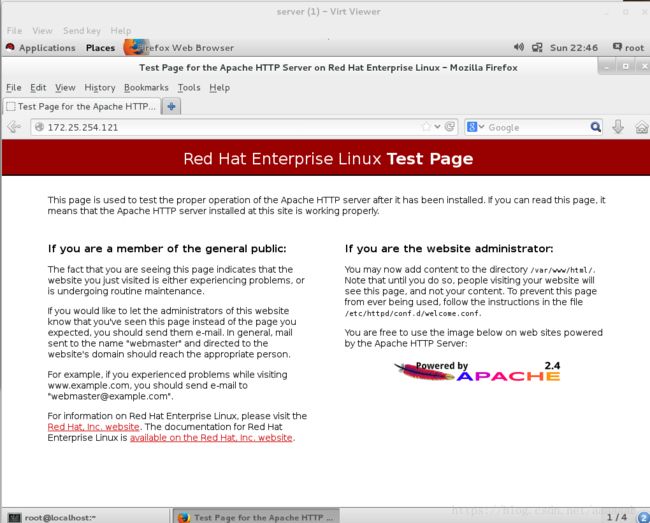
[root@desktop Desktop]# systemctl start httpd 首先打开阿帕其服务才可以进行网页测试

真机测试可以访问:

虚拟机测试可以访问:
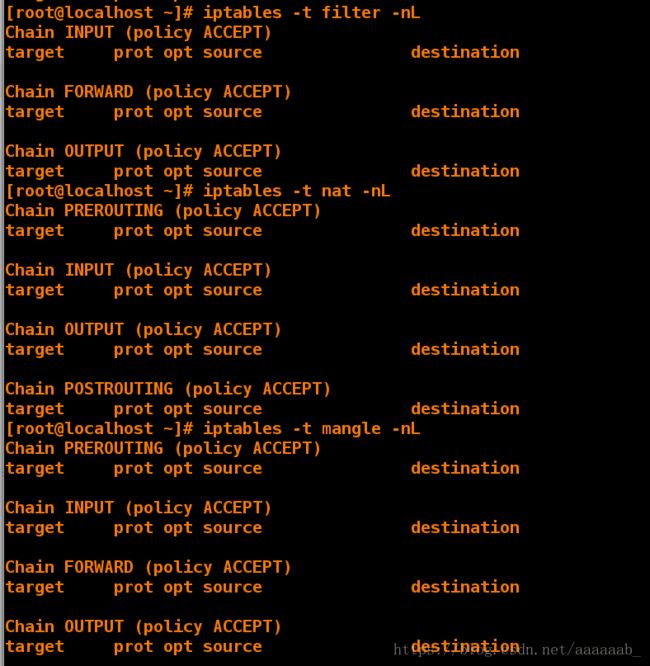
[root@desktop Desktop]# iptables -t filter -nL 查看filter表策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -t nat -nL 查看nat表策略
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -t mangle -nL 查看mangle表策略
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
添加防火墙策略:
[root@desktop Desktop]# iptables -P INPUT DROP 设置为丢弃状态
[root@desktop Desktop]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination 用真机和虚拟机测试一直转圈,因为丢弃状态不返回值

真机测试不可访问:
虚拟机测试不可访问:
[root@desktop Desktop]# iptables -P INPUT ACCEPT 重新改到接受
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 80 -j REJECT 将80端口设置为拒绝
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -D INPUT 1 删除策略
[root@desktop Desktop]# iptables -A INPUT -s 172.25.254.84 -p tcp --dport 80 -j ACCEPT 设置84主机可以访问,用真机和虚拟机测试发现均可以连接,80端口为http的端口
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 172.25.254.84 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination

真机测试:

虚拟机测试:
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 80 -j REJECT 拒绝其他用户访问,iptables从上到下读取,不拒绝的话其他用户还可以访问
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 172.25.254.84 0.0.0.0/0 tcp dpt:80
REJECT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination

真机测试:

虚拟机测试不可以访问:
[root@desktop Desktop]# iptables -D INPUT 2 删除策略
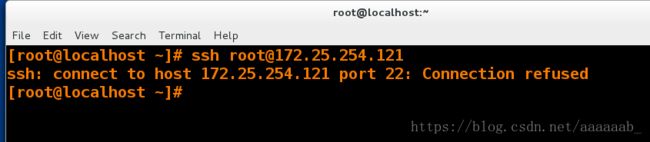
[root@desktop Desktop]# iptables -R INPUT 1 -s 172.25.254.21 -p tcp --dport 22 -j ACCEPT 允许21连接ssh服务
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 22 -j REJECT 拒绝其他主机连接
[root@desktop Desktop]# iptables -nL 用真机可以连接,其他主机无法连接
[root@desktop Desktop]# iptables -F 刷新
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination

真机测试可以使用ssh连接:

虚拟机测试不可以使用ssh连接:
iptables的常规配置:
[root@desktop Desktop]# iptables -F 刷新
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
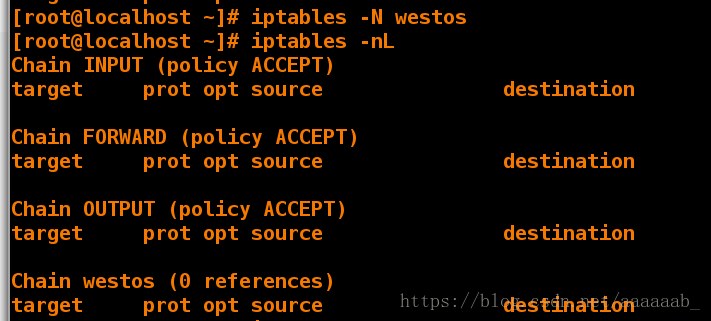
[root@desktop Desktop]# iptables -N westos 添加一行
[root@desktop Desktop]# iptables -nL 查看策略多出来一行
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain westos (0 references)
target prot opt source destination
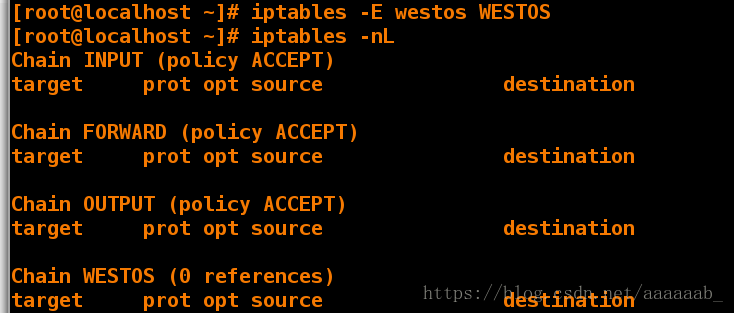
[root@desktop Desktop]# iptables -E westos WESTOS 更改名字为大写
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain WESTOS (0 references)
target prot opt source destination
[root@desktop Desktop]# iptables -X WESTOS 删除WESTOS表
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
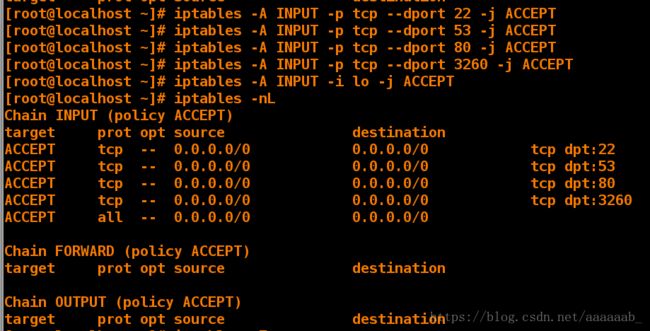
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT 允许访问22端口
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 53 -j ACCEPT 允许访问53端口
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 80 -j ACCEPT 允许访问80端口
[root@desktop Desktop]# iptables -A INPUT -p tcp --dport 3260 -j ACCEPT 允许访问3260端口
[root@desktop Desktop]# iptables -A INPUT -i lo -j ACCEPT 允许访问回环端口
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:53
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3260
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -F 刷新策略
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
将已经建立的和正在进行的设置允许访问
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -p tcp --dport 22 -j ACCEPT 允许22端口
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -p tcp --dport 53 -j ACCEPT 允许3端口
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -p tcp --dport 80 -j ACCEPT 允许80端口
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPT 允许443端口
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -p tcp --dport 3260 -j ACCEPT 允许3260端口
[root@desktop Desktop]# iptables -A INPUT -m state --state NEW -i lo -j ACCEPT 允许回环接口
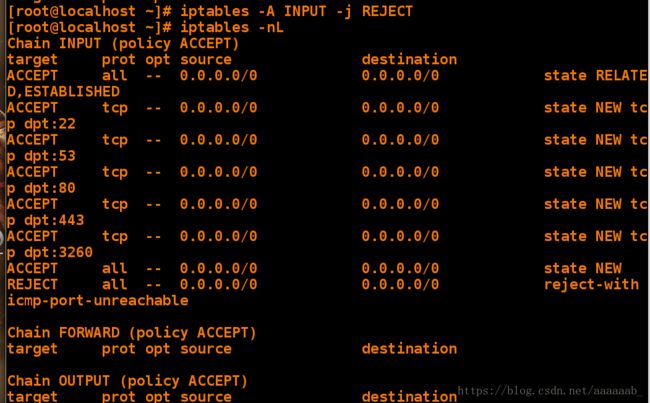
[root@localhost ~]# iptables -A INPUT -j REJECT 拒绝其他
[root@localhost ~]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:53
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:80
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:443
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:3260
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state NEW
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
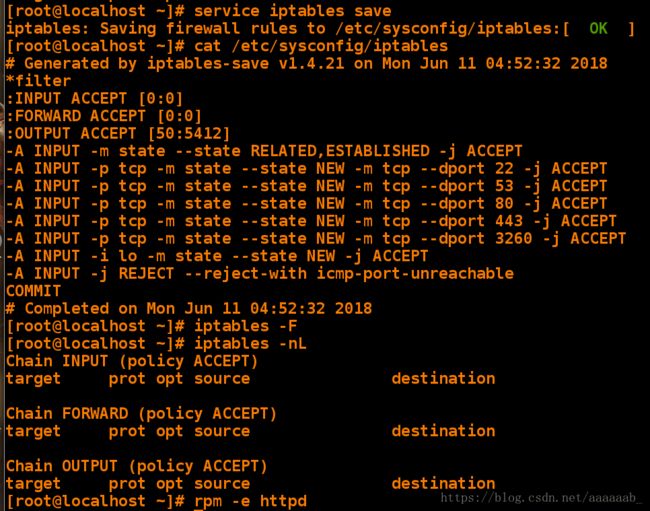
[root@localhost ~]# service iptables save 保存策略
[root@localhost ~]# cat /etc/sysconfig/iptables 查看策略文件
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 3260 -j ACCEPT
-A INPUT -i lo -m state --state NEW -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-port-unreachable
COMMIT
[root@desktop Desktop]# iptables -F 刷新
[root@desktop Desktop]# iptables -nL 查看策略
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@desktop Desktop]# rpm -e httpd 卸载阿帕其
iptables的地址伪装:
[root@localhost yum.repos.d]# nm-connection-editor 配置双网段IP,多添加一块网卡
[root@localhost yum.repos.d]# ifconfig 查看IP
eth0: flags=4163 mtu 1500
inet 172.25.254.121 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::5054:ff:feed:2ec6 prefixlen 64 scopeid 0x20
ether 52:54:00:ed:2e:c6 txqueuelen 1000 (Ethernet)
RX packets 188 bytes 29829 (29.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 129 bytes 22329 (21.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163 mtu 1500
inet 172.25.0.121 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fedb:cabf prefixlen 64 scopeid 0x20
ether 52:54:00:db:ca:bf txqueuelen 1000 (Ethernet)
RX packets 288 bytes 48105 (46.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 27 bytes 3873 (3.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@localhost yum.repos.d]# iptables -F 刷新策略
[root@localhost yum.repos.d]# iptables -t nat -nL 查看策略
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
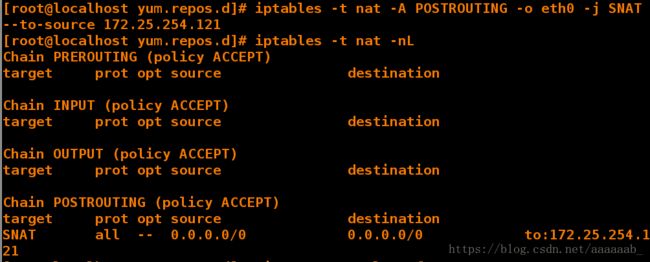
[root@localhost yum.repos.d]# iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to-source 172.25.254.121
在nat表中添加若ip为172.25.0.221的主机连接172.25.254.84的主机时,通过本台主机的eth0网卡路由转换伪装为
172.25.254.121这个ip去连接的策略.
[root@localhost yum.repos.d]# iptables -t nat -nL 查看策略
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.254.121
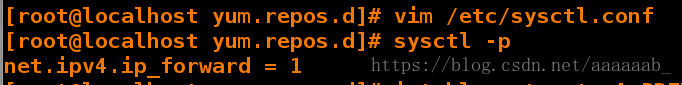
[root@localhost yum.repos.d]# vim /etc/sysctl.conf 打开路由协议
[root@localhost yum.repos.d]# sysctl -p
net.ipv4.ip_forward = 1
在server虚拟机测试:
[root@localhost Desktop]# ifconfig 配置0网段IP
eth0: flags=4163 mtu 1500
inet 172.25.0.221 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fe00:540b prefixlen 64 scopeid 0x20
ether 52:54:00:00:54:0b txqueuelen 1000 (Ethernet)
RX packets 206 bytes 32066 (31.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 181 bytes 31449 (30.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@localhost Desktop]# route -n 配置网关
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.25.0.121 0.0.0.0 UG 1024 0 0 eth0
172.25.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
[root@localhost Desktop]# ping 172.25.254.84 可以ping的通主机
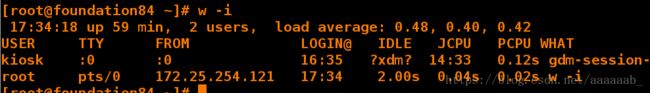
[root@localhost Desktop]# ssh [email protected] 连接主机
[root@foundation84 ~]# w -i 查看时为172.25.254.121,以及伪装成功
17:34:18 up 59 min, 2 users, load average: 0.48, 0.40, 0.42
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
kiosk :0 :0 16:35 ?xdm? 14:33 0.12s gdm-session-
root pts/0 172.25.254.121 17:34 2.00s 0.04s 0.02s w -i
在Desktop添加策略:
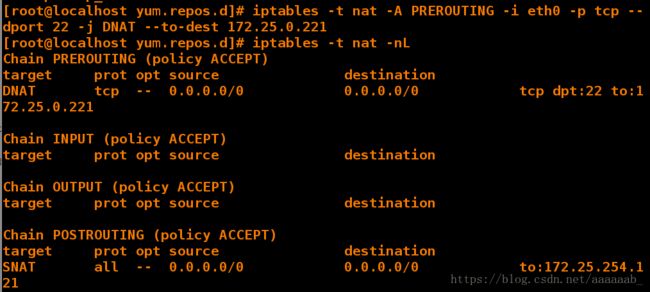
[root@localhost yum.repos.d]# iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 22 -j DNAT --to-dest 172.25.0.221
添加策略在nat表中添加若ip为172.25.254.84的主机发现连接自己的主机ip为172.25.254.121,主动去连接时直接
显示server主机的IP
[root@localhost yum.repos.d]# iptables -t nat -nL 查看策略
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 to:172.25.0.221
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:172.25.254.121
在真机测试:
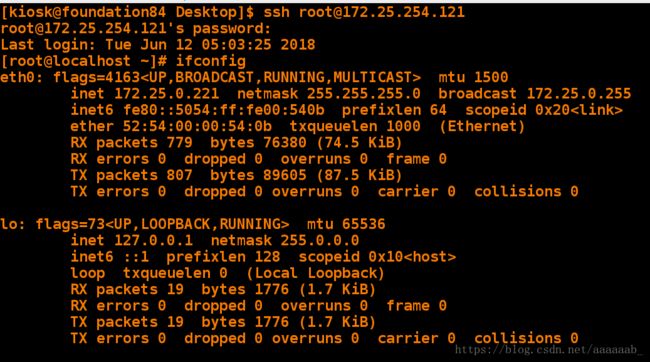
[kiosk@foundation84 Desktop]$ ssh [email protected] 连接双网卡主机
[root@localhost ~]# ifconfig 查看IP为单网卡IP
eth0: flags=4163 mtu 1500
inet 172.25.0.221 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fe00:540b prefixlen 64 scopeid 0x20
ether 52:54:00:00:54:0b txqueuelen 1000 (Ethernet)
RX packets 779 bytes 76380 (74.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 807 bytes 89605 (87.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0