运维自动化之ANSIBLE DNS服务和 BIND
1、详细叙述ansible的工作原理
ansible是一个适用于中小型环境的自动化运维工具。主机总数在500台左右试用。超过500台不建议使用ansible,可以考虑Saltstack、Puppet等。
ansible作为一个管理控制主机的工具,他不需要在被管理的主机上安装插件或者代理软件。这一优点叫做agentless。他可以直接通过ssh服务来管理其他的主机,因此提前把控制主机的pub key导入到所有被控制主机很有必要的。但是同时agentless也是一个缺点,不适合管理大型的环境,通过ssh管理的效率低,这时候就需要其他的有agent的管理软件了。
ansible命令执行过程
- 加载自己的配置文件 默认/etc/ansible/ansible.cfg
- 加载自己对应的模块文件,如command
- 通过ansible将模块或命令生成对应的临时py文件,并将该 文件传输至远程服务器的对应执行用户$HOME/.ansible/tmp/ansible-tmp-数字/XXX.PY文件
- 给文件+x执行
- 执行并返回结果
- 删除临时py文件,sleep 0退出
执行状态:
2、使用ansible在多台机器上添加用户
前提条件:
- 安装并且配置好ansible
yum install epel-release
yum install ansible
vim /etc/ansible/hosts 加入主机清单,默认端口号为22,端口有修改需要写明端口号
vim /etc/ansible/ansible.cfg 修改ansible配置文件[srvs] 192.168.38.100 142.11.227.114:80 [kvm] 142.11.227.114:80建议启用日志功能 log_path = /var/log/ansible.log 取消首次连接被控制服务器验证 host_key_checking = False 修改默认模块为shell 避免不支持某些命令,方便今后的操作不用输入-m shell module_name = shell - 控制主机的pub key已经导入到各个被控制主机的/root/.ssh/authorized_keys文件中
可参考此脚本
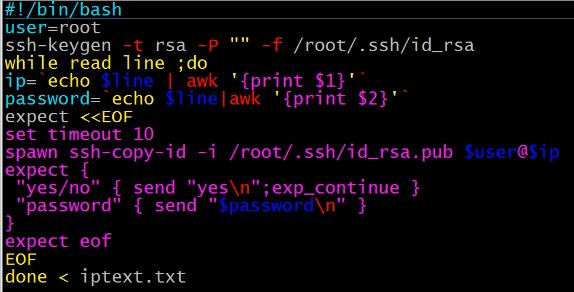
开始添加多用户
[root@centos7 .ssh]#ansible all -m user -a 'name=test001 comment="test user" shell="/sbin/nologin"' 192.168.38.100 | CHANGED => {
"ansible_facts": {
"discovered_interpreter_python": "/usr/bin/python"
},
"changed": true,
"comment": "test user",
"create_home": true,
"group": 11212,
"home": "/home/test001",
"name": "test001",
"shell": "/sbin/nologin",
"state": "present",
"system": false,
"uid": 11212
}
142.11.227.114 | CHANGED => {
"ansible_facts": {
"discovered_interpreter_python": "/usr/bin/python"
},
"changed": true,
"comment": "test user",
"create_home": true,
"group": 11212,
"home": "/home/test001",
"name": "test001",
"shell": "/sbin/nologin",
"state": "present",
"system": false,
"uid": 11212
}
验证添加成功
[root@centos7 .ssh]#ansible all -a 'id test001'
192.168.38.100 | CHANGED | rc=0 >>
uid=11212(test001) gid=11212(test001) groups=11212(test001)
142.11.227.114 | CHANGED | rc=0 >>
uid=11212(test001) gid=11212(test001) groups=11212(test001)
[root@centos7 .ssh]#ansible all -a 'getent passwd test001'
192.168.38.100 | CHANGED | rc=0 >>
test001:x:11212:11212:test user:/home/test001:/sbin/nologin
142.11.227.114 | CHANGED | rc=0 >>
test001:x:11212:11212:test user:/home/test001:/sbin/nologin
3、用ansible-playbook编译安装nginx服务
httpd与nginx默认都使用的是80端口,自己觉得是否卸载主机上的httpd或修改端口
确保所有主机的epel源代可用
- 安装nginx,
yum install nginx - 建立playbook目录
mkdir /etc/ansible/playbook - 在playbook目录中建立templates目录
mkdir /etc/ansible/playbook/templates - 复制nginx.conf到templates目录加上.j2结尾
cp /etc/nginx/nginx.conf /etc/ansible/playbook/templates/nginx.conf.j2 - 在playbook目录中新建编辑 nginx.yml
vim nginx.yml
- hosts: kvm
remote_user: root
vars:
- Nport: 8080
tasks:
- name: install
yum: name=nginx
- name: template
template: src=nginx.conf.j2 dest=/etc/nginx/nginx.conf
notify: restart
- name: service
service: name=nginx state=started enabled=yes
handlers:
- name: restart
service: name=nginx state=restarted
- 编辑nginx.conf.j2
vim /etc/ansible/playbook/templates/nginx.conf.j2
server {
listen {{Nport}} default_server;
listen [::]:{{Nport}} default_server;
- 检测playbook文件是否有误
ansible-playbook -C nginx.yml - 安装、测试
ansible-playbook nginx.yml
[root@centos7 playbook]#ansible-playbook nginx.yml
PLAY [kvm] *********************************************************************
TASK [Gathering Facts] *********************************************************
ok: [142.11.227.114]
TASK [install] *****************************************************************
changed: [142.11.227.114]
TASK [template] ****************************************************************
changed: [142.11.227.114]
TASK [service] *****************************************************************
changed: [142.11.227.114]
RUNNING HANDLER [restart] ******************************************************
changed: [142.11.227.114]
PLAY RECAP *********************************************************************
142.11.227.114 : ok=5 changed=4 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
[root@centos7 playbook]#ansible kvm -a 'ps aux | grep nginx'
142.11.227.114 | CHANGED | rc=0 >>
root 17677 0.0 0.2 125116 2176 ? Ss 11:49 0:00 nginx: master process /usr/sbin/nginx
nginx 17678 0.0 0.6 125504 6968 ? S 11:49 0:00 nginx: worker process
root 17955 0.0 0.2 113184 2708 pts/1 S+ 11:51 0:00 /bin/sh -c ps aux | grep nginx
root 17957 0.0 0.2 112716 2312 pts/1 R+ 11:51 0:00 grep nginx
[root@centos7 playbook]#ansible kvm -a 'ss -ntlp | grep 8080'
142.11.227.114 | CHANGED | rc=0 >>
LISTEN 0 128 *:8080 *:* users:(("nginx",pid=17678,fd=6),("nginx",pid=17677,fd=6))
LISTEN 0 128 :::8080 :::* users:(("nginx",pid=17678,fd=7),("nginx",pid=17677,fd=7))
4、描述域名劫持的解决方法
一般的域名劫持都是因为DNS指向为默认的DNS,其对查询过程进行限制或修改导致发生域名劫持。还有可能本地hosts被篡改。
解决方法一般为手动指定公共DNS服务器,例如8.8.8.8,可有效避免DNS域名劫持。查看本地hosts是否被篡改。
5、描述dns的递归查询
例如在家中访问 www.example.com.,我们dns服务是用的小区的dns服务器,我向小区dns服务器询问www.example.com.的IP是多少。如果小区的dns服务器上有记录,直接将IP地址给家里的电脑,家中的电脑和小区的dns这种关系就是迭代查询。
如果小区的dns服务器没有记录该网址的IP地址,那么小区的dns就会自己去互联网上通过.根返回.com的dns服务器的地址,通过.com的dns服务器获得.example的dns服务器地址等等,像这样一级一级的查询到该网站的IP最终将IP传到小区的dns服务器上,这样的查询就是递归查询。

- 递归查询:查询时要求所请求的DNS服务器应答给客户端所请求的域名和IP的对应关系,客户机向本地DNS服务器发出查询请求,然后等待返回结果,如果本地域名服务器无法解析,自己会以DNS客户机的身份向其他域名服务器查询,直到最终得到IP地址。一般来说客户机进行查询时使用递归查询。
- 迭代查询:查询时所请求的DNS服务器应答给客户端的不一定是域名和IP的对应关系,也可能是另一台DNS服务器,让客户端再将请求发送到另一台DNS服务器进行查询,每次都以客户机的身份去各个DNS服务器查询。一般用于DNS服务器之间。
6、DNS工作原理详细解析
一次完整的查询请求经过的流程:
Client -->hosts文件 -->DNS Service Local Cache --> DNS Server (recursion) --> Server Cache --> iteration(迭代) --> 根–> 顶级域名DNS–>二级域名DNS…
client读取本机hosts文件看是否有对应的解析记录,如果有,则直接访问IP,如果没有,则向本地DNS服务器进行递归查询,若本地DNS服务器中有对应的解析记录,则查询结束,若无记录,则进行下面步骤
本地DNS服务器采用迭代查询,向一个根DNS服务器进行查询
根DNS服务器告诉本地DNS服务器,数据库中没有你所请求查询的记录,返回对应顶级域DNS服务器的IP地址
本地DNS服务器向顶级域DNS服务器请求查询
顶级域DNS服务器告诉本地DNS服务器,数据库中没有你所请求查询的记录,返回二级域DNS服务器的IP地址
本地DNS服务器向二级域DNS服务器请求查询
…
直至查到对应的解析记录,本地DNS服务器返回给客户机对应的IP地址,至此,查询结束。(递归查询)
7、dns区域转发与全局转发区别与实现方法
- 全局转发: 对非本机所负责解析区域的请求,全转发给指定的服务器
- 特定区域转发:仅转发对特定的区域的请求,比全局转发优先级高
注意:关闭dnssec功能
dnssec-enable no;
dnssec-validation no;
主要配置文件:
/etc/named.conf 主要配置端口,安全,日志相关日志
/etc/named.rfc1912.zones 定义正反解区域相关
/var/named/ 正反解数据库
主配置文件语法检查:named-checkconf
解析库文件语法检查:named-checkzone “ZONE_NAME” /var/named/ZONE_NAME.zone
一. 实现区域转发
- 发出转发的dns服务器(被转发的dns服务器)关闭dnssec功能。
vim /etc/named.conf
dnssec-enable no;
dnssec-validation no;
- 填写转发到哪个dns服务器,哪些域要被转发。
vim /etc/named.rfc1912.zones
zone "ZONE_NAME" IN {
type forward;
forward {first|only};
forwarders { SERVER_IP; };
};
only:转发查询后没结果看接受转发的服务器是否再向外查询返回结果。
first:转发查询后没结果自己向互联网再查询。
- 在接收转发的服务器上定义该域名的权威解析
vim /etc/named.rfc1912.zones
zone "ZONE_NAME" IN {
type master;
file "ZONE_NAME.zone";
};
二. 实现全局转发
- 发出转发的dns服务器设置转发到哪个服务器,关闭dnssec功能。
vim /etc/named.conf
options {
listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; };
forward only ;
forwarders {192.168.38.100;};
dnssec-enable no;
dnssec-validation no;
};
接收转发的服务器设置同上。
rndc reload
8、实现智能DNS
- /etc/named.conf 中做好地区别名与规划
[root@centos7 named]# vim /etc/named.conf
acl beijing {
192.168.2.0/24;
};
acl shanghai {
192.168.38.0/24;
};
acl other {
any;
};
options {
listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any;};
dnssec-enable no;
dnssec-validation no;
};
#zone "." IN {
# type hint;
# file "named.ca";
#};
//include "/etc/named.rfc1912.zones"; #此处注销
include "/etc/named.root.key";
view view_beijing {
match-clients { beijing; };
zone "." IN {
type hint;
file "named.ca";
};
zone "test.com.beijing" {
type master;
file "test.com.zones.beijing";
};
view view_shanghai {
match-clients { shanghai; };
zone "." IN {
type hint;
file "named.ca";
};
zone "test.com.shanghai" {
type master;
file "test.com.zones.shanghai";
};
view view_other {
match-clients { other; };
zone "." IN {
type hint;
file "named.ca";
};
zone "test.com" {
type master;
file "test.com.zones";
};
- 复制并更改区域文件,注意保留权限和所属组,再建立正反数据库文件
[root@centos7 named]#cp -p /etc/named.rfc1912.zones /etc/test.com.zones.beijing
[root@centos7 named]#cp -p /etc/named.rfc1912.zones /etc/test.com.zones.shanghai
[root@centos7 named]#cp -p /etc/named.rfc1912.zones /etc/test.com.zones
[root@centos7 named]vim /etc/test.com.zones.beijing
zone "test.com" IN {
type master;
file "test.com.zone.beijing";
};
[root@centos7 named]vim /var/named/test.com.zone.beijing
$TTL 1D
@ IN SOA ns1.test.com. admin.test.com. (
20190721
1H
5M
7D
1D )
IN NS ns1.test.com.
ns1 IN A 192.168.2.6
www IN A 192.168.2.6
@ IN A 192.168.2.6
[root@centos7 named]vim /etc/test.com.zones.shanghai
zone "test.com" IN {
type master;
file "test.com.zone.shanghai";
};
[root@centos7 named]vim /var/named/test.com.zone.shanghai
$TTL 1D
@ IN SOA ns1.test.com. admin.test.com. (
20190721
1H
5M
7D
1D )
IN NS ns1.test.com.
ns1 IN A 192.168.38.128
www IN A 192.168.38.128
@ IN A 192.168.38.128
rndc reload



