部署 LVS-DR + keepalived 高可用群集(理论加案例)
文章目录
- 前言
- 一:LVS-DR工作原理
-
- 1.1:DR模式概述
- 1.2:如何分析LVS-DR数据包流向?
- 1.3:LVS-DR中存在的ARP问题
- 1.4:解决上述两个ARP问题的方法
- 二:LVS-DR部署
-
- 2.1:案例环境
- 2.2首先配置两个LVS 代理
-
- 2.2.1 安装相关软件 keepalived (双机热备)ipvsadm(LVS控制软件)
- 2.2.2 配置物理网卡接口,虚拟网卡接口
- 2.2.3 创建dr 脚本文件,方便操作
- 2.3 配置两台WEB 节点
-
-
- 2.3.1 安装httpd 软件
- 2.3.2 配置回环地址 loop 0
- 2.3.3编写web 服务脚本
- 2.4 在 两台LVS主备服务器keepalived进行如下设置:
-
- 2.4.1 配置 keepalived 参数
- 2.4.3 进行相关参数的修改,保证ROUTER-ID 不一样,vrrp 组 一样,优先级不一样
- 2.5 开启服务,将虚拟机网卡都绑定到仅主机模式,进行测试
- 2.6 测试 LVS 故障keepalived工具自动切换功能
-
- 2.6.1 手工停止虚拟接口,模拟故障测试
- 2.7测试成功,还是正常访问节点WEB服务器
-
前言
一:LVS-DR工作原理
1.1:DR模式概述
负载均衡群集工作模式–直接路由(Direct Routing)
简称DR模式,采用半开放式的网络结构,与TUN模式的结构类似,但各节点并不是分散在各地,而是与调度器位于同一个物理网络
负载调度器与各节点服务器通过本地网络连接,不需要建立专用的IP隧道
1.2:如何分析LVS-DR数据包流向?
为方便进行原理分析,将 Client与群集机器放在同一网络中,数据包流经的路线为1-2-3-4
1.Client向目标VIP发出请求, Director(负载均衡器)接收。此时IP包头及数据帧头信息为:
2 .Director根据负载均衡算法选择 Realserver_1,不修改也不封装IP报文,而是将数据帧的MAC地址改为RealServer_1的MAC地址,然后在局域网上发送。IP包头及数据帧头信息如下:
3.RealServer_1收到这个帧,解封装后发现目标IP与本机匹配( RealServer事先绑定了VIP),于是处理这个报文。随后重新封装报文,发送到局域网。此时IP包头及数据帧头信息为
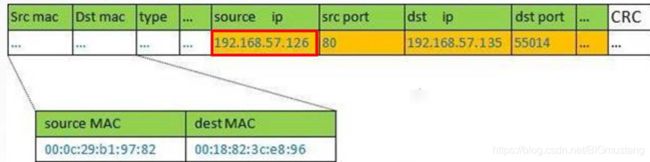
4.Client将收到回复报文。 Client认为得到正常的服务,而不会知道是哪一台服务器处理的
注意:如果跨网段,那么报文通过路由器经由 terne返回给用户
1.3:LVS-DR中存在的ARP问题
在LVS-DR负载均衡集群中,负载均衡器与节点服务器都要配置相同的VIP地址

在局域网中具有相同的IP地址,势必会造成各服务器ARP通信的紊乱
当一个ARP广播发送到LVS-DR集群时,因为负载均衡器和节点服务器都是连接到相同的网络上的,它们都会接收到ARP广播
此时只有前端的负载均衡器进行响应,其他节点服务器不应该响应ARP广播
对节点服务器进行处理,使其不响应针对VIP的ARP请求
使用虚接口lo:0承载ⅥP地址
设置内核参数 arp_ignore=1:系统只响应目的IP为本地IP的ARP请求
RealServe返回报文(源IP是VIP)经路由器转发,在重新封装报文时需要先获取路由器的MAC地址

发送ARP请求时, Linux默认使用IP包的源IP地址(即VIP)作为ARP请求包中的源IP地址,而不使用发送接口(例如ens33)的IP地址
路由器收到ARP请求后,将更新ARP表项
原有的VIP对应 Director的MAC地址会被更新为ⅥP对应RealServer的MAC地址

此时新来的请求报文,路由器根据ARP表项,会将该报文转发给RealServer,从而导致 Director的VIP失效
对节点服务器进行处理,设置内核参数arp_announce=2:系统不使用IP包的源地址来设置ARP请求的源地址,而选择发送接口的IP地址
1.4:解决上述两个ARP问题的方法
修改/etc/sysctl.conf文件
对节点服务器进行处理,使其不响应针对VIP的ARP请求
net.ipv4.conf.lo.arp_ignore = 1
net.ipv4.conf.lo.arp_announce = 2
系统不使用IP包的源地址来设置ARP请求的源地址,而选择发送接口的IP地址
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
二:LVS-DR部署
2.1:案例环境
为了进一步提高公司网站的负载能力,公司决定扩展现有的网站平台,基于LVS构筑负载均衡群集。考虑到群集的访问效率,管理员准备采用LVS群集的DR模式,共享存储设备存放在内部专有网络中
LVS1:192.168.100.20 PC-2
LVS2:192.168.100.3 PC-3
Web1:192.168.100.4 PC-4
Web2:192.168.100.5 PC-5
VIP=192.168.100.10
Win 10 :192.168.100.150
2.2首先配置两个LVS 代理
2.2.1 安装相关软件 keepalived (双机热备)ipvsadm(LVS控制软件)
root@pc-2 ~]# yum install keepalived ipvsadm -y
root@pc-3 ~]# yum install keepalived ipvsadm -y
修改配置文件,开启路由,以及关闭重定向功能
root@pc-2 ~] Vi /etc/sysctl.conf
net.ipv4.ip_forward=1
net.ipv4.conf.all.send_redirects=0
net.ipv4.conf.default.send_redirects=0
net.ipv4.conf.ens33.send_redirects=0
~
[root@pc-2 ~]# sysctl -p //使其生效
net.ipv4.ip_forward = 1 开启路由功能
PROC响应 关闭重定向功能
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.ens33.send_redirects = 0
2.2.2 配置物理网卡接口,虚拟网卡接口
[root@pc-2 network-scripts]# cp ifcfg-ens33 ifcfg-ens33:0
[root@pc-2 network-scripts]# vim ifcfg-ens33:0
2.2.3 创建dr 脚本文件,方便操作
cd /etc/init.d/
vim dr.sh
//脚本内容:
#!/bin/bash
GW=192.168.100.1
VIP=192.168.100.10
RIP1=192.168.100.4
RIP2=192.168.100.5
case "$1" in
start)
/sbin/ipvsadm --save > /etc/sysconfig/ipvsadm
systemctl start ipvsadm
/sbin/ifconfig ens33:0 $VIP broadcast $VIP netmask 255.255.255.255 broadcast $VIP up
/sbin/route add -host $VIP dev ens33:0
/sbin/ipvsadm -A -t $VIP:80 -s rr
/sbin/ipvsadm -a -t $VIP:80 -r $RIP1:80 -g
/sbin/ipvsadm -a -t $VIP:80 -r $RIP2:80 -g
echo "ipvsadm starting ---- ------[ok]"
;;
stop)
/sbin/ipvsadm -C
systemctl stop ipvsadm
ifconfig ens33:0 down
route del $VIP
echo "ipvsamd stoped--------------[ok]"
;;
status)
if [ ! -e /var/lock/subsys/ipvsadm ]; then
echo "ipvsadm stoped----------------------"
exit 1
else
echo "ipvsamd Runing------------[ok]"
fi
;;
*)
echo "Usage: $0 {start | stop | status }"
exit 1
esac
exit 0
添加权限,注意:先不要执行脚本!
chmod +x dr.sh



ifup ens33:0 //开启虚拟VIP
systemctl stop firewalld setenforce 0
service dr.sh start //开启LVS服务
2.3 配置两台WEB 节点
配置 PC-4 ,PC-5
2.3.1 安装httpd 软件
[root@pc-5 ~]# yum install -y httpd
[root@pc-4 ~]# yum install -y httpd
关闭防火墙
systemctl stop firewalld
setenforce 0
[root@pc-5 ]# vim /var/www/html/index.html
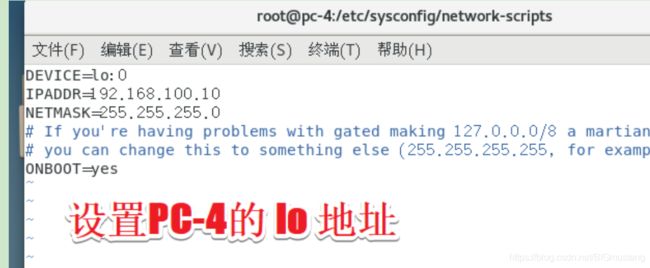
2.3.2 配置回环地址 loop 0
cd /etc/sysconfig/network-scripts/
cp ifcfg-lo ifcfg-lo:0
Vim ifcfg-lo:0
cd /etc/sysconfig/network-scripts/
cp ifcfg-lo ifcfg-lo:0
Vim ifcfg-lo:0
2.3.3编写web 服务脚本
root@pc-4 network-scripts]# cd /etc/init.d
[root@pc-4 init.d]# vim web.sh
#!/bin/bash
VIP=192.168.100.10
case "$1" in
start)
ifconfig lo:0 $VIP netmask 255.255.255.255 broadcast $VIP // 关闭ARP响应
/sbin/route add -host $VIP dev lo:0
echo "1" >/proc/sys/net/ipv4/conf/lo/arp_ignore
echo "2" >/proc/sys/net/ipv4/conf/lo/arp_announce
echo "1" >/proc/sys/net/ipv4/conf/all/arp_ignore
echo "2" >/proc/sys/net/ipv4/conf/all/arp_announce
sysctl -p >/dev/null 2>&1
echo "RealServer Start OK"
;;
stop)
ifconfig lo:0 down
route del $VIP /dev/null 2>&1
echo "0" >/proc/sys/net/ipv4/conf/lo/arp_ignore //启动ARP响应
echo "0" >/proc/sys/net/ipv4/conf/lo/arp_announce
echo "0" >/proc/sys/net/ipv4/conf/all/arp_ignore
echo "0" >/proc/sys/net/ipv4/conf/all/arp_announce
echo "RealServer Stopd"
;;
*)
echo "Usage: $0 {start|stop}"
exit 1
esac
exit 0
2.4 在 两台LVS主备服务器keepalived进行如下设置:
2.4.1 配置 keepalived 参数
PC-2 和 PC-3 服务器上
编辑keepalived
cd /etc/keepalived/
Root@pc-2 keepalived]# vim keepalived.conf
#! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 127.0.0.1 //第一处修改:改为127.0.0.1
smtp_connect_timeout 30
router_id LVS_01 //第二处修改:LVS2服务器修改为02
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state MASTER //第三处:备用服务器LVS2改为BACKUP
interface ens33 //第四处:改为ens33
virtual_router_id 10 //第五处:虚拟组,两个LVS服务器必须一样
priority 100 //第六处:备用LVS2优先级小于100,设为90
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.100.10 //第七处:只要虚拟IP地址
}
}
virtual_server 192.168.100.10 80 {
//第八处:虚拟IP地址和端口
delay_loop 6
lb_algo rr
lb_kind DR //第九处:我们使用的是LVS的DR模式
persistence_timeout 50
protocol TCP
real_server 192.168.100.4 80 {
//10、web1服务器节点
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
real_server 192.168.100.5 80 {
//11、web2的服务器节点
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
}
### 2.4.2 将文件复制到另外一台LVS
[root@pc-2 keepalived]# scp keepalived.conf root@192.168.100.3:/etc/keepalived/
The authenticity of host '192.168.100.3 (192.168.100.3)' can't be established.
ECDSA key fingerprint is SHA256:90aPw0S3HsHIz87PlUJMnwuceFtLo+xqNo6qSzF4vME.
ECDSA key fingerprint is MD5:86:db:7f:af:8d:e0:7d:c0:a2:0c:b1:17:e9:9f:0b:5d.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.3' (ECDSA) to the list of known hosts.
[email protected]'s password:
keepalived.conf
2.4.3 进行相关参数的修改,保证ROUTER-ID 不一样,vrrp 组 一样,优先级不一样
2.5 开启服务,将虚拟机网卡都绑定到仅主机模式,进行测试
systemctl restart keepalived
systemctl restart ipvsadm.service
service network restart
service dr.sh start
service web.sh start
2.6 测试 LVS 故障keepalived工具自动切换功能
keepalived工具可以自动故障切换,把LVS1服务器服务关闭,模拟故障,如果客户端依旧可以和虚拟 IP地址 互通,且能够正常访问网站的话,就说明 LVS2 就代替 LVS1 工作了,防止单点故障的效果实现了。
2.6.1 手工停止虚拟接口,模拟故障测试
root@pc-2 ~]# ifdown ens33:0
[root@pc-2 ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.100.20 netmask 255.255.255.0 broadcast 192.168.100.255
inet6 fe80::20c:29ff:fe5c:722e prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:5c:72:2e txqueuelen 1000 (Ethernet)
RX packets 6353 bytes 497090 (485.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12384 bytes 1197061 (1.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 53132 bytes 4193520 (3.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 53132 bytes 4193520 (3.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:bc:78:98 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)