2021DASCTF八月挑战赛Writeup
2021DASCTF八月挑战赛Writeup
- MISC
-
- 签到
- 寒王'sblog
- stealer
- CRYPTO
-
- easymath
- let's play with rsa~
- ezRSA
MISC
签到
看看公告就有啦(嘿嘿嘿,真-签到题)
flag{welcome_to_dasctf_aug}
寒王’sblog
到给的博客里面看,可以看到写了关于outguess隐写的内容,整个博客就博客头像一个图片,猜测是图片,拿博客内容里面的密码试,不对。仔细观察博客,要找到flag.jpg就行了,因为之前有过搭建博客的经验,就决定到这个博客的搭建的平台gitee去寻找,找到gitee上的仓库
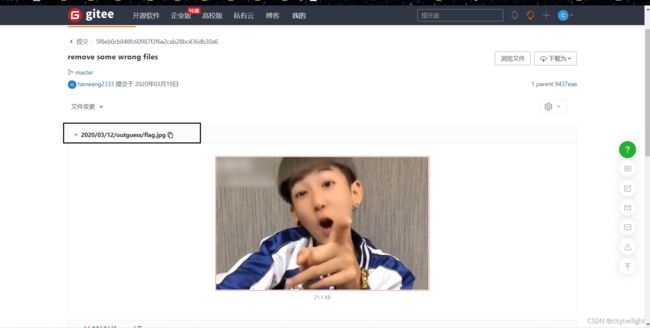
找到最新上传的文件,找到flag.jpg
在装有outguess的lunix系统下使用outguess的命令
outguess -k "hahahahahahaha" -r flag.jpg out.txt
得到flag
flag{50aa7fe02602264e7d8102746416cd74}
stealer
方法一
打开流量包,过滤DNS,发现有很多重复的数据,过滤ip
dns and ip.src==172.27.221.13
将info取出,观察发现是图片的base64编码,将字符串进行编辑方便转码。
字符串的变化如下:
原字符串:
Standard query 0x6a7a A iVBORw0KGgoAAAANSUhEUgAABMoAAAMxCAIAAACVY8g6AAAAAXNSR0IAr-.s4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAP-.lSURBVHhe7P1HlBzZmd6NUxtqjrShdtzoHB6ttMROswlNp/U9OiGKwd-.f8KbRDtXw3hdQMGWBgjcF1432aDZN04MUySGHMxqvgUajGWg*6fsoffpL-.ctf.com.cn OPT
操作:
1、去除多余字符串”Standard query 0x6a7a A”、”ctf.com.cn OPT”、”-.”
2、将“*”替换为“+”
转化后字符串:iVBORw0KGgoAAAANSUhEUgAABMoAAAMxCAIAAACVY8g6AAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAPlSURBVHhe7P1HlBzZmd6NUxtqjrShdtzoHB6ttMROswlNp/U9OiGKwdf8KbRDtXw3hdQMGWBgjcF1432aDZN04MUySGHMxqvgUajGWg+6fsoffpL
然后拿到图片
方法二(别人的做法,没弄懂)
使用tshark命令(linux安装)
tshark -r dump.pcapng -T fields -e dns.qry.name -Y "udp and dns.flags.response==0" > res.txt
from Crypto.Util.number import *
import base64
with open('D:\\桌面\\res.txt','r')as f:
lines=f.readlines()
tmp=[]
# tmp1=[]
for i,line in enumerate(lines):
if '-.ctf.com.cn' in line:
line1=line.strip().replace("-.ctf.com.cn","").replace('-.',"").replace("*","+")
tmp.append(line1)
# tmp1.append(len(line1))
b=''.join(tmp)
# print(b)
b1=base64.b64decode(b.encode())
open('res.png','wb').write(b1)
# print(tmp1)
拿到图片

flag(有点坑,只要输{}里面的md5就行)(md5里面没有o、l,所以图片里面的就是0和1)
1d3f729ac02bbc15f00adccd79207ab0
CRYPTO
easymath
题目:
assert(len(open('flag.txt', 'rb').read()) < 50)
assert(str(int.from_bytes(open('flag.txt', 'rb').read(), byteorder='big') << 10000).endswith(
'1862790884563160582365888530869690397667546628710795031544304378154769559410473276482265448754388655981091313419549689169381115573539422545933044902527020209259938095466283008'))
解题脚本:
import gmpy2
r = 1862790884563160582365888530869690397667546628710795031544304378154769559410473276482265448754388655981091313419549689169381115573539422545933044902527020209259938095466283008
y = r //(2 ** 175)
flag=(y*gmpy2.invert((2 ** 9825),(5 ** 175)))%(5 ** 175)
t=int(flag).to_bytes(50,byteorder='big')
print(t)
推理过程看大佬详细的WP
let’s play with rsa~
题目:
from sympy import isprime,nextprime
from Crypto.Util.number import getPrime as getprime ,long_to_bytes,bytes_to_long,inverse
flag='flag{***************}'
def play():
p=getprime(1024)
q=getprime(1024)
n=p*q
e=65537
print "Hello,let's play rsa~\n"
print 'Now,I make some numbers,wait a second\n'
n1=getprime(200)
n2=getprime(200)
number=n1*n2
print "Ok,i will send two numbers to you,one of them was encoded.\n"
print "Encode n1:%d,\n"%(pow(n1,e,n))
print "And n2:%d.\n"%n2
print "Information that can now be made public:the public key (n,e):(%d,%d)\n"%(n,e)
while True:
try:
c=int(raw_input("ok,now,tell me the value of the number (encode it for safe):"))
except:
print "Sorry,the input is illeagal, and the integer is accept~"
else:
break
d=inverse(e,(p-1)*(q-1))
m=pow(c,d,n)
if m==number:
print "It's easy and interesting,didn't it?\n"
print "This is the gift for you :"+flag
else:
print "Emmmmm,there is something wrong, bye~\n"
if __name__ == '__main__':
play()
题目给出n、e、pow(n1,e,n)、n2,求c
c = n u m b e r e m o d n = ( n 1 ∗ n 2 ) e m o d n = ( ( n 1 e m o d n ) ∗ ( n 2 e m o d n ) ) m o d n c=number^e modn=(n1*n2)^e modn=((n1^e modn)*(n2^emodn))modn c=numberemodn=(n1∗n2)emodn=((n1emodn)∗(n2emodn))modn
解题脚本:
(nc连上后会给出n、e、pow(n1,e,n)、n2)(这边以我nc得到的为例解题)
a = 12961409879680531683887750211274207457513312084569696075205671038512045983337591135848947097185699604453906986636309421174482607699320759296109315315716510712493223473758909665964696575970829701893860144925111613206750829054110563245759651636500800410800611799341091945238575572204744180794490600917575137957033704047292694479180193784052662788188456092611151703198998693787287001909323881137356776611226888433795185583110831437797736663143463934550216639249647171621868213923613785097805958460050341741859668930711065658867650077543948915545547210086665007538174470035036590197762464220663633877458187978934543610137
n2 = 975655394741265791809418303766264964352618962129532647048963
n=17984939304898650803158254840695698991976109768815074321859078838424106854968841553367705813676890566467526226777393337854287622085939699972674300671017434385268427211627149875201145197397614084981293689781191198014025392826496825995772507143839566355038037041002531894155725475951426118850290776380334951977592054772067742756171095427402698085736400771503751576111160577981596580675760373492947131376839865309631659266553436954094643785398989702090587019292927772255810184788705872695851653803767757272932373185881635106333541090761339331432007675440553128966093172385018789133381793617410838502288664808530049842759
e = 65537
c = (a * pow(n2, e, n)) % n
print(c)
提交c返回得到flag
ezRSA
题目:
from secret import flag
from Crypto.Util.number import *
from random import getrandbits
from hashlib import sha256
class EzRsa:
def __init__(self):
self.E = 0x10001
self.P = getPrime(1024)
self.Q = getPrime(1024)
while GCD((self.P-1)*(self.Q-1), self.E) != 1:
self.Q = getPrime(1024)
self.N = self.P*self.Q
def encrypt(self):
f = getrandbits(32)
c = pow(f, self.E, self.N)
return (f, c)
def encrypt_flag(self, flag):
f = bytes_to_long(flag)
c = pow(f, self.E, self.N)
return c
def proof():
seed = getrandbits(32)
print(seed)
sha = sha256(str(seed).encode()).hexdigest()
print(f"sha256({seed>>18}...).hexdigest() = {sha}")
sha_i = input("plz enter seed: ")
if sha256(sha_i.encode()).hexdigest() != sha:
exit(0)
if __name__ == "__main__":
proof()
print("welcome to EzRsa")
print("""
1. Get flag
2. Encrypt
3. Insert
4. Exit
""")
A = EzRsa()
coin = 5
while coin > 0:
choose = input("> ")
if choose == "1":
print(
f"pow(flag,e,n) = {A.encrypt_flag(flag)}\ne = 0x10001")
exit(0)
elif choose == "2":
f, c = A.encrypt()
print(f"plain = {f}\ncipher = {c}")
coin -= 1
elif choose == "3":
q = getrandbits(1024)
n = A.P*q
f = getrandbits(32)
c = pow(f, 0x10001, n)
print(f"plain = {f}\ncipher = {c}")
coin -= 1
elif choose == "4":
print("bye~")
else:
print("wrong input")
print("Now you get the flag right?")
给你5个coin,1次选择选项1,剩下四次选择选项2、3,当然是平均分配啦。得到四组f、c,两组同q解n,两组不同q解p
2选项
k1n=m21^e-c21
k2n=m22^e-c22
如果gcd(k1,k2)!=1:
那么gcd(k1n,k2n)=k5n
3选项
k3p*q=m31^e-c31
k4p*q=m32^e-c32
如果gcd(k3,k4)!=1:
那么gcd(k3p*q,k4p*q)=k6p
注意!! 要考虑不互素的情况
解题脚本:
import gmpy2
import libnum
m21 = 432540985
c21 = 7166105329146126000346846799091650898966999155559872071334165373085824639643357340387736867673948949437295645705541881374251463627954867215153754248479607455314501625059368006554456541594829525164594977575051605373580652734948771955132736124144931483976254038698037906320691536102595142817254635128316548640526742258396037736624974201452775566498749686521125689117077825614676728737889758051136033004868110506865885780994503922363995103685835021430586212695942148526088098869737679103317241698921778369133664568044970132074560250492688801256203642144910896398777358726349100245228945110134579964713795561704675625836
m22 = 832433238
c22 = 7068072774444874580843417684352862167509575799447044790925098273022805484339636628726051282308361580345803607470642836938247714174670185418844448110396620415640990336788728326764477161069207367942449417003955828316228120602384920985161057720856713726319102264142124823852191253035614776899528170161081527818980079567071942336953307505627425190268269896232927663142207335803294770668174075896648763132547865986794466490963711592538821527241565132434315309203043850884330880471384804577858687121008366255392040964137615612622718249221451373050550035988762430971866909043093506143514830259205676124914411640454949769514
m31 = 803092604
c31 = 9858061312093654496768968596097501224678614520625887945733170012236020650884606662567525945230720496908398041384708999618217120424456835837520254472794298782801785322426682540037835690902209518506529355172493693012753783133447141964001801908108246725869203422002782991435705743052764243289474944794105647964810575201516329006631623431476942605223169157252417903703894306636035587745490699125350078705206470856005724867576219806201586124846417599897712607698931227973794077078199208851048569386781383768930174636782623527857434298933738057735468619183445620008223850132708634891907499854374991187011529197042230646959
m32 = 407827977
c32 = 9863511828345122655318417789758326362972155249380521046094363106330914667719541369853161354832638229300504131579973818373987565381237053514335756148865347534946328612468008346912307466621874348634289579602255609545387098973079063492763912905225505720948250925345458151757932596246692755570051379007452621160936151870226301905454456709756228915895779952880287559823982391786349058583700592960020679432834444698462657381016169068254820248864870315358313005721370177632775087124268837165293488573472585505563114178522926629394131843183761480379187251213034958089397342815187352111820752209064084639988490442466085392363
c = 7381125776751959446383348016580510257704798119845665945201944033052555935656713698467247959233790127327214355429648255631628985300458608740078555958883489917944617439105827815224630836947733765684747756636698321010977136609738673905945624585893659056271171662069018034510708480585607431573246586211145591759329437967929837683542135674353508920055645757133194288396748112704213294483816147806206043194476131284869098739640171544518373288980710485452989822448431998651248525720045903096843189714992580406453445524466346573496924330678123163145497572043186951795043533663444724588959680284679456217293084234000618759022
e = 0x10001
# 3选项,求p
def p_def(p):
k = 1
while 1:
if gmpy2.is_prime(p):
return p
elif p % (k) == 0 and k != 1:
p = p // k
else:
k += 1
# 2选项求q
def q_def(n, p):
k = 1
q = n // p
while 1:
if gmpy2.is_prime(q):
return q
elif p % (k) == 0 and k != 1:
q = q // k
else:
k += 1
kp = gmpy2.gcd(m31 ** e - c31, m32 ** e - c32)
p=p_def(kp)
kn = gmpy2.gcd(m21 ** e - c21, m22 ** e - c22)
#print(kn)
q=q_def(kn,p)
n=p*q
print(n==p*q)
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
flag=pow(c,d,n)
print(flag)
print(libnum.n2s(int(flag)))