案例章节:华为防火墙NAT策略配置
前言
上一章说过了NAT的管理方式,现在主要针对NAT No-PAT,NAPT,Easy_ip进行配置。
NAT No - PAT
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info en
Info: Information center is disabled.
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.1.254 24
[USG6000V1-GigabitEthernet1/0/1]undo shu
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[USG6000V1-GigabitEthernet1/0/1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 202.96.1.1 24
[USG6000V1-GigabitEthernet1/0/0]undo shu
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]quit
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 202.96.1.2
(2)配置安全策略
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface g1/0/1 //内网接口加入 trust区域
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add int g1/0/0 //外网接口加入 untrust区域
[USG6000V1-zone-untrust]quit
[USG6000V1]security-policy //配置安全策略
[USG6000V1-policy-security]rule name sec_1 //配置第一个规则并指定规则名sec_1
[USG6000V1-policy-security-rule-sec_1]source-zone trust //指定条件
[USG6000V1-policy-security-rule-sec_1]destination-zone untrust
[USG6000V1-policy-security-rule-sec_1]source-address 192.168.1.0 24
[USG6000V1-policy-security-rule-sec_1]action permit //指定动作
[USG6000V1-policy-security-rule-sec_1]quit
[USG6000V1-policy-security]quit
[USG6000V1]
(3)配置NAT地址组,地址组中的地址对应的是公网地址
[USG6000V1]nat address-group natgroup //配置NAT地址组,指定名称 natgroup
[USG6000V1-address-group-natgroup]section 0 202.96.1.10 202.96.1.11 //通过 section关键字指定地址组的起始地址和结束地址,该地址应该为公网地址
[USG6000V1-address-group-natgroup]mode no-pat local //指定地址组的模式为no-pat,即为 NAT No-PAT模式。local关键字表示对本区域有效
[USG6000V1-address-group-natgroup]quit
[USG6000V1]
(4)配置NAT策略
[USG6000V1]nat-policy //配置NAT策略
[USG6000V1-policy-nat]rule name natpolicy //配置名称为 natpolicy的NAT规则
[USG6000V1-policy-nat-rule-natpolicy]source-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-natpolicy]source-zone trust
[USG6000V1-policy-nat-rule-natpolicy]destination-zone untrust
[USG6000V1-policy-nat-rule-natpolicy]action nat address-group natgroup //指定动作,满足条件的数据包将依据地址组做 NAT No-PAT方式的源地址转换
[USG6000V1-policy-nat-rule-natpolicy]quit
[USG6000V1-policy-nat]quit
[USG6000V1]
注:
NAT策略不同于安全策略,安全策略是针对经过的数据流常规则检查,匹配的数据包或者转发,或者丢弃,安全策略决定了流量能否通过防火墙。而NAT策略对经过的数据流做规则检查,匹配的数据包或者做地址转换,或者不做地址转换,NAT策略决定了哪些流量需要NAT转换。
(5)针对转换后的全局地址(NAT地址组中的地址)配置黑洞路由
[USG6000V1]ip route-static 202.96.1.10 32 NULL 0
[USG6000V1]ip route-static 202.96.1.11 32 NULL 0
(6) 将其他设备配置完成:
R1的配置:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info en
Info: Information center is disabled.
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 202.96.1.2 24
[R1-GigabitEthernet0/0/0]undo shu
Info: Interface GigabitEthernet0/0/0 is not shutdown.
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 202.96.2.1 24
[R1-GigabitEthernet0/0/1]undo shu
Info: Interface GigabitEthernet0/0/1 is not shutdown.
[R1-GigabitEthernet0/0/1]quit
[R1]
(7)验证NAT配置
通过验证发现,PC1可以ping外网PC2,在会话表到达最大老化时间之前更换PC1的IP地址为192.168.1.5,再次访问PC2依然可以通信。当继续将PC1的IP地址更换为192.168.1.6时,无法通信。这是因为NAT地址组中只有2个可用于转换的地址,只能2个用户同时上网,在防火墙上查看会话表及 Server-map表,输出结果如下:
<USG6000V1>display firewall session table
Current Total Sessions : 9
icmp VPN: public --> public 192.168.1.5:5762[202.96.1.11:5762] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.4:2690[202.96.1.10:2690] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:6274[202.96.1.11:6274] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:6018[202.96.1.11:6018] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.4:2434[202.96.1.10:2434] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:5506[202.96.1.11:5506] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.4:1666[202.96.1.10:1666] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.4:2946[202.96.1.10:2946] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.4:2178[202.96.1.10:2178] --> 202.96.2.2:2048
<USG6000V1>display firewall server-map
Current Total Server-map : 4
Type: No-Pat Reverse, ANY -> 202.96.1.10[192.168.1.4], Zone: untrust
Protocol: ANY, TTL:---, Left-Time:---, Pool: 0, Section: 0
Vpn: public
Type: No-Pat Reverse, ANY -> 202.96.1.11[192.168.1.5], Zone: untrust
Protocol: ANY, TTL:---, Left-Time:---, Pool: 0, Section: 0
Vpn: public
Type: No-Pat, 192.168.1.5[202.96.1.11] -> ANY, Zone: untrust
Protocol: ANY, TTL:360, Left-Time:27, Pool: 0, Section: 0
Vpn: public
Type: No-Pat, 192.168.1.4[202.96.1.10] -> ANY, Zone: untrust
Protocol: ANY, TTL:360, Left-Time:13, Pool: 0, Section: 0
Vpn: public
NAPT
(1)配置网络参数及路由。
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info en
Info: Information center is disabled.
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.1.254 24
[USG6000V1-GigabitEthernet1/0/1]undo shu
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[USG6000V1-GigabitEthernet1/0/1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 202.96.1.1 24
[USG6000V1-GigabitEthernet1/0/0]undo shu
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]quit
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 202.96.1.2
(2)配置安全策略
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g1/0/1
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add int g1/0/0
[USG6000V1-zone-untrust]quit
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_1
[USG6000V1-policy-security-rule-sec_1]source-zone trust
[USG6000V1-policy-security-rule-sec_1]destination-zone untrust
[USG6000V1-policy-security-rule-sec_1]source-address 192.168.1.0 24
[USG6000V1-policy-security-rule-sec_1]action permit
[USG6000V1-policy-security-rule-sec_1]quit
[USG6000V1-policy-security]quit
(3)配置NAT地址组,地址组中的地址对应的是公网地址
[USG6000V1]nat address-group natgroup
[USG6000V1-address-group-natgroup]section 0 202.96.1.10 202.96.1.11
[USG6000V1-address-group-natgroup]mode pat
[USG6000V1-address-group-natgroup]quit
(4)配置NAT策路
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name natpolicy
[USG6000V1-policy-nat-rule-natpolicy]source-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-natpolicy]source-zone trust
[USG6000V1-policy-nat-rule-natpolicy]destination-zone untrust
[USG6000V1-policy-nat-rule-natpolicy]action nat address-group natgroup
[USG6000V1-policy-nat-rule-natpolicy]quit
[USG6000V1-policy-nat]quit
[USG6000V1]
(5)针对转换后的全局地址(NAT地址组中的地址)配置黑洞路由。
[USG6000V1]ip route-static 202.96.1.10 32 NULL 0
[USG6000V1]ip route-static 202.96.1.11 32 NULL 0
(6)验证NAT配置
通过验证发现,PC1可以ping外网PC2,在会话表到达最大老化时间之前更换PC1的IP地址为192.168.1.5,再次访问PC2依然可以通信。当继续将PC1的IP地址更换为192.168.1.6时,依然可以通信,这是因为虽然NAT地址组中只有2个可用于转换的地址,但是NAPT模式,可以基于端口复用,一个地址理论上可以允许65535(最大端口数量)个用户上网。在防火墙上查看会话表及Server-magp表
[USG6000V1]display firewall session table
Current Total Sessions : 4
icmp VPN: public --> public 192.168.1.6:5059[202.96.1.11:2059] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:64194[202.96.1.11:2057] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:63682[202.96.1.11:2055] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.6:4547[202.96.1.11:2058] --> 202.96.2.2:2048
[USG6000V1]display firewall server-map
Current Total Server-map : 0
通过上面的输出结果可以看到,在会话表中,源地址和源端口同时被转换而且默认情况下,防火墙从地址组中的最大地址开始转换。同时,NAPT方式NAT转换中,默认不生成 Server-map表项内容。
出接口地址(Easy-IP)
(1)配置网络参数及路由。
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info en
Info: Information center is disabled.
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.1.254 24
[USG6000V1-GigabitEthernet1/0/1]undo shu
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[USG6000V1-GigabitEthernet1/0/1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 202.96.1.1 24
[USG6000V1-GigabitEthernet1/0/0]undo shu
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]quit
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 202.96.1.2
(2)配置安全策略
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g1/0/1
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add int g1/0/0
[USG6000V1-zone-untrust]quit
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_1
[USG6000V1-policy-security-rule-sec_1]source-zone trust
[USG6000V1-policy-security-rule-sec_1]destination-zone untrust
[USG6000V1-policy-security-rule-sec_1]source-address 192.168.1.0 24
[USG6000V1-policy-security-rule-sec_1]action permit
[USG6000V1-policy-security-rule-sec_1]quit
[USG6000V1-policy-security]quit
[USG6000V1]
(3)配置NAT策路
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name natpolicy
[USG6000V1-policy-nat-rule-natpolicy]source-address 192.168.1.0 24
[USG6000V1-policy-nat-rule-natpolicy]source-zone trust
[USG6000V1-policy-nat-rule-natpolicy]destination-zone untrust
//指定动作,满足条件的数据包将依据地址组做出接口方式转换
[USG6000V1-policy-nat-rule-natpolicy]action nat easy-ip //配置出接口方式
[USG6000V1-policy-nat-rule-natpolicy]quit
[USG6000V1-policy-nat]quit
[USG6000V1]
(4)验证NAT配置
通过验证发现,PC1可以ping外网PC2,在会话表到达最大老化时间之前更换PCI的IP地址为192.168.1.5,再次访问PC2依然可以通信。当继续将PCI的IP地址更换为192.168.1.6时,依然可以通信,这是因为出接口方式将内网所有地址转换为外网接口地址202.96.1.1,可以基于端口复用。一个地址理论上可以允许65535最大端口数量)个用户上网。在防火墙上查看会话表及Server-map表
[USG6000V1]display firewall session table
Current Total Sessions : 6
icmp VPN: public --> public 192.168.1.5:202[202.96.1.1:2117] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:65481[202.96.1.1:2116] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:714[202.96.1.1:2119] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:458[202.96.1.1:2118] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.5:65225[202.96.1.1:2115] --> 202.96.2.2:2048
icmp VPN: public --> public 192.168.1.6:59849[202.96.1.1:2114] --> 202.96.2.2:2048
[USG6000V1]display firewall server-map
Current Total Server-map : 0
通过上面的输出结果可以看到,在会话表中,转换后的源地址为202.96.1.1,源端口同时被转换。出接口方式NAT转换中,不需要NAT地址组,默认不生成 Server-map表项内容,也不需要配置黑洞路由。
NAT Server
NAT Server主要用于内部服务器需要对互联网提供服务的场景。
一般很少公司去配置在这个东西,做了也可能是因为某些特殊的业务
以下内容仅供参考
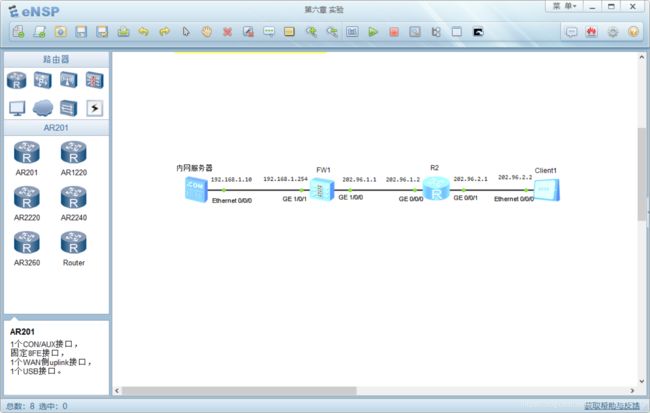
(1)配置网络参数及路由。
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]undo info en
Info: Information center is disabled.
[USG6000V1]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.1.254 24
[USG6000V1-GigabitEthernet1/0/1]undo shu
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[USG6000V1-GigabitEthernet1/0/1]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 202.96.1.1 24
[USG6000V1-GigabitEthernet1/0/0]undo shu
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[USG6000V1-GigabitEthernet1/0/0]quit
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 202.96.1.2
(2)配置安全策略
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add int g1/0/1
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add int g1/0/0
[USG6000V1-zone-untrust]quit
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name sec_1
[USG6000V1-policy-security-rule-sec_1]source-zone untrust
[USG6000V1-policy-security-rule-sec_1]destination-zone trust
[USG6000V1-policy-security-rule-sec_1]destination-address 192.168.1.0 24
[USG6000V1-policy-security-rule-sec_1]service ftp //配置条件为ftp协议
[USG6000V1-policy-security-rule-sec_1]action permit
[USG6000V1-policy-security-rule-sec_1]quit
[USG6000V1-policy-security]quit
(3)配置FTP应用层检测
该步骤可省路,华为防火墙默认情况下已经开启FTP应用层检测功能,下面只是展示配置。
[USG6000V1]firewall interzone trust untrust
[USG6000V1-interzone-trust-untrust]detect ftp
[USG6000V1-interzone-trust-untrust]quit
(4)配置 NAT Server
[USG6000V1]nat server natserver_ftp protocol tcp global 202.96.10.10 21 inside 192.168.1.10 21
natserver_ftp为 NAT Server策略的名字,
global后面跟映射后地址,
inside后面跟内部服务器的真实地址。
(5)配置黑洞路由
[USG6000V1]ip route-static 202.96.10.10 32 NULL 0
(6)R1配置静态路由
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info en
Info: Information center is disabled.
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 202.96.1.2 24
[R1-GigabitEthernet0/0/0]undo shu
Info: Interface GigabitEthernet0/0/0 is not shutdown.
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 202.96.2.1 24
[R1-GigabitEthernet0/0/1]undo shu
Info: Interface GigabitEthernet0/0/1 is not shutdown.
[R1-GigabitEthernet0/0/1]quit
[R1]ip route-static 202.96.10.0 24 202.96.1.1
(7)验证配置效果

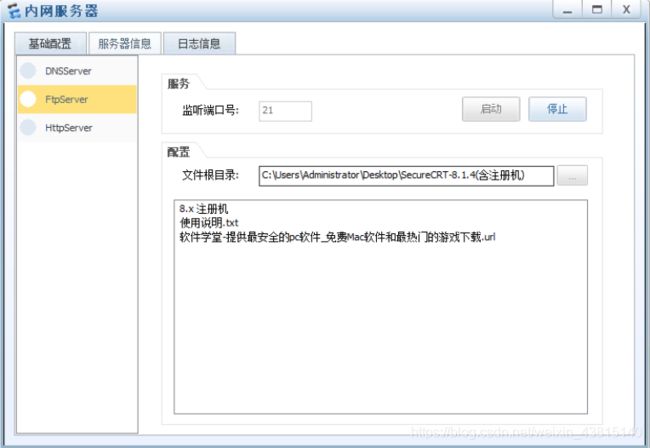
在eNSP中配置内网服务器的基础配置及服务器信息
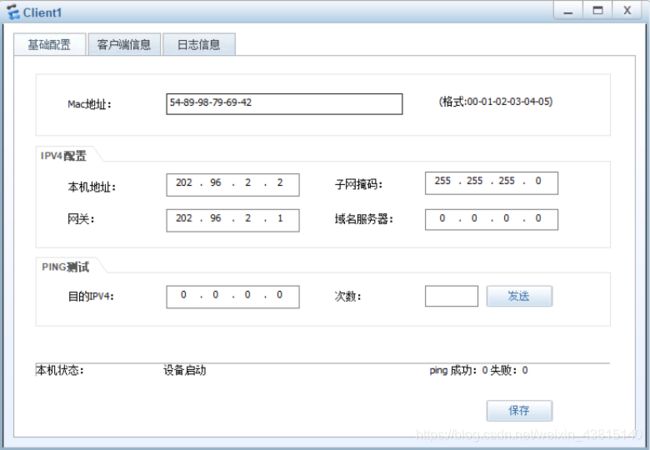
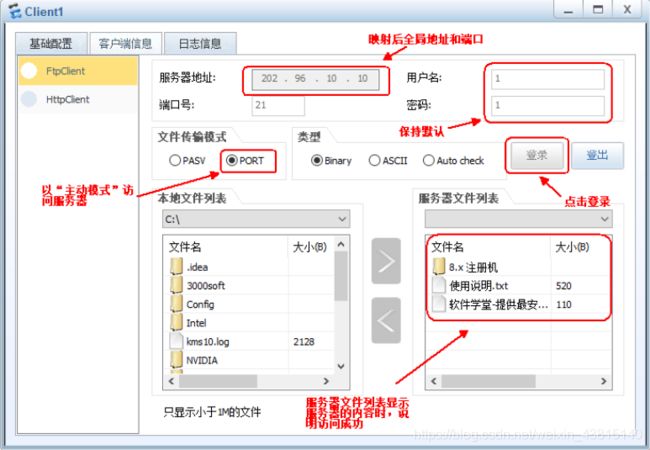
在eNSP中配置互联网客户端PC1基础配置及客户端信息配置,配置完成后单击 “登录” 按钮,如果可以看到内网服务器端的文件列表,说明访问成功