批量执行定时任务_执行批量维护任务安全策略
批量执行定时任务
介绍 (Introduction)
You may see it more commonly referenced as Database Instance File Initialization (DIFI). If you are not familiar with the file initialization, this is the process SQL Server has to go through when it is creating the data files for a given database, and also during an expansion event (either manually or from auto growth) for a database. It only pertains to the data file(s) of the database, as log files are not affected by this security policy. SQL Server will “zero out” the file, basically fill it up with a bunch of zeros to allocate the amount of space requested. If you are a new DBA, this configuration actually goes all the way back to SQL Server 2005.
您可能会看到它更常见地被称为数据库实例文件初始化(DIFI)。 如果您不熟悉文件初始化,则SQL Server在为给定数据库创建数据文件时以及在数据库的扩展事件(手动或自动增长)过程中必须经历此过程。 它仅适用于数据库的数据文件,因为日志文件不受此安全策略的影响。 SQL Server会将文件“清零”,基本上用一堆零填充它以分配请求的空间量。 如果您是新的DBA,则此配置实际上可以一直追溯到SQL Server 2005。
Now, one thing to note is that the local Administrator group on a given Windows Server automatically gets this permission. So as you should know, or be told now, you should never give your SQL Server service account local Administrator permission, it is not a good security posture for your environment. If your organization has any security standards to follow (HIPPA, SOX, PCI, etc.) it is an auditing point to verify that your SQL Server services do not have full administrator privileges on the local server.
现在,要注意的一件事是,给定Windows Server上的本地Administrator组自动获得此权限。 因此,正如您应该知道的或现在被告知的那样,您永远不要给SQL Server服务帐户本地管理员权限,这对您的环境而言不是一个好的安全状态。 如果您的组织具有要遵循的任何安全标准(HIPPA,SOX,PCI等),则它是验证您SQL Server服务在本地服务器上没有完全管理员特权的审核点。
SQL Server服务帐户 (SQL Server service account)
I am not going to go into detail of what type of service account you should use with SQL Server. Suffice to say, it is not a good thing to be running as the Local System account. In the best practice of the security world, I would suggest you use one of the following supported options:
我不会详细介绍您应该在SQL Server中使用哪种类型的服务帐户。 可以说,以本地系统帐户身份运行不是一件好事。 在安全领域的最佳实践中,建议您使用以下受支持的选项之一:
- Best option for domain environments] 域环境的最佳选择 ]
- Local User Account 本地用户帐号
- Managed Service Account 托管服务帐户
- default on Server 2008 R2+] Server 2008 R2 +上的默认帐户]
If you are working on Window Server 2008 the default service account during SQL Server installation will be the Network Service or Local System, depending on the particular service. If you are on Window Server 2008 R2 or higher the default is the Virtual Account. The Virtual Account takes naming format of “NT SERVICE\MSSQLSERVER” on a default instance. If you are on a new OS version, this is perfectly fine, and a secure method to use for the service account.
如果使用的是Window Server 2008,则SQL Server安装期间的默认服务帐户将是网络服务或本地系统,具体取决于特定的服务。 如果您使用的是Window Server 2008 R2或更高版本,则默认值为虚拟帐户。 虚拟帐户在默认实例上的命名格式为“ NT SERVICE \ MSSQLSERVER”。 如果您使用的是新的OS版本,那么这很好,并且是用于服务帐户的安全方法。
One special thing that you might not be aware of either, is that DIFI also effects your SQL Server Analysis Services (AS) databases. AS will zero out the file as well for those databases. So you should remember to add that service account into this setup as well if you have that in your environment.
您可能都不知道的一件事是DIFI也会影响您SQL Server Analysis Services(AS)数据库。 AS也将这些数据库的文件清零。 因此,如果您的环境中有该服务帐户,则还应记住将该服务帐户添加到此设置中。
问题迹象 (Problem signs)
There are actually a few messages you will find on your SQL Server instance(s) that will show DIFI could help or be needed. The message IDs 5144 and 5145 can be found in your SQL Server error logs when DIFI is not enabled on an instance. Now that does not mean DIFI will prevent this message from occurring at all, if you have auto growth set to an outrageous amount that your storage cannot keep up with, that is something different. You can review KB 2091024 to see the messages and information about the solution.
实际上,您会在SQL Server实例上找到一些消息,这些消息表明DIFI可能会有所帮助或需要。 未在实例上启用DIFI时,可以在SQL Server错误日志中找到消息ID 5144和5145。 现在,这并不意味着DIFI将完全阻止此消息的发生,如果您将自动增长设置为您的存储无法跟上的惊人数量,那是不同的。 您可以查看知识库文章2091024,以查看消息和有关解决方案的信息。
首先验证 (Verify first)
Before you go hollering at your administrator(s) about needing this permission, you can first verify that your SQL Server service account (or AS service account) actually has it or not.
在向管理员征询是否需要此权限之前,您可以首先验证您SQL Server服务帐户(或AS服务帐户)是否确实具有此权限。
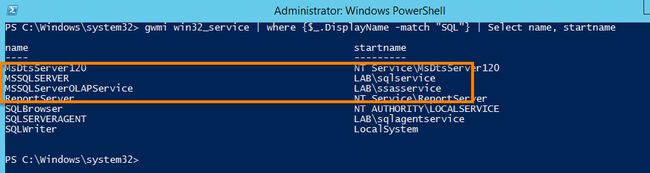
Get the service account name for a SQL Server instance, which the PowerShell way is:
gwmi win32_service | where {$_.DisplayName -match “SQL”} | select name, startname获取SQL Server实例的服务帐户名称,PowerShell方式为:
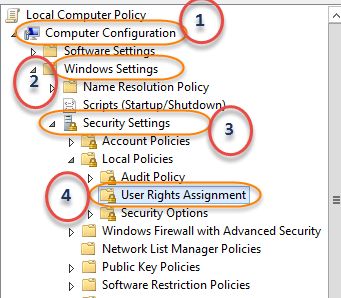
gwmi win32_service | 其中{$ _。DisplayName -match“ SQL”} | 选择名称,起始名称Another option is to type “gpedit.msc” into a run prompt
另一个选择是在运行提示符下键入“ gpedit.msc”
Go to the following path:
转到以下路径:
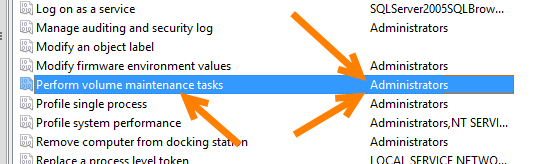
Find the “Perform Volume Maintenance Tasks” in the list
在列表中找到“执行卷维护任务”
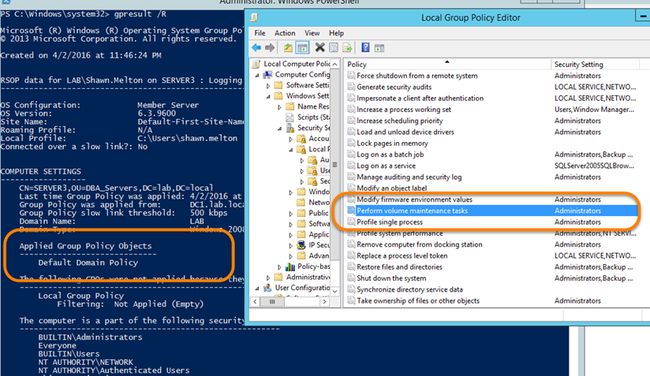
Which you can see on my server the only group that shows up is “Administrators”, so my SQL Server and AS service account do not have the permission currently.
您在服务器上看到的唯一显示的组是“管理员”,因此我SQL Server和AS服务帐户当前没有权限。
域环境设置 (Domain environment setup)
The most common environment I see is an Active Directory (AD) Domain configuration. I am going to walk through how I would set this up and hopefully show that it will save you time, and ensure any SQL Server machine you put on the domain gets this permission. The key to this time saving process is use of: Group Policies. They make the life of a system administrator or AD administrator so much easier when it comes to handing out permissions for a wide number of servers.
我看到的最常见的环境是Active Directory(AD)域配置。 我将逐步介绍如何进行设置,并希望它可以节省您的时间,并确保您放置在域中的任何SQL Server计算机都获得此权限。 节省时间的关键是使用:组策略。 当分发大量服务器的权限时,它们使系统管理员或AD管理员的工作变得更加轻松。
广告管理 (AD management)
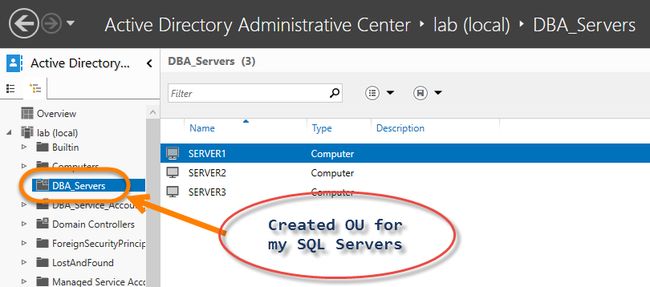
Just to explain one small thing when it comes to AD management. Just like you may order your files on your computer in folders, objects in Active Directory can be more easily managed in Organizational Units (OU). An example of my lab domain that I have setup:
只是为了解释广告管理方面的一件小事。 就像您可以在计算机上的文件夹中订购文件一样,可以在组织单位(OU)中更轻松地管理Active Directory中的对象。 我已设置的实验室域示例:
In my lab environment I created an OU called “DBA_Servers”. If you are building a new environment, or migrating a new environment, it can be useful to request your AD admin to move all of your servers to a dedicated OU. This provides two main things for your administrators:
在我的实验室环境中,我创建了一个名为“ DBA_Servers”的OU。 如果要构建新环境或迁移新环境,请要求AD管理员将所有服务器移至专用OU可能很有用。 这为您的管理员提供了两个主要方面:
- I have supported environments where a domain policy was implemented at the domain level (at that “lab (local)” level) that completely broke a customer’s SQL Server environment. Having a dedicated OU for the servers your servers can be excluded from a particular policy being applied. 我曾支持在域级别(在“实验室(本地)”级别)实施域策略的环境,该策略完全破坏了客户SQL Server环境。 具有专用于服务器的OU的服务器可以从所应用的特定策略中排除。
- If you need a policy created for your SQL Server environment, such as applying DIFI, it does not require a bunch of hurdles for your AD administrators. 如果您需要为SQL Server环境创建的策略(例如应用DIFI),则对于AD管理员来说并不需要很多障碍。
Overall, if this level of planning is done at the start of building an environment it can make things easier in the long run. As well, making things easier for those other teams that you have to work with at times (e.g. AD admins, SAN admins, etc.).
总体而言,如果在构建环境开始时就完成了这一级别的计划,从长远来看,它可以使事情变得容易。 同样,使您有时需要与之合作的其他团队(例如AD管理员,SAN管理员等)的工作变得更轻松。
域组 (Domain group)
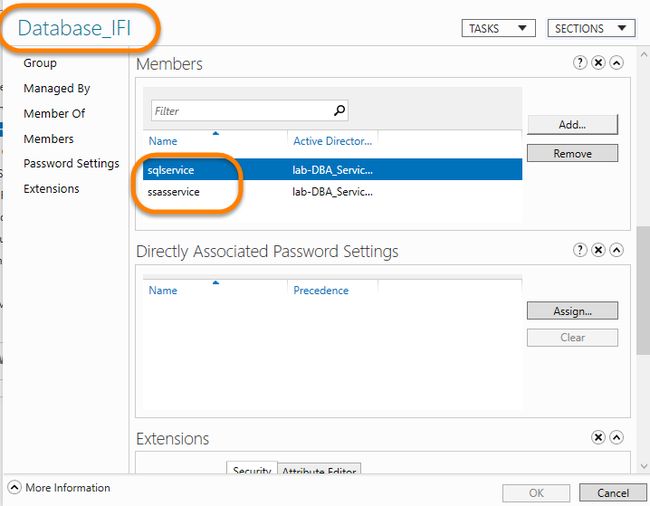
After I have that OU created, and all the SQL Server computer objects moved to it, I need to create a custom Domain Group for my SQL Server service account(s). I called mine “Database_IFI” and then added my SQL Server and the AS service account:
创建该OU,并将所有SQL Server计算机对象移至该OU之后,需要为我SQL Server服务帐户创建一个自定义域组。 我将其命名为“ Database_IFI”,然后添加了我SQL Server和AS服务帐户:
Create the group policy
创建组策略
Now I need to create the policy. When working with domain policies I have to utilize the Group Policy Management Console, but not the one I used to verify the permission (gpedit.msc), I need the “gpmmc.msc”. This console is available via the Window Server Remote Management pack that I have installed on a Windows 10 client within my lab domain.
现在,我需要创建策略。 使用域策略时,我必须利用组策略管理控制台,而不是我用来验证权限的那个(gpedit.msc),我需要“ gpmmc.msc”。 该控制台可通过我在实验室域内的Windows 10客户端上安装的Window Server远程管理包获得。
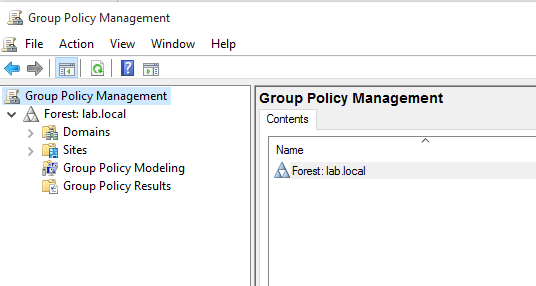
When the GPM is opened this is the view I am given:
当GPM打开时,这是我得到的视图:
I drill down into the Domains > lab.local and I am provided a list of the OUs in my AD setup along with a few other objects that are of no concern to me right now:
我向下钻取到Domains> lab.local,并在AD设置中提供了OU的列表以及一些我现在不关心的其他对象:
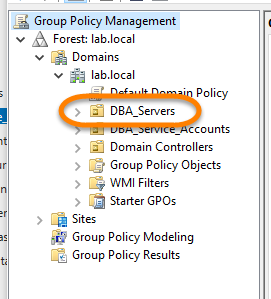
If I select the “DBA_Servers” folder, I can see that I already have one policy configured and will add another one to the list:
如果选择“ DBA_Servers”文件夹,则可以看到已经配置了一个策略,并将另一个添加到列表中:
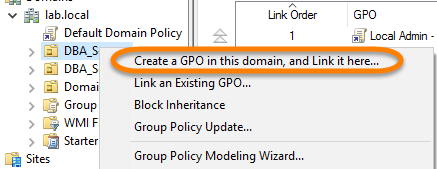
I need to right-click on the “DBA_Servers” folder and select “Create a GPO in this domain, and Link it here…”
我需要右键单击“ DBA_Servers”文件夹,然后选择“在此域中创建GPO,并在此处链接...”。
I give the GPO a good name like “Database IFI Permission – SQL Servers”. One thing about naming is it should match up to what policy it will apply. You can create a GPO and apply a dozen different permissions under one GPO, but in AD management that can be hard to manage. It is much easier to just create the GPOs with a 1:1 ratio to their permission being applied; one GPO has one permission policy configured.
我给GPO一个好名字,例如“ Database IFI Permission – SQL Servers”。 关于命名的一件事是,它应该与将应用的策略相匹配。 您可以创建一个GPO并在一个GPO下应用十二种不同的权限,但是在AD管理中可能很难管理。 创建GPO时,按其允许的比例1:1进行创建要容易得多。 一个GPO配置了一个权限策略。
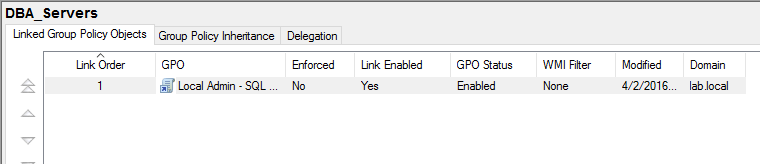
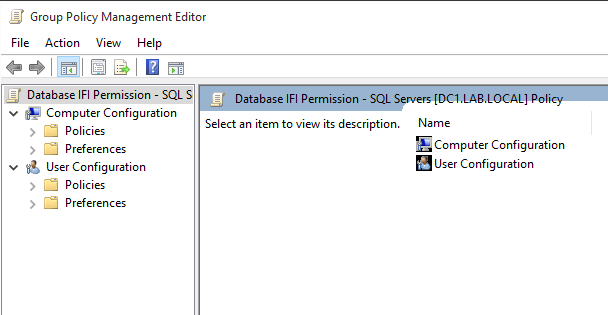
Once that GPO is named I will see it added to the list under the “DBA_Servers” folder. I right-click on that GPO and select “Edit…”, which presents me with this window:
命名该GPO之后,我将看到它已添加到“ DBA_Servers”文件夹下的列表中。 我在该GPO上单击鼠标右键,然后选择“编辑...”,该窗口向我显示:
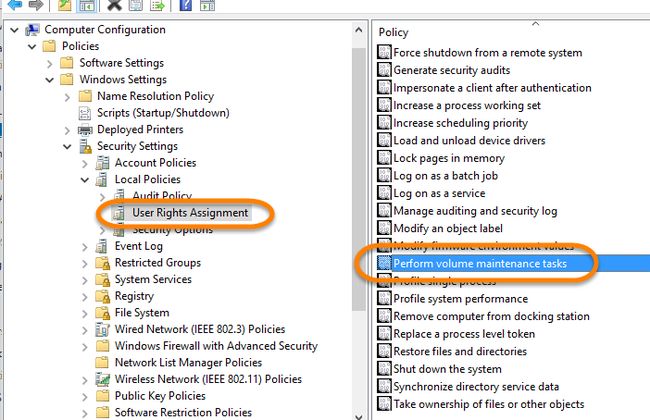
I follow a similar path as I did when I verified the setting:
我遵循与验证设置时相似的路径:
Open up the properties for the “Perform volume maintenance tasks” and just do the following steps:
打开“执行卷维护任务”的属性,然后执行以下步骤:
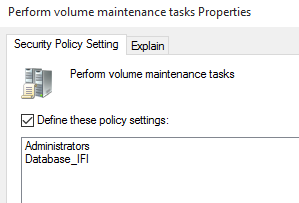
- Check the box for “Define these policy settings” 选中“定义这些策略设置”框
- Click on “Add User or Group…” 点击“添加用户或组…”
- Type in the following: Administrators;Database_IFI 键入以下内容:Administrators; Database_IFI
- Click OK twice. 单击确定两次。
One thing to remember is that whatever change is being made in a GPO, it can have an adverse effect on any member server the policy is applied on. I know that the local Administrators group already has access, and it has this for a reason so it needs to keep it. If I do not add the Administrators group to this policy, when it is applied to the servers in the OU it will be removed. So adding it here ensures it keeps it.
要记住的一件事是,无论在GPO中进行什么更改,它都会对应用该策略的任何成员服务器产生不利影响。 我知道本地Administrators组已经可以访问,并且由于某种原因它具有访问权限,因此需要保留它。 如果我没有将Administrators组添加到此策略,则将其应用于OU中的服务器时,它将被删除。 因此,在此处添加它可以确保保持不变。
现在再次验证 (Now verify again)
Now, I should be able to go back to my server and see that it has permissions. I go back to the server and check “gpedit.msc” and even try “gpresult /R” at a PowerShell prompt. I don’t see the policy applied to my server:
现在,我应该能够回到我的服务器并看到它具有权限。 我回到服务器并检查“ gpedit.msc”,甚至在PowerShell提示符下尝试“ gpresult / R”。 我没有看到该策略适用于我的服务器:
This is actually common because the Group Policy for a domain member server is not necessary applied instantly. It is guaranteed to be applied upon restart, but that is not something I want to do in a production environment. In these situations, where I know I want the policy to apply, I can force the server to reconcile the policies to the domain controller. I just run the following command: “gpupdate /force” from a PowerShell prompt:
这实际上很常见,因为不必立即应用域成员服务器的组策略。 保证可以在重新启动时应用它,但这不是我要在生产环境中执行的操作。 在这些情况下,我知道我想应用该策略,则可以强制服务器将这些策略与域控制器进行协调。 我只是在PowerShell提示符下运行以下命令:“ gpupdate / force”:
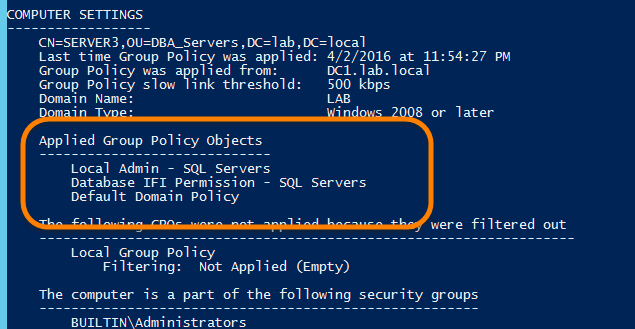
If I check “gpresult /R” results, I can see the policy is now being applied:
如果我检查“ gpresult / R”结果,则可以看到该策略正在被应用:
摘要 (Summary)
If you work out with your AD administrators to get this setup, it will allow you to ensure this security permission is applied to your SQL Server environment in the most efficient manner. This makes it easier for all teams involved and just takes a little planning, and maybe taking your administrator to lunch one day. When you get this all setup, any server you build just needs to be moved into the OU and automagically all the permissions you need can be applied. The command I used previously, “gpresult /R”, can be utilized to verify the administrators put your server in the right OU.
如果您与AD管理员一起工作以进行此设置,它将确保您以最有效的方式将此安全权限应用于SQL Server环境。 这使所有参与的团队都变得更加轻松,并且只需要进行一些计划,甚至可能让管理员有一天吃午饭。 完成所有设置后,只需将您构建的任何服务器移至OU中,即可自动应用所需的所有权限。 我之前使用的命令“ gpresult / R”可用于验证管理员将您的服务器放置在正确的OU中。
翻译自: https://www.sqlshack.com/perform-volume-maintenance-tasks-security-policy/
批量执行定时任务