2021津门杯部分RE题wp
文章目录
-
- GoodRE
- easyRe
- babydsp
GoodRE
很简单的一个TEA算法,直接用脚本解密:
def decrypt(v, k):
v0 = v[0]
v1 = v[1]
x = 0xC6EF3720
delta = 0x9E3779B9
k0 = k[0]
k1 = k[1]
k2 = k[2]
k3 = k[3]
for i in range(32):
v1 -= ((v0 << 4) + k2) ^ (v0 + x) ^ ((v0 >> 5) + k3)
v1 = v1 & 0xFFFFFFFF
v0 -= ((v1 << 4) + k0) ^ (v1 + x) ^ ((v1 >> 5) + k1)
v0 = v0 & 0xFFFFFFFF
x -= delta
x = x & 0xFFFFFFFF
v[0] = v0
v[1] = v1
return v
if __name__ == '__main__':
encryptes = [0x79AE1A3B, 0x596080D3, 0x80E03E80, 0x846C8D73, 0x21A01CF7, 0xC7CACA32, 0x45F9AC14, 0xC5F5F22F]
flag=''
for i in range(len(encryptes)//2):
encrypted=encryptes[i*2:i*2+2]
#encrypted = [0x095598db,0x80f1ec61]
key = [0x11, 0x11,0x11,0x11]
decrypted = decrypt(encrypted, key)
flag+=hex(decrypted[0])[2:]
flag+=hex(decrypted[1])[2:]
print('flag=',flag.upper())
easyRe
这题给了3个文件,一个是输出文本,一个是re6,还有一个是lua程序。
lua程序是经过加密的;输出文本用base64解码后是一串数字,一共64个。
再分析re6这个程序,输入flag长度32字节,取出3个字节做随机数种子,生成33个dword随机数。同时对lua脚本解密,解密后的脚本如下:
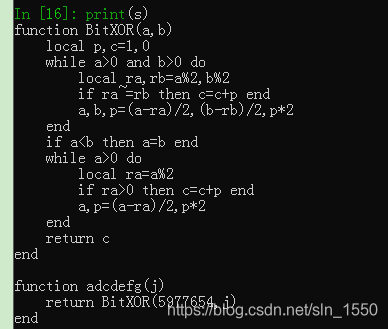
对每个输入的字节和每个随机数异或求和,再和5977654异或,最后输出,一共64个数,能和之前的输出文件对应上。
解题方法就是爆破随机数种子,在0-254之间:并用Z3求解flag,很快可以求出,如下图:

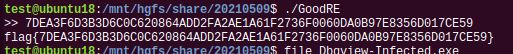
flag{e4da3b7fbbce2345d7772b0674a318d5}
babydsp
这题最耗时间,用ida打开可以看到是TMS320C6的处理器,TMS320C6x COFF Assembler格式文件,通过搜索得知可以通过CCS(Code Composer Studio)来执行和调试,这里花了很多时间下载和安装合适的CCS版本。
运行效果如下:
然后进入核心的代码:

代码比较复杂,大概算法是采用二叉树,根据输入会形成一个字符和权重值的映射表,然后就是比较函数:check_password,最终是按输入的顺序比较权重值:

输入的字符一定在“uq4i}c3eGVUDthCo_{mafMB8QJjygz2LZAvXRPWYx95sbkOwF6IpnrlESTN7KdH”这63个字符以内,因此我将这些字符全部输入(分2次),截取了字符计算后的权重值,然后按顺序匹配权重值就可以得到flag。
最终的代码如下:
tables=[0]*48
tables+=[
0x00000000,0x00000000,0x00000C97,0x00000405,
0x00000093,0x00000555,0x00000400,0x00000121,
0x000016DB,0x0000088C,0x00000000,0x00000000,
0x00000000,0x00000000,0x00000000,0x00000000,
0x00000000,0x00000A7D,0x000016EA,0x00001419,
0x00000CA2,0x000001E7,0x000002DA,0x000006E4,
0x00000090,0x000003FA,0x0000140C,0x00000030,
0x00000EE3,0x0000140B,0x00000124,0x00000556,
0x00000A7E,0x0000115E,0x00000894,0x000001E3,
0x00000091,0x00000A87,0x0000089D,0x00000A74,
0x00000C8D,0x000006DC,0x00000ED7,0x00000000,
0x00000000,0x00000000,0x00000000,0x00001A08,
0x00000000,0x000019F9,0x000006D5,0x000002DF,
0x00000092,0x0000055C,0x000019E9,0x0000115F,
0x0000116B,0x00000126,0x000013FE,0x000003FF,
0x00000123,0x000016E9,0x000002DB,0x000016F8,
0x000001E6,0x00000031,0x000002D6,0x000006DD,
0x00000EEE,0x00000000,0x00000C98,0x0000054F,
0x00000000,0x00000EE2,0x00001152,0x000019F8,
0x00000000,0x000001EA,0x00000000,0x00000000,
0x00000000,0x00000000,0x00000000,0x00000000,
]
result=[0x19e9,0x123,0x19f9,0x115f,0x19f8,0x140c,0xa87,0x6dd,0xeee,0x1a08,0x19f9,0x1a08,0x6d5,0x19f9,0x6d5,0xee2,0xee2,0xee2,0xee2,0x1a08,0xca2,0x6dd,0xa7e,0x1a08,0x2d6,0x1e7,0xc98,0x55c,0x894,0x6dd,0x55c,0x1ea]
flag=''
for i in result:
flag+=chr(tables.index(i))
print(flag)
输出:
flag{JUst_a_babyyyy_DsP_rEveRse}