iptables实现NAT
NAT(network address translation)网络地址转换。
请求报文:修改源/目标IP,根据定义如何修改
响应报文:修改源/目标IP,根据跟踪机制自动实现
SNAT:source NAT
让本地网络中的主机通过某一特定地址访问外部网络,实现地址伪装,规则定义在NAT表的POSTROUTING, INPUT链上
请求报文:修改源IP
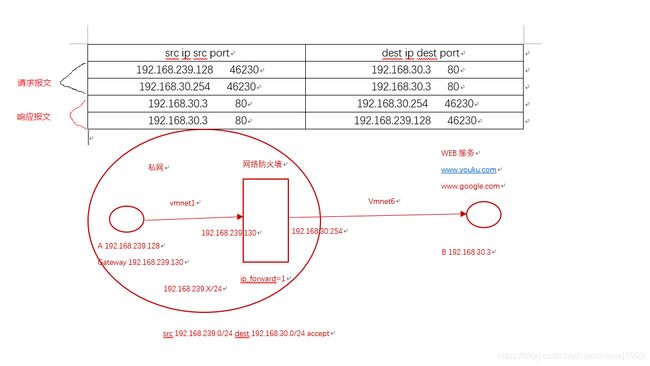
根据上面的网络拓扑图,我们来实现SNAT的功能。
在客户机上
[root@centos7 network-scripts]# route add default gw 192.168.239.130 dev ens33
[root@centos7 network-scripts]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.239.130 0.0.0.0 UG 0 0 0 ens33
0.0.0.0 192.168.43.1 0.0.0.0 UG 0 0 0 ens37
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 ens33
169.254.0.0 0.0.0.0 255.255.0.0 U 1003 0 0 ens37
192.168.43.0 0.0.0.0 255.255.255.0 U 0 0 0 ens37
192.168.122.0 0.0.0.0 255.255.255.0 U 0 0 0 virbr0
192.168.239.0 0.0.0.0 255.255.255.0 U 0 0 0 ens33
在WEB服务器上,配置web服务,采用虚拟主机的方式实现两个不同的站点。因为采用SNAT模式,服务器上看到访问HHTP服务的源地址是192.168.30.254。响应报文响应的也是这个地址,这两个地址在同一个网段内因此,WEB服务器的网关不用指向网络防火墙。
[root@centos7 conf.d]# echo www.youku.com >/var/www/html/index.html
[root@centos7 conf.d]# echo www.google.com >/var/www/html2/index.html
[root@centos7 conf.d]# cat vhosts.conf
servername www.youku.com
documentroot /var/www/html
servername www.google.com
documentroot /var/www/html2
[root@centos7 ~]# systemctl start httpd
在网络防火墙上
[root@centos7 network-scripts]# ifconfig
ens33: flags=4163 mtu 1500
inet 192.168.239.130 netmask 255.255.255.0 broadcast 192.168.239.255
inet6 fe80::20c:29ff:fe65:a88f prefixlen 64 scopeid 0x20
ether 00:0c:29:65:a8:8f txqueuelen 1000 (Ethernet)
RX packets 7002 bytes 598227 (584.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4551 bytes 565206 (551.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens37: flags=4163 mtu 1500
inet 192.168.30.254 netmask 255.255.255.0 broadcast 192.168.30.255
ether 00:0c:29:65:a8:99 txqueuelen 1000 (Ethernet)
RX packets 7007 bytes 562236 (549.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 556 bytes 53620 (52.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
开启路由转发功能
[root@centos7 network-scripts]# echo net.ipv4.ip_forward=1 >> /etc/sysctl.conf
[root@centos7 network-scripts]# sysctl -p
net.ipv4.ip_forward = 1
配置防火墙规则,这里使用的是固定IP
[root@centos7 network-scripts]# iptables -t nat -A POSTROUTING -s 192.168.239.0/24 ! -d 192.168.239.0/24 -j SNAT --to-source 192.168.30.254
测试
在客户端curl www.youku.com,然后在WEB服务器端的日志中可以看到访问的源地址是192.168.30.254
客户端
[root@centos7 ~]# curl www.youku.com
www.youku.com
查看WEB服务器的日志
[root@centos7 ~]# tail -f /var/log/httpd/access_log
192.168.30.254 - - [08/Sep/2019:14:38:42 +0800] "GET / HTTP/1.1" 200 14 "-" "curl/7.29.0"
192.168.30.254 - - [08/Sep/2019:14:39:14 +0800] "-" 408 - "-" "-"
192.168.30.254 - - [08/Sep/2019:15:47:18 +0800] "GET / HTTP/1.1" 200 14 "-" "curl/7.29.0"
192.168.30.254 - - [08/Sep/2019:15:48:12 +0800] "-" 408 - "-" "-"
192.168.30.254 - - [08/Sep/2019:15:48:30 +0800] "GET / HTTP/1.1" 200 14 "-" "curl/7.29.0"
192.168.30.254 - - [08/Sep/2019:15:48:32 +0800] "GET / HTTP/1.1" 200 14 "-" "curl/7.29.0"
192.168.30.254 - - [08/Sep/2019:15:48:33 +0800] "GET / HTTP/1.1" 200 14 "-" "curl/7.29.0"
也可以使用ping命令测试
客户端
[root@centos7 ~]# ping 192.168.30.3
PING 192.168.30.3 (192.168.30.3) 56(84) bytes of data.
64 bytes from 192.168.30.3: icmp_seq=1 ttl=63 time=0.547 ms
64 bytes from 192.168.30.3: icmp_seq=2 ttl=63 time=0.746 ms
64 bytes from 192.168.30.3: icmp_seq=3 ttl=63 time=1.48 ms
64 bytes from 192.168.30.3: icmp_seq=4 ttl=63 time=1.31 ms
在服务器端抓包,也可以发现访问的源地址是192.168.30.254
[root@centos7 ~]# tcpdump -nn icmp -i ens37
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens37, link-type EN10MB (Ethernet), capture size 262144 bytes
15:52:10.545083 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 1, length 64
15:52:10.545222 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 1, length 64
15:52:11.545745 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 2, length 64
15:52:11.545781 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 2, length 64
15:52:12.547066 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 3, length 64
15:52:12.547142 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 3, length 64
15:52:13.549105 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 4, length 64
15:52:13.549178 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 4, length 64
15:52:14.551434 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 5, length 64
15:52:14.551510 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 5, length 64
15:52:15.552668 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 6, length 64
15:52:15.552743 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 6, length 64
15:52:16.554881 IP 192.168.30.254 > 192.168.30.3: ICMP echo request, id 10769, seq 7, length 64
15:52:16.555005 IP 192.168.30.3 > 192.168.30.254: ICMP echo reply, id 10769, seq 7, length 64
DNAT:destination NAT
把本地网络中的主机上的某服务开放给外部网络访问(发布服务和端口映射),但隐藏真实IP。作用在NAT表的PREROUTING , OUTPUT链上
请求报文:修改目标IP
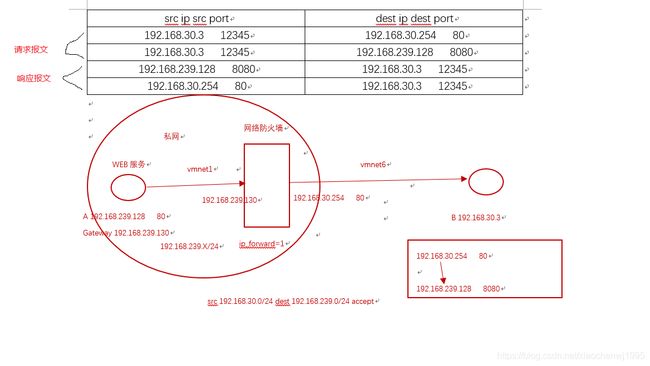
在内网的服务器上
[root@centos7 html]# echo 192.168.239.128 server> index.html
[root@centos7 html]# cat index.html
192.168.239.128 server
[root@centos7 html]# systemctl start httpd
[root@centos7 html]# ss -ntl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:111 *:*
LISTEN 0 5 192.168.122.1:53 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 128 127.0.0.1:631 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 127.0.0.1:6010 *:*
LISTEN 0 128 :::111 :::*
LISTEN 0 128 :::8080 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 128 ::1:631 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 ::1:6010 :::*
LISTEN 0 80 :::3306 :::*
[root@centos7 html]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.239.130 0.0.0.0 UG 0 0 0 ens33
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 ens33
192.168.122.0 0.0.0.0 255.255.255.0 U 0 0 0 virbr0
192.168.239.0 0.0.0.0 255.255.255.0 U 0 0 0 ens33
配置网络防火墙规则
[root@centos7 ~]# iptables -t nat -A PREROUTING -s 0/0 -d 192.168.30.254 -p tcp --dport 80 -j DNAT --to-destination 192.168.239.128:8080
测试,在外网的主机上
[root@centos7 ~]# curl 192.168.30.254:80
192.168.239.128 server
[root@centos7 ~]# curl 192.168.30.254
192.168.239.128 server
[root@centos7 ~]# curl 192.168.30.254
192.168.239.128 server
查看http日志信息,可以看到访问的源地址是192.168.30.3
[root@centos7 html]# tail -f /var/log/httpd/access_log
192.168.30.3 - - [08/Sep/2019:16:55:14 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
192.168.30.3 - - [08/Sep/2019:16:55:19 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
192.168.30.3 - - [08/Sep/2019:16:55:24 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
192.168.30.3 - - [08/Sep/2019:16:55:41 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
192.168.30.3 - - [08/Sep/2019:16:55:48 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
192.168.30.3 - - [08/Sep/2019:16:55:49 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.29.0"
实现端口转发,
REDIRECT:
NAT表,可用于:PREROUTING OUTPUT 自定义链。通过改变目标IP和端口,将接受的包转发至不同端口
使用:–to-ports port[-port]
这条规则作用在本机上,在192.168.239.128上设置。
root@centos7 html]# iptables -t nat -A PREROUTING -d 192.168.239.128 -p tcp --dport 8080 -j REDIRECT --to-ports 80
测试
[root@centos7 network-scripts]# curl 192.168.239.128:8080
192.168.239.128 server
[root@centos7 network-scripts]# curl 192.168.239.128:8080
192.168.239.128 server