Hybrid Encryption I(RSA和AES算法混合加密方案破解)
Hybrid Encryption I
https://www.mysterytwisterc3.org/en/challenges/level-ii/hybrid-encryption-i
Hybrid Encryption
A drawback of symmetric encryption schemes is the problem of key exchange.
Prior to the actual encryption the parties have to exchange a secret key in asecure way.
The encryption itself can be performed very efficiently.
Asymmetric encryption schemes solve the problem of key exchange
by using a key pair consisting of public and private key.
The data encryption, however, is very costly
To use the advantages of both symmetric and asymmetric, in practise one often uses a hybrid encryption.
This means that a random key K for some symmetric scheme is generated and the plaintext is encrypted using that scheme.
To transfer this session key K to the receiver, a public key scheme is employed to encrypt the session key.
You eavesdropped on a hybrid encryption communication.
You know that the asymmetric scheme RSA is used in its plain form, i.e. the session key is encrypted as c = K e mod N.
The session key itself is used in an 128 bit AES Cipher in ECB mode to encrypt the plaintext message.
Find the plaintext message.
In the addidional file you will find the public RSA parameters (N,e) and the ciphertexts.
The encryption of the session key under RSA is given as cp and the encryption of the plaintext under AES using the session key is given as cs.
混合加密
对称加密方案的一个缺点是密钥交换问题。
在进行实际加密之前,双方必须以安全的方式交换密钥。
加密本身可以非常有效地执行。
非对称加密方案解决了密钥交换问题
通过使用由公钥和私钥组成的密钥对。
然而,数据加密是非常昂贵的
利用对称和不对称的优点,在练习一通常使用混合加密。
这意味着生成某个对称方案的随机密钥K,明文使用该方案加密。
为了将这个会话密钥K传输给接收者,我们使用了一个公钥方案对会话密钥进行加密。
你窃听了一个混合加密通讯。
您知道非对称方案RSA在其普通格式中使用形式,即会话密钥加密为c = Ke mod N。
会话密钥本身以128位AES密码在ECB模式下用于加密明文消息。
查找明文消息。
在附加文件中,您将发现公共RSA参数(N,e)和密文。
在RSA下的会话密钥加密后以cp的形式给出,在AES下使用会话密钥对明文进行加密后为cs。
题目的意思是先使用了非对称算法RSA加密了对称算法AES的会话密钥,所以我们第一步首先要解密RSA算法得到会话密钥,题目中给出了已知的条件有:
密文:c_p =
0xc0eacf32dc0492464d9616fefc3d01f56589a137781bf6cf56784dea1c44ef52d61b1025655f370eb78646716f93e0a5
参数N:n =
0x9c5f36caf9adc60b4447897c639f1564ed0709251147276de030db395555c8afed912a198b334bd230198173128298126e958e38cac653e061035e300505eed1
指数e:e = 0x3
加密过程:c = me mod n,e=3
①当m3
②当m3>n,即m3=c+i * n。哪我们就爆破i,对c+i*n开三次根,直到得到的结果是整数。
源代码:
import gmpy2
c_p = 0xc0eacf32dc0492464d9616fefc3d01f56589a137781bf6cf56784dea1c44ef52d61b1025655f370eb78646716f93e0a5
n = 0x9c5f36caf9adc60b4447897c639f1564ed0709251147276de030db395555c8afed912a198b334bd230198173128298126e958e38cac653e061035e300505eed1
e = 0x3
i=0
while 1:
# c_p+i*n开三次根,直到返回找到一个整数根
temp =gmpy2.iroot(c_p+i*n, e)
# 返回结果包括开根的结果和是否为整数,(mpz(309658584779820310739729975902632468029), True)
if(temp[1]==1):
print(temp[0])
break
i=i+1
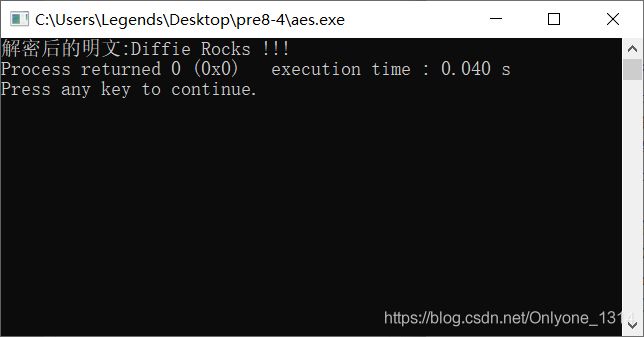
得到的用于AES算法中的会话密钥是309658584779820310739729975902632468029。
AES密钥的16进制形式就是0xe8f612f7fb5b6ac2a3e99a52ba6cde3d,又已知密文c_s=0xfd0b934c23288975648cd1d03ed3c5e2,接下来以128位AES密码在ECB模式下解密。
源代码aes.c:
#include